Best 7 Cyber Threat Tracking Solutions as Examined by Specialists for 2024

Cyber threat tracking refers to a proactive security action taken to identify and eliminate possible risks on a network before they cause significant harm. To identify this kind of danger, security experts rely on cyber threat tracking tools. These tools are programs powered by sophisticated analytics, machine learning, and artificial intelligence to identify unusual patterns in a system’s network and endpoints. They utilize methods such as behavioral analytics, pattern recognition, statistical analysis, and AI/ML modeling.
With data from Statista showing that 72% of businesses worldwide experienced ransomware attacks in 2023, more companies are seeking cyber threat tracking solutions this year.
In this article, we present the top cyber threat tracking tools for 2024 and compare their characteristics, advantages, and limitations.
Comparison of Top Threat Tracking Solutions
Beneath is a table detailing the leading threat tracking solutions and how their features stack up against each other.
Splunk: Leading Choice

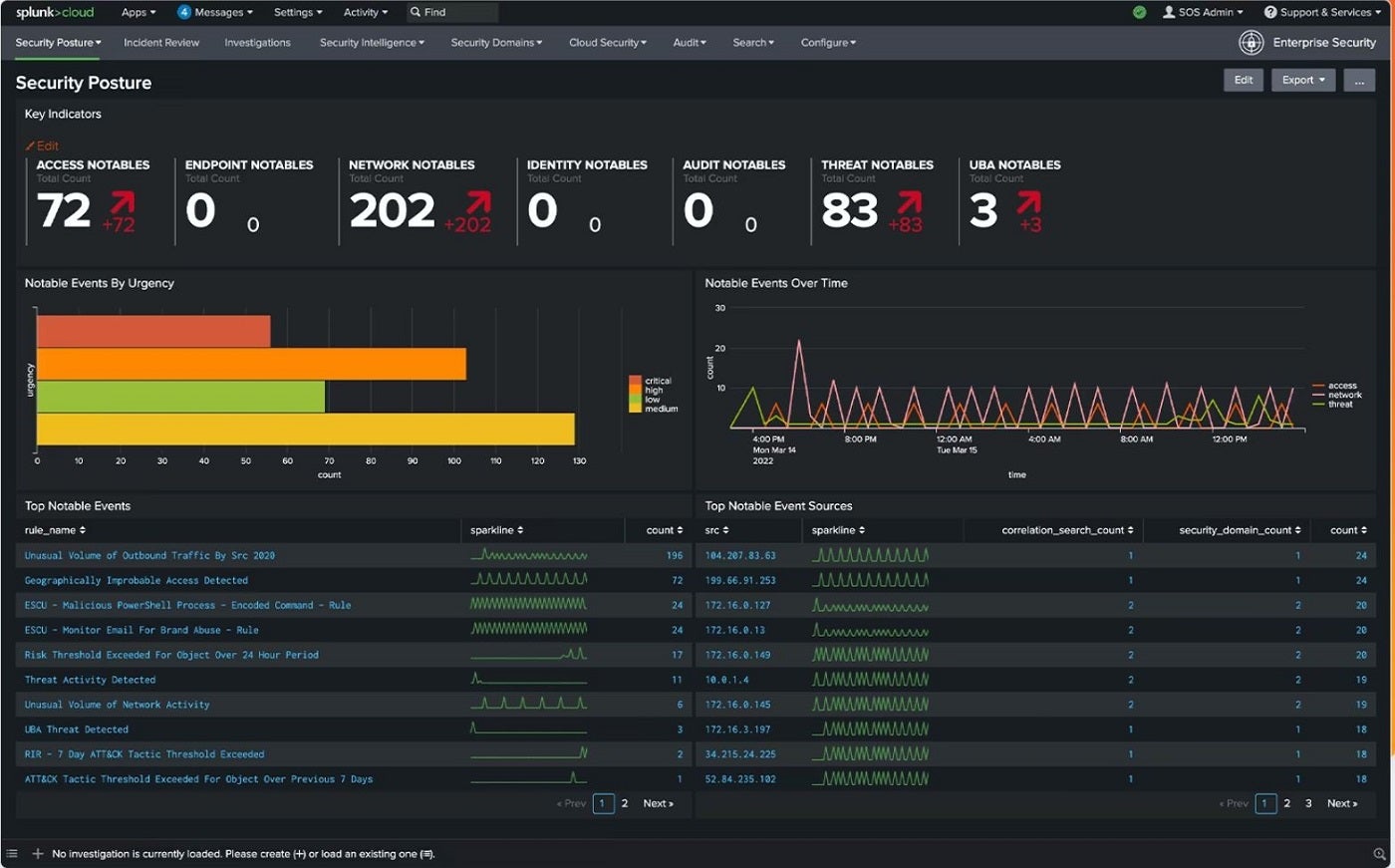
For the finest all-around cyber threat tracking tool, Splunk is the top recommendation. With cloud, on-premises, and hybrid options, Splunk as a security information and event management platform is a high-quality solution for proactively tackling hidden risks. It delivers robust data query capabilities that cater to extensive security operations like enterprise-level threat tracking.
SEE: 5 Best Endpoint Detection & Response Solutions for 2024 (TechRepublic)
Through Splunk, security teams can create threat-hunting queries, analysis routines, and automated defensive rules. An outstanding feature of Splunk’s SIEM capabilities is its speed, enabling quick threat detection for early-stage identification and resolution. It also offers advanced threat identification with approximately 1,400 detection frameworks and an open, adaptable data monitoring platform.
