
An analysis by Cisco Talos delved into the primary 14 ransomware factions operating between 2023 and 2024. The study served to uncover their modus operandi and shed light on intriguing Tactics, Techniques, and Protocols. Moreover, the security firm uncovered the vulnerabilities most exploited by ransomware perpetrators.
Key Findings on Ransomware Attack Patterns from Cisco Talos
Almost all ransomware assailants follow a standardized attack sequence.
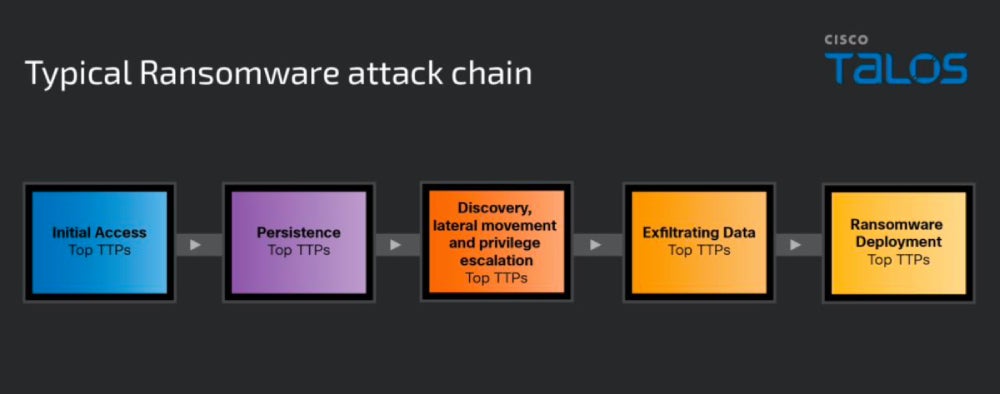
Initial Step Taken by Ransomware Operators
The first phase entails breaching the targeted entity. To achieve this objective, ransomware operators employ various approaches — a prevalent tactic involves social manipulation where deceptive emails are dispatched carrying malicious attachments or links that trigger malware on the targeted system. Subsequently, the malware enables the attacker to introduce additional tools and malware to progress towards their objectives. Multifactor authentication circumvention is a possibility at this juncture, accomplished through diverse methods due to either flawed MFA implementation or possession of legitimate credentials.
Talos also highlighted an escalating trend where ransomware affiliates scout internet-facing systems for susceptibilities or configuration lapses that could render the system vulnerable. Particularly precarious are systems running outdated or unpatched software.
Subsequent Step for Ransomware Operators
The subsequent phase revolves around establishing persistence as a precautionary measure in case the initial compromise vector is detected. This persistence on systems is typically achieved by tweaking Windows registry keys or enabling automated execution of the malevolent code during system startup. Additionally, local, domain, and/or cloud accounts may be established for persistence.
Follow-Up Measure for Ransomware Operators
In this stage, the assailant probes the network environment to garner a deeper comprehension of the infrastructure’s internal components. Valuable data that can be leveraged for ransom is identified during this stage. To traverse the entire network successfully, assailants frequently utilize tools to heighten their privileges to administrator level, along with employing tools conducive to network scanning. Commonly-used tools for these activities include Living Off the Land binaries (LOLbins), renowned for being executable files inherent to the operating system and less likely to trigger alarms.
Final Action for Ransomware Operators
The offender prepares to harvest and pilfer sensitive data, typically compressing it with utilities like 7-Zip or WinRAR before transmitting the data to servers controlled by the attacker using Remote Monitoring and Management tools or more tailored options like StealBit or Exabyte, developed by groups such as LockBit and BlackByte ransomware.
Potential Additional Measure for Ransomware Operators
If the motive is data theft or extortion, the operation concludes. However, if the objective is data encryption, the attacker must verify the ransomware within the environment by testing the delivery mechanisms and communication between the ransomware and the C2 server before initiating encryption across the network and notifying the victim of the breach, prompting them to remit the ransom.
Recurrent Vulnerabilities Exploited by Ransomware Operatives
Cisco Talos disclosed that three vulnerabilities in publicly accessible applications are frequently targeted by ransomware threat actors.
- CVE-2020-1472, also known as Zerologon, capitalizes on a flaw in the Netlogon Remote Protocol facilitating authentication bypass, allowing attackers to modify computer passwords within an Active Directory domain controller without authentication. This exploit is heavily favored by ransomware actors as it grants unauthorized network access.
- CVE-2018-13379, a vulnerability in Fortinet FortiOS SSL VPN, permits path traversal enabling attackers to retrieve system files via specially crafted HTTP packets. This technique might yield access to VPN session tokens, facilitating unauthenticated entry to the network.
- CVE-2023-0669, a vulnerability in GoAnywhere MFT, empowers attackers to execute arbitrary code on a server utilizing the GoAnywhere Managed File Transfer software. This constitutes the most recently flagged vulnerability in Cisco Talos’ report.
All of these vulnerabilities provide ransomware actors with initial entry points to manipulate systems for executing additional malicious payloads, embedding persistence, or facilitating lateral movements within compromised networks.
FOR MORE INSIGHTS: Cybersecurity’s Benefits and Best Practices offered by TechRepublic Premium
Significant TTPs of Fourteen Ransomware Collectives
Cisco Talos observed the TTPs employed by 14 of the most predominant ransomware groups based on their attack volume, customer impact, and distinctive behavior.
One significant discovery about the TTPs reveals that many of the leading groups prioritize establishing initial compromise and eluding defenses within their attack sequences.
Ransomware threat actors frequently obscure their malicious code by packing and compressing it and alter the systems registry to deactivate security alerts on the endpoint or server. They may also restrict certain recovery options for users.
The most common credential access approach highlighted by Cisco Talos researchers is dumping LSASS memory contents to extract plaintext passwords, hashed passwords, or authentication tokens stored in memory.
An emerging trend in C2 activities involves utilizing commercially accessible tools such as RMM applications. These applications are generally trusted within the environment and enable the attacker to blend in with corporate network traffic.
Ways to alleviate the ransomware threat
Primarily, it is crucial to implement patches and updates for all systems and software; this ongoing maintenance is essential to minimize the vulnerability of being exploited by a breach.
Enforce strict password guidelines and MFA. Ensure that each user sets complex and unique passwords, with MFA enforced to prevent unauthorized access to the targeted network by an attacker with valid credentials.
Adopt best practices to fortify all systems and environments. Disable unnecessary services and features to reduce the attack area. Also, decrease exposure to the internet by limiting the number of public-facing services as much as possible.
Segment networks using VLANs or comparable technologies. Isolate sensitive data and systems from other networks to thwart lateral movements by an attacker.
Monitor endpoints with a Security Information and Event Management system, and deploy Endpoint Detection and Response or Extended Detection and Response tools.
Disclaimer: I am employed by Trend Micro, however, the opinions expressed in this article are my own.





