Tax-paying individuals in Mexico and Chile have been targeted by a Mexico-based cybercrime group that goes by the name Fenix to breach targeted networks and steal valuable data.
A key hallmark of the operation entails cloning official portals of the Servicio de Administración Tributaria (SAT) in Mexico and the Servicio de Impuestos Internos (SII) in Chile and redirecting potential victims to those sites.
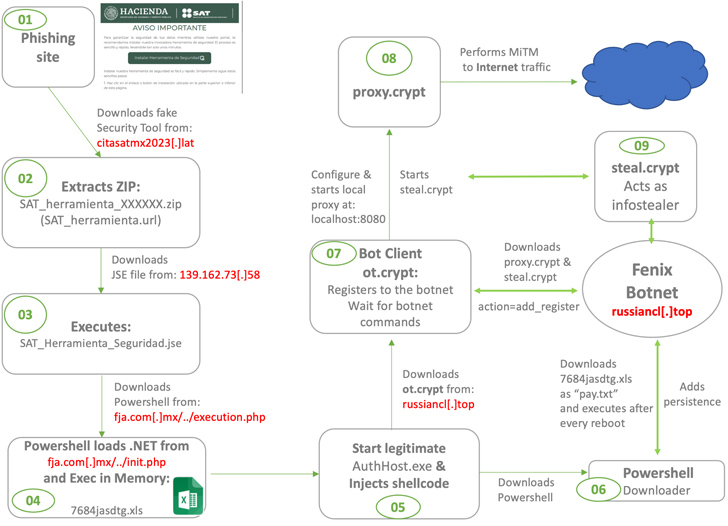
“These fake websites prompt users to download a supposed security tool, claiming it will enhance their portal navigation safety,” Metabase Q security researchers Gerardo Corona and Julio Vidal said in a recent analysis.
“However, unbeknownst to the victims, this download actually installs the initial stage of malware, ultimately enabling the theft of sensitive information such as credentials.”
The goal of Fenix, according to the Latin America-focused cybersecurity firm, is to act as an initial access broker and get a foothold into different companies in the region, and sell the access to ransomware affiliates for further monetization.
Evidence gathered so far points to the threat actor orchestrating phishing campaigns coinciding with government activities during the year since at least the fourth quarter of 2022.
The mechanics of the campaign proceeds thus: Visitors landing on the impersonated websites are urged to download software that supposedly safeguards their data while browsing the portal. Alternatively, users are lured via phishing sites set up to download legitimate apps like AnyDesk.
“[Fenix] compromises weak websites using vulnerable WordPress engines and also creates new domains to launch phishing campaigns,” the researchers said, adding the group “creates typosquatting domains similar to known apps like AnyDesk, WhatsApp, etc.”
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
But in reality, the ZIP file containing the purported software is used as a springboard to activate an infection sequence that leads to the execution of an obfuscated PowerShell script, which, in turn, loads and runs a .NET binary, after which the message “Ahora se encuentra protegido” (meaning “Now you are protected” in Spanish) is displayed to keep up the ruse.
The .NET executable subsequently paves the way for establishing persistence on the compromised host and deploying a botnet malware that’s capable of running commands received from a remote server, loading a stealer module that exfiltrates credentials stored in web browsers and crypto wallets, and ultimately deleting itself.
“We are seeing new malicious groups being created in LATAM to provide initial access to ransomware gangs,” the researchers concluded. “These local actors are not amateur and will increase their technical expertise and therefore more difficult to track, detect and eradicate, it is important to anticipate their actions.”