
A
possible
Chinese
attack
campaign
on
compromised
unpatched
SonicWall
SMA
edge
devices
stayed
undetected
since
2021
and
could
persist
even
through
firmware
updates.

ArtemisDiana/Adobe
Stock
As
reported
by
a
new
Mandiant
research
document,
a
new
malware
is
made
of
several
bash
scripts
and
a
single
Executable
and
Linkable
Format
(ELF)
binary
file
identified
as
a
TinyShell
backdoor
variant.
Tinyshell
is
a
publicly
available
tool
used
by
several
threat
actors
(Figure
A).
Figure
A
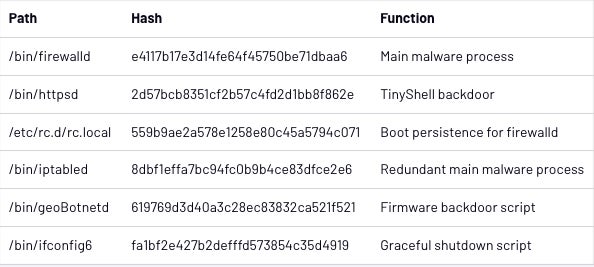
Mandiant.
List
of
malware
files
used
in
the
attack.
The
main
malware
process
is
a
file
called
“firewalld,”
which
executes
the
TinyShell
backdoor
with
parameters
that
allow
it
to
provide
a
reverse
shell
to
the
threat
actor.
The
reverse
shell
calls
a
C2
server
at
a
time
and
day
provided
by
the
script.
If
no
IP
address
is
provided
when
calling
the
TinyShell
binary,
it
embeds
a
hardcoded
IP
address
to
reach.
A
copy
of
the
“firewalld”
file
called
“iptabled”
was
altered
to
ensure
continuity
of
the
primary
malware
in
case
of
a
crash
or
termination.
The
two
scripts
were
set
up
to
activate
one
another
in
case
the
other
wasn’tt
already
running,
which
created
a
backup
instance
of
the
primary
malware
process
and
thereby
enhanced
its
resilience.
The
“firewalld”
process
is
launched
at
boot
time
by
a
startup
script
named
“rc.local”
intended
to
facilitate
an
attacker’s
prolonged
access.
A
file
named
“ifconfig6”
is
also
used
to
increase
stability.
The
main
“firewalld”
process
adds
a
small
patch
to
a
legitimate
SonicWall
binary
named
“firebased,”
which
replaces
a
shutdown
string
with
a
call
to
the
“ipconfig6”
script.
Mandiant
researchers
suspect
that
attackers
encountered
issues
when
the
“firebased”
script
was
shutting
down
the
instance
and
decided
to
create
a
small
script
to
patch
it.
Once
everything
is
set,
the
final
goal
of
the
malware
is
to
routinely
execute
a
SQL
command
to
grab
the
hashed
credentials
of
all
logged
in
users.
The
attacker
could
then
retrieve
those
hashes
to
crack
them
offline.
Firmware
updates
modified
A
bash
script
named
“geoBotnetd”
found
on
an
infected
device
checks
every
10
seconds
for
a
firmware
upgrade
to
appear
in
/cf/FIRMWARE/NEW/INITRD.GZ.
If
that’s
the
case,
the
script
will
backup
the
file,
unzip
it,
mount
it,
and
then
copy
over
the
whole
package
of
malware
files.
It
also
adds
a
backdoored
root
user
named
“acme”
to
the
system.
The
malware
then
rezips
it
all
and
puts
it
back
in
place.
This
technique,
although
not
very
sophisticated,
shows
how
motivated
the
attackers
are
to
keep
their
access
long-term,
because
a
solid
knowledge
of
the
firmware
upgrade
process
is
necessary
to
create
and
deploy
such
a
technique.
Mandiant
researchers
indicate
that
this
technique
is
consistent
with
another
attack
campaign
they
have
analyzed
that
supported
key
Chinese
government
priorities.
A
long
running
campaign
for
cyber
espionage
purposes
While
the
primary
vector
of
infection
stays
unknown
in
this
attack
campaign,
Mandiant
researchers
indicate
that
the
malware
or
a
predecessor
of
it
was
likely
deployed
in
2021
and
that
the
threat
actor
probably
retained
access,
even
through
multiple
firmware
updates.
Because
the
sole
purpose
of
the
malware
is
to
steal
user
credentials,
it
is
strongly
suspected
that
the
attack
campaign
follows
cyber
espionage
goals.
Mandiant
insists
on
the
fact
that
developing
malware
for
a
managed
appliance
is
no
trivial
task,
as
vendors
do
not
generally
offer
direct
access
to
the
operating
system
or
even
to
the
filesystem
of
such
devices.
This
makes
it
harder
to
develop
exploits
and
malware
for
those
devices.
How
to
protect
from
this
threat
For
this
particular
attack,
SonicWall
urges
SMA100
customers
to
upgrade
to
version
10.2.1.7
or
higher.
The
upgrade
includes
hardening
enhancements
such
as
File
Integrity
Monitoring
(FIM)
and
anomalous
process
identification.
On
a
larger
scale,
protecting
edge
devices
from
compromise
requires
a
multi
layered
approach
that
includes
both
physical
and
software
security
measures.
In
addition,
educate
employees
on
cybersecurity
best
practices,
such
as
identifying
phishing
emails
and
avoiding
suspicious
websites
or
downloads.
While
the
initial
infection
vector
isn’t
known,
it’s
highly
possible
that
it
might
have
been
phishing
emails.
Disclosure:
I
work
for
Trend
Micro,
but
the
views
expressed
in
this
article
are
mine.











