A
new
phishing
technique
called
“file
archiver
in
the
browser”
can
be
leveraged
to
“emulate”
a
file
archiver
software
in
a
web
browser
when
a
victim
visits
a
.ZIP
domain.
“With
this
phishing
attack,
you
simulate
a
file
archiver
software
(e.g.,
WinRAR)
in
the
browser
and
use
a
.zip
domain
to
make
it
appear
more
legitimate,”
security
researcher
mr.d0x
disclosed
last
week.
Threat
actors,
in
a
nutshell,
could
create
a
realistic-looking
phishing
landing
page
using
HTML
and
CSS
that
mimics
legitimate
file
archive
software,
and
host
it
on
a
.zip
domain,
thus
elevating
social
engineering
campaigns.
In
a
potential
attack
scenario,
a
miscreant
could
resort
to
such
trickery
to
redirect
users
to
a
credential
harvesting
page
when
a
file
“contained”
within
the
fake
ZIP
archive
is
clicked.
“Another
interesting
use
case
is
listing
a
non-executable
file
and
when
the
user
clicks
to
initiate
a
download,
it
downloads
an
executable
file,”
mr.d0x
noted.
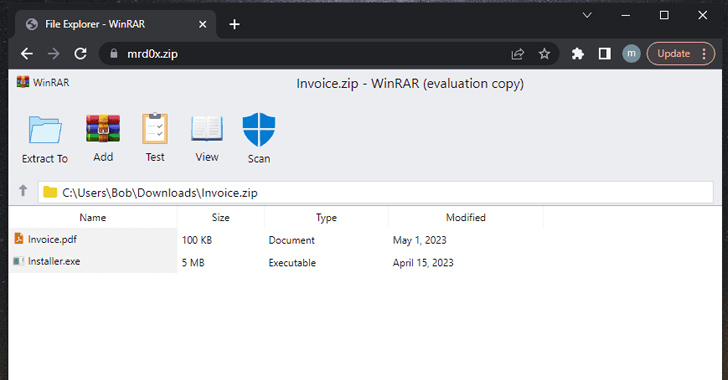
“Let’s
say
you
have
an
‘invoice.pdf’
file.
When
a
user
clicks
on
this
file,
it
will
initiate
the
download
of
a
.exe
or
any
other
file.”
On
top
of
that,
the
search
bar
in
the
Windows
File
Explorer
can
emerge
as
a
sneaky
conduit
where
searching
for
a
non-existent
.ZIP
file
opens
it
directly
in
the
web
browser
should
the
file
name
correspond
to
a
legitimate
.zip
domain.
“This
is
perfect
for
this
scenario
since
the
user
would
be
expecting
to
see
a
ZIP
file,”
the
researcher
said.
“Once
the
user
performs
this,
it
will
auto-launch
the
.zip
domain
which
has
the
file
archive
template,
appearing
pretty
legitimate.”
The
development
comes
as
Google
rolled
out
eight
new
top-level
domains
(TLDs),
including
“.zip”
and
“.mov,”
that
have
raised
some
concerns
that
it
could
invite
phishing
and
other
types
of
online
scams.
This
is
because
.ZIP
and
.MOV
are
both
legitimate
file
extension
names,
potentially
confusing
unsuspecting
users
into
visiting
a
malicious
website
rather
than
opening
a
file
and
dupe
them
into
accidentally
downloading
malware.
“ZIP
files
are
often
used
as
part
of
the
initial
stage
of
an
attack
chain,
typically
being
downloaded
after
a
user
accesses
a
malicious
URL
or
opens
an
email
attachment,”
Trend
Micro
said.
“Beyond
ZIP
archives
being
used
as
a
payload,
it’s
also
likely
that
malicious
actors
will
use
ZIP-related
URLs
for
downloading
malware
with
the
introduction
of
the
.zip
TLD.”
While
reactions
are
decidedly
mixed
on
the
risk
posed
as
a
result
of
confusion
between
domain
names
and
file
names,
it’s
expected
to
equip
actors
acting
in
bad
faith
with
yet
another
vector
for
phishing.
The
discovery
also
comes
as
cybersecurity
company
Group-IB
said
it
detected
a
25%
surge
in
the
use
of
phishing
kits
in
2022,
identifying
3,677
unique
kits,
when
compared
to
the
preceding
year.
Of
particular
interest
is
the
uptick
in
the
trend
of
using
Telegram
to
collect
stolen
data,
almost
doubling
from
5.6%
in
2021
to
9.4%
in
2022.
That’s
not
all.
Phishing
attacks
are
also
becoming
more
sophisticated,
with
cybercriminals
increasingly
focusing
on
packing
the
kits
with
detection
evasion
capabilities
such
as
the
use
of
antibots
and
dynamic
directories.
“Phishing
operators
create
random
website
folders
that
are
only
accessible
by
the
recipient
of
a
personalized
phishing
URL
and
cannot
be
accessed
without
the
initial
link,”
the
Singapore-headquartered
firm
said.
“This
technique
allows
phishers
to
evade
detection
and
blacklisting
as
the
phishing
content
will
not
reveal
itself.”
UPCOMING
WEBINAR
Zero
Trust
+
Deception:
Learn
How
to
Outsmart
Attackers!
Discover
how
Deception
can
detect
advanced
threats,
stop
lateral
movement,
and
enhance
your
Zero
Trust
strategy.
Join
our
insightful
webinar!
According
to
a
new
report
from
Perception
Point,
the
number
of
advanced
phishing
attacks
attempted
by
threat
actors
in
2022
rose
356%.
The
total
number
of
attacks
increased
by
87%
over
the
course
of
the
year.
This
continued
evolution
of
phishing
schemes
is
exemplified
by
a
fresh
wave
of
attacks
that
have
been
observed
leveraging
compromised
Microsoft
365
accounts
and
restricted-permission
message
(.rpmsg)
encrypted
emails
to
harvest
users’
credentials.
“The
use
of
encrypted
.rpmsg
messages
means
that
the
phishing
content
of
the
message,
including
the
URL
links,
are
hidden
from
email
scanning
gateways,”
Trustwave
researchers
Phil
Hay
and
Rodel
Mendrez
explained.
Another
instance
highlighted
by
Proofpoint
entails
the
possible
abuse
of
legitimate
features
in
Microsoft
Teams
to
facilitate
phishing
and
malware
delivery,
including
utilizing
meeting
invites
post-compromise
by
replacing
default
URLs
with
malicious
links
via
API
calls.
“A
different
approach
that
attackers
can
utilize,
given
access
to
a
user’s
Teams
token,
is
using
Teams’
API
or
user
interface
to
weaponize
existing
links
in
sent
messages,”
the
enterprise
security
firm
noted.
“This
could
be
done
by
simply
replacing
benign
links
with
links
pointing
to
nefarious
websites
or
malicious
resources.”
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.