Exclusive Scarlet Royal Assignment: Intel discover various sets of Chinese government-sponsored actions against Southeast Asian officials

In the month of May 2023, during an intense search within the operations data of Sophos Managed Detection and Response, Mark Parsons from Sophos MDR unearthed a sophisticated, ongoing cyber-espionage operation backed by the Chinese government, known as “Scarlet Royal.” This operation was directed towards a prominent governmental institution in Southeast Asia.
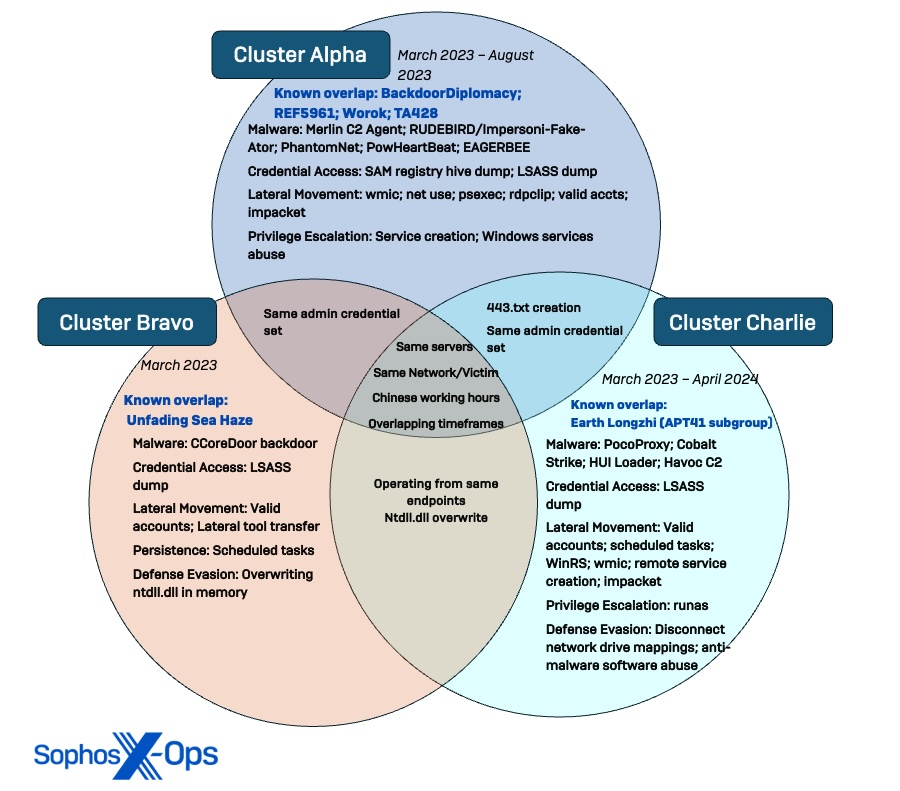
The search was initiated following the detection of a DLL sideloading tactic that manipulated VMNat.exe, a VMware element. During the subsequent inquiry, we traced a minimum of three clusters engaged in intrusive activities spanning from March 2023 to December 2023. Additionally, the investigation revealed previously undisclosed malware connected to these threat clusters, along with an upgraded version of the previously mentioned EAGERBEE malware. Following our internal categorization protocol, Sophos identified these clusters as Cluster Alpha (STAC1248), Cluster Bravo (STAC1807), and Cluster Charlie (STAC1305).
Although our insight into the targeted network was restricted due to the extensive implementation of Sophos endpoint protection within the organization, our inquiries uncovered indications of earlier intrusion activities dating back to the beginning of 2022. This raised suspicions about the long-term access the threat actors had to unmanaged resources within the network.
The identified clusters were observed utilizing tools and infrastructure that interconnect with public disclosures by other researchers regarding Chinese threat actors such as BackdoorDiplomacy, REF5961, Worok, TA428, the recently-designated Unfading Sea Haze, and the APT41 subgroup Earth Longzhi. Additionally, Sophos MDR reported the actors trying to obtain documents labeled with names suggesting their intelligence value, including military documents related to strategies in the South China Sea.
Following our investigation, Sophos confidently affirms that the primary objective behind this campaign was to secure ongoing access to the targeted network for cyber-espionage in service of Chinese state objectives. This encompassed breaching critical IT systems, conducting surveillance on specific users, gathering sensitive military and technical details, and deploying various malware implants for command-and-control (C2) communications. We reasonably suspect that these clusters of activities were part of a well-coordinated campaign directed by a singular entity. Sophos is divulging indicators and details of the Crimson Palace campaign to aid in potential public research and assist other defenders and analysts in disrupting associated operations.
Sophos has conveyed the intrusion details to authorized contacts within the targeted entity on multiple occasions. Sophos MDR continues to closely monitor the environment to provide updates on the scope and scale of ongoing activities to the victimized organization, as well as gather intelligence to track attack strategies and develop enhanced detections for all Sophos clients. Intelligence from this campaign has also been shared with governmental and industry partners, including Elastic Security and Trend Micro, who have previously noted similar threats.
The key discoveries of our investigation included:
- Innovative malware variations: Sophos identified the use of newly discovered malware named CCoreDoor (also identified by BitDefender) and PocoProxy, alongside an updated version of the EAGERBEE malware with fresh capabilities to block communications to anti-virus (AV) provider domains within the targeted organization’s network. Other observed malware variants comprise NUPAKAGE, Merlin C2 Agent, Cobalt Strike, PhantomNet backdoor, RUDEBIRD malware, and the PowHeartBeat backdoor.
