A cyber risk assessment is a process of identifying, analyzing, and evaluating the cyber threats and vulnerabilities that could affect your organization’s assets, operations, and reputation. A cyber risk assessment can help you prioritize your security efforts, comply with regulations, and communicate with stakeholders.
There are different approaches and frameworks for conducting a cyber risk assessment, depending on your organization’s needs and goals. Some of the common ones are:
- The NIST Cybersecurity Framework (CSF), which provides a set of best practices and standards for improving the security and resilience of critical infrastructure sectors.
- The ISO/IEC 27001, which is an international standard for establishing, implementing, maintaining, and improving an information security management system (ISMS).
- The FAIR model, which is a quantitative method for measuring and managing cyber risk in financial terms.
- The CyberInsight model, which is a unique risk model based on the VERIS and MITRE frameworks, that helps you map attack routes and model attack consequences.
How to Conduct a Cyber Risk Assessment

1.Identify and Prioritize Assets:
First, identify all the critical assets that the organization has, such as hardware, software, data, and intellectual property. Next, rank them according to their value and importance for the organization. This will help to prioritize the risk assessment efforts. Security professionals need to know what the assets are in order to protect them.
Importance of prioritizing assets : Prioritizing assets is a key process in investment budgeting and data security. It helps organizations allocate their limited resources to the most valuable and critical assets, and manage the risks associated with them. By prioritizing assets, organizations can optimize their performance, efficiency, and profitability
How to identify Critical Assets: Critical assets are those that are essential for supporting the mission and functions of an organization. They can include hardware, software, data, and intellectual property. To identify critical assets, you need to consider the following aspects:
- The impact of asset failure on the organization’s objectives, performance, reputation, and stakeholders.
- The likelihood of asset failure due to threats, vulnerabilities, and exposure.
- The value and importance of the asset to the organization and its customers.
There are different methods to identify critical assets, such as risk assessments, asset inventories, network traffic monitoring, and stakeholder consultations13. You can use these methods to create a list of critical assets and rank them according to their criticality. This will help you prioritize your risk management and asset protection efforts.
How to protect critical assets from cyber attacks ?
Cyber attacks are a serious threat to any organization that relies on digital assets, such as data, software, hardware, and intellectual property. To protect your critical assets from cyber attacks, you need to follow some best practices, such as:
- Adopting a zero-trust policy that assumes all users, devices, and software are insecure and requires strict identity verification and access control.
- Educating your employees about cyber risks and how their actions can expose or protect your assets from attackers.
- Implementing a backup solution that continuously and automatically backs up your critical data and system configurations.
- Using AI and machine learning to monitor your network and detect anomalies and threats in real time.
- Developing a comprehensive and cross-functional strategy that identifies and prioritizes your critical assets, assesses and mitigates your vulnerabilities, and defines and delivers your security goals.
2. Threat Modeling
Threat modeling is a process of identifying, analyzing, and mitigating the potential threats to a system. Identify the possible threats and attack vectors that could compromise your assets by using threat modeling techniques. Learn the TTPs that threat actors typically use.
What are some common threat modeling techniques?
There are different techniques that can be used for threat modeling, depending on the goals, scope, and complexity of the system. Here are some common threat modeling techniques
- STRIDE: This technique uses six categories of threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It helps to identify the threats based on the system’s data flows, trust boundaries, and interactions.
- PASTA: This technique stands for Process for Attack Simulation and Threat Analysis. It is a risk-based approach that simulates the attacker’s perspective and evaluates the impact and likelihood of the threats.
- VAST: This technique stands for Visual, Agile, and Simple Threat modeling. It is a scalable and collaborative approach that integrates threat modeling into agile development processes and uses visual diagrams to communicate the threats.
- Trike: This technique is an audit-based approach that focuses on the security requirements and goals of the system. It uses a risk model that defines the actors, assets, and actions of the system, and evaluates the threats based on the risk appetite of the stakeholders.
- CVSS: This technique stands for Common Vulnerability Scoring System. It is a standard method for rating the severity of the vulnerabilities in a system. It uses a numerical score that reflects the impact, exploitability, and scope of the vulnerabilities.
- Attack Trees: This technique uses a graphical representation of the possible attack scenarios and paths that an attacker can take to compromise a system. It helps to analyze the attack vectors, dependencies, and countermeasures of the threats.
- Security Cards: This technique uses a deck of cards that represent different security concepts, such as threats, assets, human factors, and principles. It is a creative and interactive approach that facilitates brainstorming and discussion among the stakeholders.
- hTMM: This technique stands for hybrid Threat Modeling Method. It is a comprehensive and systematic approach that combines the strengths of different threat modeling techniques, such as STRIDE, PASTA, and Attack Trees. It uses a four-phase process that covers the identification, analysis, evaluation, and treatment of the threats.
Common TTPs used by threat actors
TTPs are the tactics, techniques, and procedures that threat actors use to conduct cyberattacks. They describe the behavior, methods, and tools of the adversaries. Some of the common TTPs used by threat actors are: ( Source SPlank)
- Command and Scripting Interpreter: This technique involves using various scripting languages and shells to execute commands on a compromised system. It can be used for initial access, persistence, defense evasion, lateral movement, and collection.
