ESET
discovered
a
stealthy
Unified
Extensible
Firmware
Interface
(UEFI)
bootkit
dubbed
BlackLotus
that
is
able
to
bypass
the
Secure
Boot
on
Windows
11.
Researchers
from
ESET
discovered
a
new
stealthy
Unified
Extensible
Firmware
Interface
(UEFI)
bootkit,
named
BlackLotus,
that
is
able
to
bypass
Secure
Boot
on
Windows
11.
Secure
Boot is
a
security
feature
of
the
latest
Unified
Extensible
Firmware
Interface
(UEFI)
2.3.1
designed
to
detect
tampering
with
boot
loaders,
key
operating
system
files,
and
unauthorized
option
ROMs by
validating
their
digital
signatures.
“Detections
are
blocked
from
running
before
they
can
attack
or
infect
the
system
specification.”
BlackLotus
is
the
first
UEFI
bootkit
that
is
able
to
bypass
the
security
feature
on
fully
up-to-date
Windows
11
systems.
The
BlackLotus
malware
is
a
UEFI
bootkit
that
is
available
for
sale
on
hacking
forums since
at
least
October
2022.
The
powerful
malware
is
offered
for
sale
at
$5,000,
with
$200
payments
per
new
updates.
Black
Lotus
is
written
in
assembly
and
C
and
is
only
80kb
in
size,
the
malicious
code
can
be
configured
to
avoid
infecting
systems
in
countries
in
the
CIS
region.
The
malware
supports
anti-virtualization,
anti-debugging,
and
code
obfuscation.
Black
Lotus
is
able
to
disable
security
solutions,
including
Hypervisor-protected
Code
Integrity
(HVCI),
BitLocker,
and
Windows
Defender.
The
rootkit
is
able
to
bypass
security
defenses
like
UAC
and
Secure
Boot,
it
is
able
to
load unsigned drivers
used
to
perform
a
broad
range
of
malicious
activities.
The
threat
is
very
stealthy,
it
can
achieve
persistence
at
the
UEFI
level
with
Ring
0
agent
protection.
Black
Lotus
supports
a
full
set
of
backdoor
capabilities,
it
could
be
also
used
to
potentially
target
IT
and
OT
environments.
Black
Lotus
is
bringing
APT
capabilities
to
malicious
actors
in
the
threat
landscape.
“Considering
this
tradecraft
used
to
be
relegated
to
APTs
like
the
Russian
GRU
and
APT
41
(China
nexus),
and
considering
prior
criminal
discoveries
we’ve
made
(e.g. Trickbot‘s #Trickboot module),
this
represents
a
bit
of
a
‘leap’
forward,
in
terms
of
ease
of
use,
scalability,
accessibility
and
most
importantly,
the
potential
for
much
more
impact
in
the
forms
of
persistence,
evasion
and/or
destruction.” wrote Scott
Scheferman
from
firmware
security
firm
Eclypsium.
ESET
researchers
reported
that
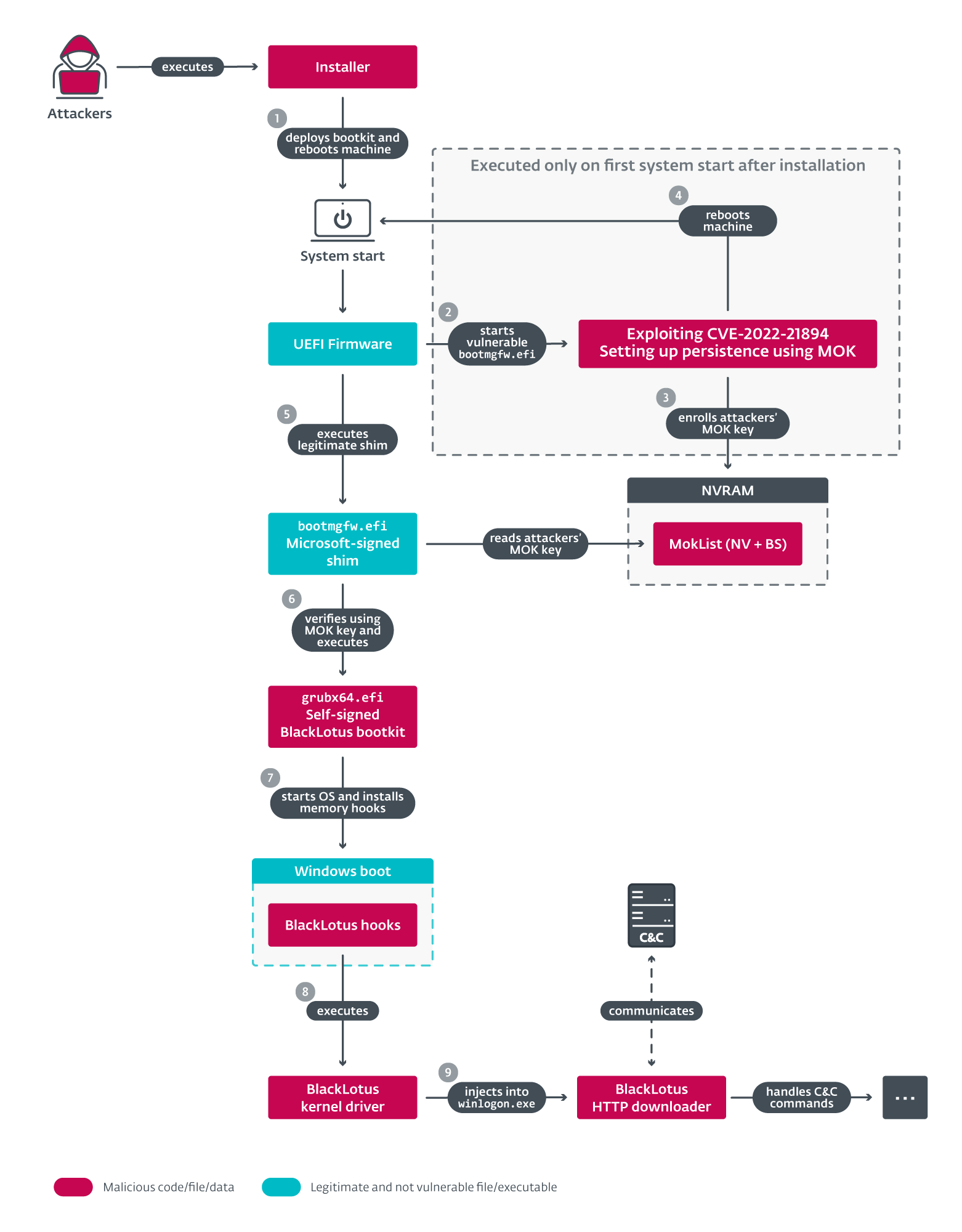
the
bootkit
exploits
the
vulnerability