- Extensive exploitation of dynamic link libraries (DLL) through Windows and anti-virus executables: The Scarlet Royal operation encompassed over 15 unique DLL sideloading scenarios, most of which exploited Windows Services, authentic Microsoft executables, and AV provider applications.
- Prioritization of evasive strategies and tools: The threat actors employed various new evasion methods, such as manipulating ntdll.dll in memory to detach the Sophos AV agent process from the kernel, misusing AV software for sideloading, and testing different techniques to determine the most effective and elusive ways to execute their payloads.
- Three discrete clusters with indications of coordination: While Sophos identified three distinguishable behavioral patterns, the synchronization of operations and overlaps in compromised infrastructure and objectives suggest a level of synchronization or coordination among the clusters within the operational environment.
Due to the vast amount of intelligence collected during our exploration of this campaign, we have split our report into two parts. This article presents a summary of the campaign and highlights the overlap among the observed activity clusters alongside the unique malware associated with them. A complete technical analysis of the activity clusters can be found in a technical appendix, also released concurrently. Links to relevant sections of the detailed analysis are provided within this article to guide readers to further details in that specific article.
Previous Breach
The targeted organization is classified by Sophos as a “hybrid estate,” indicating that only a segment of the organization has deployed Sophos Managed Detection and Response (MDR) and Extended Detection and Response (XDR) coverage.
of access points. Due to this, the Sophos team is lacking a comprehensive view of all assets within the environment, which leads to the evaluation that the extent of the compromise likely reaches beyond Sophos-protected endpoints and servers.
Initial entry occurred outside of Sophos’ visibility into the organization, however, subsequent related activities dating back to early 2022 were observed. Among these were the detection of NUPAKAGE malware (Troj/Steal-BLP), a tailored tool utilized for exfiltration that has been publicly linked by Trend Micro to the Chinese threat group Earth Preta (also known as Mustang Panda).
The organization later registered a subset of their access points with Sophos’ MDR service. Discovery of suspicious activities prompted the MDR Operations team to examine the organization’s domain. This included an investigation in December 2022 into intrusion activities where DLL-stitching was employed to obscure and implement two malicious backdoors on target domain controllers. During this period, the detections of Troj/Backdr-NX and ATK/Stowaway-C were extended across Sophos customers to identify the stitched DLL payloads, and a behavioral detection mechanism was devised to discover the addition of a service DLL to the Windows registry.
Further examination into these prior compromises can be found here.
Assessment of Activity Clusters
The investigation that pinpointed the activity clusters outlined in this report commenced in May 2023. During the investigation, Sophos analysts identified several trends indicating distinct patterns of behavior were active within the network simultaneously during the same timeframe. These patterns included:
- Validation data, such as originating subnet, workstation name, and account utilization
- Strategies, including specific instructions and choices frequently employed by the attackers
- Attacker C2 infrastructure
- Unique utilities and the locations they were deployed
- Targeted user accounts and devices
- Timing of the observed behaviors
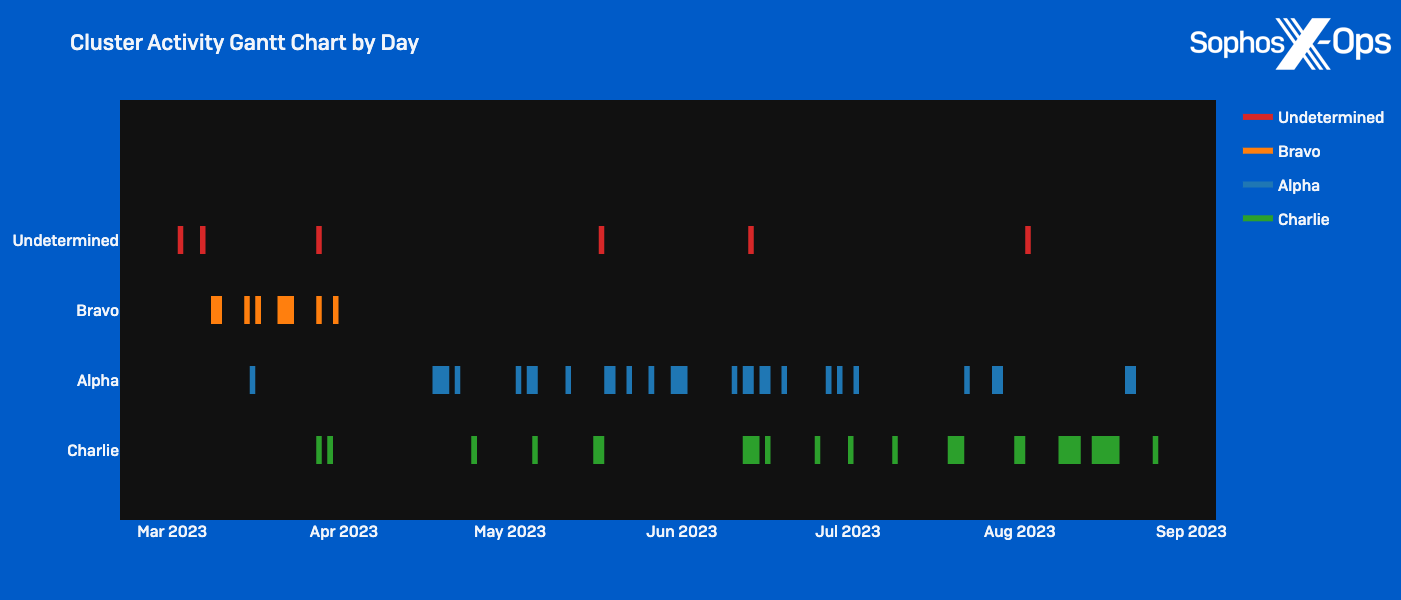
Based on these patterns, we determine with reasonable confidence that the espionage campaign comprised at least three activity clusters with distinct sets of infrastructure and TTPs operating in the organization’s network from at least March to September 2023.
