Microsoft has unveiled 135 patches impacting 19 product families today. Out of these, ten critical remote code execution problems are addressed, with 18 having a CVSS base score of 8.0 or above. One of the significant issues, an elevation of privilege problem in the Windows Common Log File system driver with an Important severity level, is actively exploited in the wild.
Microsoft estimates that at the time of patching, 11 CVEs are more vulnerable to exploitation within the next 30 days. Some of this month’s issues can be directly detected by Sophos protections, and detailed information on these is presented in the table below.
Besides these updates, the release also covers sixteen Important-severity Adobe Reader issues that impact ColdFusion. These are outlined in Appendix D below. This month, we have included all Edge CVEs in our count whenever possible, though these patches were mostly released separately from today’s main update.
As customary, we have included additional appendices at the end of this post categorizing all of Microsoft’s patches based on severity, predicted exploit timeline, CVSS Base score, and product family. An appendix detailing advisory-style updates is also included, along with a breakdown of patches affecting the remaining supported Windows Server platforms.
In Numbers
- Total CVEs: 135
- Publicly disclosed: 0
- Exploits detected: 1
- Severity
- Critical: 10
- Important: 114
- Low: 2
- High / Medium / Low: 9 (Edge-related CVEs issued by Chromium; see Appendix C)
- Impact
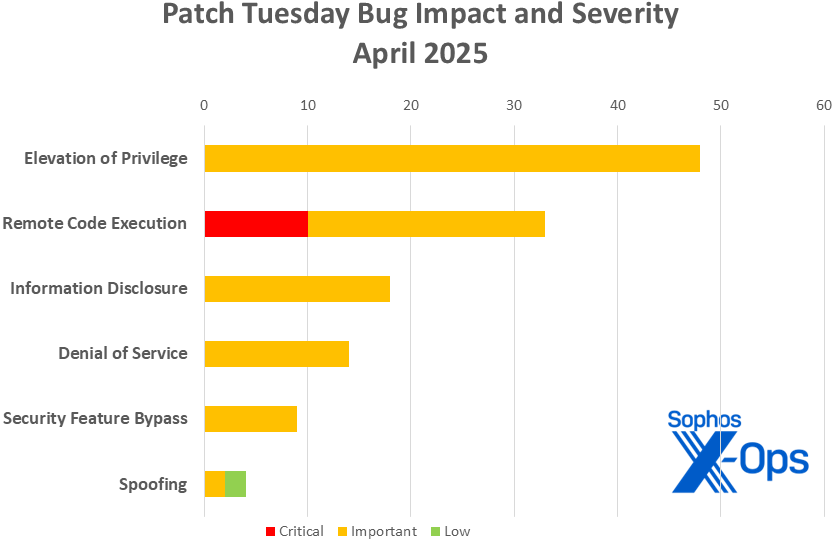
- Elevation of Privilege: 48
- Remote Code Execution: 33
- Information Disclosure: 18
- Denial of Service: 14
- Security Feature Bypass: 9
- Spoofing: 4
- Unknown: 9 (Edge-related CVEs issued by Chromium; see Appendix C)
- CVSS score 9.0 or higher: 0
- CVSS base score 8.0 or higher: 18
Figure 1: Elevation of privilege accounts for over a third of all April patches, but all the Critical-severity items are remote code execution. (Please note that nine of the Edge updates covered in this issue are not released with full impact information and follow a different severity schema, and thus do not appear in this chart; please see Appendix C)
Products
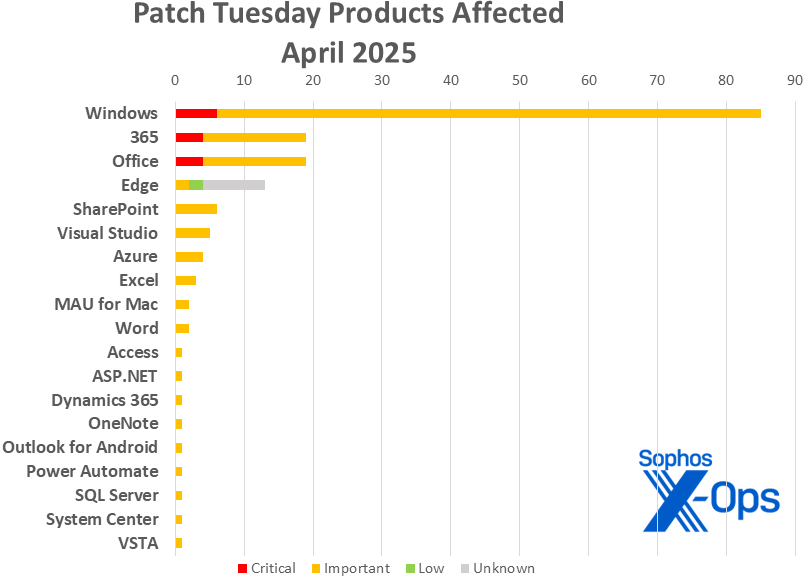
- Windows: 89
- 365: 15
- Office: 15
- Edge: 13
- SharePoint: 6
- Visual Studio: 5
- Azure: 4
- Excel: 3
- Microsoft AutoUpdate (MAU) for Mac: 2
- Word: 2
- Access: 1
- ASP.NET: 1
- Dynamics 365: 1
- OneNote: 1
- Outlook for Android: 1
- Power Automate for Desktop: 1
- SQL Server: 1
- System Center: 1
- Visual Studio Tools for Applications (VSTA): 1
CVEs considered for multiple product families are counted separately for each family. It’s worth mentioning that in April some CVE names may not closely align with affected products. In particular, certain CVEs could reference products not listed in the affected products for the CVE and vice versa.
