Dark Pink APT Group Leverages TelePowerBot and KamiKakaBot in Sophisticated Attacks
The
threat
actor
known
as
Dark
Pink
has
been
linked
to
five
new
attacks
aimed
at
various
entities
in
Belgium,
Brunei,
Indonesia,
Thailand,
and
Vietnam
between
February
2022
and
April
2023.
This
includes
educational
entities,
government
agencies,
military
bodies,
and
non-profit
organizations,
indicating
the
adversarial
crew’s
continued
focus
on
high-value
targets.
Dark
Pink,
also
called
Saaiwc
Group,
is
an
advanced
persistent
threat
(APT)
actor
believed
to
be
of
Asia-Pacific
origin,
with
attacks
targeting
entities
primarily
located
in
East
Asia
and,
to
a
lesser
extent,
in
Europe.
The
group
employs
a
set
of
custom
malware
tools
such
as
TelePowerBot
and
KamiKakaBot
that
provide
various
functions
to
exfiltrate
sensitive
data
from
compromised
hosts.
“The
group
uses
a
range
of
sophisticated
custom
tools,
deploys
multiple
kill
chains
relying
on
spear-phishing
emails,”
Group-IB
security
researcher
Andrey
Polovinkin
said
in
a
technical
report
shared
with
The
Hacker
News.
“Once
the
attackers
gain
access
to
a
target’s
network,
they
use
advanced
persistence
mechanisms
to
stay
undetected
and
maintain
control
over
the
compromised
system.”
The
findings
also
illustrate
some
key
modifications
to
the
Dark
Pink
attack
sequence
to
impede
analysis
as
well
as
accommodate
improvements
to
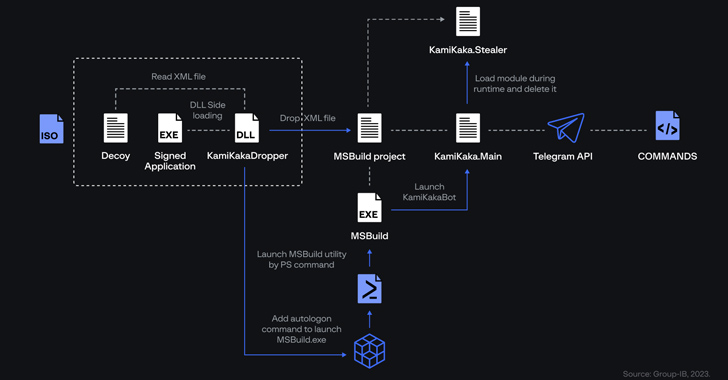
KamiKakaBot,
which
executes
commands
from
a
threat
actor-controlled
Telegram
channel
via
a
Telegram
bot.
The
latest
version,
notably,
splits
its
functionality
into
two
distinct
parts:
One
for
controlling
devices
and
the
other
for
harvesting
valuable
information.
The
Singapore-headquartered
company
said
it
also
identified
a
new
GitHub
account
associated
with
the
account
that
contains
PowerShell
scripts,
ZIP
archives,
and
custom
malware
which
were
committed
between
January
9,
2023,
and
April
11,
2023.
Besides
using
Telegram
for
command-and-control,
Dark
Pink
has
been
observed
exfiltrating
stolen
data
over
HTTP
using
a
service
called
webhook[.]site.
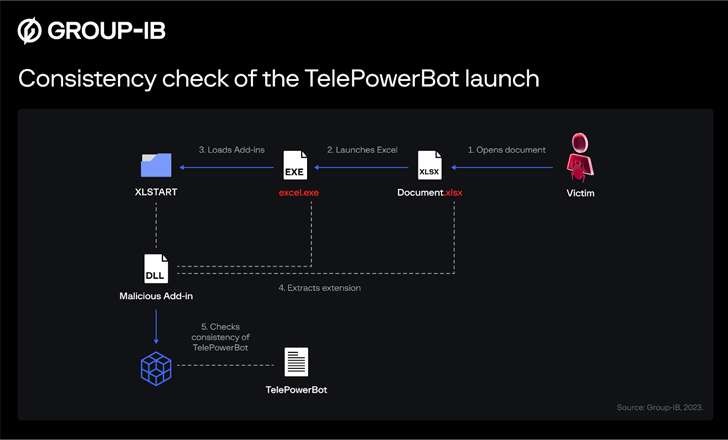
Another
notable
aspect
is
the
use
of
an
Microsoft
Excel
add-in
to
ensure
the
persistence
of
TelePowerBot
within
the
infected
host.
UPCOMING
WEBINAR
Zero
Trust
+
Deception:
Learn
How
to
Outsmart
Attackers!
Discover
how
Deception
can
detect
advanced
threats,
stop
lateral
movement,
and
enhance
your
Zero
Trust
strategy.
Join
our
insightful
webinar!
“With
webhook[.]site,
it
is
possible
to
set
up
temporary
endpoints
in
order
to
capture
and
view
incoming
HTTP
requests,”
Polovinkin
noted.
“The
threat
actor
created
temporary
endpoints
and
sent
sensitive
data
stolen
from
victims.”
Dark
Pink,
its
espionage
motives
notwithstanding,
remains
shrouded
in
mystery.
That
said,
it’s
suspected
that
the
hacking
crew’s
victimology
footprint
could
be
broader
than
previously
assumed.
The
fact
that
the
adversary
has
been
linked
to
only
13
attacks
(counting
the
five
new
victims)
since
mid-2021
indicates
an
attempt
to
maintain
a
low
profile
for
stealthiness.
It’s
also
a
sign
of
the
threat
actor
carefully
selecting
their
targets
and
keeping
the
number
of
attacks
at
a
minimum
to
reduce
the
likelihood
of
exposure.
“The
fact
that
two
attacks
were
executed
in
2023
indicates
that
Dark
Pink
remains
active
and
poses
an
ongoing
risk
to
organizations,”
Polovinkin
said.
“Evidence
shows
that
the
cybercriminals
behind
these
attacks
keep
updating
their
existing
tools
in
order
to
remain
undetected.”