For further details on the attack sequences of the observed clusters and specifics on the innovative strategies and tools, please refer to the attack chain details report.
Alpha Cluster (STAC1248)
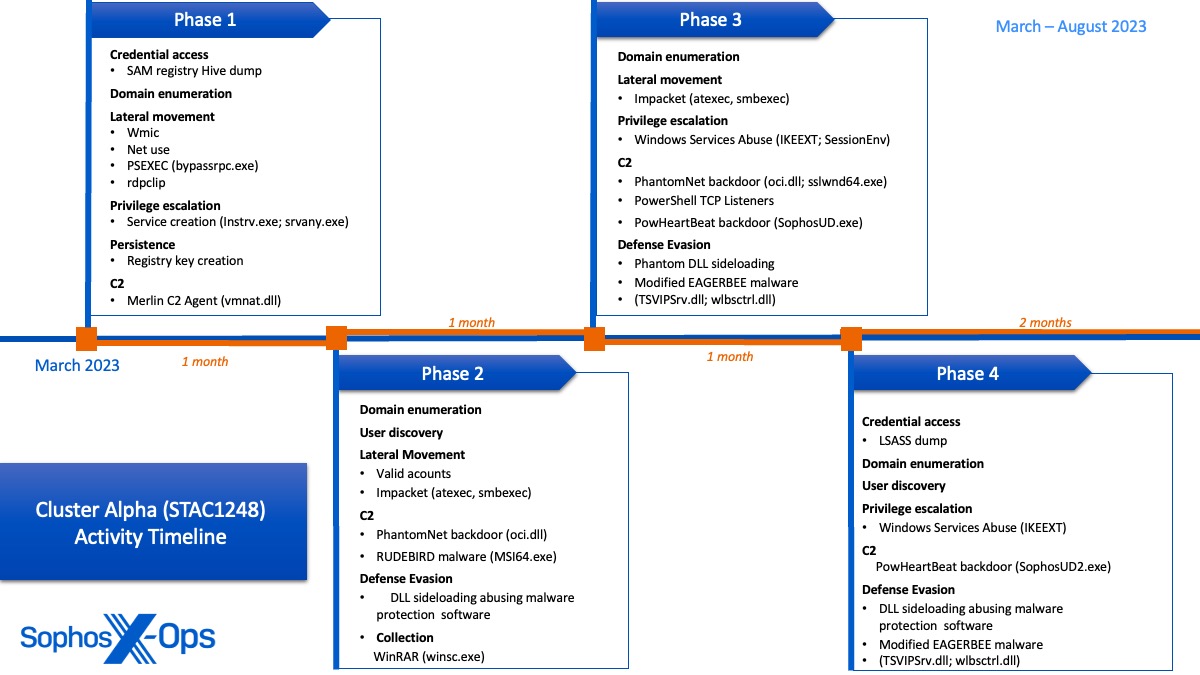
We noticed Alpha Cluster activities from early March to at least August 2023. These activities included multiple attempts at sideloading to deploy various malware and establish persistent C2 connections within client and server subnets. Throughout these activities, we observed modifications of successful methods that led to the same results, indicating that the threat actors may have been utilizing the victim network as a testing ground to experiment with different techniques. In addition to leveraging unique methods to disable AV protections and escalate privileges, the actor in Alpha Cluster emphasized thoroughly mapping server subnets, enumerating administrator accounts, and conducting reconnaissance on Active Directory infrastructure.
Key insights
- Rollout of new EAGERBEE malware variations with enhanced capability to alter packets to disrupt security agent network communications
- Utilization of multiple persistent C2 connections including Merlin Agent, PhantomNet backdoor, RUDEBIRD malware, EAGERBEE malware, and PowHeartBeat backdoor
- Employment of uncommon LOLBins instsrv.exe and srvany.exe for service persistence with elevated SYSTEM privileges
- Sideloading of eight distinct DLLs exploiting Windows Services, legitimate Microsoft binaries, and software from endpoint protection vendors
Additional examination of Alpha Cluster can be found here.