Figure 2: In April, nineteen product families are impacted by the patches; as mentioned earlier, nine of the Edge updates in this issue lack full impact details and adhere to a different severity classification, showing up as “unknown” in terms of impact; refer to Appendix C for more
Key Highlights of April Updates
Besides the previously mentioned issues, a range of specific matters deserve attention.
CVE-2025-26642, CVE-2025-27745, CVE-2025-27747, CVE-2025-27748, CVE-2025-27749, CVE-2025-27750, CVE-2025-27751, CVE-2025-2772, CVE-2025-29791, CVE-2025-29816, CVE-2025-29820, CVE-2025-29822 (12 CVEs) – a range of issues related to Office
This month, Office faces a significant load of patches, particularly impacting users of Office LTSC for Mac 2021 and 2024. These twelve CVEs affect those versions, but the update is not yet available; affected parties should keep an eye on these CVEs for updates. Worse yet, five of the twelve (CVE-2025-27745, CVE-2025-27748, CVE-2025-27749, CVE-2025-27752, CVE-2025-29791) utilize the Preview Pane as an attack vector, elevating four to Critical severity from Important.
CVE-2025-26647 — Vulnerability in Windows Kerberos Elevation of Privilege
This elevation of privilege issue with an Important severity level seems to revolve around an attacker’s ability to compromise a trusted Certificate Authority (CA). If itthe intruder could take such action and then generate a certificate with a specific Subject Key Identifier (SKI) value. Subsequently, this certificate might be utilized to establish a connection with the system, ultimately assuming the identity of any account. Recommendations for addressing this issue include updating all Windows machines and domain controllers to the latest patch, keeping a check on audit events to identify any machine or device that has not been updated, and activating Enforcement Mode after discontinuing the use of certificates issued by authorities not in the NTAuth store. CA compromise has always been a persistent issue in the ecosystem; with Microsoft marking this CVE as more prone to exploitation in the next 30 days, it deserves priority in your environment.
—
CVE-2025-27743 — Microsoft System Center Elevation of Privilege Vulnerability
This vulnerability of Importance-severity, affects a range of System Center products (Operations Manager, Service Manager, Orchestrator, Data Protection Manager, Virtual Machine Manager) and impacts customers who reuse existing System Center .exe installer files to deploy new instances in their environments. The flaw originates from an untrusted search path in System Center, which an attacker could manipulate, with authorized access and proficiency in DLL hijacking, to escalate their privileges. Microsoft advises affected users to remove their existing installer setup files (.exe) and download the latest version of their System Center product (.ZIP).
—
CVE-2025-29809 — Windows Kerberos Security Feature Bypass Vulnerability
Another issue that might demand additional attention from administrators, this Important-severity security feature bypass necessitates the rollback of a prior policy. According to Microsoft’s guidance, “The policy mentioned in the Advisory for preventing the rollback of Virtualization-based Security (VBS) relevant security updates has been adjusted to accommodate the latest alterations. If you have deployed this policy, it will need to be redeployed utilizing the updated policy.”
Furthermore, for readers who might have missed the notification, Microsoft is not yet discontinuing driver update synchronization via WSUS (Windows Server Update Services) as initially planned. Those who are still dependent on this service (particularly for “disconnected” devices) are given an extension but should continue to prepare for the migration to cloud-based services now prioritized by Microsoft.
—
Figure 3: Similar to last month’s remote code execution, elevation of privilege vulnerabilities crossed the 100-CVE threshold with the latest Patch Tuesday release.
—
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2025-27482 | Exp/2527482-A | Exp/2527482-A |
| CVE-2025-29792 | Exp/2529792-A | Exp/2529792-A |
| CVE-2025-29812 | Exp/2529812-A | Exp/2529812-A |
| CVE-2025-29812 | Exp/2529812-A | Exp/2529812-A |
—
As is the case every month, if you prefer not to wait for your system to automatically download Microsoft’s updates, you have the option to manually download them from the Windows Update Catalog website. Utilize the winver.exe tool to ascertain the build of Windows 10 or 11 you are currently using, and then download the Cumulative Update package tailored for your specific system’s architecture and build number.
—
Appendix A: Impact and Severity of Vulnerabilities
This compilation of April patches is organized by impact, further arranged by severity, then sorted by CVE.