Reasons for Selecting Splunk
Splunk was chosen for its robust threat tracking capabilities, offering rapid detection and analysis regardless of the threat type. It is also ranked highly for its ability to handle tracking in large enterprises and settings. This is evident through its flexibility in cloud, on-premises, or hybrid threat tracking and comprehensive detection framework.
Pricing Details
This solution provides a 14-day trial period. For pricing, reach out to the vendor.
Key Features
- Integration across multiple platforms.
- Adaptable data monitoring platform that is open.
- Dashboard for incident review aiding in quick threat prioritization.
- Security posture dashboard and threat topology.
- Advanced threat detection capabilities.
- Alerting based on risk assessment.
Advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Provides threat intelligence management. | Unclear pricing structure. |
| Offers publicly accessible threat hunting guides. | |
| Allows customization of event prioritization. | |
| Various deployment options with flexibility. | |
| Frequent and prompt security content updates. | |
| Scalable threat detection and analysis for enterprises. |
VMware Carbon Black Endpoint: Ideal for offline and hybrid settings

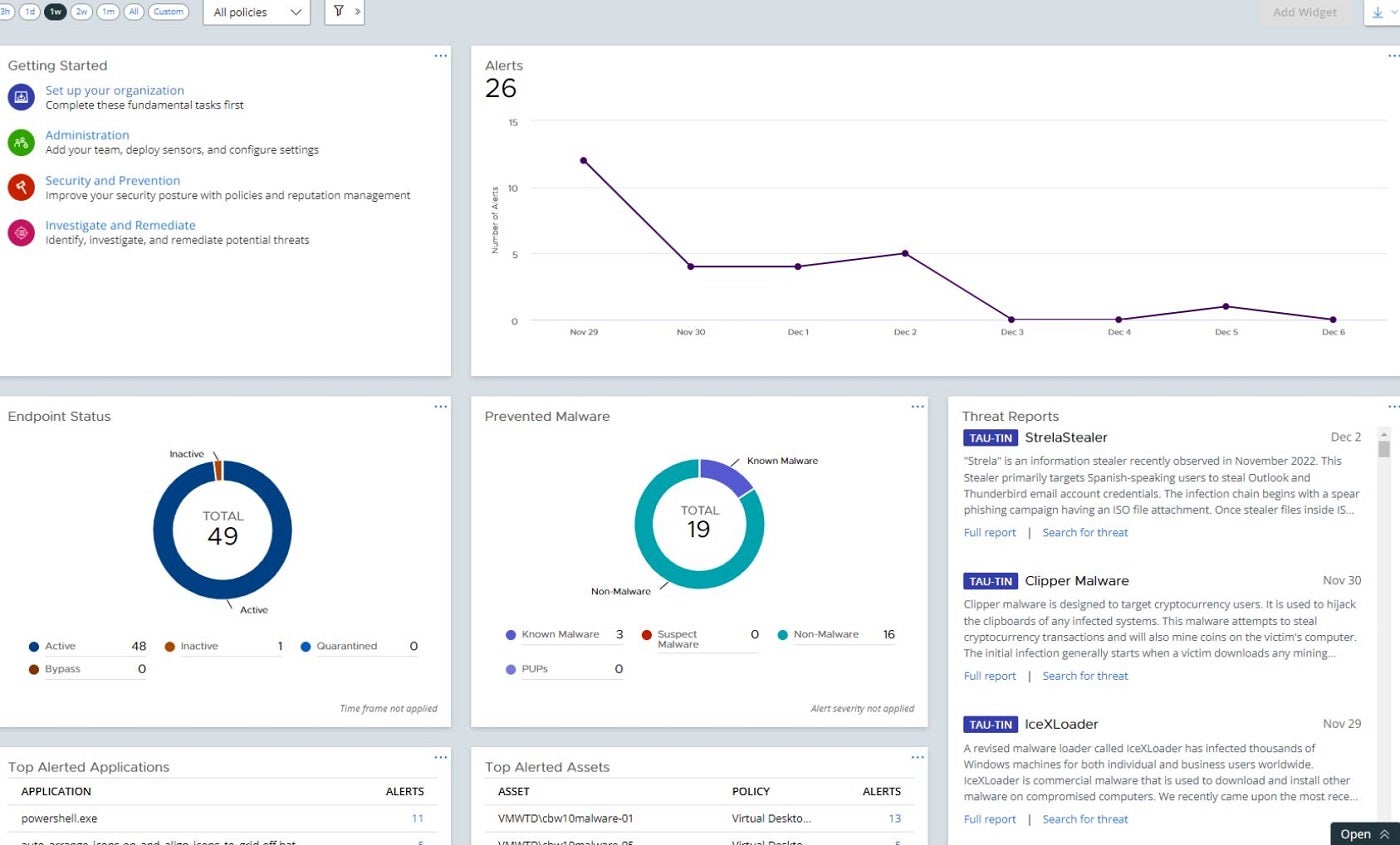
If you operate in a hybrid or offline environment, consider VMware Carbon Black Endpoint, created by VMware. It comprises a threat-hunting tool with behavioral endpoint detection and response (EDR), extended detection and response (XDR), and a modern antivirus solution (NGAV). These functions, combined with its machine learning capability, deliver advanced threat discovery. The tool continuously monitors and evaluates endpoint actions and behaviors to identify sophisticated threats.