Bravo Cluster (STAC1807)
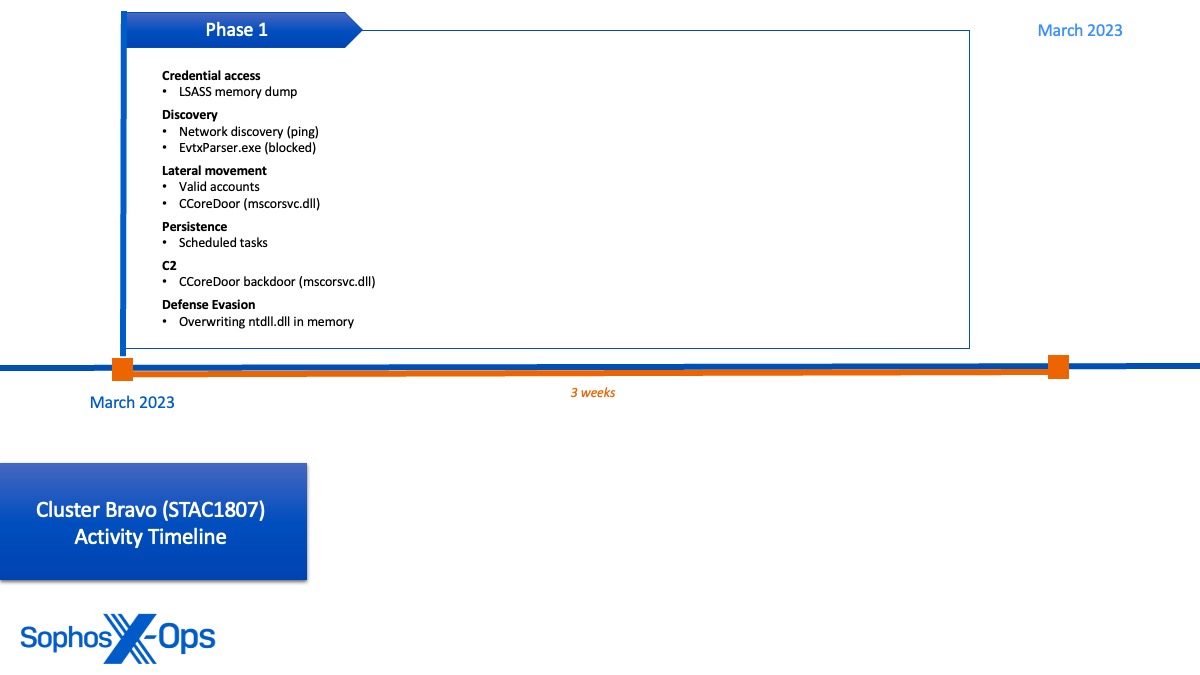
Contrary to the activities in the other two clusters that spanned several months, the activities in Bravo Cluster were only noted within the targeted organization’s environment for a three-week period in March 2023 (coinciding with the first session of China’s 14th National People’s Congress). Identified as a mini cluster due to its brief duration, Bravo Cluster activities focused primarily on utilizing valid accounts to spread across the network laterally, with the objective of sideloading a novel backdoor for establishing C2 connections and sustaining persistence on target servers.
Key behaviors observed included:
- Deployment of a backdoor (referred to as CCoreDoor by us, and classified as EtherealGh0st by BitDefender) to move laterally, establish external C2 connections, perform reconnaissance, and extract credentials (also simultaneously detected by BitDefender)
- Use of renamed versions of a signed an authorized side-loadable binary (mscorsvw.exe) to mask backdoor deployment and traverse from the initial host to other remote servers
- Establishment of connections with other hosts verified to be operational within other government organizations in the country, which also could potentially be compromised
- Replacement of ntdll.dll in memory with an on-disk version to disconnect the Sophos endpoint protection agent process from the kernel
For more in-depth information regarding Cluster Bravo, you can refer to this source.
Cluster Charlie (STAC1305)
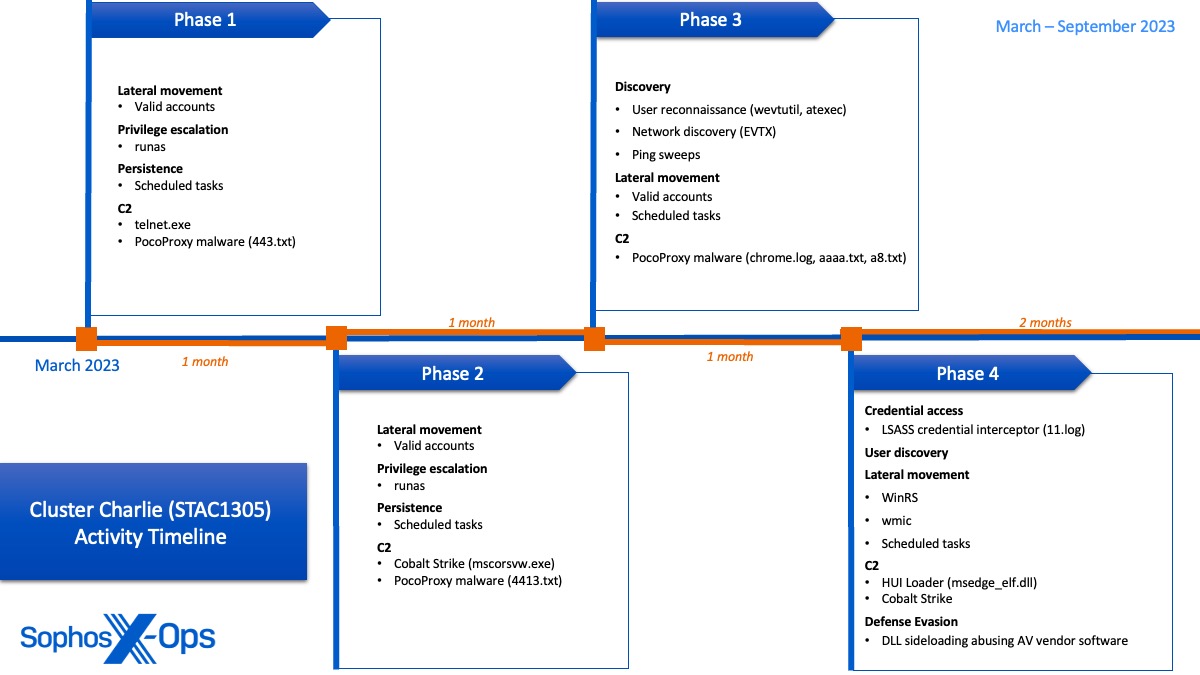
The hunter team from Sophos MDR detected activities linked to Cluster Charlie within the target network for an extended duration, ranging from March to at minimum April 2024. Emphasizing access management, the perpetrator deployed multiple incarnations of a previously unidentified malware, named PocoProxy, to establish continuity on target systems and switch to fresh external C2 infrastructure.