Elevation of Privilege (48 CVEs)
| Importance severity | |
| CVE-2025-20570 | Visual Studio Code Elevation of Privilege Vulnerability |
| CVE-2025-21191 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-21204 | Windows Process Activation Elevation of Privilege Vulnerability |
| CVE-2025-24058 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24060 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24062 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24073 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24074 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-26639 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2025-26640 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-26648 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-26649 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-26665 | Windows upnphost.dll Elevation of Privilege Vulnerability |
| CVE-2025-26675 | Windows Subsystem for Linux Elevation of Privilege Vulnerability |
| CVE-2025-26679 | RPC Endpoint Mapper Service Elevation of Privilege Vulnerability |
| CVE-2025-26681 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26687 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26688 | Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability |
| CVE-2025-27467 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27475 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2025-27476 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27478 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-27483 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27484 | Windows Universal Plug and Play (UPnP) Device Host Elevation of Privilege Vulnerability |
| CVE-2025-27489 | Azure Local Elevation of Privilege Vulnerability |
| CVE-2025-27490 | Windows Bluetooth Service Elevation of Privilege Vulnerability |
| CVE-2025-27492 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-27727 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-27728 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2025-27730 | Windows Digital Media Elevation of Privilege Vulnerability |
| Vulnerability ID: CVE-2025-27731 | Microsoft Windows OpenSSH Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27732 | Windows Graphics Component Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27733 | NTFS Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27739 | Windows Kernel Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27740 | Active Directory Certificate Services Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27741 | NTFS Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27743 | Microsoft System Center Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-27744 | Microsoft Office Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29792 | Microsoft Office Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29800 | Microsoft AutoUpdate (MAU) Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29801 | Microsoft AutoUpdate (MAU) Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29802 | Visual Studio Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Management Studio Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29804 | Visual Studio Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29810 | Active Directory Domain Services Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29811 | Windows Mobile Broadband Driver Privilege Escalation Vulnerability |
| Vulnerability ID: CVE-2025-29812 | DirectX Graphics Kernel Privilege Escalation Vulnerability |
Remote Code Execution (33 Vulnerabilities)
| Severe severity | |
| Vulnerability ID: CVE-2025-26663 | Windows LDAP Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-26670 | LDAP Client Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-26686 | Windows TCP/IP Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27480 | Windows Remote Desktop Services Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27482 | Windows Remote Desktop Services Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27491 | Windows Hyper-V Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27745 | Microsoft Office Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27748 | Microsoft Office Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27749 | Microsoft Office Remote Code Execution Vulnerability |
| Vulnerability ID: CVE-2025-27752 | Exploit in Microsoft Excel Vulnerability |
| Serious risk level | |
| CVE-2025-21205 | Windows Phone System Vulnerability |
| CVE-2025-21221 | Windows Telephone System Vulnerability |
| CVE-2025-21222 | Windows Phone System Vulnerability |
| CVE-2025-25000 | Microsoft Edge Security Vulnerability |
| CVE-2025-26642 | Microsoft Office Security Issue |
| CVE-2025-26666 | Windows Media Vulnerability |
| CVE-2025-26668 | Windows Routing and Remote Access Service (RRAS) Vulnerability |
| CVE-2025-26671 | Windows Remote Desktop Services Vulnerability |
| CVE-2025-26674 | Windows Media Security Risk |
| CVE-2025-27477 | Windows Phone System Exploit |
| CVE-2025-27481 | Windows Telephone System Vulnerability |
| CVE-2025-27487 | Remote Desktop Client Exploit |
| CVE-2025-27729 | Windows Shell Security Risk |
| CVE-2025-27746 | Microsoft Office Security Threat |
| CVE-2025-27747 | Microsoft Word Security Risk |
| CVE-2025-27750 | Exploit in Microsoft Excel Vulnerability |
| CVE-2025-27751 | Exploit in Microsoft Excel Vulnerability |
| CVE-2025-29791 | Exploit in Microsoft Excel Vulnerability |
| CVE-2025-29793 | Microsoft SharePoint Security Threat |
| CVE-2025-29794 | Microsoft SharePoint Security Threat |
| CVE-2025-29815 | Microsoft Edge Security Exposure |
| CVE-2025-29820 | Microsoft Word Security Risk |
| CVE-2025-29823 | Exploit in Microsoft Excel Vulnerability |
Data Exposure (18 CVEs)
| Serious risk level | |
| CVE-2025-21197 | Windows NTFS Data Exposure Vulnerability |
| CVE-2025-21203 | Windows Routing and Remote Access Service (RRAS) Data Exposure Vulnerability |
| CVE-2025-25002 | Azure Local Cluster Data Exposure Vulnerability |
| CVE-2025-26628 | Azure Local Cluster Data Leak Vulnerability |
| CVE-2025-26664 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-26667 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-26669 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-26672 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-26676 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-27474 | Windows Routing and Remote Access Service (RRAS) Data Leak Vulnerability |
