
Learn
how
to
protect
your
business
and
staff
from
the
MortalKombat
ransomware
and
Laplas
Clipper
malware.

SomYuZu/Adobe
Stock
A
new
attack
campaign
launched
by
an
unknown
threat
actor
targets
the
U.S.
with
two
malware
families:
MortalKombat
ransomware
and
Laplas
Clipper.
We
detail
how
these
malware
campaigns
are
executed
and
how
to
keep
your
business
safe.
Jump
to:
How
these
cybersecurity
attacks
are
executed
This
attack
campaign
as
described
by
Cisco
Talos
starts
with
a
phishing
email
(Figure
A)
that
impersonates
CoinPayments,
a
legitimate
cryptocurrency
payment
gateway.
The
content
is
very
brief,
describing
a
payment
in
Bitcoin
that
has
been
canceled
due
to
a
time-out
problem.
It
seems
reasonable
to
believe
only
people
making
transactions
in
Bitcoin
would
open
the
attached
file,
which
is
a
ZIP
archive
file
containing
a
malicious
BAT
loader
script.
Figure
A

Cisco
Talos.
Phishing
content
impersonating
a
legitimate
cryptocurrency
platform.
Once
executed,
the
loader
downloads
another
ZIP
file
from
a
server
belonging
to
the
attackers’
infrastructure,
whose
content
might
be
MortalKombat
ransomware
or
Laplas
Clipper
malware
(Figure
B).
Figure
B

Cisco
Talos.
Initial
compromise
flow
for
the
attack
campaign.
What
is
MortalKombat
ransomware?
According
to
a
Cisco
Talos
researcher,
MortalKombat
ransomware
was
first
observed
in
January
2023.
This
32-bit
Windows
executable
file,
once
executed,
copies
itself
into
the
local
user
profile’s
temporary
folder
before
dropping
an
image
file
that
will
be
loaded
as
the
victims’
wallpaper
(Figure
C).
Figure
C

Cisco
Talos.
Wallpaper
with
instructions,
as
installed
by
MortalKombat
ransomware.
The
ransomware
contains
a
huge
list
of
file
extensions
it
targets
for
encryption.
Every
time
there
is
a
match,
the
matching
file
is
encrypted.
The
ransomware
also
checks
for
logical
drives
connected
to
the
machine
it
runs
on,
and
searches
for
the
same
file
extensions
through
all
folders
recursively,
encrypting
more
files
as
they
are
found.
All
encrypted
files
receive
a
new
file
extension
—
Remember_you_got_only_24_hours_to_make_the_payment_if_you_dont_pay_prize_will_triple_Mortal_Kombat_Ransomware
—
and
the
same
ransom
note
file
is
created
in
every
folder
where
files
are
encrypted.
Files
in
the
recycle
bin
folder
are
having
their
file
name
changed,
too,
with
the
same
file
extension.
The
Cisco
Talos
researcher
found
similarities
between
MortalKombat
ransomware
and
a
much
older
ransomware
dubbed
Xorist,
which
appeared
in
2010
and
has
been
widely
used
to
create
ransomware
variants.
A
particular
Alcmeter
registry
key
string
and
a
ClassName
string
X0r157
are
markers
of
the
Xorist
ransomware
and
have
been
found
in
the
code
of
the
MortalKombat
ransomware.
Deeper
code
analysis
from
Talos
brought
high
confidence
that
the
MortalKombat
ransomware
belongs
to
the
same
family
as
Xorist.
What
is
Laplas
Clipper
malware?
The
Laplas
Clipper
malware
version
Cisco
Talos
found
was
developed
in
the
Go
programming
language,
but
previous
versions
have
used
other
languages
including
VB.NET.
The
malware
embeds
encrypted
strings
that
are
decrypted
in
the
initial
phase
of
execution
of
the
malware.
The
malware
copies
itself
on
the
system
and
establishes
persistence
before
monitoring
the
users’
clipboard
to
look
for
cryptocurrency
wallet
addresses.
Once
a
cryptocurrency
wallet
is
detected
in
the
clipboard,
it
is
replaced
by
an
attacker-controlled
wallet
sent
by
the
C2
server.
The
malware
knows
these
cryptocurrencies:
Dash,
Bitcoin,
Bitcoin
Cash,
Zcash,
Litecoin,
Ethereum,
Binance
coin,
Dogecoin,
Monero,
Ripple,
Tezos,
Ronin,
Tron,
Cardano
and
Cosmos.
The
malware
is
advertised
on
cybercriminals’
underground
marketplaces
(Figure
D)
and
sold
as
a
service
for
$59
per
month,
according
to
Cyble
Research
&
Intelligence
Labs.
Figure
D

