North
Korea-linked
APT Kimsuky has
been
linked
to
a
social
engineering
campaign
aimed
at
experts
in
North
Korean
affairs.
SentinelLabs
researchers
uncovered
a
social
engineering
campaign
by
the
North
Korea-linked
APT
group
Kimsuky
that
is
targeting
experts
in
North
Korean
affairs.
The
attacks
are
part
of
a
broader
campaign
recently
detailed
in
a
joint
advisory
published
by
US
intelligence.
The
campaign
has
the
objective
of
stealing
Google
and
subscription
credentials
of
a
reputable
news
and
analysis
service
focusing
on
North
Korea,
as
well
as
delivering
reconnaissance
malware.
Kimsuky cyberespionage
group (aka
ARCHIPELAGO,
Black
Banshee, Thallium,
Velvet
Chollima, APT43)
was
first spotted by
Kaspersky
researcher
in
2013.
At
the
end
of
October
2020,
the US-CERT
published
a
report
on
Kimusky’s
recent
activities that
provided
information
on
their
TTPs
and
infrastructure.
The
APT
group
mainly
targets
think
tanks
and
organizations
in
South
Korea,
other
victims
were
in
the
United
States,
Europe,
and
Russia.
In
the
latest
Kimsuky
campaign,
the
state-sponsored
group
focused
on
nuclear
agendas
between
China
and
North
Korea,
relevant
to
the
ongoing
war
between
Russia
and
Ukraine.
Threat
actors
engage
in
extensive
email
correspondence
with
the
victims
and
use
spoofed
URLs,
websites
mimicking
legitimate
web
platforms,
and
weaponized
documents.
The
attackers
were
spotted
delivering
the
recently
discovered
reconnaissance
tool
ReconShark
malware.
The
campaign
focuses
on
the
theft
of
email
credentials
and
NK
News
subscription
credentials.
SentinelLabs
attributes
the
campaign
to
Kimsuky
based
on
the
type
of
malware
used,
the
attack
infrastructure,
and
TTPs.
“A
hallmark
of
the
activity
we
discuss
in
this
post
is
Kimsuky’s
focus
on
establishing
initial
contact
and
developing
a
rapport
with
their
targets
prior
to
initiating
malicious
activities.
As
part
of
their
initial
contact
strategy,
the
group
impersonated
Chad
O’Carroll,
the
founder
of
NK
News
and
the
associated
holding
company
Korea
Risk
Group,
using
an
attacker-created
domain,
nknews[.]pro,
which
closely
resembles
the
legitimate
NK
News
domain
nknews.org.”
reads
the
report
published
by
SentinelOne
“The
initial
email
requests
the
review
of
a
draft
article
analyzing
the
nuclear
threat
posed
by
North
Korea.”
The
researchers
observed
Kimsuky
sending
an
HTML-formatted
spear
phishing
message
which
requests
them
to
review
a
draft
analysis
of
the
nuclear
threat
posed
by
North
Korea.
The
email
is
crafted
to
stimulate
a
subsequent
conversation
with
the
recipient,
it
impersonates
NK
News
leadership
and
lacks
any
malicious
artifacts.

Upon
engaging
the
target
in
the
conversation,
the
APT
group
eventually
follows
up
with
an
email
that
contains
an
URL
to
a
Google
document.
In
case
the
recipient
is
not
responsive,
the
nation-state
actors
follow
up
with
a
reminder
email
in
an
attempt
to
engage
the
target
in
conversation.
The
attackers
spoofed
the
URL’s
destination
by
setting
the
href HTML
property to
direct
to
a
website
under
the
control
of
the
attackers.
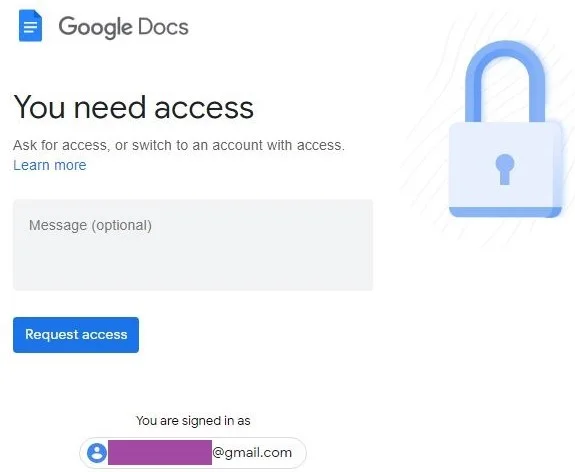
The
displayed
URL
points
to
a
document
hosted
on
Google
Docs,
delving
into
the
topic
of
the
North
Korean
nuclear
threat.
The
article
contains
visible
edits
to
give
the
impression
of
a
genuine
draft
article.
The
spoofed
destination
of
the
URL
redirects
the
victim
to
a
Kimsuky’s
website
that
masquerades
as
a
legitimate
Google
Docs
site
for
requesting
document
access,
such
as
https[://]drive-google[.]shanumedia[.]com/pdf/ul/ji78fghJHKtgfLKJIO/s2.php?menu=ZGFu[...]vbQ==
The
URL
includes
a
Base-64
encoded
segment
that
is
the
value
of
the
menu URL
query
parameter,
which
resolves
to
the
victim’s
email
address.
The
email
address
is
displayed
in
the
fake
login
page
to
trick
the
visitor
into
thinking
that
is
is
a
legitimate
page
of
access
request.
The
researchers
also
observed
threat
actors
distributing
password-protected
weaponized
Office
documents
during
conversations
with
the
victims.
The
archive
was
used
to
deploy
the
ReconShark
reconnaissance
tool.
“SentinelLabs
remains
actively
engaged
in
monitoring
the
activities
conducted
by
Kimsuky.
The
findings
presented
in
this
post
highlight
the
group’s
persistent
commitment
to
targeted
social
engineering
attacks
and
underscore
the
need
for
increased
awareness
and
understanding
of
Kimsuky’s
tactics
among
potential
targets.”
concludes
the
report.
“Maintaining
vigilance
and
implementing
effective
security
measures
are
imperative
to
mitigate
the
risks
posed
by
this
persistent
threat
actor.”
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Kimsuky)







