From Ransomware to Cyber Espionage: 55 Zero-Day Vulnerabilities Weaponized in 2022

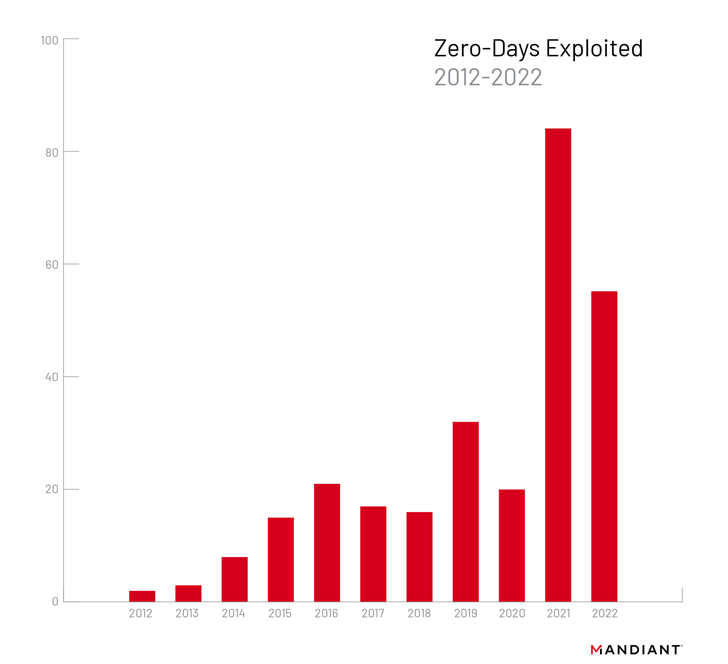
As
many
as
55
zero-day
vulnerabilities
were
exploited
in
the
wild
in
2022,
with
most
of
the
flaws
discovered
in
software
from
Microsoft,
Google,
and
Apple.
While
this
figure
represents
a
decrease
from
the
year
before,
when
a
staggering
81
zero-days
were
weaponized,
it
still
represents
a
significant
uptick
in
recent
years
of
threat
actors
leveraging
unknown
security
flaws
to
their
advantage.
The
findings
come
from
threat
intelligence
firm
Mandiant,
which
noted
that
desktop
operating
systems
(19),
web
browsers
(11),
IT
and
network
management
products
(10),
and
mobile
operating
systems
(six)
accounted
for
the
most
exploited
product
types.
Of
the
55
zero-day
bugs,
13
are
estimated
to
have
been
abused
by
cyber
espionage
groups,
with
four
others
exploited
by
financially
motivated
threat
actors
for
ransomware-related
operations.
Commercial
spyware
vendors
were
linked
to
the
exploitation
of
three
zero-days.
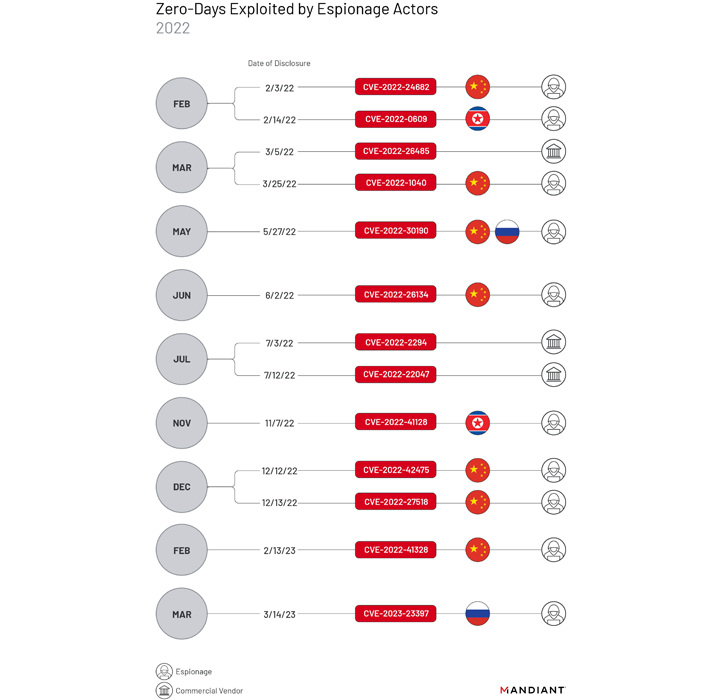
Among
state-sponsored
groups,
those
attributed
to
China
have
emerged
as
the
most
prolific,
exploiting
seven
zero-days
–
CVE-2022-24682,
CVE-2022-1040,
CVE-2022-30190,
CVE-2022-26134,
CVE-2022-42475,
CVE-2022-27518,
and
CVE-2022-41328
–
during
the
year.