VIEW: 4 Effective Threat Hunting Techniques to Counter Malicious Activities in 2024 (TechRepublic)
I admire how Carbon Black Endpoint can employ unsupervised machine learning models to spot irregularities that could signal malicious behavior throughout the cyber kill chain. Despite lacking audit and remediation in its Standard edition, I trust that organizations can achieve adequate EDR visibility in offline, hybrid, and disconnected situations.
Reasons for Selecting VMware Carbon Black Endpoint
I included VMware Carbon Black Endpoint on this list due to its EDR visibility that caters to offline, isolated, and disconnected surroundings.
Cost
Contact the vendor for pricing details.
Characteristics
- Advanced antivirus solution.
- Behavioral Endpoint Detection and Response (EDR).
- Anomaly identification.
- Enhanced endpoint and container tracking.
- Automated threat probing.
Advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Linkage with renowned security utilities like Splunk, LogRhythm, and Proofpoint. | Absence of audit and remediation in the standard variant. |
| Support for compliance and audit functionalities. | |
| Visibility of endpoints within and beyond the corporate network. | |
| Advanced Cloud Security with Predictive Capabilities. | |
| Reciprocal threat exchange among clients. |
CrowdStrike Falcon Overwatch: Great for Advanced Threat Detection
Top Choice for Advanced Threat Hunting

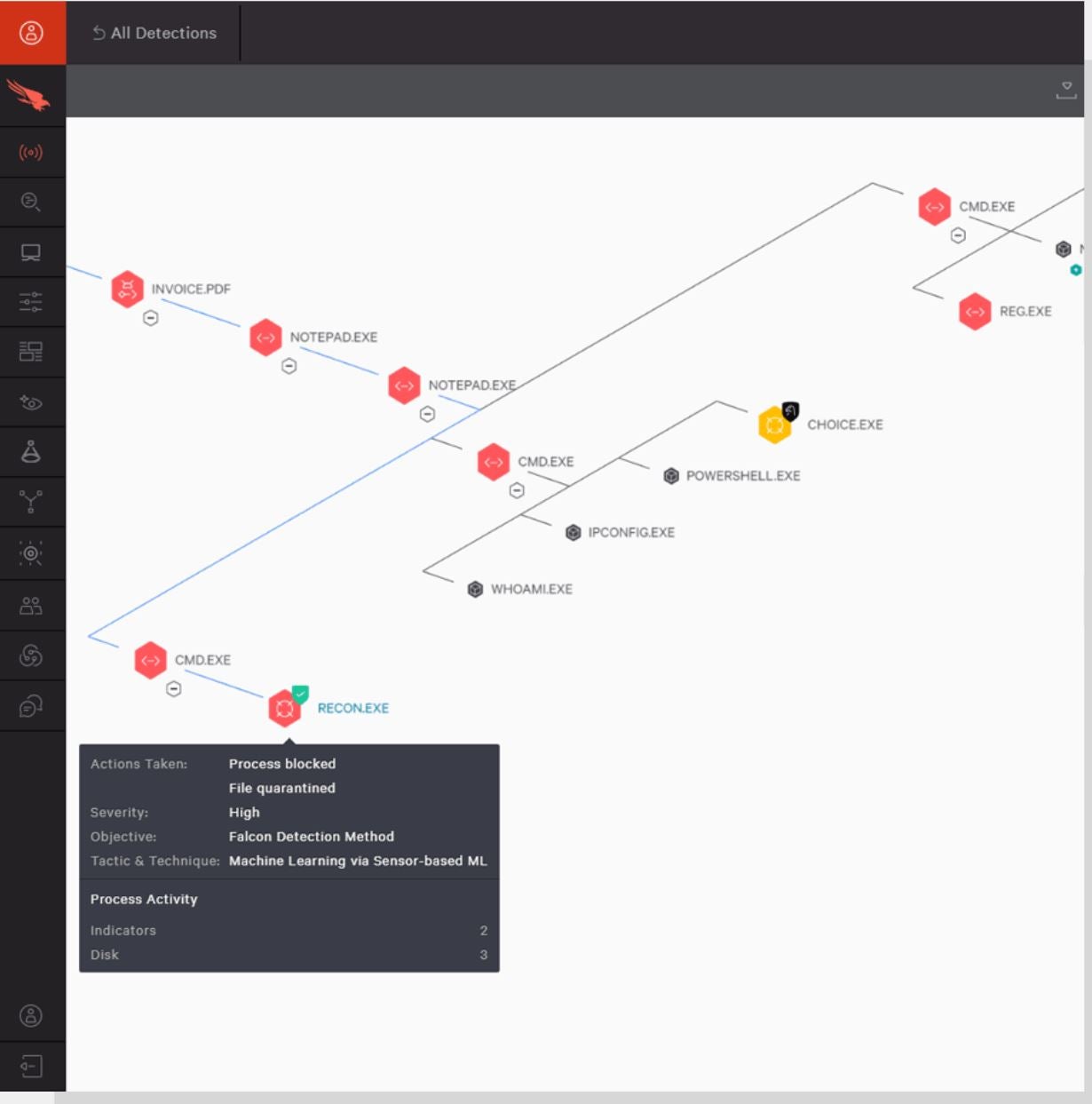
If your aim is to engage in advanced threat hunting, I highly recommend exploring CrowdStrike Falcon Overwatch equipped with advanced EDR and XDR. CrowdStrike’s Overwatch utilizes the SEARCH methodology to pursue and thwart threats. Using this methodology, CrowdStrike’s Overwatch harnesses cloud-scale data, insights from in-house analysts, and threat intelligence to sift through substantial data volumes for indications of intrusion or assault. In addition, its agile sensor monitors and gathers data from a wide array of endpoint occurrences uploaded to its cloud storage for examination.
