FakeCalls Vishing Malware Targets South Korean Users via Popular Financial Apps

An
Android
voice
phishing
(aka
vishing)
malware
campaign
known
as
FakeCalls
has
reared
its
head
once
again
to
target
South
Korean
users
under
the
guise
of
over
20
popular
financial
apps.
“FakeCalls
malware
possesses
the
functionality
of
a
Swiss
army
knife,
able
not
only
to
conduct
its
primary
aim
but
also
to
extract
private
data
from
the
victim’s
device,”
cybersecurity
firm
Check
Point
said.
FakeCalls
was
previously
documented
by
Kaspersky
in
April
2022,
describing
the
malware’s
capabilities
to
imitate
phone
conversations
with
a
bank
customer
support
agent.
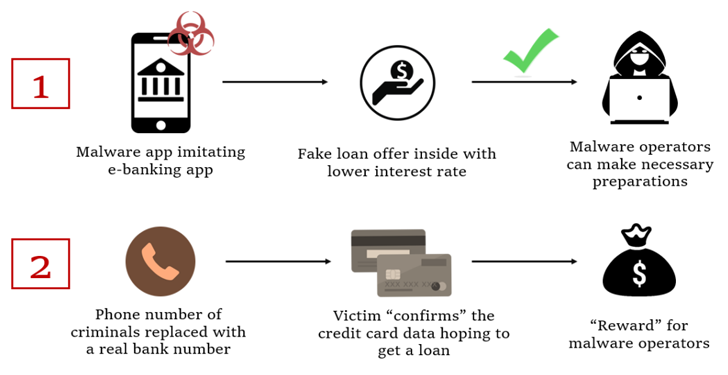
In
the
observed
attacks,
users
who
install
the
rogue
banking
app
are
enticed
into
calling
the
financial
institution
by
offering
a
fake
low-interest
loan.
At
the
point
where
the
phone
call
actually
happens,
a
pre-recorded
audio
with
instructions
from
the
real
bank
is
played.
At
the
same
time,
malware
also
conceals
the
phone
number
with
the
bank’s
real
number
to
give
the
impression
that
a
conversation
is
happening
with
an
actual
bank
employee
on
the
other
end.
The
ultimate
goal
of
the
campaign
to
get
the
victim’s
credit
card
information,
which
the
threat
actors
claim
is
required
to
qualify
for
the
non-existent
loan.
The
malicious
app
also
requests
for
intrusive
permissions
so
as
to
harvest
sensitive
data,
including
live
audio
and
video
streams,
from
the
compromised
device,
which
are
then
exfiltrated
to
a
remote
server.
The
latest
FakeCalls
samples
further
implement
various
techniques
to
stay
under
the
radar.
One
of
the
methods
involves
adding
a
large
number
of
files
inside
nested
directories
to
the
APK’s
asset
folder,
causing
the
length
of
the
file
name
and
path
to
breach
the
300-character
limit.
“The
malware
developers
took
special
care
with
the
technical
aspects
of
their
creation
as
well
as
implementing
several
unique
and
effective
anti-analysis
techniques,”
Check
Point
said.
“In
addition,
they
devised
mechanisms
for
disguised
resolution
of
the
command-and-control
servers
behind
the
operations.”
While
the
attack
exclusively
focuses
on
South
Korea,
the
cybersecurity
company
has
warned
that
the
same
tactics
can
be
repurposed
to
target
other
regions
across
the
world.
The
findings
also
come
as
Cyble
shed
light
on
two
Android
banking
trojans
dubbed
Nexus
and
GoatRAT
that
can
harvest
valuable
data
and
carry
out
financial
fraud.
Nexus,
a
rebranded
version
of
SOVA,
also
incorporates
a
ransomware
module
that
encrypts
the
stored
files
and
can
abuse
Android’s
accessibility
services
to
extract
seed
phrases
from
cryptocurrency
wallets.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
In
contrast,
GoatRAT
is
designed
to
target
Brazilian
banks
and
joins
the
likes
of
BrasDex
and
PixPirate
to
commit
fraudulent
money
transfer
over
the
PIX
payments
platform
while
displaying
a
fake
overlay
window
to
hide
the
activity.
The
development
is
part
of
a
growing
trend
where
threat
actors
have
unleashed
increasingly
sophisticated
banking
malware
to
automate
the
whole
process
of
unauthorized
money
transfers
on
infected
devices.
Cybersecurity
company
Kaspersky
said
it
detected
196,476
new
mobile
banking
trojans
and
10,543
new
mobile
ransomware
trojans
in
2022,
with
China,
Syria,
Iran,
Yemen,
and
Iraq
emerging
as
the
top
countries
attacked
by
mobile
malware,
including
adware.
Spain,
Saudi
Arabia,
Australia,
Turkey,
China,
Switzerland,
Japan,
Colombia,
Italy,
and
India
lead
the
list
of
top
countries
infected
by
mobile
financial
threats.
“Despite
the
decline
in
overall
malware
installers,
the
continued
growth
of
mobile
banking
Trojans
is
a
clear
indication
that
cybercriminals
are
focusing
on
financial
gain,”
Kaspersky
researcher
Tatyana
Shishkova
said.