Much
of
the
exploitation
has
focused
on
vulnerabilities
in
edge
network
devices
such
as
firewalls
for
obtaining
initial
access.
Various
China-nexus
clusters
have
also
been
spotted
leveraging
a
flaw
in
Microsoft
Diagnostics
Tool
(aka
Follina)
as
part
of
disparate
campaigns.
“Multiple
separate
campaigns
may
indicate
that
the
zero-day
was
distributed
to
multiple
suspected
Chinese
espionage
clusters
via
a
digital
quartermaster,”
Mandiant
said,
adding
it
points
to
the
“existence
of
a
shared
development
and
logistics
infrastructure
and
possibly
a
centralized
coordinating
entity.”
North
Korean
and
Russian
threat
actors,
on
the
other
hand,
have
been
linked
to
the
exploitation
of
two
zero-days
each.
This
includes
CVE-2022-0609,
CVE-2022-41128,
CVE-2022-30190,
and
CVE-2023-23397.
The
disclosure
comes
as
threat
actors
are
also
getting
better
at
turning
newly
disclosed
vulnerabilities
into
powerful
exploits
for
breaching
a
wide
range
of
targets
across
the
world.
“While
the
discovery
of
zero-day
vulnerabilities
is
a
resource-intensive
endeavor
and
successful
exploitation
is
not
guaranteed,
the
total
number
of
vulnerabilities
disclosed
and
exploited
has
continued
to
grow,
the
types
of
targeted
software,
including
Internet
of
Things
(IoT)
devices
and
cloud
solutions,
continue
to
evolve,
and
the
variety
of
actors
exploiting
them
has
expanded,”
Mandiant
said.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
The
Mandiant
report
also
follows
a
warning
from
Microsoft‘s
Digital
Threat
Analysis
Center
about
Russia’s
persistent
kinetic
and
cyber
targeting
as
the
war
in
Ukraine
continues
into
the
second
year.
The
tech
giant
said
since
January
2023
it
has
observed
“Russian
cyber
threat
activity
adjusting
to
boost
destructive
and
intelligence
gathering
capacity
on
Ukraine
and
its
partners’
civilian
and
military
assets.”
It
further
warned
of
a
possible
“renewed
destructive
campaign”
mounted
by
the
nation-state
group
known
as
Sandworm
(aka
Iridium)
on
organizations
located
in
Ukraine
and
elsewhere.
What’s
more,
Moscow-backed
hackers
have
deployed
at
least
two
ransomware
and
nine
wiper
families
against
over
100
Ukrainian
entities.
No
less
than
17
European
countries
have
been
targeted
in
espionage
campaigns
between
January
and
mid-February
2023,
and
74
countries
have
been
targeted
since
the
start
of
the
war.
Other
key
traits
associated
with
Russian
threat
activity
include
the
use
of
ransomware
as
weapons
of
cyber
sabotage,
gaining
initial
access
through
diverse
methods,
and
leveraging
real
and
pseudo
hacktivist
groups
to
expand
the
reach
of
Moscow’s
cyber
presence.