The
threat
actor
known
as
Asylum
Ambuscade
has
been
observed
straddling
cybercrime
and
cyber
espionage
operations
since
at
least
early
2020.
“It
is
a
crimeware
group
that
targets
bank
customers
and
cryptocurrency
traders
in
various
regions,
including
North
America
and
Europe,”
ESET
said
in
an
analysis
published
Thursday.
“Asylum
Ambuscade
also
does
espionage
against
government
entities
in
Europe
and
Central
Asia.”
Asylum
Ambuscade
was
first
documented
by
Proofpoint
in
March
2022
as
a
nation-state-sponsored
phishing
campaign
that
targeted
European
governmental
entities
in
an
attempt
to
obtain
intelligence
on
refugee
and
supply
movement
in
the
region.
The
goal
of
the
attackers,
per
the
Slovak
cybersecurity
firm,
is
to
siphon
confidential
information
and
web
email
credentials
from
official
government
email
portals.
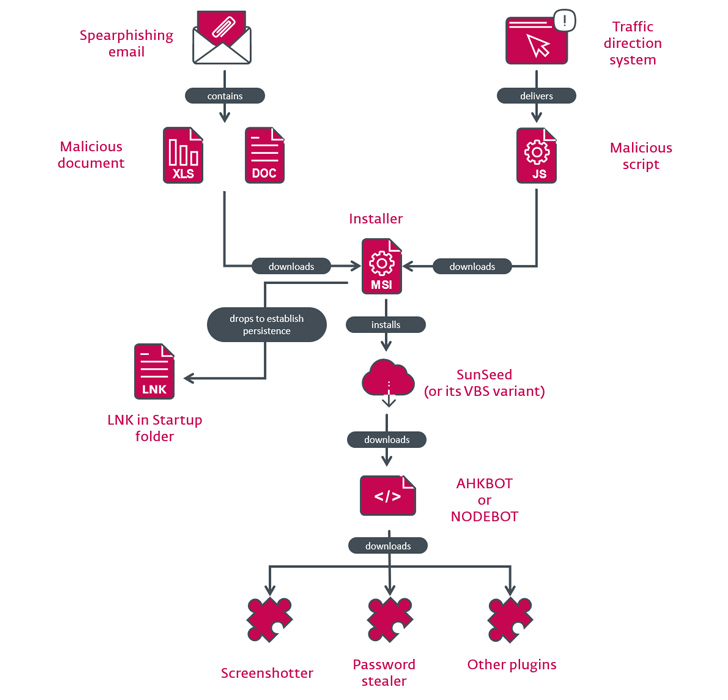
The
attacks
start
off
with
a
spear-phishing
email
bearing
a
malicious
Excel
spreadsheet
attachment
that,
when
opened,
either
exploits
VBA
code
or
the
Follina
vulnerability
(CVE-2022-30190)
to
download
an
MSI
package
from
a
remote
server.
The
installer,
for
its
part,
deploys
a
downloader
written
in
Lua
called
SunSeed
(or
its
Visual
Basic
Script
equivalent)
that,
in
turn,
retrieves
an
AutoHotkey-based
malware
known
as
AHK
Bot
from
a
remote
server.
What’s
notable
about
Asylum
Ambuscade
is
its
cybercrime
spree
that
has
claimed
over
4,500
victims
across
the
world
since
January
2022,
with
a
majority
of
them
located
in
North
America,
Asia,
Africa,
Europe,
and
South
America.
“The
targeting
is
very
wide
and
mostly
includes
individuals,
cryptocurrency
traders,
and
small
and
medium
businesses
(SMBs)
in
various
verticals,”
ESET
researcher
Matthieu
Faou
said.
While
one
aspect
of
the
attacks
is
designed
to
steal
cryptocurrency,
the
targeting
of
SMBs
is
likely
an
attempt
to
monetize
the
access
by
selling
it
to
other
cybercriminal
groups
for
illicit
profits.
The
compromise
chain
follows
a
similar
pattern
barring
the
initial
intrusion
vector,
which
entails
the
use
of
a
rogue
Google
Ad
or
a
traffic
direction
system
(TDS)
to
redirect
potential
victims
to
a
bogus
website
delivering
a
malware-laced
JavaScript
file.
UPCOMING
WEBINAR
🔐
Mastering
API
Security:
Understanding
Your
True
Attack
Surface
Discover
the
untapped
vulnerabilities
in
your
API
ecosystem
and
take
proactive
steps
towards
ironclad
security.
Join
our
insightful
webinar!
The
attacks
have
also
made
use
of
a
Node.js
version
of
AHK
Bot
codenamed
NODEBOT
that’s
then
used
to
download
plugins
responsible
for
taking
screenshots,
plundering
passwords,
gathering
system
information,
and
installing
additional
trojans
and
stealers.
Given
the
almost
identical
attack
chains
across
cybercrime
and
espionage
efforts,
it’s
suspected
that
“Asylum
Ambuscade
is
a
cybercrime
group
that
is
doing
some
cyber
espionage
on
the
side.”
The
overlaps
also
extend
to
another
activity
cluster
dubbed
Screentime
that’s
known
to
target
companies
in
the
U.S.
and
Germany
with
bespoke
malware
designed
to
steal
confidential
information.
Proofpoint
is
tracking
the
threat
actor
under
the
name
TA866.
“It
is
quite
unusual
to
catch
a
cybercrime
group
running
dedicated
cyberespionage
operations,”
Faou
said,
making
it
somewhat
of
a
rarity
in
the
threat
landscape.