CVE-2022-21894
to
bypass
UEFI
Secure
Boot
and
maintain
persistence.
This
is
the
first
publicly
known
bootkit
that
abuses
this
vulnerability
in
the
wild.
“Exploiting
CVE-2022-21894
to
bypass
the
Secure
Boot
feature
and
install
the
bootkit.
This
allows
arbitrary
code
execution
in
early
boot
phases,
where
the
platform
is
still
owned
by
firmware
and
UEFI
Boot
Services
functions
are
still
available.”
reads
the
analysis
published
by
the
experts.
“This
allows
attackers
to
do
many
things
that
they
should
not
be
able
to
do
on
a
machine
with
UEFI
Secure
Boot
enabled
without
having
physical
access
to
it,
such
as
modifying
Boot-services-only
NVRAM
variables.
And
this
is
what
attackers
take
advantage
of
to
set
up
persistence
for
the
bootkit
in
the
next
step. “
The
experts
pointed
out
that
despite
the
issue
was
addressed
by
Microsoft
in
January
2022,
its
exploitation
is
still
possible
as
the
affected, validly
signed binaries
have
still
not
been
added
to
the UEFI
revocation
list.
Upon
successful
installation
of
the
bootkit,
the
malicious
code
deploys
a
kernel
driver
and
an
HTTP
downloader,
used
for
C2
communication,
which
can
load
additional
user-mode
or
kernel-mode
payloads.
“Many
critical
vulnerabilities
affecting
security
of
UEFI
systems
have
been
discovered
in
the
last
few
years.
Unfortunately,
due
the
complexity
of
the
whole
UEFI
ecosystem
and
related
supply-chain
problems,
many
of
these
vulnerabilities
have
left
many
systems
vulnerable
even
a
long
time
after
the
vulnerabilities
have
been
fixed
–
or
at
least
after
we
were
told
they
were
fixed.”
“Many
critical
vulnerabilities
affecting
security
of
UEFI
systems
have
been
discovered
in
the
last
few
years,”
Smolár
said.
“Unfortunately,
due
the
complexity
of
the
whole
UEFI
ecosystem
and
related
supply-chain
problems,
many
of
these
vulnerabilities
have
left
many
systems
vulnerable
even
a
long
time
after
the
vulnerabilities
have
been
fixed
–
or
at
least
after
we
were
told
they
were
fixed.”
concludes
the
report.
“It
was
just
a
matter
of
time
before
someone
would
take
advantage
of
these
failures
and
create
a
UEFI
bootkit
capable
of
operating
on
systems
with
UEFI
Secure
Boot
enabled.
As
we
suggested
last
year
in
our RSA
presentation,
all
of
this
makes
the
move
to
the
ESP
more
feasible
for
attackers
and
a
possible
way
forward
for
UEFI
threats
–
the
existence
of
BlackLotus
confirms
this.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
UEFI)