Threat
actors
are
actively
exploiting
the
Fortinet
FortiNAC
vulnerability
CVE-2022-39952
a
few
hours
after
the
publication
of
the
PoC
exploit
code.
This
week,
researchers
at
Horizon3
cybersecurity
firm
have
released
a
proof-of-concept
exploit
for
a
critical-severity
vulnerability,
tracked
as CVE-2022-39952,
in Fortinet’s
FortiNAC
network
access
control
solution.
Last
week,
Fortinet
has
released
security
updates
to
address
two
critical
vulnerabilities
in
FortiNAC
and
FortiWeb
solutions.
The
two
vulnerabilities,
tracked
as CVE-2022-39952 and CVE-2021-42756,
are
respectively
an
external
control
of
file
name
or
path
in
Fortinet
FortiNAC
and
a
collection
of
stack-based
buffer
overflow
issues
in
the
proxy
daemon
of
FortiWeb.
The CVE-2022-39952 flaw
(CVSS
score
of
9.8)
is
an
external
control
of
file
name
or
path
in
the
keyUpload
scriptlet
of
FortiNAC.
The
vulnerability
was
internally
discovered
and
reported
by
Gwendal
Guégniaud
of
Fortinet
Product
Security
team.
“An
external
control
of
file
name
or
path
vulnerability
[CWE-73]in
FortiNAC
webserver
may
allow
an
unauthenticated
attacker
to
perform
arbitrary
write
on
the
system.” reads
the
advisory.
The
affected
products
are:
FortiNAC
version
9.4.0
FortiNAC
version
9.2.0
through
9.2.5
FortiNAC
version
9.1.0
through
9.1.7
FortiNAC
8.8
all
versions
FortiNAC
8.7
all
versions
FortiNAC
8.6
all
versions
FortiNAC
8.5
all
versions
FortiNAC
8.3
all
versions
The
CVE-2022-39952
vulnerability
is
fixed
in
FortiNAC
9.4.1
and
later,
9.2.6
and
later,
9.1.8
and
later,
and
7.2.0
and
later.
The
PoC
exploit
code
released
by
Horizon3
writes
a
cron
job
to
/etc/cron.d/
that
creates
a
reverse
shell
every
minute.
Unfortunately,
the
threat
actors
started
exploiting
the
Fortinet
FortiNAC
vulnerability
CVE-2022-39952
the
same
day
Horizon3
released
the
PoC
exploit.
The
nonprofit
cybersecurity
organization
Shadowserver
reported
that
attackers
started
targeting
its
honeypots
in
an
attempt
to
exploit
the
flaw.
Andrew
Morris,
the
founder
of
CEO
of
GreyNoise
Intelligence,
also
confirmed
that
his
firm
started
observing
broad
exploitation
of
the
FortiNAC
CVE-2022-39952.
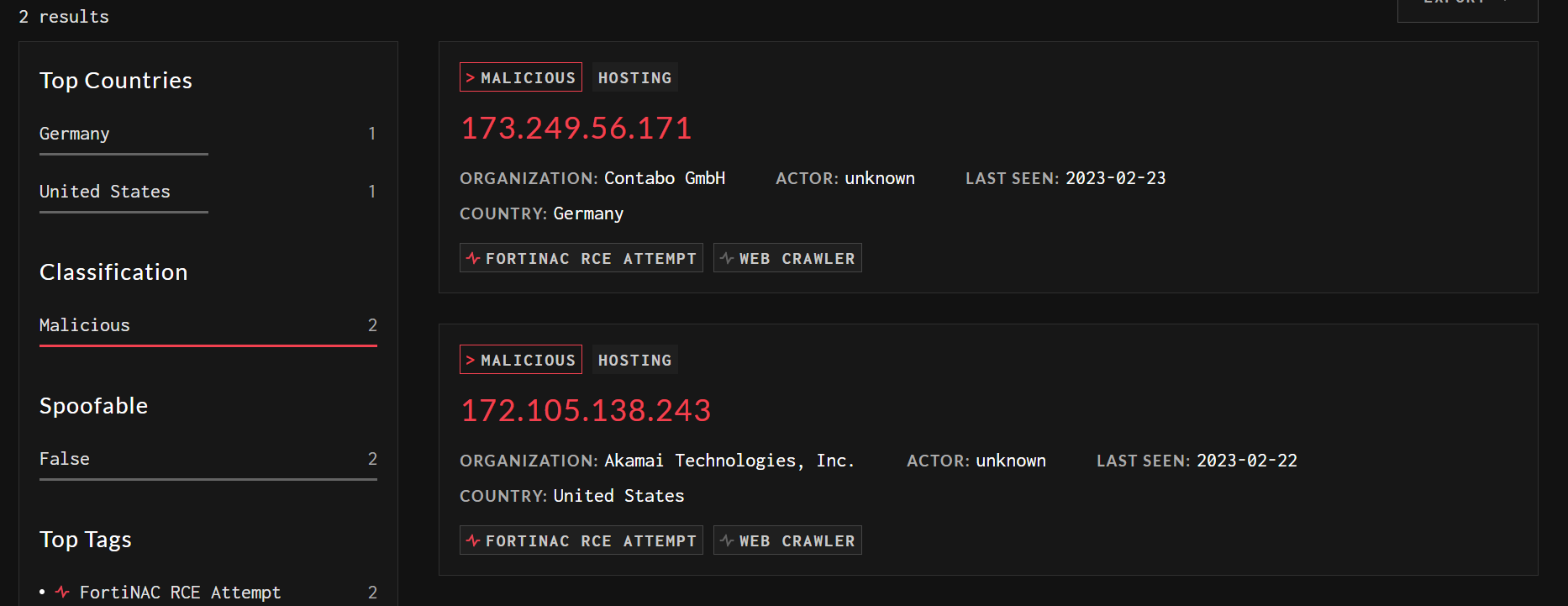
At
the
time
of
this
writing,
the
attacks
observed
by
GreyNoise
originated
from
two
IP
addressed,
respectively
in
Germany
and
the
US.
Researchers
German
Fernandez
from
CronUp
reported
that
threat
actors
have
started
with
the
mass
deployment
of
Webshells
(backdoors)
on
FortiNAC
devices
vulnerable
to
CVE-2022-39952.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Fortinet)