- Credential Dumping: This technique involves extracting account login and password information from the operating system and software. It can be used for privilege escalation, lateral movement, and collection.
- PowerShell: This technique involves using the PowerShell framework to run commands and scripts on a compromised system. It can be used for initial access, execution, persistence, defense evasion, lateral movement, and collection.
- Spearphishing Attachment: This technique involves sending a targeted email with a malicious attachment to a specific individual or group. It can be used for initial access and execution.
- Process Injection: This technique involves injecting malicious code into the address space of another process. It can be used for execution, privilege escalation, defense evasion, and persistence.
- User Execution: This technique involves tricking the user into running or enabling malicious code on their system. It can be used for initial access and execution.
- Registry Run Keys / Startup Folder: This technique involves modifying registry keys or files in the startup folder to execute malicious code when the system boots up or the user logs in. It can be used for persistence and defense evasion.
- Remote File Copy: This technique involves copying files from one system to another over a network. It can be used for initial access, lateral movement, and collection. Scheduled Task / Job: This technique involves creating or modifying scheduled tasks or jobs to execute malicious code at a specific time or interval. It can be used for persistence, privilege escalation, and defense evasion.
- Valid Accounts: This technique involves using legitimate credentials to access systems or services. It can be used for initial access, persistence, privilege escalation, and lateral movement.
For more information and examples of these and other TTPs, you can check out the MITRE ATT&CK framework, which is a comprehensive collection of TTPs that attackers use in the real world
3. Vulnerability Assesment
Scan and assess your system, application, and network for any weaknesses and security gaps. Fix or reduce these vulnerabilities to lower the chances of successful attacks
How to Prioritize vulnerabilities for patching
Prioritizing vulnerabilities for patching is a crucial step in vulnerability management. It helps you to focus on the most critical and urgent risks to your system and reduce the attack surface. However, prioritizing vulnerabilities can be challenging, as there are many factors to consider, such as severity, exploitability, impact, asset value, and threat intelligence.
Here are some general steps to help you prioritize your vulnerabilities for patching
- Perform regular vulnerability scans and assessments to identify and inventory your system, application, and network vulnerabilities. You can use various tools and methods for this, such as Nessus, Nmap, OpenVAS, or OWASP ZAP.
- Use a standard scoring system, such as CVSS, to rate the severity of each vulnerability based on its impact and exploitability. CVSS provides a numerical score from 0 to 10, where 10 is the most severe.
- Use threat intelligence sources, such as [MITRE ATT&CK], [NIST NVD], or [CVE Details], to gather information about the current and emerging threats, exploits, and attack vectors that target your vulnerabilities. This can help you to assess the likelihood and urgency of each vulnerability being exploited.
- Use asset information and value, such as the function, location, owner, and sensitivity of each asset, to determine the potential impact and damage of each vulnerability being exploited. This can help you to align your vulnerability prioritization with your business goals and priorities.
- Use a risk-based approach, such as [PASTA], [VAST], or [hTMM], to combine the severity, exploitability, impact, and asset value of each vulnerability into a risk score or ranking. This can help you to prioritize the vulnerabilities that pose the highest risk to your organization and require immediate attention.
- Apply patches or mitigations to the highest priority vulnerabilities as soon as possible, following the best practices and guidelines for patch management. You can use various tools and methods for this, such as WSUS, Iterian, Heimdal, or Cekino
- Monitor and verify the effectiveness of your patches or mitigations, and update your vulnerability inventory and risk assessment accordingly. You can use various tools and methods for this, such as Picus or Rapid7
4. Historical Incident Analysis
Learn from past security incidents and breaches that affected your organization or similar sectors. Understand the threats you are up against and how well your security controls work. Mistakes are inevitable, but they can help you improve. Use them to develop and apply new solutions.
What are some common types of security incidents and breaches?
Some common types of security incidents and breaches are:
- Phishing attacks: These are deceptive emails or messages that trick users into sharing sensitive information or clicking on malicious links.
- Malware attacks: These are malicious software programs that infect and damage computer systems, networks, and data.
- Spoofing attacks: These are fraudulent activities that impersonate legitimate entities or individuals to gain unauthorized access or trust
- Identity-based attacks: These are attacks that exploit the identity and credentials of users or devices to bypass security controls or perform malicious action.
- Code injection attacks: These are attacks that insert malicious code into a web application or database to execute unauthorized commands or access sensitive data.
- Supply chain attacks: These are attacks that compromise a third-party vendor or service provider that has access to the target organization’s systems or data.
- Denial-of-service (DoS) attacks: These are attacks that overwhelm a system or network with excessive traffic or requests to disrupt its normal functioning or availability.
- Ransomware attacks: These are a type of malware attack that encrypts the victim’s data or systems and demands a ransom for their decryption or restoration.
- Data breaches: These are incidents that expose or leak confidential or sensitive information to unauthorized parties.
- Physical security breaches: These are incidents that involve the loss or compromise of physical assets, such as equipment, documents, or buildings.