On a day in June 2023, the level of activity within Cluster Charlie escalated as the actors engaged in some of their most noticeable explorations, including extensive scrutiny of Event Logs for comprehensive user and network reconnaissance. The results of this reconnaissance were utilized to initiate automated scans across the network, with the probable objective of charting all users and endpoints within that network. Intriguingly, this day corresponded with a holiday in the respective country of the targeted organization, insinuating that the threat actor strategically saved their most conspicuous actions for a day with reduced anticipated responsiveness. Subsequent to ongoing discovery and lateral movement endeavors over subsequent months, Cluster Charlie’s activity was subsequently observed striving to transmit confidential data, which based on the nature of the files and data amassed, we evaluate with a high degree of assurance was for espionage motives.
Noteworthy observed actions included:
- Rollout of multiple instances of a previously unreported malware (identified as PocoProxy) for consistent C2 interactions
- Compilation and transmission of an extensive array of data, encompassing sensitive military and political records, infrastructure architecture data, and access credentials/tokens for further profound access
- Installation of a custom malware loader dubbed HUI loader to infuse a Cobalt Strike Beacon into mstsc.exe, an action thwarted by Sophos HMPA safeguards
- Insertion of an LSASS logon credential interceptor into svchost.exe to capture credentials on domain controllers
- Execution of wevtutil commands for specified user reconnaissance, utilizing the findings to initiate automated ping scans targeting a multitude of destinations across the network
For further insights on Cluster Charlie, you may visit this link: Source.
Attribution and Cluster Intersection
Established on the blend of victimology, chronological analysis, infrastructure, tool implementation, and achievements on targets, we confidently conclude the monitored activity clusters are linked to operations sponsored by the Chinese state.
In addition to the synchronization of operational timings within the clusters with standard Chinese working hours, various observed Tactics, Techniques, and Procedures (TTPs) align with industry documentation on actors associated with China. Furthermore, the target network is a prominent government entity within a Southeast Asian nation characterized by recurring disputes with China over South China Sea territories. The primary objective of this campaign, as we assess, is prolonged espionage, demonstrable through the establishment of redundant C2 pathways by the three clusters across the network to guarantee consistent access and acquire data pertinent to Chinese state concerns.
Consistent Work Hours of Chinese Origin
Per our scrutiny of activity frequencies, operations across the clusters predominantly took place between 00:00 and 09:00 Coordinated Universal Time (UTC) from Monday to Friday, correlating to the standard practice of Chinese work hours from 8am to 5pm China Standard Time (CST).
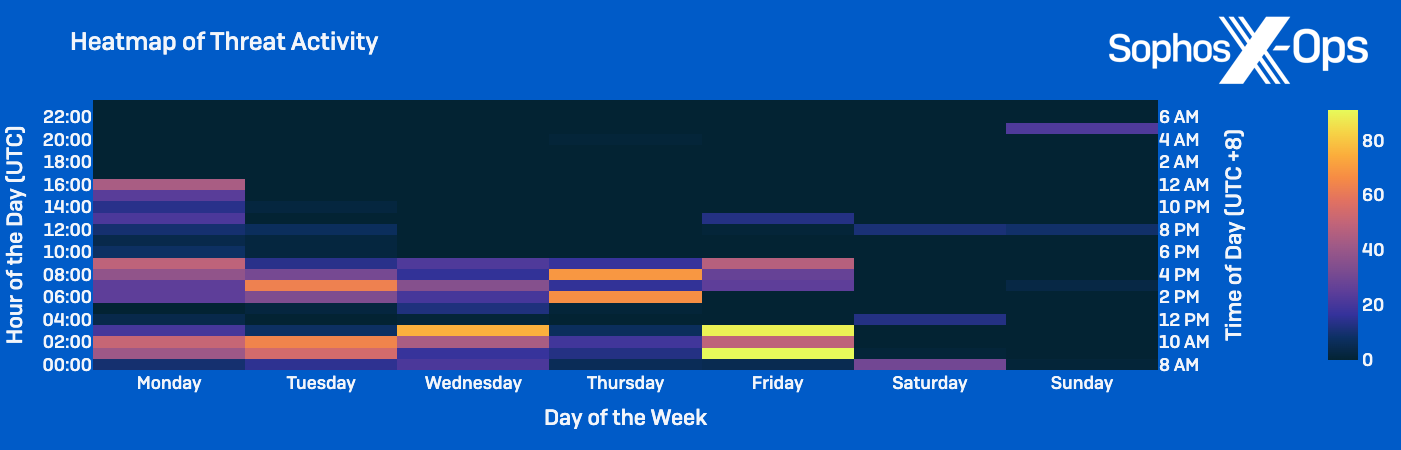
Examination of Clusters’ Operation Schedules
An evaluation of the temporal patterns within the individual activity clusters disclosed noticeable fluctuations in the timing of their actions, where seldom did they engage in extensive operations simultaneously.
In fact, it appears that the clusters have organized their activities around each other, suggesting the actors within these clusters might be privy to the actions of the others. At junctures, the activities of Cluster Alpha and Cluster Charlie seemed to alternate daily, for instance, where Cluster Alpha activity ceased for three days concurrently with a spike in Cluster Charlie activity observed in June.