Cyble.
Ad
for
Laplas
Clipper
malware
on
a
cybercriminal
underground
marketplace.
As
a
result
of
the
infection,
unsuspecting
victims
think
they
are
making
a
cryptocurrency
payment
without
trouble;
in
fact,
they
are
being
scammed,
and
their
transaction
amount
is
sent
to
an
attacker-controlled
wallet.
U.S.
is
the
main
target
for
this
security
threat
The
main
target
for
this
attack
campaign,
as
provided
by
Cisco
Talos,
is
the
U.S.,
followed
by
the
U.K.,
Turkey
and
the
Philippines
(Figure
E).
Figure
E
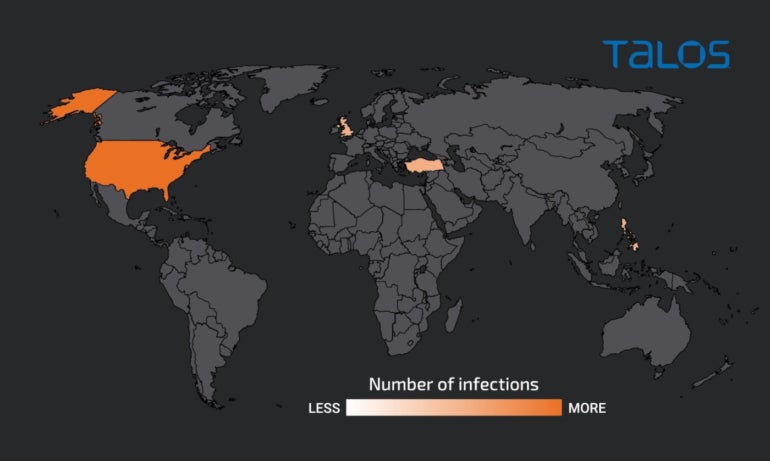
Cisco
Talos.
Victimology
shows
the
U.S.
as
the
most
impacted
country
of
the
attack
campaign.
While
no
intelligence
is
provided
about
the
phishing
email
targets,
it
is
reasonable
to
believe
that
the
targeted
emails
are
probably
from
users
dealing
with
cryptocurrency.
How
to
protect
your
business
from
MortalKombat
and
Laplas
malware
The
initial
infection
relies
on
social
engineering
and
not
vulnerabilities.
It
is
advised
to
raise
awareness
to
all
employees
by
providing
them
with
regular
security
training
and
tips
to
avoid
falling
for
social
engineering-driven
infections,
especially
via
emails.
Plus,
all
operating
systems
and
software
should
always
be
up
to
date
and
patched
to
prevent
being
compromised
by
a
common
vulnerability
and
to
deploy
security
solutions
at
every
level
of
the
corporate
infrastructure.
In
the
case
of
the
Laplas
Clipper,
as
it
alters
the
content
of
the
clipboard
by
replacing
one
cryptocurrency
wallet
for
another,
it
is
strongly
advised
to
always
check
that
the
result
from
a
copy/paste
operation
of
a
wallet
is
the
exact
same
one
as
the
initial
one.
Another
security
tip
is
to
make
regular
data
backups,
with
backups
staying
offline,
so
that
it
is
still
possible
to
revert
to
good
data
when
ransomware
has
hit
the
infrastructure.
Disclosure:
I
work
for
Trend
Micro,
but
the
views
expressed
in
this
article
are
mine.
Read
next:
Security
awareness
and
training
policy
(TechRepublic
Premium)