Some Tools to help you prevent Security Incdnets and breaches
- Xcitium Complete: Access operational ease with rich, built-in XDR integrations across the entire security tech stack providing XDR deep visibility, XDR real-time context, automated containment, Complete XDR detection, and Complete XDR response. Only actionable alerts/ no alert fatigue. A fully integrated Xcitium Complete XDR platform means a significant reduction in the total cost of ownership.
- Binalyze Air: 100% breach prevention is no longer a realistic expectation. This challenge is driving a trend towards blending traditional cyber security strategies with cyber resilience to ensure that, when a breach occurs, the organization has the tactical tools in place for fast and effective incident response. Digital Forensics & Incident Response (DFIR) is evolving to become fast, remote, integrated and scalable across the corporate network, pushing forensic readiness toward the centre of the security stack.
- Cekino Gardiyan: Gardiyan is a system operation management software that ensures safe monitoring and management in large working networks, informs system managers in line with corporate policies when necessary and ensures that the necessary measures are taken quickly by reporting the problems that occur with network, client and patch management software it comprises.
- ThreatMon:ThreatMon is a technology company that specializes in delivering comprehensive cybersecurity solutions tailored to the specific needs of businesses.ThreaMon is devoted to safeguarding digital assets from external threats. ThreatMon delivers an intelligence-driven cybersecurity solution that combines Threat Intelligence, External Attack Surface Management, and Digital Risk Protection to identify vulnerabilities and provide personalized security solutions for maximum security
5. Risk Scenarios
Create cyber risk scenarios that show the possible cyber threats and how they could affect your critical assets. Estimate how probable and severe these scenarios are. Here are some sample risk scenarios and how to analyze them. To be successful always Consider Real-World Incidents and Prioritize Scenarios based on recent attacks which hit a simlar sector of your orgnzation and never forget to Document and review the possible impacts .
Common cyber risk scenarios?
- Ransomware attacks: These are attacks that encrypt the victim’s data or systems and demand a ransom for their decryption or restoration. They can cause significant financial losses, operational disruptions, and reputational damage.
- Phishing attacks: These are deceptive emails or messages that trick users into sharing sensitive information or clicking on malicious links. They can lead to identity theft, data breaches, malware infections, and account compromises.
- Supply chain attacks: These are attacks that compromise a third-party vendor or service provider that has access to the target organization’s systems or data. They can expose the organization to malicious code, data theft, or unauthorized access.
- Denial-of-service (DoS) attacks: These are attacks that overwhelm a system or network with excessive traffic or requests to disrupt its normal functioning or availability. They can affect the organization’s productivity, performance, and customer satisfaction.
- Data breaches: These are incidents that expose or leak confidential or sensitive information to unauthorized parties. They can result in legal liabilities, regulatory fines, customer loss, and brand damage.
Example Scenario Ransomware Attack
- Threat: A cybercriminal distributes ransomware through a malicious email attachment or compromised website.
- Attack Vector: An employee unknowingly opens the infected attachment or visits the compromised website, triggering the ransomware download.
- Potential Impact: The ransomware encrypts critical files and data, rendering them inaccessible.
- Consequences: The organization experiences a disruption in business operations, data loss, and possible financial losses due to downtime and potential ransom payments.
6. Business Impact Analysis (BIA):
Business Impact Analysis (BIA) is a process that evaluates the potential effects of a disruption or incident on an organization’s business activities and resources. It helps to identify the most critical and valuable assets, and to develop recovery strategies and plans to ensure operational resilience and continuity. BIA involves the following steps:
- Identify and prioritize the business functions and processes that are essential for the organization’s mission and goals.
- Assess the operational and financial impacts of losing or degrading these functions and processes due to various scenarios, such as natural disasters, cyberattacks, or supply chain disruptions.
- Determine the recovery time objectives (RTOs) and recovery point objectives (RPOs) for each function and process, which indicate the maximum acceptable downtime and data loss.
- Analyze the resource requirements and dependencies for each function and process, such as personnel, equipment, software, data, and suppliers.
- Document and communicate the results and recommendations of the BIA to the relevant stakeholders and decision-makers.
BIA is an important component of business continuity management (BCM), which is the process of ensuring the organization’s ability to survive and recover from any disruption or crisis. BIA helps to align the BCM strategy and solutions with the organization’s priorities and risks. BIA also helps to improve the organization’s preparedness, resilience, and agility in the face of uncertainty and change.
How to Perform a BIA in your orgnization ?
Step 1: Project setup
It may sound like a cliche, but “People don’t plan to fail; they fail to plan”. This has some truth to it. Every project requires a solid base from the start to achieve the best outcomes.
Tips for project setup: The quality of your BIA depends on the steps you take before starting, such as getting organizational support and defining the work scope clearly.
- Executive sponsorship: Support from senior-level management is critical to ensure participation in the BIA’s production at all levels within the company as well as enacting its final conclusions and recommendations.
- Organizational education: The BIA requires input from multiple personnel and departments, so explaining why their input — and time! — is critical will increase engagement and data accuracy.
- Statement of work: To prevent the scope of the BIA becoming too wide or going off track, a statement of work will keep your BIA team focused throughout the entire process.