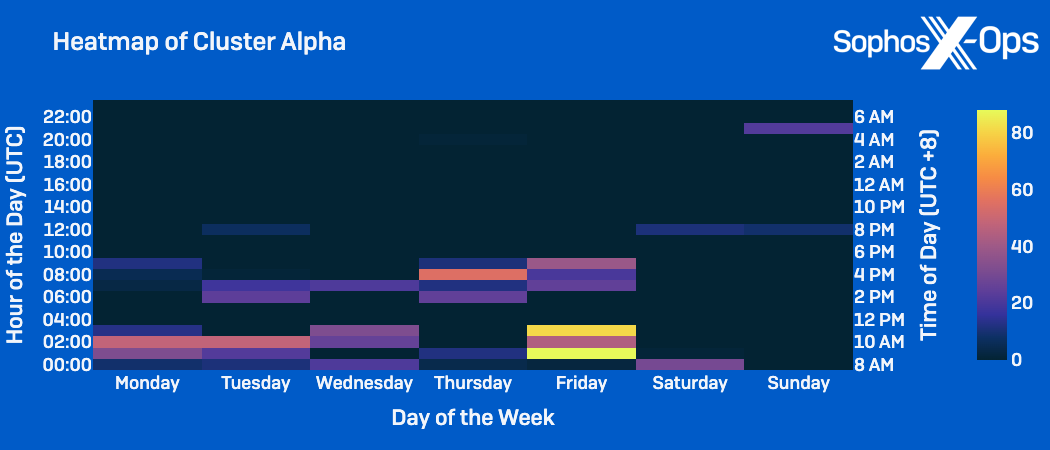
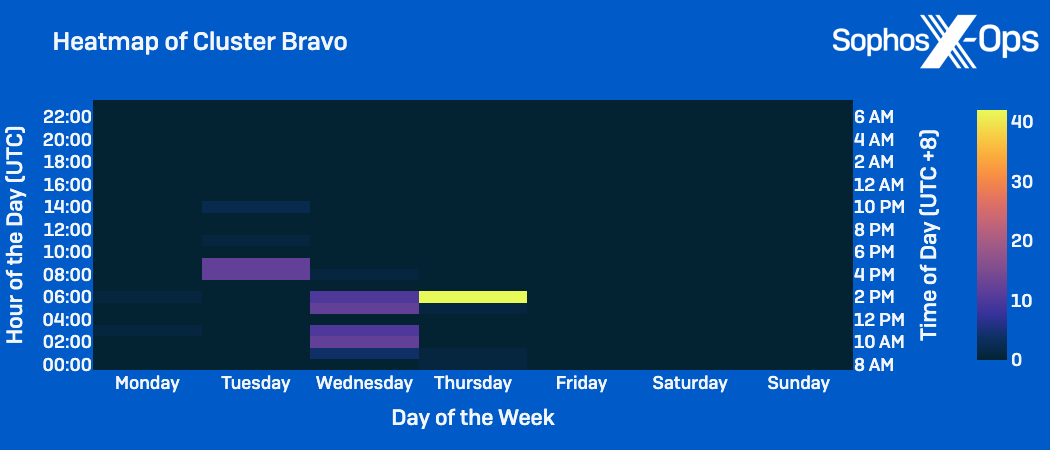
When inspecting the timeframes and weekdays of peak activity for the clusters, we observed similar patterns:
- Cluster Alpha behaviors: Frequently happening on weekdays within the usual working hours of 8am to 5pm CST, with a peak on Fridays.
- Cluster Bravo behaviors: Taking place within the standard working hours of 8am to 5pm CST, but mainly concentrated on Tuesdays, Wednesdays, and Thursdays.
- Cluster Charlie behaviors: Demonstrating the most variability beyond the regular work hours; Activity reaching its highest points from Monday through Wednesday, between 12pm to 6pm CST.
- The notable spike in Cluster Charlie’s activity on Mondays from 3pm to 12am CST corresponds to an increase in activity observed in the cluster during June.
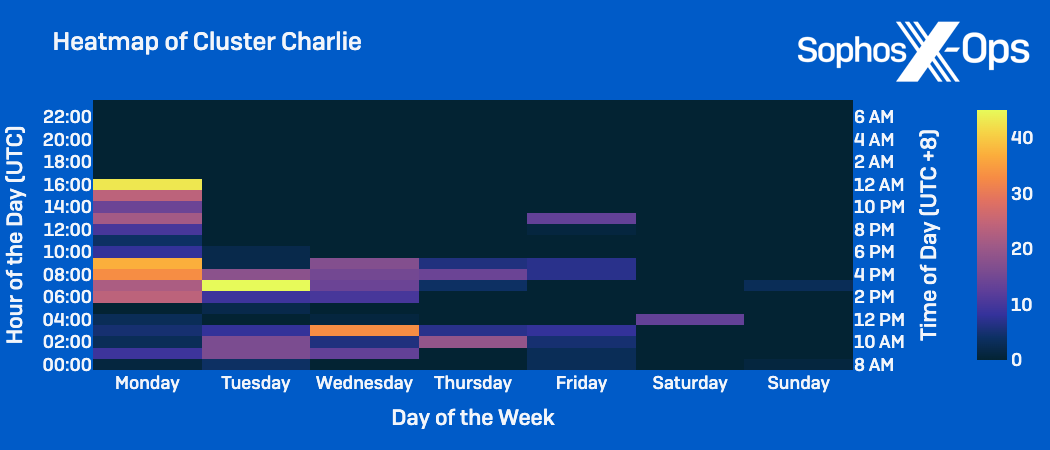
Assigning Grouped Actions
Despite having a high level of faith, Sophos MDR refrains from directly associating the observed threat clusters with Chinese state-backed operations, refraining from attributing them to any known threat actor groups presently. One rationale behind this decision is the tendency for Chinese threat entities to share infrastructure and toolsets, complicating the process of making attributions. Nevertheless, we have identified instances where our findings align with third-party reports, providing additional context to the observed activity.
