

weerapat1003/Adobe
Stock
Credential
security
company
Beyond
Identity
has
launched
the
Zero
Trust
Authentication
initiative
for
organizations
to
hack-proof
user
credentials,
with
backing
from
major
firms.
Zero
trust
is
a
framework
that
secures
infrastructure
and
data,
in
part
by
eliminating
arbitrary
perimeter
and
demanding
authentication
from
all
users
and
endpoints
inside
and
out.
It
includes,
therefore,
credentials.
In
an
effort
to
codify
just
how
IT
should
apply
that
in
practice,
companies
including
Zero
Scaler,
Optiv,
Palo
Alto
Networks,
Crowdstrike
and
Ping
Identity
are
supporting
an
initiative
led
by
security
firm
Beyond
Identity
to
lay
out
a
zero
trust
architecture
to
inoculate
corporate
accounts
and
credentials
against
phishing
and
ransomware,
among
other
threats.
The
company
held
a
virtual
kickoff
on
March
15,
2023
in
New
York
to
announce
the
program,
which
aims
to
address
weak
links
in
security,
passwords
and
MFA
that
can
allow
attacks
such
as
that
which
led
to
the
hacking
of
a
LastPass
engineer’s
corporate
laptop
in
2022.
SEE:
Mobile
Device
Security
Policy
(TechRepublic
Premium)
“Fundamentally,
we
are
talking
about
authentication,
but
authentication
that
rises
to
the
zero
trust
level,”
said
Patrick
McBride,
chief
marketing
officer
at
Beyond
Identity.
“Because
so
many
auth
protocols
out
there
are
easily
bypassed
—
not
even
a
speed
bump.”
Jump
to:
Passwordless,
phishing
free
protocols
among
ZTA
measures
The
company
laid
out
a
set
of
measures
organizations
can
implement
to
bolster
defenses
and
insulate
endpoints
from
lateral
movement:
-
Passwordless
–
No
use
of
passwords
or
other
shared
secrets,
as
these
can
easily
be
obtained
from
users,
captured
on
networks,
or
hacked
from
databases. -
Phishing
resistant
–
No
opportunity
to
obtain
codes,
magic
links,
or
other
authentication
factors
through
phishing,
adversary-in-the-middle,
or
other
attacks. -
Capable
of
validating
user
devices
–
Able
to
ensure
that
requesting
devices
are
bound
to
a
user
and
authorized
to
access
information
assets
and
applications. -
Capable
of
assessing
device
security
posture
–
Able
to
determine
whether
devices
comply
with
security
policies
by
checking
that
appropriate
security
settings
are
enabled,
and
security
software
is
actively
running. -
Capable
of
analyzing
many
types
of
risk
signals
–
Able
to
ingest
and
analyze
data
from
endpoints
and
security
and
IT
management
tools. -
Continuous
risk
assessment
–
Able
to
evaluate
risk
throughout
a
session
rather
than
relying
on
one-time
authentication. -
Integrated
with
the
security
infrastructure
–
Integrating
with
a
variety
of
tools
in
the
security
infrastructure
to
improve
risk
detection,
accelerate
responses
to
suspicious
behaviors,
and
improve
audit
and
compliance
reporting.
How
to
achieve
high
security
credentials
McBride
said
that
to
establish
high
trust
in
the
user
identity,
a
passwordless,
phishing
resistant
MFA
is
critical,
e.g.,
a
FIDO2
passkey:
a
FIDO2
passkey.
Based
on
FIDO
authentication
standards
and
using
asymmetric
public/private
pairs,
FIDO2
login
credentials
are
unique
for
each
web
site,
and,
like
biometric
passkeys,
never
leave
a
user’s
device
and
are
never
stored
on
a
server “That
also
gives
phishing
resistance.
I’m
not
sending
anything
over
the
network
that
is
usable
by
a
bad
guy,”
McBride
added
(Figure
A).
Figure
A
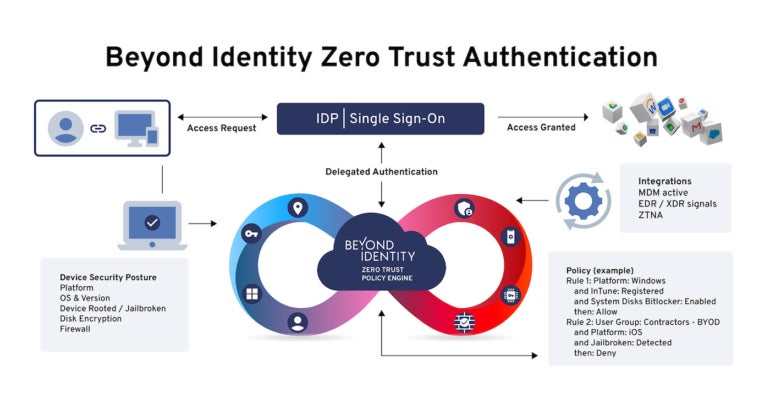
Beyond
Identity.
Continuous
look
of
Beyond
Identity
‘policy
engine’
Chris
Cummings,
VP
product
and
solutions
at
Beyond
Identity
explained
that
continuous
monitoring
is
critical
to
security.
