Threat
activity
clusters
affiliated
with
the
Chinese
and
Russian
cybercriminal
ecosystems
have
been
observed
using
a
new
piece
of
malware
that’s
designed
to
load
Cobalt
Strike
onto
infected
machines.
Dubbed
SILKLOADER
by
Finnish
cybersecurity
company
WithSecure,
the
malware
leverages
DLL
side-loading
techniques
to
deliver
commercial
adversary
simulation
software.
The
development
comes
as
improved
detection
capabilities
against
Cobalt
Strike,
a
legitimate
post-exploitation
tool
used
for
red
team
operations,
is
forcing
threat
actors
to
seek
alternative
options
or
concoct
new
ways
to
propagate
the
framework
to
evade
detection.
“The
most
common
of
these
include
adding
complexity
to
the
auto-generated
beacon
or
stager
payloads
via
the
utilization
of
packers,
crypters,
loaders,
or
similar
techniques,”
WithSecure
researchers
said.
SILKLOADER
joins
other
loaders
such
as
KoboldLoader,
MagnetLoader,
and
LithiumLoader
that
have
been
recently
discovered
incorporating
Cobalt
Strike
components.
It
also
shares
overlaps
with
LithiumLoader
in
that
both
employ
the
DLL
side-loading
method
to
hijack
a
legitimate
application
with
the
goal
of
running
a
separate,
malicious
dynamic
link
library
(DLL).
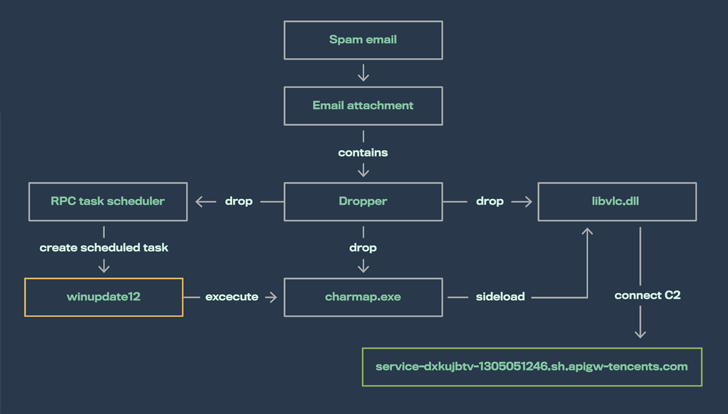
SILKLOADER
achieves
this
via
specially
crafted
libvlc.dll
files
that
are
dropped
alongside
a
legitimate
but
renamed
VLC
media
player
binary
(Charmap.exe).
WithSecure
said
it
identified
the
shellcode
loader
following
an
analysis
of
“several
human-operated
intrusions”
targeting
various
entities
spanning
a
wide
range
of
organizations
located
in
Brazil,
France,
and
Taiwan
in
Q4
2022.
Although
these
attacks
were
unsuccessful,
the
activity
is
suspected
to
be
a
lead-up
to
ransomware
deployments,
with
the
tactics
and
tooling
“heavily
overlapping”
with
those
attributed
to
the
operators
of
the
Play
ransomware.
In
one
attack
aimed
at
an
unnamed
French
social
welfare
organization,
the
threat
actor
gained
a
foothold
into
the
network
by
exploiting
a
compromised
Fortinet
SSL
VPN
appliance
to
stage
Cobalt
Strike
beacons.
“The
threat
actor
maintained
a
foothold
in
this
organization
for
several
months,”
WithSecure
said.
“During
this
time,
they
performed
discovery
and
credential
stealing
activities,
followed
by
deployment
of
multiple
Cobalt
Strike
beacons.”
But
when
this
attempt
failed,
the
adversary
switched
to
using
SILKLOADER
to
bypass
detection
and
deliver
the
beacon
payload.
That’s
not
all.
Another
loader
known
as
BAILLOADER,
which
is
also
used
to
distribute
Cobalt
Strike
beacons,
has
been
linked
to
attacks
involving
Quantum
ransomware,
GootLoader,
and
the
IcedID
trojan
in
recent
months.
BAILLOADER,
for
its
part,
is
said
to
exhibit
similarities
with
a
crypter
codenamed
Tron
that
has
been
put
to
use
by
different
adversaries
to
distribute
Emotet,
TrickBot,
BazarLoader,
IcedID,
Conti
ransomware,
and
Cobalt
Strike.
This
has
given
rise
to
the
possibility
that
disparate
threat
actors
share
Cobalt
Strike
beacons,
crypters,
and
infrastructure
provided
by
third-party
affiliates
to
service
multiple
intrusions
utilizing
different
tactics.
In
other
words,
SILKLOADER
is
likely
being
offered
as
an
off-the-shelf
loader
through
a
Packer-as-a-Service
program
to
Russian-based
threat
actors.
“This
loader
is
being
provided
either
directly
to
ransomware
groups
or
possibly
via
groups
offering
Cobalt
Strike/Infrastructure-as-a-Service
to
trusted
affiliates,”
WithSecure
said.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
“Most
of
these
affiliates
appear
to
have
been
part
of
or
have
had
close
working
relationships
with
the
Conti
group,
its
members,
and
offspring
after
its
alleged
shutdown.”
SILKLOADER
samples
analyzed
by
the
company
show
that
early
versions
of
the
malware
date
back
to
the
start
of
2022,
with
the
loader
exclusively
put
to
use
in
different
attacks
targeting
victims
in
China
and
Hong
Kong.
The
shift
from
East
Asian
targets
to
other
countries
such
as
Brazil
and
France
is
believed
to
have
occurred
around
July
2022,
after
which
all
SILKLOADER-related
incidents
have
been
attributed
to
Russian
cybercriminal
actors.
This
has
further
given
way
to
a
hypothesis
that
“SILKLOADER
was
originally
written
by
threat
actors
acting
within
the
Chinese
cybercriminal
ecosystem”
and
that
the
“loader
was
used
by
the
threat
actors
within
this
nexus
at
least
as
early
as
May
2022
till
July
2022.”
“The
builder
or
source
code
was
later
acquired
by
a
threat
actor
within
the
Russian
cybercriminal
ecosystem
between
July
2022
and
September
2022,”
WithSecure
said,
adding,
“the
original
Chinese
author
sold
the
loader
to
a
Russian
threat
actor
once
they
no
longer
had
any
use
for
it.”
Both
SILKLOADER
and
BAILLOADER
are
just
the
latest
examples
of
threat
actors
refining
and
retooling
their
approaches
to
stay
ahead
of
the
detection
curve.
“As
the
cybercriminal
ecosystem
becomes
more
and
more
modularized
via
service
offerings,
it
is
no
longer
possible
to
attribute
attacks
to
threat
groups
simply
by
linking
them
to
specific
components
within
their
attacks,”
WithSecure
researchers
concluded.
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.