DarkGate Malware Swaps AutoIt with AutoHotkey in Recent Cyber Intrusions
The DarkGate malware-as-a-service (MaaS) operations are now using an AutoHotkey mechanism instead of AutoIt scripts to introduce the final phases of cyber attacks, indicating persistent efforts by threat actors to outsmart detection mechanisms.
The changes were identified in the 6th version of DarkGate launched in March 2024 by RastaFarEye, the developer who has been offering the software on a subscription basis to around 30 clients. The malware has been active since at least 2018.
DarkGate is a fully-featured remote access trojan (RAT) that comes with command-and-control (C2) and rootkit capabilities, along with various modules for stealing credentials, logging keys, capturing screens, and managing remote desktop sessions.
“DarkGate campaigns adapt quickly by altering several components to evade security solutions,” noted Trellix security researcher Ernesto Fernández Provecho in an analysis on Monday. “This marks the first instance where DarkGate has utilized AutoHotKey, a relatively uncommon scripting interpreter, to launch DarkGate.”
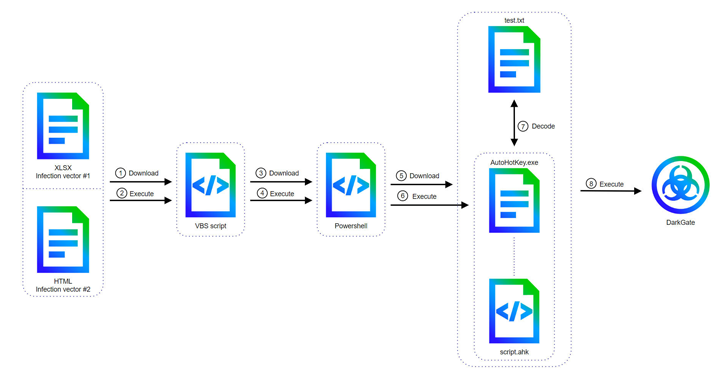
It’s noteworthy that McAfee Labs first documented DarkGate’s shift to AutoHotKey in late April 2024, with attack sequences exploiting vulnerabilities such as CVE-2023-36025 and CVE-2024-21412 to bypass Microsoft Defender SmartScreen protections through Microsoft Excel or HTML attachments in phishing emails.
Other techniques involve leveraging Excel files with embedded macros to run a Visual Basic Script file that initiates PowerShell commands to eventually execute an AutoHotKey script, which then fetches and decodes the DarkGate payload from a text file.
The latest version of DarkGate introduces significant enhancements in its configuration, evasion tactics, and the roster of supported commands, now encompassing audio recording, mouse manipulation, and keyboard supervision functionalities.
“Version 6 brings not only new commands but also omits some from previous versions, such as privilege escalation, cryptomining, or hVNC (Hidden Virtual Network Computing) components,” Fernández Provecho remarked, suggesting that this could be a strategy to eliminate features that might lead to detection.
“Furthermore, given that DarkGate is marketed to a limited clientele, it’s possible that these features were not in demand by customers, compelling RastaFarEye to eliminate them.”
This revelation coincides with the detection of cyber criminals exploiting Docusign by vending authentic-looking customizable phishing templates on dark web platforms, transforming the service into a rich hunting ground for phishers specialized in pilfering credentials for phishing and business email compromise (BEC) schemes.
“These deceitful emails, meticulously crafted to emulate legitimate document signing requests, entice unsuspecting recipients to click on malicious links or disclose sensitive details,” noted Abnormal Security in a statement.