Step 2: Data collection
The quality of your BIA depends on the data you show. You need to collect data from various people and departments in a systematic and thorough way.
Tips for data collection: You need consistent “instruments” – that is, methods – to get your data, regardless of what kind of information you are getting during the BIA process.
- Quantitative data: This type of data can be expressed numerically — percentages and statistics, for example — and is usually generated through the use of surveys.
- Qualitative data: This data cannot be expressed numerically because it is more descriptive and based on people’s perceptions. Therefore, using interviews with a uniform set of open-ended questions will best gather this information.
Step 3: Data analysis
The quality and scope of the data you gather on people, procedures, devices, and vendors are essential, but the BIA’s value lies in its analysis. Without that, you will have many data points that lack the relevant context to show their significance. Tips for data analysis: The BIA focuses on the financial consequences of – most of the time! – extreme events, so you should be familiar with some common terms and metrics that you will apply.
- Recovery Time Objective (RTO): The amount of time required for a business process to be restored after an interruption to avoid unacceptable consequences from a lack of continuity.
- Recovery Point Objective (RPO): The amount of time during a disruption before data loss exceeds the maximum allowable threshold or tolerance.
- Level of impact: This is typically measured on a scale of 1-5, where 1 indicates minimal impact and 5 is maximum impact.
Step 4: Preparing the BIA
Sure, I can rewrite your sentence in a different way. Here is one possible option: After analyzing the data, you need to create a report that senior-level executives can comprehend easily, even if they have different levels of knowledge and skill about the detailed information you offer.
Tips for preparing the BIA: As mentioned before, the BIA shows the financial consequences of operational interruptions and the most vital processes of the company. Therefore, concentrate on the 10-15 most crucial processes rather than giving a comprehensive summary.
- Implementing recommendations: What your company does with the BIA’s recommendations is critical and will ideally lead to related activities such as a follow-up gap analysis or feasibility study.
- Scheduling the next BIA: The BIA is not a one-and-done project. At best, it provides a snapshot of potential financial liabilities and critical processes at one point in time. Be prepared to conduct BIAs on an annual basis to generate updated findings, because no business is static.
Step 5 Generating your BIA
reating your BIA By following the business impact analysis steps above, you will get the most practical outcomes for your organization and its change management plan. Also, there is no fixed way to create a BIA, but if you choose to make your own, using the best project management software will help you work more effectively and productively.
Source : I did get help from Fool.com , here is the link :
7. Data Classification :
Data classification is the process of categorizing data according to its type, sensitivity, and value to the organization. It helps to understand the potential impact and risk of data loss, theft, or compromise, and to implement appropriate security controls and policies to protect the data.
Data classification is a key component of data-centric security management, which is an approach that aims to enhance data protection regardless of where the data is stored or shared.
Data classification involves the following steps:
- Identify the data sources and types within the organization, such as customer data, employee data, financial data, intellectual property, etc.
- Define the data classification levels and criteria, such as public, internal, confidential, or restricted, based on the data’s confidentiality, integrity, and availability requirements.
- Assign the data classification labels and metadata to the data, either manually or automatically, using tools and methods such as data discovery, data tagging, or data encryption.
- Communicate and enforce the data classification policies and rules to the data owners, users, and custodians, and provide them with the necessary training and guidance.
- Monitor and audit the data classification process and outcomes, and update them as needed to reflect the changes in the data lifecycle, business needs, and regulatory obligations.
Common data classification levels and criterias
Data classification levels and criteria are the ways of organizing and labeling data according to its type, sensitivity, and value to the organization. They help to understand the potential impact and risk of data loss, theft, or compromise, and to implement appropriate security controls and policies to protect the data. Some common data classification levels are:
- Public: This is the data that is in the public domain and can be freely accessed and shared by anyone. It has no confidentiality, integrity, or availability requirements. Examples of public data are press releases, marketing materials, or public websites.
- Internal: This is the data that is intended for internal use only and should not be disclosed to unauthorized parties. It has low to moderate confidentiality, integrity, and availability requirements. Examples of internal data are employee records, policies, or procedures.
- Confidential: This is the data that has special sensitivity and should be protected from unauthorized access or disclosure. It has high confidentiality, integrity, and availability requirements. Examples of confidential data are customer data, financial data, intellectual property, or health information.
- Restricted: This is the data that is highly sensitive and should be handled on a need-to-know basis. It has very high confidentiality, integrity, and availability requirements. Examples of restricted data are trade secrets, classified information, or strategic data.
Some common data classification criteria are:
- Content-based: This is the criterion that assigns tags based on the contents of certain pieces of data. It reviews the information stored in a database, document, or other sources, and then applies labels that define the data type and a sensitivity level
- Context-based: This is the criterion that uses environmental information, such as metadata, to create data classification labels. It considers factors like the application used to author the data, the location, the author, or the date, to indicate the data type and the sensitivity level.