| CVE-2025-27736 | Windows Power Dependency Coordinator Data Leak Vulnerability |
| CVE-2025-27738 | Windows Resilient File System (ReFS) Data Leak Vulnerability |
| CVE-2025-27742 | NTFS Data Leak Vulnerability |
| CVE-2025-29805 | Outlook for Android Data Leak Vulnerability |
| CVE-2025-29808 | Windows Cryptographic Services Data Leak Vulnerability |
| CVE-2025-29817 | Microsoft Power Automate Desktop Data Leak Vulnerability |
| CVE-2025-29819 | Windows Admin Center in Azure Portal Data Leak Vulnerability |
| CVE-2025-29821 | Microsoft Dynamics Business Central Data Leak Vulnerability |
Service Unavailability (14 CVEs)
| Significant seriousness | |
| CVE-2025-21174 | Windows Standards-Based Storage Management Service Service Unavailability Vulnerability |
| CVE-2025-26641 | Microsoft Message Queuing (MSMQ) Service Unavailability Vulnerability |
| CVE-2025-26651 | Windows Local Session Manager (LSM) Service Unavailability Vulnerability |
| CVE-2025-26652 | Windows Standards-Based Storage Management Service Service Unavailability Vulnerability |
| CVE-2025-26673 | Windows Lightweight Directory Access Protocol (LDAP) Service Unavailability Vulnerability |
| CVE-2025-26680 | Windows Standards-Based Storage Management Service Service Unavailability Vulnerability |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Service Unavailability Vulnerability |
| CVE-2025-27469 | Windows Lightweight Directory Access Protocol (LDAP) Service Unavailability Vulnerability |
| CVE-2025-27470 | Windows Standards-Based Storage Management Service Service Unavailability Vulnerability |
| CVE-2025-27471 | Microsoft Streaming Service Service Unavailability Vulnerability |
| CVE-2025-27473 | HTTP.sys Service Unavailability Vulnerability |
| CVE-2025-27479 | Kerberos Key Distribution Proxy Service Service Unavailability Vulnerability |
| CVE-2025-27485 | Windows Guidelines-Based Storage Management Service Denial of Service Weakness |
| CVE-2025-27486 | Windows Guidelines-Based Storage Management Service Denial of Service Weakness |
Security Attribute Bypass (9 CVEs)
| Critical severity | |
| CVE-2025-26635 | Windows Greetings Attribute Bypass Weakness |
| CVE-2025-26637 | BitLocker Attribute Bypass Weakness |
| CVE-2025-26678 | Windows Guardian Program Control Attribute Bypass Weakness |
| CVE-2025-27472 | Windows Sign of the Internet Attribute Bypass Weakness |
| CVE-2025-27735 | Windows Virtualized Security (VBS) Attribute Bypass Weakness |
| CVE-2025-27737 | Windows Security Zone Assignment Attribute Bypass Weakness |
| CVE-2025-29809 | Windows Kerberos Attribute Bypass Weakness |
| CVE-2025-29816 | Microsoft Document Attribute Bypass Weakness |
| CVE-2025-29822 | Microsoft Digital Note Attribute Bypass Weakness |
Impersonation (4 CVE)
| Critical severity | |
| CVE-2025-26644 | Windows Greetings Impersonation Weakness |
| CVE-2025-26647 | Windows Kerberos Privilege Escalation Weakness |
| CVE-2025-25001 | Microsoft Edge for iOS Impersonation Weakness |
| CVE-2025-29796 | Microsoft Edge for iOS Impersonation Weakness |
Appendix B: Vulnerability and CVSS Score
This is a compilation of the April CVEs evaluated by Microsoft to be either under attack in the wild or more prone to be exploited in the wild within the initial 30 days after being issued. The list is further organized by CVE.
| Exploitation identified | |
| CVE-2025-29824 | Windows Shared Log File System Driver Privilege Escalation Weakness |
| Exploitation more likely in the next 30 days | |
| CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Weakness |
| CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Weakness |
| CVE-2025-27472 | Windows Sign of the Internet Attribute Bypass Weakness |
| CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Weakness |
| CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Weakness |
| CVE-2025-27727 | Windows Setup Program Privilege Escalation Weakness |
| CVE-2025-29792 | Elevated Privilege Vulnerability in Microsoft Office |
| CVE-2025-29793 | Remote Code Execution Vulnerability in Microsoft SharePoint |
| CVE-2025-29794 | Remote Code Execution Vulnerability in Microsoft SharePoint |
| CVE-2025-29809 | Security Feature Bypass Vulnerability in Windows Kerberos |
| CVE-2025-29812 | Elevated Privilege Vulnerability in DirectX Graphics Kernel |
The following list displays Microsoft-assessed CVSS Base scores of 8.0 or above for CVEs in April. The entries are organized by score and then by CVE. To learn more about CVSS, please visit our guide on patch prioritization framework.
| CVSS Score | Temporal CVSS | CVE | Title |
| 8.8 | 7.7 | CVE-2025-21205 | Remote Code Execution Vulnerability in Windows Telephony Service |
| 8.8 | 7.7 | CVE-2025-21221 | Remote Code Execution Vulnerability in Windows Telephony Service |
| 8.8 | 7.7 | CVE-2025-21222 | Remote Code Execution Vulnerability in Windows Telephony Service |
| 8.8 | 7.7 | CVE-2025-25000 | Remote Code Execution Vulnerability in Microsoft Edge (Chromium-based) |
| 8.8 | 7.7 | CVE-2025-26669 | Information Disclosure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| 8.8 | 7.7 | CVE-2025-27477 | Remote Code Execution Vulnerability in Windows Telephony Service |
| 8.8 | 7.7 | CVE-2025-27481 | Remote Code Execution Vulnerability in Windows Telephony Service |
| 8.8 | 7.7 | CVE-2025-27740 | Elevated Privilege Vulnerability in Active Directory Certificate Services |
| 8.8 | 7.7 | CVE-2025-29794 | Remote Code Execution Vulnerability in Microsoft SharePoint |
| 8.6 | 7.5 | CVE-2025-27737 | Security Feature Bypass Vulnerability in Windows Security Zone Mapping |
| 8.4 | 7.3 | CVE-2025-26678 | Security Feature Bypass Vulnerability in Windows Defender Application Control |
| 8.1 | 7.1 | CVE-2025-26647 | Elevation of Privilege Vulnerability in Windows Kerberos |
| 8.1 | 7.1 | CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-26671 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.0 | 7.0 | CVE-2025-27487 | Remote Desktop Client Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of April’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Issues affecting Windows Server are further sorted in Appendix E.