He
said
Beyond
Identity’s
policy
engine
takes
signals
in
and
sends
instructions
out
either
to
authenticate
or
not
authenticate
to
the
single
sign-on
Okta,
or
to
take
action
on
a
specific
device
(for
example,
quarantine
it
until
the
user
or
IT
can
inspect
it).
“That
notion
of
continuity
stems
from
Palo
Alto
Networks,”
he
said.
“They
really
emphasize
continuous
and
the
reason
why
they
work
with
us
is
because
we
provide
continuous
verification
—
one
of
the
seven
elements
of
Zero
Trust
Authentication
—
and
they
do
that
for
application
access.
A
key
aspect
of
implementation
is
ease
of
use
—
removing
time-consuming
tasks
for
the
valid
endpoint
device
user,
noted
McBride.
He
explained
end
users
want
to
be
able
to
access
their
devices
quickly,
and
that
forcing
users
though
cumbersome,
high-friction
security
methods
often
prompts
users
to
switch
them
off
entirely.
“We
think
you
can
have
your
cake
and
eat
it
too:
High
security
with
low
friction,”
said
McBride.
Moving
beyond
passwords
and
MFA
According
to
McBride,
the
ZTA
principles
will
help
organizations
move
beyond
the
limitations
of
passwords
and
multi-factor
authentication.
“Auth
methods
aren’t
working.
Passwords
are
fundamentally
flawed,
so
if
you
store
them
or
transit
over
networks
they
get
stolen,
and
every
75%
to
80%
of
initial
access
comes
from
these
issues,”
he
said.
The
ZTA
protocols
include
risk
scoring
and
what
the
company
refers
to
as
continuous
authentication
capabilities
—
authentication
decisions
that
are
risk
based
and
updated,
based
on
data
from
cybersecurity
tools
for
an
‘always-on’
zero
trust
world,
per
the
company.
SEE:
1Password
is
looking
to
a
password-free
future.
Here’s
why
(TechRepublic)
Threats
in
the
wild:
Multiple
attack
vectors
through
valid
accounts
The
Mitre
ATT&K
framework
keeps
a
log
of
cyber
threat
actors
and
techniques.
Among
them
are
17
credential
access
techniques
used
to
obtain
and
abuse
credentials
of
existing
accounts
to
gain
access,
persist
within
a
system,
escalate
privilege
and
so
on.
The
organization
notes
that
credentials
can
even
be
used
to
access
remote
systems
and
external
services
including
VPNs,
Outlook
Web
Access,
network
devices,
and
remote
desktops.
A
brief
sample
of
the
more
than
40
threat
groups
that
Mitre
reports
have
exploited
valid
accounts
over
the
past
decade
and
a
half
includes:
-
APT18:
Leverages
legitimate
credentials
to
log
into
external
remote
services
to
target
technology,
manufacturing,
human
rights
groups,
government
and
medical
industries. -
Axiom:
Suspected
Chinese
cyber
espionage
group
that
used
previously
compromised
administrative
accounts
to
escalate
privileges. -
Spider
Wizard:
a
Russia
state
actor
using
valid
credentials
for
privileged
accounts
with
the
goal
of
accessing
domain
controllers. -
Polonium:
A
Lebanon-based
group
has
primarily
targeted
Israeli
organizations,
including
critical
manufacturing,
information
technology,
and
defense
industry
companies
using
valid
compromised
credentials.
“For
attackers,
the
initial
vector
of
choice
is
valid
accounts,”
said
McBride.
“Sophisticated
actors
use
this
all
the
time
and
there
is
an
arms
length
list
of
bad
actors
using
them,
and
they
use
them
because
they
constitute
the
‘easy
button.’
They
don’t
want
to
burn
a
zero
day,
or
use
a
really
sophisticated
method
if
there’s
an
easy
button
to
use.”
He
added
that
phishing,
contrary
to
popular
opinion,
is
the
second
most
common
way
to
deploy
ransomware.
Number
one
is
logging
in
using
stolen
credentials
to
gain
remote
access
to
software,
desktop
or
servers.
“Weak
authentication
has
real
world
consequences,”
he
said.
“Year
after
year,
identity
and
authentication
vulnerabilities
remain
the
single
largest
source
of
ransomware
and
security
breaches,
so
something
has
to
fundamentally
change
to
close
this
vulnerability
and
enable
organizations
to
meet
the
security
mandates
issued
by
the
White
House,
NIST
and
CISA,”
said
Chase
Cunningham,
chief
strategy
officer
at
Ericom
Software,
who
is
backing
the
initiative,
in
a
statement.
Jay
Bretzmann,
research
VP
at
IDC,
added:
“Delivering
continuous
verification
of
identity
—
user
and
devices
—
is
essential
to
meeting
the
promise
of
zero
trust..
Beyond
Identity
has
taken
the
approach
to
utilize
signals
from
security
infrastructure
in
near
real-time
to
raise
the
security
standard
and
capitalize
on
existing
security
infrastructure
investments
in
EDR
and
SASE
tools.”