VIEW: CrowdStrike vs Trellix (2024): What Are the Main Differences? (TechRepublic)
An exceptional feature of Overwatch is its threat graph, aiding cybersecurity analysts in identifying the sources of threats and their potential propagation. This can offer valuable insights for adopting preemptive security measures to avert future attacks.
Reasons behind my selection of CrowdStrike Falcon Overwatch
I opted for CrowdStrike Falcon Overwatch due to its focused approach to advanced threat hunting and automated response to threats, achieved through a fusion of advanced EDR, XDR, and exclusive functionalities.
Pricing
CrowdStrike Falcon Overwatch provides a 15-day trial and presents two packages: Falcon Overwatch and Falcon Overwatch Elite. Kindly reach out to the provider for a price estimate.
VIEW: CrowdStrike vs Sophos (2024): Which Solution Is Better for Your Business? (TechRepublic)
Notable Features
- Enhanced EDR and XDR.
- Enhanced visibility with Falcon USB Device control.
- Automated threat intelligence.
- Threat Graph.
- Firewall management.
Advantages and disadvantages
| Pros | Cons |
|---|---|
| Augmented threat alerts including context. | Exclusive threat hunting and investigation guidance limited to Falcon Overwatch Elite users. |
| Includes managed service options. | |
| Provides a 15-day trial period. | |
| XDR capabilities for advanced threat detection and response. | |
| Quarterly threat hunting reports. |
SolarWinds Security Event Manager: Best for centralized threat management

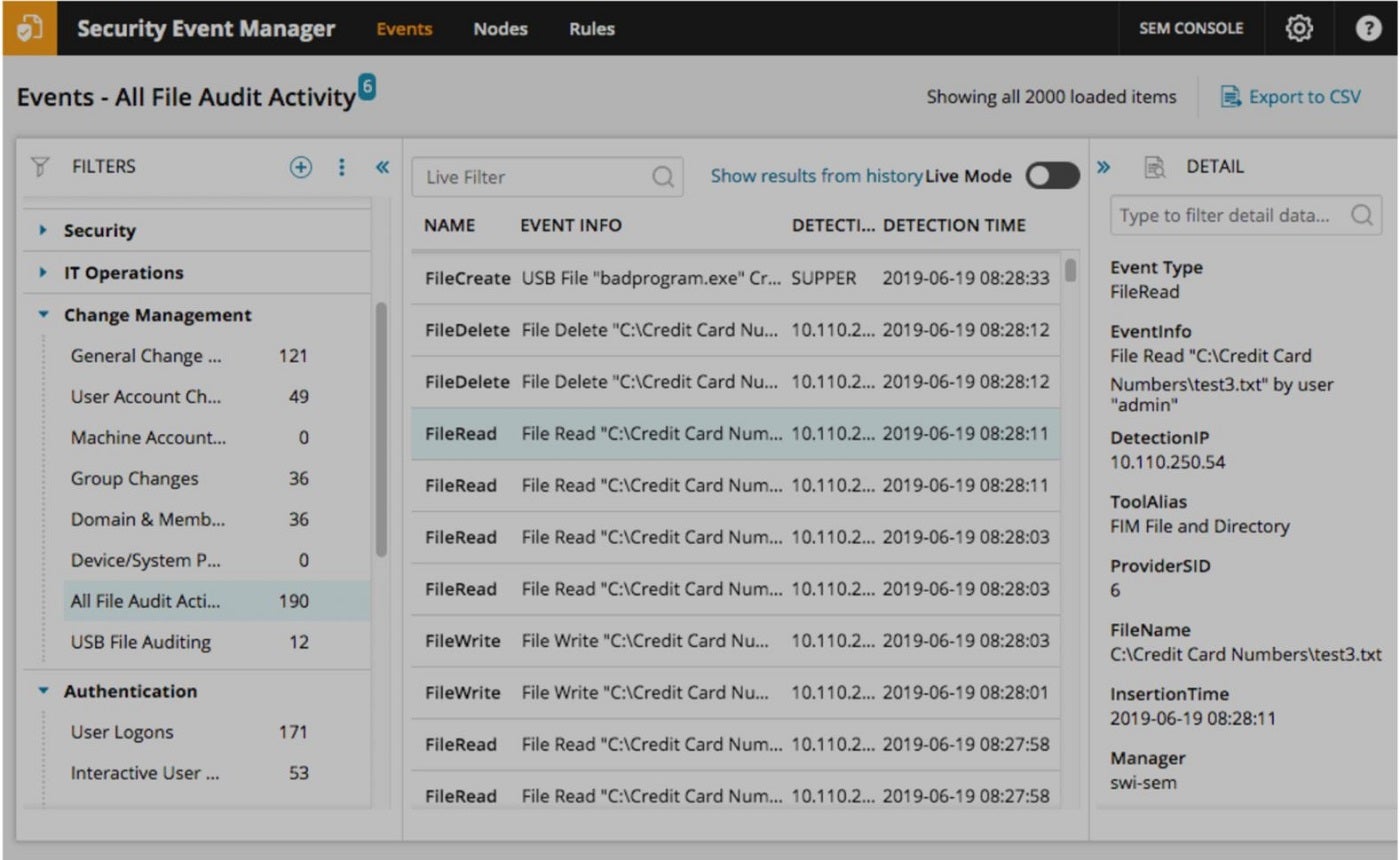
If individuals are seeking centralized threat management, the SolarWinds Security Event Manager proves to be a commendable choice. SolarWinds delivers its threat hunting functionalities through a fusion of real-time network performance metrics and data sourced from various outlets, such as the Simple Network Management Protocol (SNMP) and log records. The data acquired through SNMP enables the system to amass details about network devices, performance metrics, and other vital aspects in real-time.