Windows (89 CVEs)
| Critical severity | |
| CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2025-26686 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27491 | Windows Hyper-V Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-21174 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-21191 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-21197 | Windows NTFS Information Disclosure Vulnerability |
| CVE-2025-21203 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-21204 | Windows Process Activation Elevation of Privilege Vulnerability |
| CVE-2025-21205 | Windows Telephony Service Remote Code Execution Vulnerability |
| Security Vulnerability ID: CVE-2025-21221 | Vulnerability in Windows Telephony Service allowing Remote Code Execution |
| Security Vulnerability ID: CVE-2025-21222 | Remote Code Execution Vulnerability in Windows Telephony Service |
| Security Vulnerability ID: CVE-2025-24058 | Elevation of Privilege Vulnerability in Windows DWM Core Library |
| Security Vulnerability ID: CVE-2025-24060 | Elevation of Privilege Vulnerability in Microsoft DWM Core Library |
| Security Vulnerability ID: CVE-2025-24062 | Elevation of Privilege Vulnerability in Microsoft DWM Core Library |
| Security Vulnerability ID: CVE-2025-24073 | Elevation of Privilege Vulnerability in Microsoft DWM Core Library |
| Security Vulnerability ID: CVE-2025-24074 | Elevation of Privilege Vulnerability in Microsoft DWM Core Library |
| Security Vulnerability ID: CVE-2025-26635 | Vulnerability in Windows Hello leading to Security Feature Bypass |
| Security Vulnerability ID: CVE-2025-26637 | Security Feature Bypass Vulnerability in BitLocker |
| Security Vulnerability ID: CVE-2025-26639 | Elevation of Privilege Vulnerability in Windows USB Print Driver |
| Security Vulnerability ID: CVE-2025-26640 | Elevation of Privilege Vulnerability in Windows Digital Media Components |
| Security Vulnerability ID: CVE-2025-26641 | Denial of Service Vulnerability in Microsoft Message Queuing (MSMQ) |
| Security Vulnerability ID: CVE-2025-26644 | Spoofing Vulnerability in Windows Hello feature |
| Security Vulnerability ID: CVE-2025-26647 | Elevation of Privilege Vulnerability in Windows Kerberos Authentication system |
| Security Vulnerability ID: CVE-2025-26648 | Elevation of Privilege Vulnerability in Windows Kernel function calls |
| Security Vulnerability ID: CVE-2025-26649 | Elevation of Privilege Vulnerability in Windows Secure Channel communication protocol |
| Security Vulnerability ID: CVE-2025-26651 | Denial of Service Vulnerability in Windows Local Session Manager (LSM) |
| Security Vulnerability ID: CVE-2025-26652 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| Security Vulnerability ID: CVE-2025-26664 | Information Disclosure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| Security Vulnerability ID: CVE-2025-26665 | Elevation of Privilege Vulnerability in Windows upnphost.dll component |
| Security Vulnerability ID: CVE-2025-26666 | Remote Code Execution Vulnerability in Windows Media components for Remote Access |
| Security Vulnerability ID: CVE-2025-26667 | Information Disclosure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| Security Vulnerability ID: CVE-2025-26668 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| Security Vulnerability ID: CVE-2025-26669 | Information Disclosure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| Security Vulnerability ID: CVE-2025-26671 | Remote Code Execution Vulnerability in Windows Remote Desktop Services |
| Security Vulnerability ID: CVE-2025-26672 | Information Disclosure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| Security Vulnerability ID: CVE-2025-26673 | Denial of Service Vulnerability in Windows Lightweight Directory Access Protocol (LDAP) |
| Security Vulnerability ID: CVE-2025-26674 | Remote Code Execution Vulnerability in Windows Media components for Remote Access |
| Security Vulnerability ID: CVE-2025-26675 | Security Vulnerability in Windows Subsystem for Linux Requiring Higher Privileges |
| CVE-2025-26676 | Information Exposure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| CVE-2025-26678 | Bypassing of Security Feature in Windows Defender Application Control |
| CVE-2025-26679 | Increased Privileges Vulnerability in RPC Endpoint Mapper Service |
| CVE-2025-26680 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2025-26681 | Privilege Escalation Vulnerability in Win32k System |
| CVE-2025-26687 | Privilege Elevation Vulnerability in Win32k System |
| CVE-2025-26688 | Privilege Elevation Vulnerability in Microsoft Virtual Hard Disk |
| CVE-2025-27467 | Privilege Escalation Vulnerability in Windows Digital Media System |
| CVE-2025-27469 | Denial of Service Vulnerability in Windows Lightweight Directory Access Protocol (LDAP) |