Cluster Alpha Assessment
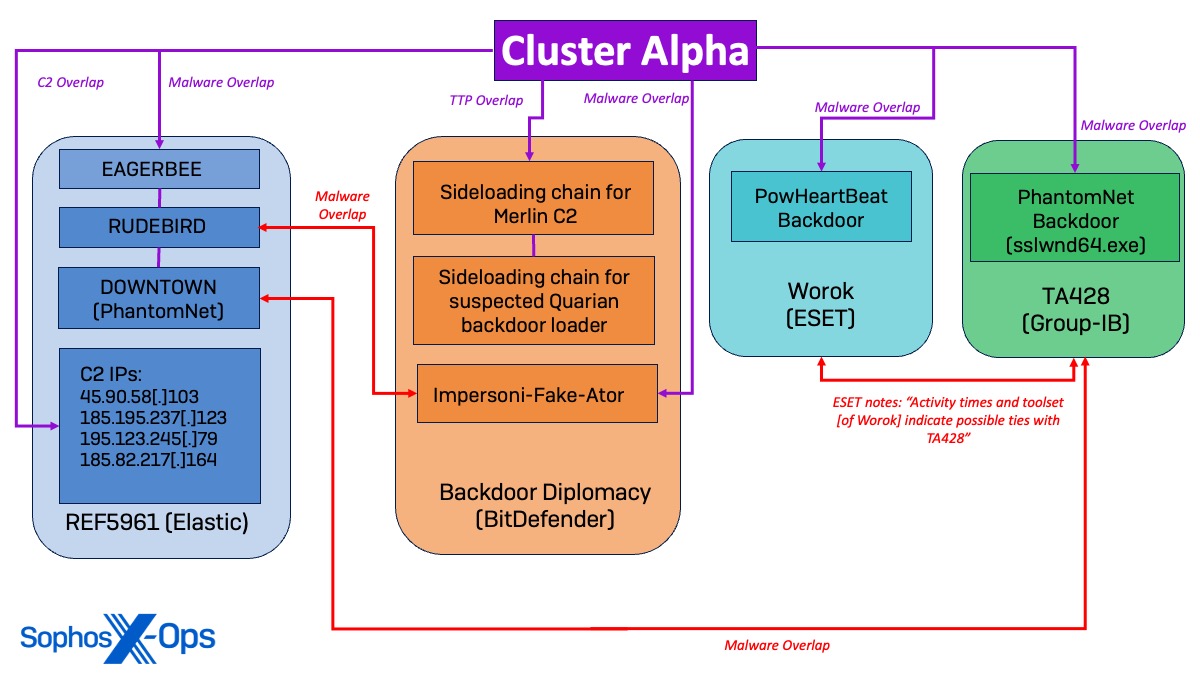
REF5961 Parallels
Three malware variants employed in Cluster Alpha show similarities to malware outlined in an October 2023 report by Elastic Security Labs concerning a Chinese-affiliated actor monitored as REF5961. The report details REF5961’s use of EAGERBEE, RUDEBIRD, and DOWNTOWN (PhantomNet) malware in an attempt to infiltrate the Foreign Affairs Ministry of an Association of Southeast Asian Nations (ASEAN) member. Additionally, some malware used in Cluster Alpha was observed communicating with several C2 IP addresses associated with REF5961.
BackdoorDiplomacy Parallels
The behavior of Cluster Alpha also matches a case study by BitDefender on a cyber espionage operation in the Middle East carried out by a Chinese threat actor traced…being known to intersect with other stated threat groups such as APT15, Playful Taurus, Vixen Panda, NICKEL, and Ke3chang.
The same sideloading chains described in the BitDefender report to introduce a Merlin C2 Agent and a suspected loader for the Quarian backdoor were observed by Sophos MDR hunters. Thanks to Sophos Endpoint controls, the malicious payload was removed before execution. However, the resemblance in sideloading procedures indicates a link between Cluster Alpha and previous campaigns of BackdoorDiplomacy.
Sophos Labs notably noted similarities between the RUDEBIRD malware monitored by Elastic and the Impersoni-Fake-Ator malware described by BitDefender. This suggests a potential connection between the REF5961 intrusion set and the Backdoor Diplomacy actor. While this connection is remarkable, we recognize that additional observations and samples are necessary to verify the extent of the overlap between these two reported actors with stronger confidence.
Similarities between Worok and TA428
Moreover, the PowHeartBeat backdoor utilized in Cluster Alpha has been linked by ESET to the Worok cyberespionage group, which is stated to have potential associations with the Chinese APT TA428. Enhancing this connection, the DOWNTOWN (PhantomNet) malware employed in Cluster Alpha was also attributed to TA428 by Elastic. Shortly after Group-IB Threat Intelligence identified the sample with suspected TA428 activity, Sophos observed the PhantomNet backdoor implant (sslwnd64.exe).
Cluster Bravo
The resemblance between the CCoreDoor backdoor used in Cluster Bravo operations and EtherealGh0st, as detailed in a BitDefender report from May 2024, is striking. EtherealGh0st is associated with a Chinese-nexus actor tracked by BitDefender as Unfading Sea Haze. The similarity exists in the usage of the CCore Library and StartWorkThread for decryption of the C2 hostname and port, as well as in the commands accepted by the backdoor. There is also an overlap in domains with the use of the C2 domain message.ooguy[.]com—Sophos MDR detected this C2 communicating with the CCoreDoor backdoor, and BitDefender’s report mentions the domain found in the EtherealGh0st sample they gathered.
