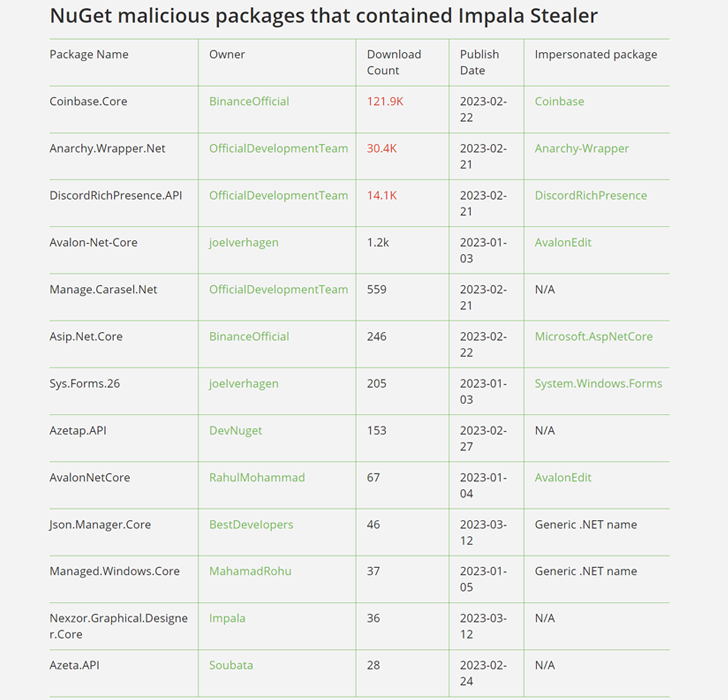
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages

Cybersecurity
researchers
have
detailed
the
inner
workings
of
the
cryptocurrency
stealer
malware
that
was
distributed
via
13
malicious
NuGet
packages
as
part
of
a
supply
chain
attack
targeting
.NET
developers.
The
sophisticated
typosquatting
campaign,
which
was
detailed
by
JFrog
late
last
month,
impersonated
legitimate
packages
to
execute
PowerShell
code
designed
to
retrieve
a
follow-on
binary
from
a
hard-coded
server.
The
two-stage
attack
culminates
in
the
deployment
of
a
.NET-based
persistent
backdoor,
called
Impala
Stealer,
which
is
capable
of
gaining
unauthorized
access
to
users’
cryptocurrency
accounts.
“The
payload
used
a
very
rare
obfuscation
technique,
called
‘.NET
AoT
compilation,’
which
is
a
lot
more
stealthy
than
using
‘off
the
shelf’
obfuscators
while
still
making
the
binary
hard
to
reverse
engineer,”
JFrog
told
The
Hacker
News
in
a
statement.
.NET
AoT
compilation
is
an
optimization
technique
that
allows
apps
to
be
ahead-of-time
compiled
to
native
code.
Native
AOT
apps
also
have
faster
startup
time
and
smaller
memory
footprints,
and
can
run
on
a
machine
without
.NET
runtime
installed.
The
second-stage
payload
comes
with
an
auto-update
mechanism
that
enables
it
to
retrieve
new
versions
of
the
executable
from
a
remote
location.
It
further
achieves
persistence
by
injecting
JavaScript
code
into
Discord
or
Microsoft
Visual
Studio
Code
apps,
thereby
activating
the
launch
of
the
stealer
binary.
The
binary
then
proceeds
to
search
for
the
installation
of
the
Exodus
Wallet
desktop
application
and
inserts
JavaScript
code
into
various
HTML
files
in
order
to
harvest
and
exfiltrate
sensitive
data
to
a
hard-coded
Discord
webhook.
The
JavaScript
snippet,
for
its
part,
is
fetched
from
an
online
paste
website
from
where
it’s
already
been
deleted.
That
said,
it’s
suspected
that
the
code
may
have
been
used
to
steal
user
credentials
and
access
other
information
of
interest.
“The
bad
actors
used
typosquatting
techniques
to
deploy
a
custom
malicious
payload
[…]
which
targets
the
Exodus
crypto
wallet
and
leaks
the
victim’s
credentials
to
cryptocurrency
exchanges,
by
using
code
injection,”
Shachar
Menashe,
senior
director
at
JFrog
Security
Research,
said.
UPCOMING
WEBINAR
Learn
to
Secure
the
Identity
Perimeter
–
Proven
Strategies
Improve
your
business
security
with
our
upcoming
expert-led
cybersecurity
webinar:
Explore
Identity
Perimeter
strategies!
“Our
investigation
proves
no
open
source
software
repository
is
completely
trust-worthy,
so
safety
measures
should
be
taken
at
every
step
of
the
software
development
lifecycle
to
ensure
the
software
supply
chain
remains
secure.”
The
findings
come
as
Phylum
unearthed
a
malicious
npm
package
named
mathjs-min
that
was
uploaded
to
the
repository
on
March
26,
2023,
and
found
to
harbor
a
credential
stealer
that
grabs
Discord
passwords
from
the
official
app
as
well
as
web
browsers
like
Google
Chrome,
Brave,
and
Opera.
“This
package
is
actually
a
modified
version
of
the
widely
used
Javascript
math
library
mathjs,
and
was
injected
with
malicious
code
after
being
forked,”
the
software
supply
chain
security
firm
said.
“The
modified
version
was
then
published
to
NPM
with
the
intention
of
passing
it
off
as
a
minified
version
of
the
genuine
mathjs
library.”