| CVE-2025-27470 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2025-27471 | Denial of Service Vulnerability in Microsoft Streaming Service |
| CVE-2025-27472 | Security Feature Bypass Vulnerability in Windows Mark of the Web System |
| CVE-2025-27473 | Denial of Service Vulnerability in HTTP.sys |
| CVE-2025-27474 | Information Exposure Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| CVE-2025-27475 | Privilege Escalation Vulnerability in Windows Update Stack |
| CVE-2025-27476 | Privilege Escalation Vulnerability in Windows Digital Media System |
| CVE-2025-27477 | Remote Code Execution Vulnerability in Windows Telephony Service |
| CVE-2025-27478 | Privilege Escalation Vulnerability in Windows Local Security Authority (LSA) |
| CVE-2025-27479 | Denial of Service Vulnerability in Kerberos Key Distribution Proxy Service |
| CVE-2025-27481 | Remote Code Execution Vulnerability in Windows Telephony Service |
| CVE-2025-27483 | Privilege Escalation Vulnerability in NTFS System |
| CVE-2025-27484 | Privilege Escalation Vulnerability in Windows Universal Plug and Play (UPnP) Device Host |
| CVE-2025-27485 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2025-27486 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2025-27487 | Remote Code Execution Vulnerability in Remote Desktop Client |
| CVE-2025-27490 | Privilege Elevation Vulnerability in Windows Bluetooth Service |
| CVE-2025-27492 | Privilege Elevation Vulnerability in Windows Secure Channel |
| CVE-2025-27727 | Privilege Escalation Vulnerability in Windows Installer |
| CVE-2025-27728 | Vulnerability for Escalating Privileges in Windows Kernel-Mode Drivers |
| CVE-2025-27729 | Exploit for Running Code Remotely in Windows Shell |
| CVE-2025-27730 | Windows Digital Media Vulnerability for Escalating Privileges |
| CVE-2025-27731 | Privilege Escalation Vulnerability in Microsoft OpenSSH for Windows |
| CVE-2025-27732 | Windows Graphics Component Vulnerability for Escalating Privileges |
| CVE-2025-27733 | NTFS Vulnerability for Escalating Privileges |
| CVE-2025-27735 | Security Feature Bypass Vulnerability in Windows Virtualization-Based Security (VBS) |
| CVE-2025-27736 | Information Disclosure Vulnerability in Windows Power Dependency Coordinator |
| CVE-2025-27737 | Security Feature Bypass Vulnerability in Windows Security Zone Mapping |
| CVE-2025-27738 | Information Disclosure Vulnerability in Windows Resilient File System (ReFS) |
| CVE-2025-27739 | Privilege Escalation Vulnerability in Windows Kernel |
| CVE-2025-27740 | Vulnerability for Escalating Privileges in Active Directory Certificate Services |
| CVE-2025-27741 | NTFS Privilege Escalation Vulnerability |
| CVE-2025-27742 | NTFS Vulnerability for Information Disclosure |
| CVE-2025-29808 | Information Disclosure Vulnerability in Windows Cryptographic Services |
| CVE-2025-29809 | Security Feature Bypass Vulnerability in Windows Kerberos |
| CVE-2025-29810 | Elevation of Privilege Vulnerability in Active Directory Domain Services |
| CVE-2025-29811 | Privilege Escalation Vulnerability in Windows Mobile Broadband Driver |
| CVE-2025-29812 | Elevation of Privilege Vulnerability in DirectX Graphics Kernel |
| CVE-2025-29824 | Elevation of Privilege Vulnerability in Windows Common Log File System Driver |
365 (15 CVEs)
| Critical level of severity | |
| CVE-2025-27745 | Vulnerability for Remote Code Execution in Microsoft Office |
| CVE-2025-27748 | Vulnerability for Remote Code Execution in Microsoft Office |
| CVE-2025-27749 | Vulnerability for Remote Code Execution in Microsoft Office |
| CVE-2025-27752 | Vulnerability for Remote Code Execution in Microsoft Excel |
| Severity level of importance | |
| CVE-2025-26642 | Vulnerability for Remote Code Execution in Microsoft Office |
| CVE-2025-27746 | Vulnerability for Remote Code Execution in Microsoft Office |
| CVE-2025-27747 | Vulnerability for Remote Code Execution in Microsoft Word |
| Security Issue | |
| Security Threat | |
| Security Concern | |
| Damaging Vulnerability | |
| Hazardous Vulnerability Exposure | |
| Exposure to Security Risks | |
| Chromium-based Vulnerability | |
| Exploit Weakness in Security Measures | |
| Vulnerability in Microsoft Edge | |
| Security Flaw in Edge Browser | |
| Web Browser Vulnerability | |
| Weak Link in Browser Security | |
| Vulnerability in Microsoft Edge | |
Challenges (13 Issues)
| Problematic severity | |
| Difficulty in Security Measures | Weaknesses in Protection |
| Security Risks in Challenge | Challenge Vulnerabilities |
| Complexity of Issues | |
| Challenges in Security Controls | Security Challenge Complexity |
| CVE-2025-25001 | Microsoft Edge for iOS Spoofing |
Weakness
SharePoint (6 Weaknesses)
| Significant severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Weakness |