- User-based: This is the criterion that relies on the knowledge and judgment of a user to apply a data classification label to a specific piece of data. The user can be a data owner, a data steward, or a data creator
- Cybersecurity management: data classification demystified , read more here
8. Control Assessment:
Measure how well the current security controls and measures work. This involves checking how firewalls, intrusion detection systems, access controls, encryption, and so on are set up and used
How to measure the effectiveness of existing security controls ?
There are different methods and metrics that can be used to evaluate the performance and efficiency of security programs and controls. Some of the common ones are:
- Security metrics: These are quantitative or qualitative measures that reflect the objectives and outcomes of security processes. They can be categorized into operational statistics, performance measures, and compliance goals.
- Vulnerability assessments and penetration testing: These are techniques that identify and exploit the weaknesses and gaps in security configuration and defenses. They can help validate the security posture and resilience of the systems and networks.
- Internal audit or objective assessment: This is a process that verifies and validates the operation and implementation of security controls and policies. It can help identify any deviations, risks, or issues that need to be addressed.
Depending on the specific needs and goals of the organization, different methods and metrics can be applied and combined to measure the effectiveness of security controls. However, some general factors that should be considered are:
- Maturity: This refers to how well the security controls and processes are maintained and updated according to the best practices and standards.
- Coverage: This refers to how much of the scope and perimeter of the organization’s assets and operations are protected by the security controls
- Technical effectiveness: This refers to how well the security controls block or mitigate the threats and attacks that try to breach or compromise the organization’s systems and data.
What are some common security control frameworks?
Security control frameworks are sets of policies, guidelines, and best practices that help organizations manage their information security risks and implement appropriate security controls. There are many security control frameworks that can be used for different purposes, industries, and compliance goals. Here are some examples of common security control frameworks:
- NIST SP 800-53: This framework provides a catalog of security and privacy controls for federal information systems and organizations. It is based on the standards and guidelines developed by the National Institute of Standards and Technology (NIST). It helps organizations comply with the Federal Information Security Management Act (FISMA) and other regulations.
- CIS Critical Security Controls: This framework consists of 20 prioritized and actionable controls that address the most common and impactful cyber threats. It is developed by the Center for Internet Security (CIS), a non-profit organization that collaborates with experts from government, industry, and academia. It helps organizations improve their security posture and reduce their attack surface.
- ISO 27001: This framework defines the requirements for establishing, implementing, maintaining, and improving an information security management system (ISMS). It is based on the standards and guidelines developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It helps organizations demonstrate their commitment to information security and achieve certification.
- NIST Cybersecurity Framework: This framework provides a voluntary and flexible approach to managing cybersecurity risk for critical infrastructure sectors and other organizations. It is based on the standards and guidelines developed by NIST and other sources. It helps organizations align their security activities with their business objectives and improve their resilience.
- HIPAA Security Rule: This framework specifies the administrative, technical, and physical safeguards that covered entities and business associates must implement to protect the confidentiality, integrity, and availability of protected health information (PHI). It is based on the regulations issued by the Department of Health and Human Services (HHS) under the Health Insurance Portability and Accountability Act (HIPAA). It helps organizations comply with the HIPAA and protect the privacy and security of health information.
- PCI DSS: This framework defines the technical and operational requirements for securing cardholder data and payment transactions. It is based on the standards and guidelines developed by the Payment Card Industry Security Standards Council (PCI SSC), a global organization that represents the major payment card brands. It helps organizations comply with the PCI DSS and prevent payment card fraud.
- GDPR: This framework establishes the rules and principles for the protection of personal data of individuals in the European Union (EU) and the European Economic Area (EEA). It is based on the regulations issued by the European Parliament and the Council of the European Union under the General Data Protection Regulation (GDPR). It helps organizations comply with the GDPR and respect the rights and freedoms of data subjects.
- Understanding IT security frameworks: Types and examples click here
- Essential Guide to Security Frameworks & 14 Examples click here
- 7 Cybersecurity Frameworks That Help Reduce Cyber Risk (List & Resources) click here
- Essential Guide to Security Frameworks & 14 Example click here
9. User Awareness and Training:
To enhance the security level of the organization, assess how well the employees understand cybersecurity and provide them with security education. Use frequent cyber training and newsletters to keep them informed of the latest cyber risks, methods, and solutions.
How to enhance your cybersecurity posture via User Awareness and Training.
User Awareness and Training is a key component of any cybersecurity strategy, as it helps to educate and empower the users to protect themselves and the organization from cyber threats. Some of the benefits of User Awareness and Training are:
- It reduces the likelihood of human errors and mistakes that can compromise security, such as clicking on phishing links, using weak passwords, or sharing sensitive information.
- It increases the awareness of the current and emerging cyber risks, methods, and solutions, and how to recognize and respond to them appropriately.
- It fosters a culture of security and responsibility among the users, and encourages them to report any suspicious or anomalous activities.
Some of the tips on how to enhance your cybersecurity posture via User Awareness and Training are:
- Conduct a security assessment to identify the gaps and weaknesses in your current security posture, and the areas that need improvement.
- Define your security objectives and goals, and align them with your business needs and priorities.
- Develop a security awareness and training program that covers the topics and skills that are relevant and applicable to your organization and users, such as safe social media practices, securing mobile devices, and ensuring cyber hygiene while working remotely.
