Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT

Threat actors are creating fake websites hosting trojanized software installers to trick unsuspecting users into downloading a downloader malware called Fruity with the goal of installing remote trojans tools like Remcos RAT.
“Among the software in question are various instruments for fine-tuning CPUs, graphic cards, and BIOS; PC hardware-monitoring tools; and some other apps,” cybersecurity vendor Doctor Web said in an analysis.
“Such installers are used as a decoy and contain not only the software potential victims are interested in, but also the trojan itself with all its components.”
The exact initial access vector used in the campaign is unclear but it could potentially range from phishing to drive-by downloads to malicious ads. Users who land on the fake site are prompted to download a ZIP installer package.
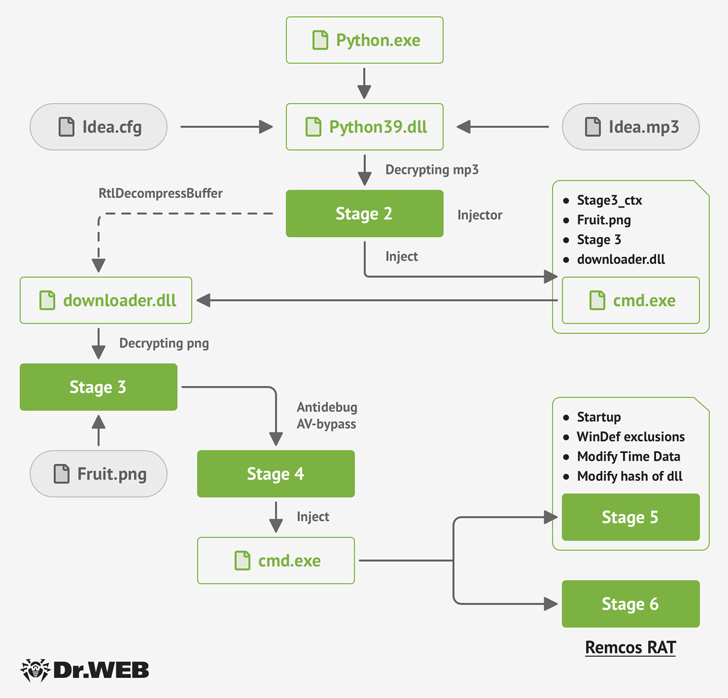
The installer, besides activating the standard installation process, stealthily drops the Fruity trojan, a Python-based malware that unpacks an MP3 file (“Idea.mp3”) to load an image file (“Fruit.png”) to activate the multi-stage infection.
“This image file uses the steganography method to hide two executables (.dll libraries) and the shellcode for the next-stage initialization inside it,” Doctor Web said.
Fruity is also designed to bypass antivirus detection on the compromised host and ultimately launch the Remcos RAT payload using a technique called process doppelgänging.
That said, the attack sequence could be exploited to distribute all kinds of malware, which makes it imperative that users stick to downloading software only from trustworthy sources.
The development comes as Bitdfender disclosed details of a malspam campaign delivering the Agent Tesla malware to harvest sensitive data from compromised endpoints.
It also follows a surge in malvertising operations that have targeted customers and businesses with tainted software boosted via ads on search engines.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
This includes a new wave of attacks dubbed Nitrogen in which fraudulent ISO archives are distributed using bogus ads that impersonate download pages for applications such as AnyDesk, WinSCP, Cisco AnyConnect, Slack, and TreeSize.
“This malvertising campaign leads to the propagation of the infection after initial exposure,” Bitdefender researchers Victor Vrabie and Alexandru Maximciuc said.
“For as long as they dwell in the victim’s network, the attackers’ primary goal is to obtain credentials, set up persistence on important systems and exfiltrate data, with extortion as the end goal.”





 " title="
" title="
