The
U.S.
Cybersecurity
and
Infrastructure
Security
Agency
(CISA)
and
Federal
Bureau
of
Investigation
(FBI)
have
published
a
joint
advisory
regarding
the
active
exploitation
of
a
recently
disclosed
critical
flaw
in
Progress
Software’s
MOVEit
Transfer
application
to
drop
ransomware.
“The
Cl0p
Ransomware
Gang,
also
known
as
TA505,
reportedly
began
exploiting
a
previously
unknown
SQL
injection
vulnerability
in
Progress
Software’s
managed
file
transfer
(MFT)
solution
known
as
MOVEit
Transfer,”
the
agencies
said.
“Internet-facing
MOVEit
Transfer
web
applications
were
infected
with
a
web
shell
named
LEMURLOOT,
which
was
then
used
to
steal
data
from
underlying
MOVEit
Transfer
databases.”
The
prolific
cybercrime
gang
has
since
issued
an
ultimatum
to
several
impacted
businesses,
urging
them
to
get
in
touch
by
June
14,
2023,
or
risk
getting
all
their
stolen
data
published.
Microsoft
is
tracking
the
activity
under
the
moniker
Lace
Tempest
(aka
Storm-0950),
which
has
also
been
implicated
in
the
exploitation
of
a
critical
security
vulnerability
in
PaperCut
servers.
Active
since
at
least
February
2019,
the
adversary
has
been
linked
to
a
wide
range
of
activities
in
the
cybercrime
ecosystem,
including
operating
a
ransomware-as-a-service
(RaaS)
and
acting
as
an
affiliate
for
other
RaaS
schemes.
It
has
also
been
observed
acting
as
an
initial
access
broker
(IAB)
to
profit
off
access
to
compromised
enterprise
networks
and
also
as
a
customer
of
other
IABs,
underscoring
the
interconnected
nature
of
the
threat
landscape.
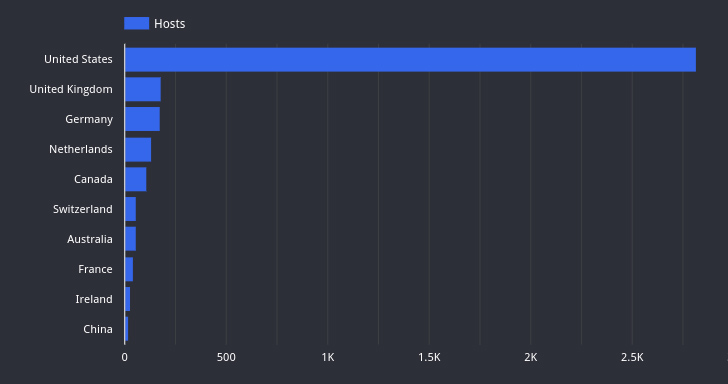
 |
|
Source: Kroll |
The
abuse
of
CVE-2023-34362,
an
SQL
injection
flaw
in
MOVEit
Transfer,
is
a
sign
of
the
adversary
continuously
seeking
zero-day
exploits
in
internet-facing
applications
and
using
them
to
their
advantage
in
order
to
extort
victims.
It’s
worth
noting
that
Cl0p
carried
out
similar
mass
exploitation
attacks
on
other
managed
file
transfer
applications
such
as
Accellion
FTA
and
GoAnywhere
MFT
over
the
past
year.
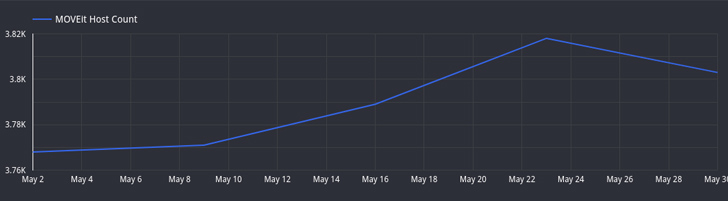
Attack
surface
management
firm
Censys
said
it
has
observed
a
drop
in
the
number
of
hosts
running
exposed
MOVEit
Transfer
instances
from
over
3,000
hosts
to
little
more
than
2,600.
“Several
of
these
hosts
are
associated
with
high-profile
organizations,
including
multiple
Fortune
500
companies
and
both
state
and
federal
government
agencies,”
Censys
noted,
highlighting
finance,
technology,
and
healthcare
as
the
sectors
with
the
most
exposures.
UPCOMING
WEBINAR
🔐
Mastering
API
Security:
Understanding
Your
True
Attack
Surface
Discover
the
untapped
vulnerabilities
in
your
API
ecosystem
and
take
proactive
steps
towards
ironclad
security.
Join
our
insightful
webinar!
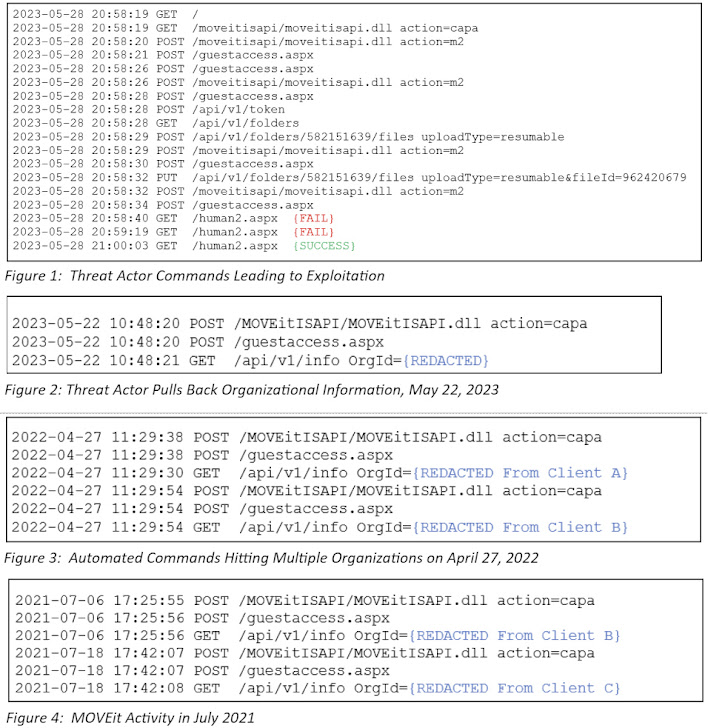
Kroll,
in
an
analysis
shared
with
The
Hacker
News,
said
it
identified
activity
indicating
that
the
Clop
threat
actors
were
likely
experimenting
with
ways
to
exploit
this
particular
flaw
in
April
2022
and
as
far
back
as
July
2021.
The
finding
is
particularly
significant
as
it
serves
to
illustrate
the
attacker’s
technical
expertise
and
the
planning
that
has
gone
into
staging
the
intrusions
much
before
the
recent
wave
of
exploitations
began.
“Commands
during
the
July
2021
time
frame
appeared
to
be
run
over
a
longer
amount
of
time,
suggesting
that
testing
may
have
been
a
manual
process
at
that
point
before
the
group
created
an
automated
solution
that
it
began
testing
in
April
2022,”
Kroll
said.
The
July
2021
exploitation
is
said
to
have
originated
from
an
IP
address
(45.129.137[.]232)
that
was
previously
attributed
to
the
Cl0p
actor
in
connection
with
attempts
to
exploit
flaws
in
SolarWinds
Serv-U
product
around
the
same
time.
“This
is
the
third
time
Cl0p
ransomware
group
have
used
a
zero
day
in
webapps
for
extortion
in
three
years,”
security
researcher
Kevin
Beaumont
said.
“In
all
three
cases
they
were
products
with
security
in
the
branding.”