| CVE-2025-27746 | Microsoft Office Remote Code Execution Weakness |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Weakness |
| CVE-2025-29793 | Microsoft SharePoint Remote Code Execution Weakness |
| CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Weakness |
| CVE-2025-29820 | Microsoft Word Remote Code Execution Weakness |
Visual Studio (5 Weaknesses)
| Significant severity | |
| CVE-2025-20570 | Visual Studio Code Elevation of Privilege Weakness |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Denial of Service Weakness |
| CVE-2025-29802 | Visual Studio Elevation of Privilege Weakness |
| CVE-2025-29804 | Visual Studio Elevation of Privilege Weakness |
Azure (4 Weaknesses)
| Significant severity | |
| CVE-2025-25002 | Azure Local Cluster Information Disclosure Weakness |
| CVE-2025-26628 | Azure Local Cluster Information Disclosure Weakness |
| CVE-2025-27489 | Azure Local Cluster Information Disclosure Weakness |
| Azure Privilege Escalation Vulnerability | Windows Admin Center in Azure Portal Disclosure Vulnerability |
Excel (3 CVEs)
| Significant severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27750 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-27751 | Microsoft Excel Remote Code Execution Vulnerability |
Microsoft AutoUpdater for Mac (2 CVEs)
| Significant severity | |
| CVE-2025-29800 | Microsoft AutoUpdate (MAU) Privilege Escalation Vulnerability |
| CVE-2025-29801 | Microsoft AutoUpdate (MAU) Privilege Escalation Vulnerability |
Word (2 CVEs)
| Significant severity | |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29816 | Microsoft Word Security Feature Bypass Vulnerability |
Access (1 CVE)
| Significant severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
ASP.NET (1 CVE)
| Significant severity | |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Denial of Service Vulnerability |
Dynamics 365 (1 CVE)
| Significant severity | |
| CVE-2025-29821 | Microsoft Dynamics Business Central Disclosure Vulnerability |
OneNote (1 CVE)
| Significant severity | |
| CVE-2025-29822 | Microsoft OneNote Security Feature Bypass Vulnerability |
Outlook for Android (1 CVE)
| Significant severity | |
| CVE-2025-29805 | Outlook for Android Disclosure Vulnerability |
Automated Power Desktop (1 CVE)
| Significant severity | |
| CVE-2025-29817 | Microsoft Automated Power Desktop Information Leak Vulnerability |
Structured Query Language Server (1 CVE)
| Significant severity | |
| CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Manager Studio Elevation of Privileges Vulnerability |
Network Center (1 CVE)
| Significant severity | |
| CVE-2025-27743 | Microsoft Network Center Elevation of Privileges Vulnerability |
VSTA (1 CVE)
| Significant severity | |
| CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Manager Studio Elevation of Privileges Vulnerability |
Appendix D: Warnings and Other Goods
This month’s release contains 16 Adobe alerts.
| CVE-2025-24446 | APSB25-15 | Incorrect Input Validation |
| CVE-2025-24447 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30281 | APSB25-15 | Poor Access Management |
| CVE-2025-30282 | APSB25-15 | Incorrect Authentication |
| CVE-2025-30283 | APSB25-15 | Incorrect Input Validation |
| CVE-2025-30284 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30285 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30286 | APSB25-15 | Improper Deactivation of Special Components in an OS Command (‘OS Command Injection’) |
| CVE-2025-30287 | APSB25-15 | Incorrect Authentication |
| CVE-2025-30288 | APSB25-15 | Poor Access Management |
| CVE-2025-30289 | APSB25-15 | Improper Deactivation of Special Components in an OS Command (‘OS Command Injection’) |
| CVE-2025-30290 | APSB25-15 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
| CVE-2025-30291 | APSB25-15 | Information Leakage |
| CVE-2025-30292 | APSB25-15 | |
| CVE-2025-30293 | APSB25-15 | Incorrect Input Validation |
| CVE-2025-30294 | APSB25-15 | Incorrect Input Validation |
Appendix E: Impacted Windows Server editions
In this table, you can find the CVEs from the April release affecting nine Windows Server editions from 2008 to 2025. The table distinguishes between different versions of the platform but does not delve into specific details like Server Core. High-severity issues are highlighted in red; an “x” denotes that the CVE is not relevant to that edition. Administrators are advised to utilize this appendix as a reference point to determine their individual exposure, as the circumstances of each reader will vary, particularly concerning products no longer in mainstream support. For precise Knowledge Base references, please refer to Microsoft. Please be aware that CVE-2025-27475 pertains solely to a Windows client issue and is therefore included in this table without any server editions noted.