VIEW: Top 8 Advanced Threat Protection Tools and Software for 2024 (TechRepublic)
By parsing and understanding log data, SEM can recognize patterns, anomalies, and potential threats. The central hub of SEM is a noteworthy inclusion as it empowers security teams to aggregate, scrutinize, and address security events arising from diverse security technologies like firewalls, intrusion detection systems, and endpoint protection solutions.
Reasons for Selecting SolarWinds Security Event Manager
I opted for SEM due to its centralized platform and seamless merging with various security technologies, thereby offering a streamlined approach to security management. This aids security professionals in gaining a comprehensive view of all potential threats or data that might assist in identifying.weak spots or potential vulnerabilities.
Cost
SolarWinds Event Manager provides options for subscription and perpetual licensing. Reach out to the supplier for a personalized estimate.
Characteristics
- Incorporated file integrity monitoring.
- Centralized collection and standardization of logs.
- Inclusion of tools for compliance reporting.
- Advanced analysis of pfSense firewall logs.
- Innovative software for security against advanced persistent threats (APTs).
Advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Provides real-time statistics on network performance. | Lacks a cloud-based version. |
| Logs audit events centrally for tracking security incidents. | |
| Enhanced security, real-time monitoring, and advanced troubleshooting with the pfSense firewall log analyzer. | |
| Integration with diverse security technologies for enhanced visibility. | |
| Offers detailed analysis of log entries to improve threat detection. |
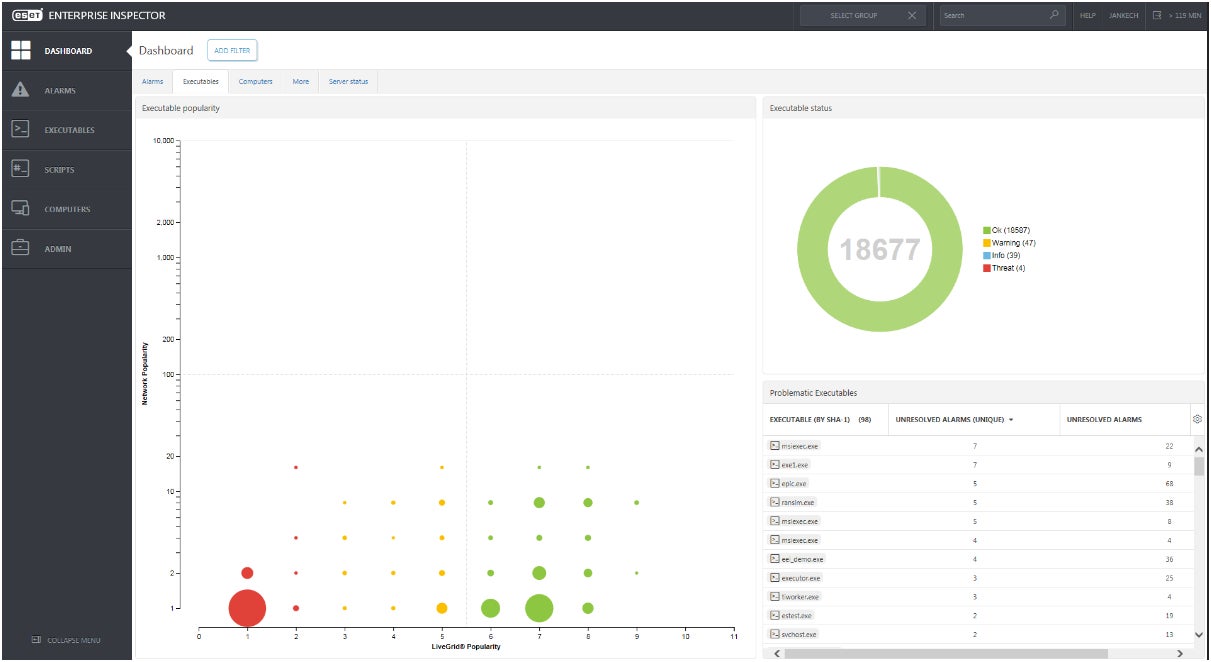
ESET Enterprise Inspector: Optimal for tandem cyber threat pursuit service

If your organization is interested in cyber threat pursuit services alongside a dedicated software tool, my recommendation would be ESET Enterprise Inspector. Enterprise Inspector, an EDR tool by ESET, is specifically designed for real-time examination of endpoint data and identification of persistent cyber threats. Its EDR capability allows re-scanning of entire event databases, making it perfect for historical pursuit of threats. This also facilitates the easy identification of new indicators of compromise as threat hunters tweak detection rules while scanning the database.
