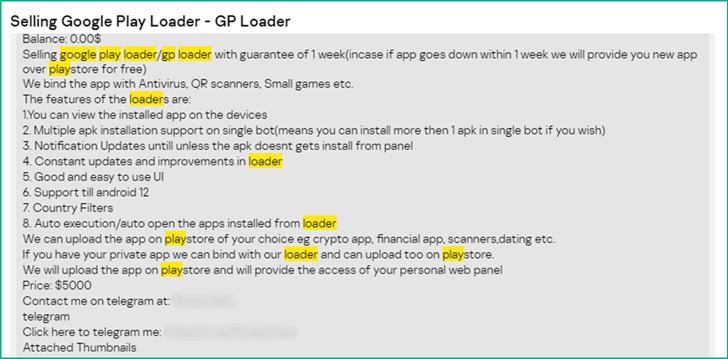
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security

Malicious
loader
programs
capable
of
trojanizing
Android
applications
are
being
traded
on
the
criminal
underground
for
up
to
$20,000
as
a
way
to
evade
Google
Play
Store
defenses.
“The
most
popular
application
categories
to
hide
malware
and
unwanted
software
include
cryptocurrency
trackers,
financial
apps,
QR-code
scanners,
and
even
dating
apps,”
Kaspersky
said
in
a
new
report
based
on
messages
posted
on
online
forums
between
2019
and
2023.
Dropper
apps
are
the
primary
means
for
threat
actors
looking
to
sneak
malware
via
the
Google
Play
Store.
Such
apps
often
masquerade
as
seemingly
innocuous
apps,
with
malicious
updates
introduced
upon
clearing
the
review
process
and
the
applications
have
amassed
a
significant
user
base.
This
is
achieved
by
using
a
loader
program
that’s
responsible
for
injecting
malware
into
a
clean
app,
which
is
then
made
available
for
download
from
the
app
marketplace.
Users
who
install
the
tampered
app
are
prompted
to
grant
it
intrusive
permissions
to
facilitate
malicious
activities.
The
apps,
in
some
instances,
also
incorporate
anti-analysis
features
to
detect
if
they
are
being
debugged
or
installed
in
a
sandboxed
environment,
and
if
so,
halt
their
operations
on
the
compromised
devices.
As
another
option,
threat
actors
can
purchase
a
Google
Play
developer
account
–
either
hacked
or
newly
created
by
the
sellers
–
for
anywhere
between
$60
and
$200,
depending
on
the
number
of
already
published
apps
and
download
counts.
App
developer
accounts
lacking
in
strong
password
or
two-factor
authentication
(2FA)
protections
can
be
trivially
cracked
and
put
up
for
sale,
thereby
allowing
other
actors
to
upload
malware
to
existing
apps.
A
third
alternative
is
the
use
of
APK
binding
services,
which
are
responsible
for
hiding
a
malicious
APK
file
in
a
legitimate
application,
for
distributing
the
malware
through
phishing
texts
and
dubious
websites
advertising
cracked
games
and
software.
Binding
services,
as
opposed
to
loaders,
cost
less
owing
to
the
fact
that
the
poisoned
apps
are
not
available
via
the
Google
Play
Store.
Notably,
the
technique
has
been
used
to
deliver
Android
banking
trojans
like
SOVA
and
Xenomorph
in
the
past.
UPCOMING
WEBINAR
Learn
to
Secure
the
Identity
Perimeter
–
Proven
Strategies
Improve
your
business
security
with
our
upcoming
expert-led
cybersecurity
webinar:
Explore
Identity
Perimeter
strategies!
Some
other
illicit
services
offered
for
sale
on
cybercrime
markets
include
malware
obfuscation
($30),
web
injects
($25-$80),
and
virtual
private
servers
($300),
the
latter
of
which
can
be
used
to
control
infected
devices
or
to
redirect
user
traffic.
Furthermore,
attackers
can
buy
installs
for
their
Android
apps
(legitimate
or
otherwise)
through
Google
Ads
for
$0.5
on
average.
Installation
costs
vary
based
on
the
targeted
country.
To
mitigate
risks
posed
by
Android
malware,
users
are
recommended
to
refrain
from
installing
apps
from
unknown
sources,
scrutinize
app
permissions,
and
keep
their
devices
up-to-date.