Furthermore, BitDefender reported the initial use of EtheralGh0st around mid-March 2023, aligning with our timeline as CCoreDoor was first deployed on March 14, 2023. Additionally, there are similarities in victimology, as Unfading Sea Haze reportedly targets government and military organizations in countries bordering the South China Sea.
Cluster Charlie
Earth Longzhi Similarities (APT41)
Although the entity operating in Cluster Charlie introduced a previously unreported malware family, their C2 infrastructure coincides with findings by Trend Micro regarding a group known as Earth Longzhi, identified as a Chinese subgroup of APT41.
Sophos observed the PocoProxy sample 443.txt communicating with the known Earth Longzhi C2 IP 198.13.47[.]158 approximately a month before Trend Micro referenced that IP in their report. Other infrastructure utilized in Cluster Charlie aligns with Earth Longzhi’s previous infrastructure patterns as well, specifically in the usage of variants of the speedtest[.]com domain. In this intrusion, we witnessed the deployment of both googlespeedtest33[.]com and <victim name>speedtest[.]com. Similarly, two distinct Trend Micro reports have documented Earth Longzhi registering speedtest[.]com C2 domains with a similar format, such as vietsovspeedtest[.]com and evnpowerspeedtest[.]com.
Cluster Overlap
Although the evidence indicates three separate sets of TTPs functioning at different times with bespoke tooling, there are also evident intersections between them. For instance, instances where the clusters utilized identical credentials, like the actors in Cluster Alpha and Cluster Bravo employing the same insecure administrator account, were noted. This account was compromised during an internal penetration test and used to take actions on various systems.
Moreover, while the clusters operated on different endpoints, they targeted multiple primary servers and domain controllers. However, their presence on the same server on the same day was rare. As previously stated, temporal analysis of the clusters’ activity indicates a corresponding dynamic in the timing of their operations.
Analyzing the Overlap
During our analysis of the clusters and their interrelations, we found ourselves in a position similar to Cybereason’s Nocturnus Team, who undertook a comparable clustering effort in 2021 focused on Chinese targeting of telecommunication companies. As highlighted, identifying the nature of overlaps between clusters can be fraught with challenges, with “what ifs?” influencing the determination of the activities behind network intrusions.
In this instance, the activity clusters were witnessed within the same organization, during the same period, and even on the same endpoints. Hence, establishing attribution accurately can be a daunting task. The complexity of the analysis escalates when considering that Chinese state-sponsored threat groups are known to collaborate and share infrastructure and tooling.
Although the clusters display distinct behavioral patterns, the timing delineations of their operations, the overlaps in compromised infrastructure, and their shared objectives suggest a connection among them. While we cannot definitively determine the situation with high confidence, we present two plausible hypotheses to elucidate the dynamic between the observed clusters:
- The observed clusters reflect the activities of multiple independent actors collaborating with shared targets.
- The observed clusters indicate the efforts of a single group utilizing a broad array of tools, varied infrastructure, and numerous operators.
Presently, most of the evidence leans towards the first hypothesis as the most probable based on the level of coordination detected. However, we recognize that more data is required to affirm this assessment with stronger confidence. These hypotheses could evolve as our intelligence gathering continues and new evidence surfaces to shed light on the identities and relationships of the observed clusters.
Conclusions
Following our analysis, we ascertain with moderate confidence that multiple distinct Chinese state-sponsored actors have been active within this prominent Southeast Asian government organization since at least March 2022. While high-confidence attribution or clarification of the relationships between these clusters remains unachievable presently, our ongoing investigation suggests that the activities of the clusters reflect the work of separate actors assigned by a central body with parallel objectives serving Chinese state interests.
Although this report centers on Crimson Palace activities up to August 2023, we are continuing to monitor related intrusion attempts targeting this establishment. Following our actions to block the actors’ C2 implants in August, the threat actors remained silent for several weeks. Cluster Alpha’s last known active implant halted C2 communications in August 2023, and no resurgence of activity from the cluster has been observed. However, the scenario differs for Cluster Charlie.
After a period of dormancy, actors in Cluster Charlie were observed re-entering the network using a web shell and resuming their activities at an increased pace and in a more elusive manner. They started performing tasks on targets within the network, including efforts for exfiltration in November [link to section in second post]. Significantly, instead of leaving their implants on disks for prolonged periods, the actors employed different instances of their web shell to re-enter the network for their sessions and started modulating various C2 channels and methods of deploying implants on target systems.
Sophos MDR threat hunters continue to monitor and explore intrusion activities within this network, and disseminate intelligence to the wider community.
This cyberespionage campaign was unearthed through Sophos MDR’s human-led threat hunting service, which plays a pivotal role in proactively identifying threat activities. In addition to enhancing MDR operations, the MDR threat hunting service contributes to our SophosLabs pipeline to offer enhanced protection and detections.
The investigation into this campaign underlines the value of an efficient intelligence cycle, illustrating how a threat hunt triggered by a raised detection can generate intelligence for creating new detections and initiating additional hunts.
Acknowledgements:
Sophos X-Ops acknowledges the contributions of Colin Cowie, Jordon Olness, Hunter Neal, Andrew Jaeger, Pavle Culum, Kostas Tsialemis, and Daniel Souter from Sophos Managed Detection and Response, and Gabor Szappanos, Andrew Ludgate, and Steeve Gaudreault from SophosLabs in this report.