- Use various methods and formats to deliver the security awareness and training content, such as in-class training, videos, simulations, tests, posters, newsletters, and screensavers.
- Evaluate the effectiveness and impact of your security awareness and training program, and measure the changes in user behavior and security posture. Use feedback and data to improve and update your program as needed.
- Repeat and reinforce the security awareness and training program regularly, and keep it current and engaging.
10. External Threat Intelligence:
Keep up with the latest cyber risks and weaknesses that affect your organization by using external sources of threat intelligence.
Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors. It helps security teams to make better decisions, prevent cyber attacks, and respond faster to incidents. Some common sources of threat intelligence are:
- Internal data: This is information that an organization gathers from its own data, network logs, incident responses, etc. It can help to identify the specific threats and vulnerabilities that affect the organization’s systems and assets
- Open-source intelligence (OSINT): This is information from resources that are considered public domain, such as websites, blogs, forums, social media, news articles, etc. It can help to gain insights into the general trends and patterns of cyber threats and actors
- Critical vendors: These are third-party providers that offer products or services that are essential for the organization’s operations, such as cloud providers, software vendors, hardware manufacturers, etc. They can provide information on the security issues and updates related to their offerings
- Government agencies: These are official entities that collect and share information on cyber threats and incidents that affect the national or global security, such as CERTs, CSIRTs, FBI, DHS, etc. They can provide information on the high-level and strategic aspects of cyber threats and actors
- Private sources: These are specialized organizations that offer threat intelligence services or platforms, such as Xcitium, ThreatMon IBM, Palo Alto Networks, etc. They can provide information on the detailed and tactical aspects of cyber threats and actors, such as indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), threat actor profiles, etc
The Importance of CTI
Every organization has certain core objectives regardless of their size, business type, or geographical location, such as increasing their income, mitigating risks, dropping expenditures, increasing the number of clients and satisfying employees, conforming to regulations, and so on. However, information security is often overlooked and is frequently not seen as a core objective due to its cost, and as a result, the time spent on security awareness training is minimal. To combat this prevalent outlook, in this section, you are going to learn how cyber threat intelligence can have a positive impact on your organization. The key benefits of threat intelligence are as follows:
• Mitigating risk: Adversaries are constantly discovering new ways to infiltrate organizations. Threat intelligence provides visibility into these existing and emerging security hazards, which will reduce the risk of data loss, prevent or minimize the disruption of business operations, and increase regulatory compliance.
• Stopping financial loss: Security breaches can cost your organization in the form of post-incident remediation and restoration processes as well as in fines, investigations, and lawsuits. Using a threat intelligence tool can help you to make timely, informed decisions to prevent system failure and the theft of confidential data. It also assists in protecting your organization’s intellectual property and in saving your brand’s reputation
• Increasing operating success: Threat intelligence helps in the creation of a more efficient security team. Using automated threat sharing platforms to validate and correlate threat data, and to integrate the data into your organization will strengthen your security posture and can lower your IR time. Moreover, it will allow your operational workforce to work more efficiently and will save your business money.
• Reducing costs: Threat intelligence benefits any kind of organization regardless of its shape and size. It helps process threat data to better understand attackers, respond to incidents, and proactively predict and block the possible next moves of attackers. Leveraging external threat intelligence can reduce costs
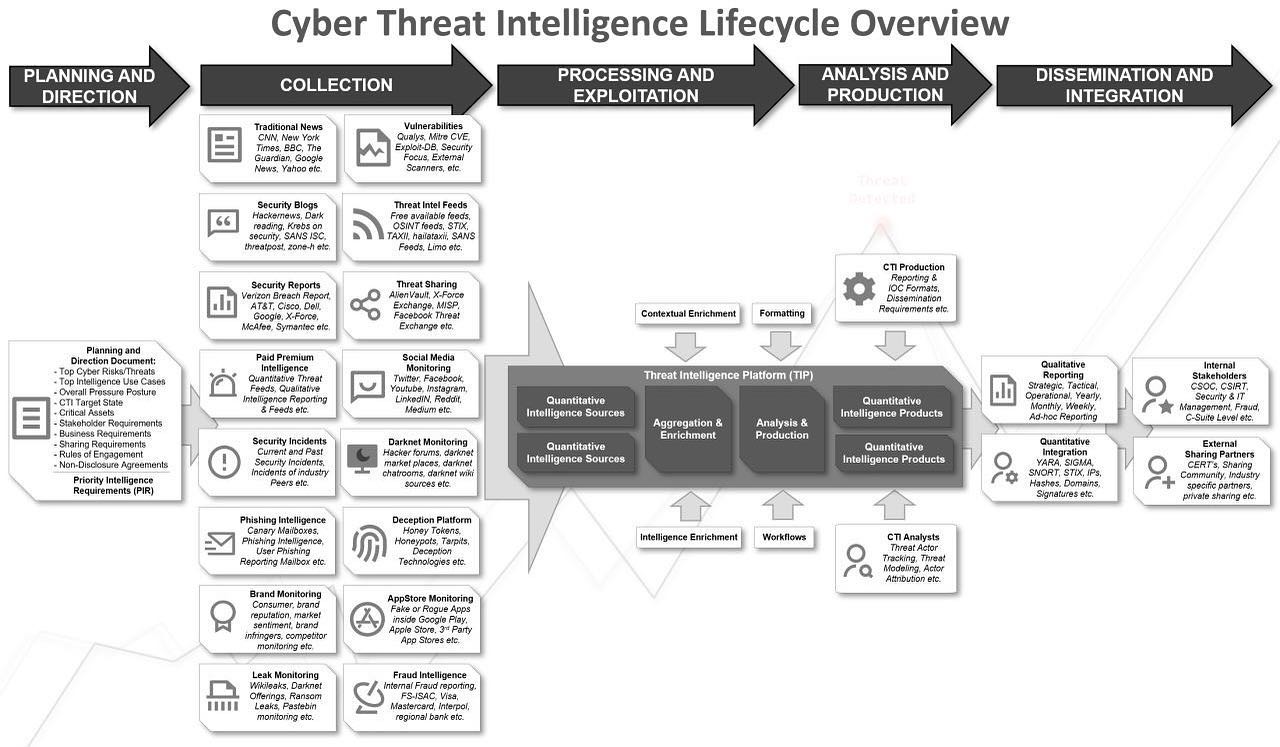
