Experts
warn
of
phishing
attacks
that
are
combining
the
use
of
compromised
Microsoft
365
accounts
and
.rpmsg
encrypted
emails.
Trustwave
researchers
have
observed
threat
actors
using encrypted
RPMSG
attachments
sent
via
compromised
Microsoft
365
accounts
in
a
phishing
campaign
aimed
at
stealing
Microsoft
credentials.
RPMSG
files
are used
to
deliver
e-mails
with
Rights-Managed
Email
Object
Protocol
enabled.
This
protocol
controls
e-mail
access
and
usage
permissions.
Instead
of
a
plain
text,
e-mails
via
RPMSG
files
are
sent
with
content
encrypted
and
stored
as
encrypted
file
attachment.
The
recipients
can
read
the
encrypted
messages
only
after
being
authenticated
with
their
Microsoft
account
or
obtaining
a
one-time
passcode.
The
attacks
analyzed
by
Trustwave
commenced
with
a
phishing
message
originating
from
a
compromised
Microsoft
365
account,
in
this
case
from
the
payments
processing
company
Talus
Pay.
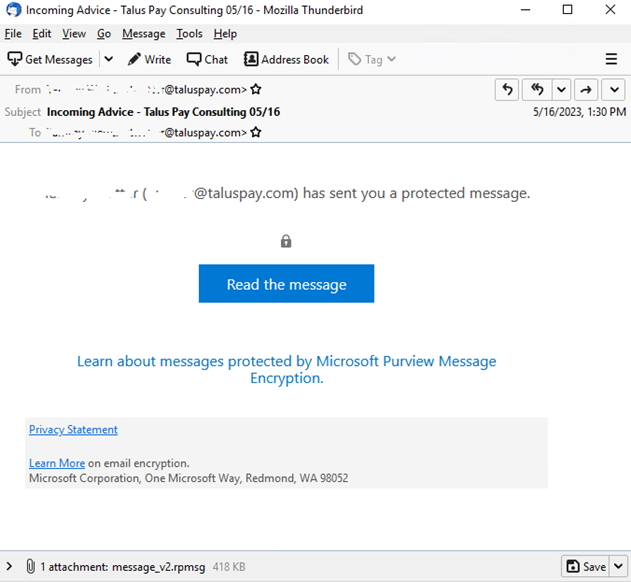
“The
recipients
were
users
in
the
billing
department
of
the
recipient
company.
The
message
shows
a
Microsoft
encrypted
message.
In
the
email,
the
From:
and
To:
email
address
displayed
in
the
header
were
the
same,
but
the
message
was
delivered
to
various
third
party
recipients.”
reads
the
report
published
by
Trustwave.
The
message
attempts
to
trick
recipients
into
clicking
the
“Read
the
message”
button
to
decrypt
the
protected
message.
Upon
clicking
the
link,
the
recipients
are
redirected
to
an
Office
365
webpage
with
a
request
to
sign
into
their
Microsoft
account.
Once
authenticated
with
the
Microsoft
service,
the
recipients
are
redirected
to
a
page
displaying
the
attackers’
phishing
email.
The
message
contains
a
“Click
here
to
Continue”
button
that
points
to
a
fake
SharePoint
document
hosted
on
Adobe’s
InDesign
service.

If
the
recipient
clicks
on
“Click
Here
to
View
Document”
on
the
Adobe
document,
he
will
be
redirected
to
the
final
page,
which
resembles
the
domain
of
the
original
sender,
Talus
Pay.
However,
this
landing
page
has
a
.us
TLD
and
was
registered
recently
on
May
16,
2023.
The
page
only
displays
a
“Loading…Wait”
message
in
the
title
bar,
while
in
the
background
it
relies
on
a
Javascript
that
collects
system
information.
The
script
uses
the
open
source
FingerprintJS
library
to
collect
recipient’s
data,
including
visitor
ID,
connect
token
(hardcoded
from
the
configuration),
connect
hash
(hardcoded
from
the
configuration),
video
card
renderer
information,
system
language,
device
memory,
hardware
concurrency
(#
of
processor),
browser
plugins
installed,
browser
window
size,
orientation,
and
screen
resolution,
and
OS
architecture.
Once
the
script
has
completed
the
collection
data,
the
page
will
show
a
fake
cloned
Microsoft
365
login
form.
Once
the
recipient
has
provided
its
credentials,
they
will
be
sent
to
a
remote
server
under
the
control
of
the
attackers.
“These
phishing
attacks
are
challenging
to
counter.
They
are
low
volume,
targeted,
and
use
trusted
cloud
services
to
send
emails
and
host
content
(Microsoft
and
Adobe).
The
initial
emails
are
sent
from
compromised
Microsoft
365
accounts
and
appear
to
be
targeted
towards
recipient
addresses
where
the
sender
might
be
familiar.”
concludes
the
report.
“The
use
of
encrypted
.rpmsg
messages
means
that
the
phishing
content
of
the
message,
including
the
URL
links,
are
hidden
from
email
scanning
gateways.
The
only
URL
link
in
the
body
of
the
message
points
to
a
Microsoft
Encryption
service.”
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, RPMSG
files)