I particularly appreciate ESET’s provision of their own ESET Threat Hunting service, in complement with ESET Enterprise Inspector. This is perfect for businesses that lack the workforce or specialized security personnel for undertaking cyber threat pursuit.
Reasons for Choosing ESET Inspector
ESET Inspector is included in this compilation due to its dedicated cyber threat pursuit service together with the EDR functionality of ESET Enterprise Inspector. I believe this serves as an excellent solution for smaller enterprises that lack sizable IT or security teams but still desire to leverage advanced cyber threat pursuit capabilities.
Pricing
It is advisable to engage with ESET’s Sales team for customized pricing details and a formal quotation.
Characteristics
- Detection based on behavior and reputation.
- Automated capabilities for hunting down threats.
- Option for a dedicated cyber threat pursuit service.
- Defense against attacks that are file less.
- Alerts that can be customized.
Advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Easily modifiable detection rules. | Possibly demanding on older systems. | On-cloud or on-site deployment options. |
| Ideal for enterprises with limited security knowledge. | |
| Merges with other ESET products for synchronized reaction. | |
| Smooth implementation process. |
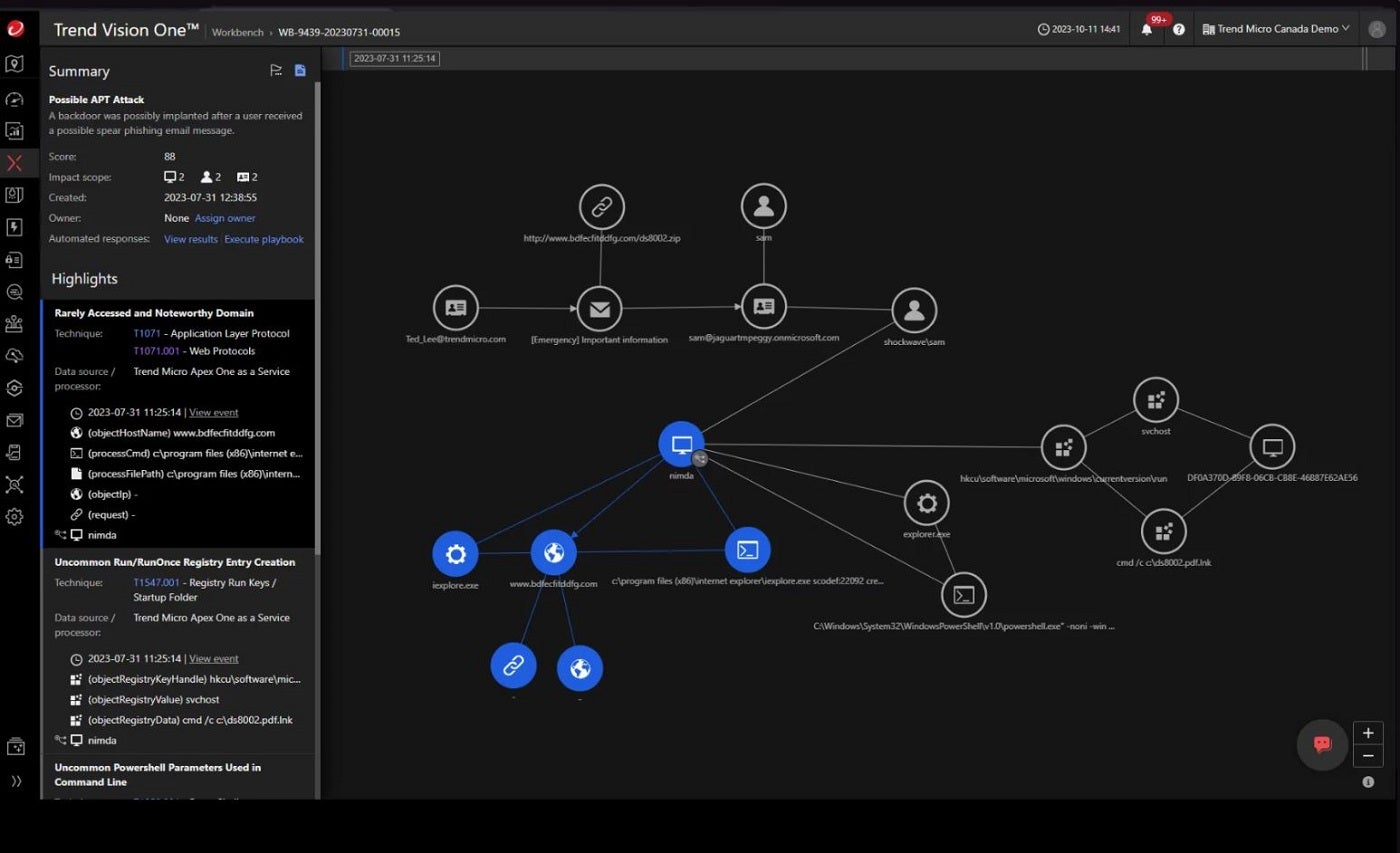
Trend Micro Managed XDR: Ideal for specialized SOC assistance

If you require a service with dedicated SOC assistance, I recommend exploring Trend Micro Managed XDR. Its security service provides continuous 24/7 monitoring and analysis and is distinguished by its capability to correlate information from a broad array of sources, such as email, endpoint, server, cloud, workload, and network.