Key pointers when building your CTI Program: (Building a Cyber Threat Intelligence Platform in 5 steps)
1. Start with a “planning and direction document” to derive the Priority Intelligence Requirements (PIR)
2. If you have limited or non-existent budget start with open source/free first.
3. Be aware that a vendor collection scope might overlap but might vary in terms of quantity or quality.
4. There is no one single vendor that does everything perfectly.
5. SOAR seems one of the best product Categories out there that is able to a lot of the later CTI Lifecycle steps (although only a sub-set of SOAR vendors support TIP-like platform capabilities).
For more information:
To Learn more about Incident response : https://www.erdalozkaya.com/incident-response/
You can learn more about Cybersecurity in my book “Cybersecurity : The Beginners Guide”
more info about my book : https://www.erdalozkaya.com/cybersecurity-the-beginners-guide-3
Amazon Australia : https://www.amazon.com.au/Cybersecurity-Beginners-Dr-Erdal-Ozkaya/dp/1789616190/
Free Threat Intel resources :
https://valkyrie.comodo.com/products/
Threat Intel post from my blog ;
11. Regulatory Compliance
Ensure compliance with relevant cybersecurity regulations and standards, such as GDPR, HIPAA, PCI DSS, etc., as non-compliance can lead to significant risks.
Regulatory compliance is the adherence to the laws, standards, and guidelines that are relevant to the organization’s industry, location, and operations. It helps to ensure the protection of the organization’s data, systems, and reputation from cyber threats and legal consequences
Cybersecurity risk assessment is the process of identifying, analyzing, and evaluating the cyber risks that the organization faces, and the impact and likelihood of those risks. It helps to prioritize the mitigation and remediation actions that the organization needs to take to reduce the cyber risks to an acceptable level.
The importance of regulatory compliance in cybersecurity risk assessment is that it:
- Provides a framework and a baseline for the organization to follow when conducting the risk assessment, and to measure the effectiveness and maturity of the security controls and processes
- Helps the organization to avoid fines, penalties, lawsuits, and reputational damage that can result from non-compliance or data breaches
- Enhances the trust and confidence of the organization’s customers, partners, and stakeholders, and demonstrates the organization’s commitment to security and privacy.
- Enables the organization to leverage the best practices and guidance from the regulatory bodies and industry experts, and to benefit from the shared knowledge and experience of the compliance community.
12. Quantitative and Qualitative Analysis
Quantitative and qualitative analysis are two different methods for assessing and managing cyber risk. They have different advantages and disadvantages, depending on the context and the objectives of the risk assessment.
Quantitative analysis tries to assign objective numerical or measurable values to the components of the risk assessment, such as the likelihood and impact of cyber events, and the potential loss in dollars and cents1. This allows for a more precise and consistent evaluation of risk, and a better comparison and prioritization of different risk scenarios. However, quantitative analysis also requires more data and expertise, and may not capture all the nuances and uncertainties of cyber risk.
Qualitative analysis is based more on the subjective experience and knowledge of the assessor, and uses ordinal or relative scales, such as low, medium, and high, to rate the frequency and magnitude of cyber risk.
This allows for a more flexible and intuitive approach, and can incorporate factors that are difficult to quantify, such as reputation, trust, and compliance. However, qualitative analysis also suffers from bias and inconsistency, and may not provide enough clarity and detail for decision making and resource allocation.
Both methods can be useful for cyber risk assessment, depending on the situation and the goals. Some experts suggest using a combination of both methods, or a hybrid approach, to leverage the strengths and mitigate the weaknesses of each method.
For example, one could use qualitative analysis to identify and screen the most relevant risks, and then use quantitative analysis to perform a detailed analysis and evaluation of those risks. Alternatively, one could use quantitative analysis to estimate the range and distribution of possible losses, and then use qualitative analysis to factor in the qualitative aspects and influences of risk.
