Adhesive Werewolf goes after the aviation field in Russia and Belarus

Morphisec experts witnessed a malevolent actor, known as Adhesive Werewolf, focusing on organizations in Russia and Belarus.
Adhesive Werewolf, a malevolent actor initially identified in April 2023, started by targeting public entities in Russia and Belarus. The group has broadened its reach to different sectors including a pharmaceutical firm and a Russian research institute specializing in microbiology and vaccine development.
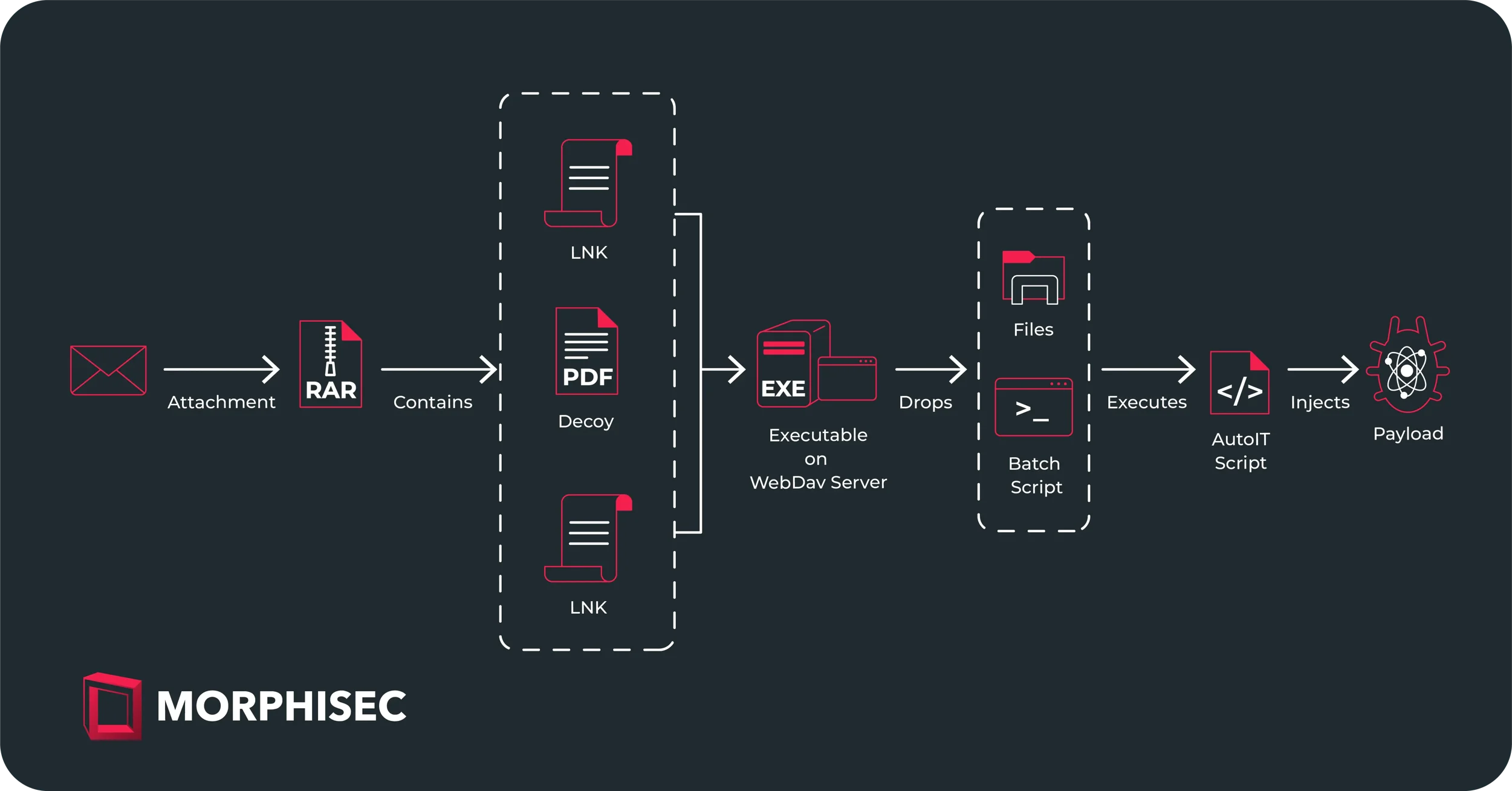
In the most recent operation, Adhesive Werewolf aimed at the aviation sector by sending emails supposedly coming from the First Deputy General Director of AO OKB Kristall, a company based in Moscow involved in the production and maintenance of aircraft and spacecraft. Previously, the group utilized phishing emails with links to harmful files. However, in the latest campaign, the malevolent actor sent archive files containing LNK documents pointing to a payload kept on WebDAV servers.
After executing the binary stored on a WebDAV server, an obscured Windows batch script is activated. This script initiates an AutoIt script that ultimately injects the final payload.
“In prior campaigns, the infection process started with phishing emails containing a link to download a harmful file from platforms like gofile.io. Nevertheless, in the latest campaign, the infection approach has been altered.” as stated in the research released by Morphisec. “The initial email includes an archive attachment; when the recipient decompresses the archive, they come across LNK and decoy files. These LNK files direct to an executable hosted on a WebDAV server. Upon execution, this triggers a Batch script, which then launches an AutoIt script that ultimately introduces the final payload.”
The archive contains a decoy PDF File and two LNK Files Disguised as DOCX Documents named Повестка совещания.docx.lnk (Meeting agenda) and Список рассылки.docx.lnk (Mailing list) respectively.
The malevolent actor used deceptive messages allegedly sent by the First Deputy General Director and Executive Director of AO OKB Kristall. The recipients are individuals from the aerospace and defense sector who are invited to a video conference on future collaboration. The messages include a password-protected archive containing a malicious payload.
The payloads used by the malevolent actors consist of off-the-shelf RATs or data stealers. Recently, Adhesive Werewolf was seen employing Rhadamanthys Stealer and Ozone RAT in their campaigns. In previous attacks the group also utilized MetaStealer, DarkTrack, and NetWire.
“These malicious software tools enable thorough espionage and data exfiltration. While there is no definitive proof of Adhesive Werewolf’s origin, the geopolitical landscape suggests likely connections to a pro-Ukrainian cyberespionage faction or hacktivists, although this attribution remains uncertain.” concludes the report that also provides Indicators of Compromise (IoCs).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – Hacking, malware)