I applaud Trend Micro for this comprehensive approach, as it bolsters threat investigation and offers deeper insight into the origin and distribution of targeted attacks. The solution persistently scans for signs of compromise or attack, including those communicated via US-CERT and third-party notifications, ensuring a proactive stance in threat investigation.
Another notable aspect is how Managed XDR furnishes specialized assistance for Security Operations Center (SOC) teams, diminishing the time required to recognize, scrutinize, and counter threats. As a component of Trend Service One, it encompasses premium support and incident response services, amplifying its worth throughout the product.
Reasons for Selecting Trend Micro Managed XDR
I opted for Trend Micro Managed XDR due to its around-the-clock support for Security Operations Center (SOC) teams and its threat exploration features that enhance detection and response time.
Pricing Details
Trend Micro Managed XDR provides a no-obligation 30-day trial. Reach out to the provider for pricing information.
Characteristics
- Endpoint spotting and response capabilities.
- Continuous analysis and monitoring.
- Advanced threat intelligence system.
- Comprehensive detection and response methods.
- Enhanced security analytics.
Advantages and disadvantages
| Strengths | Drawbacks |
|---|---|
| Tailored assistance for SOC and IT security teams. | Absence of on-premises alternative. |
| Includes server and email safeguarding features. | |
| Preemptive threat tracking for sophisticated risks. | |
| Identifies threats and auto-generates IoCs to prevent future attacks. | |
| Produces threat alerts and detailed incident assessments. |
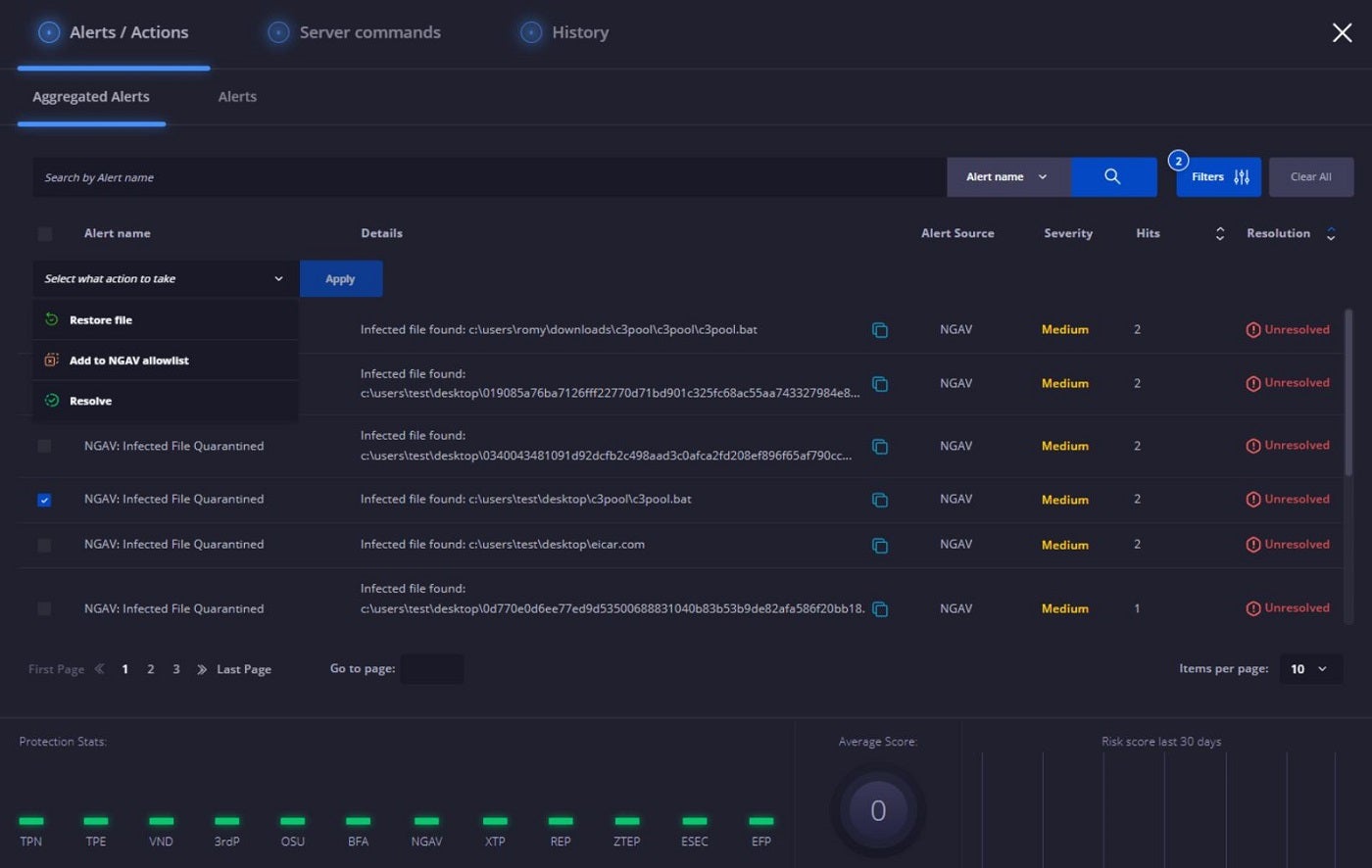
Heimdal Threat Hunting and Action Center: Ideal for swift single-command threat control

For effortless, single-command control of threats, I endorse Heimdal Threat Hunting and Action Center. The threat detection and recognition feature of Heimdal equips SecOps teams and IT admins with tools to identify and supervise unusual activities across devices and networks. Utilizing its advanced XTP engine, the Heimdall suite, and the MITRE ATT&CK framework, this platform showcases relevant data pertaining to endpoints for identifying network-level threats.