| 2008 | 2008-R2 | 2012 | 2012-R2 | 2016 | 2019 | 2022 | 2022 23H2 | 2025 | ||||||||||
| CVE-2025-21174 | × | × | × | ■ | ■ | ■ | ■ | × | ■ | |||||||||
| CVE-2025-21191 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-21197 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-21203 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-21204 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-21205 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-21222 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-24058 | × | × | × | × | × | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-24060 | × | × | × | × | × | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-24062 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-24073 | × | ■ | ■ | ■ | ■ | ■ | ||||||||||||
| CVE-2025-24074 | × | × | × | × | × | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-26635 | × | × | × | × | × | ■ | ■ | ■ | × | |||||||||
| CVE-2025-26637 | × | × | × | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-26639 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| Security Vulnerability 2025-26640 | × | × | × | × | × | ■ | × | ■ | ■ | |||||||||
| Security Vulnerability 2025-26641 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security Vulnerability 2025-26644 | × | × | × | × | × | ■ | × | × | ■ | |||||||||
| Security Vulnerability 2025-26647 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security Vulnerability 2025-26648 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ||||||||||
| CVE-2025-26649 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-26651 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-26652 | × | × | × | ■ | ■ | ■ | ■ | × | ■ | |||||||||
| CVE-2025-26663 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability ID: CVE-2025-26664 | Severity: Critical | Impact: High | Risk: High | Priority: High | Action: Required | Resolution: In Progress | Deadline: ASAP | Owner: John Doe | ||||||||||
| Vulnerability ID: CVE-2025-26665 | Severity: Critical | Impact: High | Risk: High | Priority: High | Action: Required | Resolution: In Progress | Deadline: ASAP | Owner: John Doe | ||||||||||
| Vulnerability ID: CVE-2025-26666 | Severity: High | Impact: High | Risk: High | Priority: High | Action: Immediate | Resolution: Pending | Deadline: Today | Owner: Jane Smith | ||||||||||
| Vulnerability ID: CVE-2025-26667 | Severity: Critical | Impact: High | Risk: High | Priority: High | Action: Required | Resolution: In Progress | Deadline: ASAP | Owner: John Doe | ||||||||||
| Vulnerability ID: CVE-2025-26668 | Severity: Critical | Impact: High | Risk: High | Priority: High | Space | ■Space | ■Space | ■Space | ■Space | ■Space | ||||||||
| CVE-2025-26669Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | ||||||||||
| CVE-2025-26670Space | ■Space | ■Space | ■Space | ■ | ■Space | ■Space | ■Space | ■Space | ■ | |||||||||
| CVE-2025-26671Space | ×Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | ■Space | |||||||||
| CVE-2025-26672Space | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-26674 | × | × | × | × | × | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-26675 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-26676 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-26678 | × | × | × | × | × | ■ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ||||||||
| CVE-2025-26679 | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | |||||||||
| CVE-2025-26680 | × | × | × | ⚫️ | ⚫️ | ⚫️ | ⚫️ | × | ⚫️ | |||||||||
| CVE-2025-26681 | × | × | × | × | × | × | ⚫️ | ⚫️ | ⚫️ | |||||||||
| CVE-2025-26686 | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | ⚫️ | |||||||||
| CVE-2025-26687 | ⚫️ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security Vulnerability ID: CVE-2025-26688 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security Vulnerability ID: CVE-2025-27467 | × | × | × | × | × | ■ | × | ■ | ■ | |||||||||
| Security Vulnerability ID: CVE-2025-27469 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security Vulnerability ID: CVE-2025-27470 | × | × | × | ■ | ■ | ■ | ⬛️ | ❌ | ⬛️ | ⬛️ | ||||||||
| CVE-2025-27471 | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | |||||||||
| CVE-2025-27472 | ❌ | ❌ | ⬛️ | ⬛️ | ❌ | ❌ | ❌ | ❌ | ❌ | |||||||||
| CVE-2025-27473 | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | |||||||||
| CVE-2025-27474 | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | ⬛️ | |||||||||
| CVE-2025-27475 | ❌ | × | × | × | × | × | × | × | × | |||||||||
| CVE-2025-27476 | × | × | × | × | × | ■ | × | ■ | ■ | |||||||||
| CVE-2025-27477 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27478 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27479 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability – CVE-2025-27480 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability – CVE-2025-27481 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability – CVE-2025-27482 | × | × | × | × | ■ | ■ | ■ | ■ | ■ | |||||||||
| Vulnerability – CVE-2025-27483 | × | × | × | ■ | ■ | ■ | × | × | × | |||||||||
| Vulnerability – CVE-2025-27484 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27485 | × | × | × | ■ | ■ | ■ | ■ | × | ■ | |||||||||
| CVE-2025-27486 | × | × | × | ■ | ■ | ■ | ■ | × | ■ | |||||||||
| CVE-2025-27487 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27490 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-27491 | × | × | × | × | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27492 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-27727 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| Security | Security | |||||||||||||||||
| Vulnerability | Security | Security | Security | Security | ||||||||||||||
| Threat | Security | Security | Security | Security | Security | Security | Security | Security | Security | × | × | × | × | |||||
| CVE-2025-27735 | × | × | × | × | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27736 | × | × | × | × | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27737 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27738 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27739 | × | × | × | × | × | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-27740 | ■ | ■ | ■ | ■ | ■ | |||||||||||||
| CVE-2025-27741 | ■ | ■ | ■ | ■ | ||||||||||||||
| CVE-2025-27742 | ■ | ■ | ■ | ■ | ||||||||||||||
| CVE-2025-29808 | × | × | × | × | ■ | × | × | |||||||||||
| CVE-2025-29809 | ■ | × | × | × | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-29810 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | |||||||||
| CVE-2025-29811 | × | × | × | × | × | × | × | ■ | ■ | |||||||||
| CVE-2025-29812 | × | × | × | × | × | × | ■ | ■ | ■ | |||||||||
| CVE-2025-29824 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |