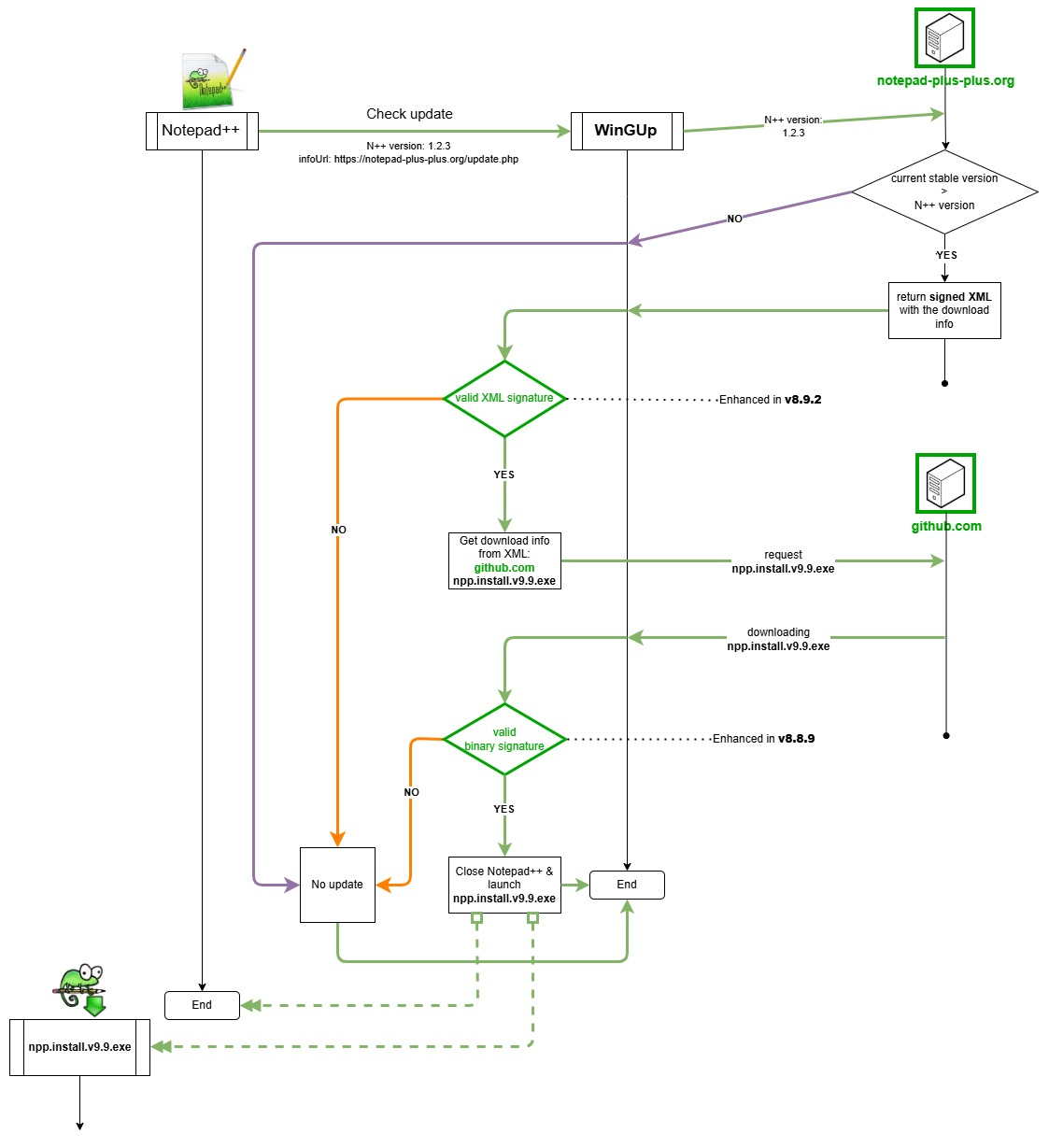
From Firewall Management to Adaptive Security: What IDC’s 2026 Report Means for Security Leaders
Last year, IDC called firewall policy management a foundation organizations could no longer ignore.
This year, the message is more direct.

Are cloud environments truly protected by NHIs?
Last year, IDC called firewall policy management a foundation organizations could no longer ignore.
This year, the message is more direct.
In its 2026 report, Building on Enforcement: Network Security Policy Management for Adaptive Security, IDC reframes the category entirely. Firewall management is no longer the focus. Instead, IDC positions Network Security Policy Management (NSPM) as the control plane that enables zero trust, continuous compliance, microsegmentation alignment, and AI-driven governance across hybrid and multicloud environments.
This isn’t a minor refresh. It’s a maturation of the market.
Policy management has moved from operational hygiene to architectural necessity.
The Category Has Evolved: Firewall Management → NSPM
The language change matters.
“Firewall management” implies rule cleanup and device configuration. “Network Security Policy Management” reflects something broader: governance across distributed enforcement layers.
IDC now frames policy as the connective layer that unifies:
Network and host controls
Hybrid and multicloud enforcement
Identity-aligned segmentation
Compliance mandates and audit readiness
Automated, risk-aware change workflows
Without strong policy governance, zero trust initiatives drift. Microsegmentation loses alignment, exceptions accumulate, and risk compounds quietly.
NSPM is no longer about managing rules. It’s about maintaining intent.
Security in an AI-Enabled Digital Enterprise
The 2026 report reflects the operational reality security leaders face today.
Organizations operate across hybrid and multicloud architectures. Attack velocity is rising. Identity exposure is expanding. Regulatory mandates are tightening. At the same time, business transformation initiatives depend on speed.
IDC forecasts global network security spending will reach $51 billion by 2029, reinforcing how central policy-driven enforcement has become to IT operations. And AI and automation remain among the least likely areas to see budget cuts.
Security leaders are being asked to do two things at once:
Reduce operational friction
Increase governance and resilience
Manual policy processes, siloed tools, and inconsistent enforcement models cannot scale under those conditions.
NSPM becomes the mechanism that allows security to move at business speed—without losing control.
Compliance Moves from Audit Exercise to Embedded Enforcement
One of the clearest shifts in the 2026 report is how IDC positions compliance.
In prior guidance, compliance was often framed as a reporting challenge. In 2026, it becomes an enforcement challenge.
In this year’s report, IDC identifies compliance with security policies and regulations as the number one cybersecurity metric. Regulatory mandates like NIS2, DORA, CIRCIA, and emerging AI governance frameworks increasingly require:
Strong segmentation
Identity assurance
Continuous validation
Provable control alignment
NSPM is positioned as the enforcement layer that operationalizes these mandates.
Continuous compliance cannot depend on spreadsheets and periodic audits. It requires real-time policy visibility, impact analysis, and validation before change.
The implication is clear: governance must be built into the control plane, not added on afterward.
Zero Trust Gets Operational
Zero trust adoption continues to grow. This year’s report shows that 69% of organizations have implemented a zero trust strategy, with another 29% planning implementation within two years.
But there’s a gap.
More than half of organizations report low to moderate confidence in their ability to apply zero trust principles across their network.
The missing piece? Continuous alignment between host-based segmentation controls and network policy enforcement.
The 2026 report emphasizes extending zero trust by integrating microsegmentation with NSPM. These initiatives require continuous synchronization between:
Host-based rules
Network paths
Asset identity
Business intent
Without that alignment, segmentation degrades over time.
Zero trust is no longer just an architectural philosophy. It requires operational policy governance in 2026 and beyond.
Context-Aware Policy Design Becomes a Differentiator
Perhaps the most important addition in the 2026 report is the focus on context-aware policy governance.
Security teams are under pressure to accelerate change while avoiding outages, misconfigurations, and compliance violations. IDC points to a new generation of capabilities designed to improve change quality upstream:
Validating change requests against asset identity and vulnerability state
Modeling topology paths before enforcement
Performing impact analysis against existing rules and regulatory requirements
Embedding least-privilege guidance during request submission
Maintaining human-in-the-loop oversight for high-risk changes
This signals a shift from reactive remediation to design-centric governance.
Automation alone is not enough. Automation governed by context—with visibility, validation, and orchestration—becomes the standard.
AI Moves from Productivity to Governance
In 2025, AI discussions focused largely on report generation and natural language interaction.
In 2026, IDC elevates AI into the governance layer.
AI-enhanced NSPM now includes:
Risk scoring across multi-vendor environments
Policy hygiene benchmarking
Predictive identification of drift
Anomaly detection across enforcement layers
Contextual validation of policy changes
This is an incredibly meaningful progression.
AI is no longer just a productivity assistant. In 2026 and beyond, it becomes a decision amplifier—helping security teams prioritize risk, maintain hygiene, and anticipate gaps before they become incidents.
As organizations accelerate AI adoption across the business, applying AI to policy governance becomes equally critical.
A Clear Maturity Path: Visibility → Governance → Automation → Resilience
The 2026 report concludes with a structured progression:
Visibility into how assets, identities, and applications connect
Governance that aligns policy intent to risk and compliance
Automation with validation and orchestration
Resilience through layered enforcement
This maturity model reinforces the broader message: adaptive security depends on governed policy control.
Firewall management was the starting point. NSPM is the evolution.
For security leaders navigating hybrid complexity, regulatory pressure, and AI-driven transformation, the shift is structural.
Policy is no longer just about enforcement. It is the control plane that makes adaptive security possible.
Read the Full IDC 2026 Report
IDC’s 2026 update makes one thing clear: Network Security Policy Management is no longer a tactical investment. It is foundational to zero trust execution, continuous compliance, AI-driven governance, and resilient hybrid operations.
If you’re evaluating how your organization aligns policy governance with zero trust, microsegmentation, and regulatory mandates, the full report provides valuable data, market insights, and practical guidance.
Download the complete IDC 2026 InfoBrief to explore the data, adoption trends, and strategic guidance shaping the future of policy-driven security.
*** This is a Security Bloggers Network syndicated blog from www.firemon.com authored by FireMon. Read the original post at: https://www.firemon.com/blog/idc-2026-nspm-adaptive-security/