Users acquire insights through risk evaluations and forensic analysis, enhancing their grasp of potential risks. I personally value the continuous scanning by the XTP engine — adding a tactical component to threat identification and monitoring. It further allows for prompt corrective actions with a single instruction wherever threats are detected.
Reasons for Opting for Heimdal Threat Hunting and Action Center
To me, Heimdal stands out due to its one-click execution of functionalities like scanning, isolating, and quarantining, along with comprehensive incident examinations supported by its Action Center.
Price Details
Request a quotation from the provider.
Characteristics
- Advanced antivirus, firewall, and mobile device management (MDM) operations.
- Incident examination and management functionalities.
- Tracking and monitoring of activities.
- XTP Engine and MITRE ATT&CK framework integrations.
- Quarantine capabilities.
Advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Offers a centralized list of the identified threats. | Lack of online price information. |
| Real-time monitoring of threats and alerts provided. | |
| Enables quick reporting and statistical analysis. | |
| Allows for single-command remediation through the action center. | |
| Provides a unified perspective for intelligence, hunting, and response. | |
Key Elements of Cyber Threat Hunting Tools
From log inspection and proactive threat detection to information exchange and sharing intelligence, cyber threat hunting solutions can be equipped with multiple characteristics that differentiate them from conventional security monitoring tools. Below are essential attributes that I believe every threat-hunting tool must possess.
Data aggregation and examination
Tools for hunting threats collect and consolidate vast datasets from diverse origins like logs, events, endpoint telemetry, and network traffic. Using advanced analytics and machine learning, they identify unusual patterns and aberrations. These solutions improve their comprehension of potential threats by evaluating or analyzing alerts from SIEM systems and Intrusion detection systems (IDS). They scrutinize the information gathered from firewalls, IDS, DNS, file and user data, antivirus solutions, and other security devices to gain better insight into what should be considered as potential threats and the most efficient remediation methods.
Proactive discovery and identification of threats
This functionality aids security analysts in exploring and probing extensive data amassed from various sources. The advanced search and query language support empowers them to search, filter, and query the data. Security teams can refine and customize their searches as per specific organizational requirements to extract details such as time ranges, specific IP addresses, user accounts, or activity types. A crucial aspect of this feature is its ability to conduct real-time analysis by querying live data streams for swift identification of ongoing threats and historical data analysis to uncover past occurrences or patterns that might have initially escaped notice.
SEE: Reasons Why Your Business Requires Cybersecurity Awareness Training (TechRepublic Premium)
Cooperation and sharing of intelligence
Threat hunting transcends individual efforts because processing individually collected data is limiting. Effective collaboration and sharing of intelligence among organizations, security teams, and industry peers are crucial, and this necessitates integrating sharable threat intelligence feeds into threat hunting tools. The sharing of threat intelligence, tactics, techniques, and procedures (TTPs) eases threat hunting and remediation across a variety of organizations.
Analysis of behavior
Threat-hunting tools leverage behavioral analysis to grasp and interpret normal behavior patterns of users and systems. They employ methods like user and entity behavior analytics (UEBA), machine learning algorithms, and continuous monitoring to identify irregularities, provide context, and enable early threat detection. This element also helps reduce false alarms and boosts proactive identification and response to security hazards.
Automated reaction
This feature prioritizes alerts based on preset criteria, guaranteeing immediate attention to critical or identified threats. It involves dynamic playbooks, integration with security orchestration platforms, and actions such as incident containment and isolation, user account remediation, and alert ordering. Through automated responses, organizations can diminish dwell time, streamline incident response, maintain compliance with security policies, and ensure enhanced protection of networks and systems against security risks and threats.
Selecting the Optimal Cyber Threat-Hunting Tool for My Enterprise
Choosing the most suitable cyber threat-hunting tool for individual or business requirements revolves around various factors, including personal or business objectives, integration of the tool with the existing security infrastructure, and budget constraints. These seven tools serve as excellent options depending on individual/business necessities.
For instance, if a dedicated threat hunting service on top of the threat hunting solution is necessary, a tool like ESET Enterprise Inspector would be the ideal choice. Conversely, if the aim is a comprehensive single-action remediation encompassing scanning, quarantine, isolation, and detailed incident investigation, then the Heimdal Threat Hunting and Action Center emerges as the top option. This principle applies to other tools as each boasts a unique approach to threat hunting and remediation.
Nonetheless, the effectiveness of any tool hinges on its seamless integration into an organization’s existing infrastructure and security protocols. It is always advisable to assess these tools in relation to the specific needs and challenges faced by your organization.
Methodology of Evaluation
For this evaluation, I took into account crucial features of threat-hunting solutions, the varied methodologies employed by each tool to detect threats, their remediation procedures, integration capabilities with current systems, and the availability of personalized support from vendors. Information was gathered from the websites of different vendors and review platforms like Gartner to gain deeper insights into each tool. Developer reputation and industry standing were also considered in the assessment.