13. Continuous Monitoring
Continuous Monitoring is a technique that automates the process of regularly examining and assessing an organization’s security measures. It helps the organization discover vulnerabilities and address them before intruders exploit them.
Continuous Monitoring is part of a comprehensive risk management strategy that provides ongoing assurance that the security controls are aligned with the organizational risk tolerance and the information needed to respond to risk in a timely manner.
Continuous Monitoring can also reduce the need for a separate reauthorization process, as it fulfills the three-year security reauthorization requirement.
Some of the best practices for Continuous Monitoring in cyber risk assessment are:
- Identify what needs to be protected and prioritize the most critical assets and data.
- Patch vulnerabilities regularly and keep the systems and software updated.
- Continuously monitor all endpoints, including devices, networks, applications, and user behaviors.
- Identify changes in standard user behavior and flag any anomalies or suspicious activities.
- Continuously monitor third parties and suppliers that have access to the organization’s data or systems.
- Leverage data and analytics to measure the effectiveness of the security controls and the risk posture.
- Foster a culture of security awareness and education among the employees and stakeholders.
- These are some of the best practices that can help you implement Continuous Monitoring effectively and reduce the cyber risk for your organization.
14. Third-Party Assessments
Third-Party Assessments are evaluations of the cybersecurity practices and policies of external partners, vendors, or suppliers that have access to an organization’s data or systems.
They are important for cyber risk assessment because they can help identify and mitigate the potential threats and vulnerabilities that third parties may introduce to the organization’s network and information security.
Third-Party Assessments can also help the organization comply with industry standards and regulations, such as PCI DSS, HIPAA, GDPR, and others, that require due diligence and oversight of third-party relationships Some of the benefits of conducting Third-Party Assessments are:
- Reducing the likelihood and impact of data breaches and cyberattacks that originate from or exploit third-party weaknesses
- Enhancing the trust and reputation of the organization and its partners by demonstrating a commitment to cybersecurity and privacy
- Improving the performance and efficiency of the organization and its partners by streamlining the data flow and security controls
- Saving costs and resources by avoiding fines, lawsuits, remediation, and reputational damage that may result from third-party incidents
- Some of the steps involved in conducting Third-Party Assessments are: Mapping the data flow and identifying the third parties that have access to the organization’s data or systems.
- Assessing the level of risk and criticality of each third party based on the type, volume, and sensitivity of the data they handle
- Reviewing the security policies, procedures, and practices of each third party and verifying their compliance with the relevant standards and regulations
- Testing the security controls and measures of each third party and validating their effectiveness and adequacy
- Reporting the findings and recommendations of the assessment and communicating them to the relevant stakeholders
- Monitoring and auditing the third-party security posture and performance on a regular basis and updating the assessment as needed.
- Third-Party Assessments are a vital component of cyber risk assessment and management. They can help the organization protect its data and systems from external threats and enhance its security posture and resilience.
What are some challenges of Third-Party Assessments?
- Lack of resources or expertise: Conducting effective third-party risk assessments can be challenging due to a lack of resources or expertise needed for proper implementation. Additionally, it may be difficult to obtain accurate information about a vendor’s background which can make it hard to properly evaluate them before entering into a contract agreement.
- Slow and cumbersome process: “Organizations struggle to manage third-party risk programs for various reasons, but one of the main challenges is a slow and cumbersome assessment process,” the research explained. “Assessments are typically lengthy to complete and often lack the critical information necessary to make a sound decision on vendor suitability.”
- Data privacy concerns: Data privacy concerns will continue to top TPRM priorities in 2020, but those lists will be overstuffed with other pressing matters, including resilience, nth party risk management, new and emerging operational risks, challenges stemming from the rapid convergence of information technology (IT) and operational technology (OT), vexing cyber-attacks and a range of improvement initiatives, starting with continuous monitoring.
- Inconsistent standards and regulations: Different industries and regions may have different standards and regulations for third-party risk management, such as PCI DSS, HIPAA, GDPR, and others. This can create confusion and complexity for organizations that have to comply with multiple and sometimes conflicting requirements
15. Regular Updates:
Regular Updates are essential for cyber risk assessment because they help keep the systems and software updated with the latest security patches and fixes. Regular Updates can prevent or mitigate the exploitation of known vulnerabilities by malicious actors, and reduce the likelihood and impact of cyberattacks and data breaches.
Regular Updates can also improve the performance and efficiency of the systems and software, and ensure their compatibility and interoperability with other components. Some of the benefits of Regular Updates are:
- Enhancing the security posture and resilience of the organization and its assets.
- Complying with the industry standards and regulations that require regular updates, such as PCI DSS, HIPAA, GDPR, and others.
- Saving costs and resources by avoiding downtime, remediation, and reputational damage that may result from outdated systems and software.
- Some of the challenges of Regular Updates are: Lack of resources or expertise to perform regular updates effectively and efficiently.
- Slow and cumbersome process that may disrupt the normal operations and services of the organization.
- Data privacy concerns that may arise from sharing sensitive information with third-party providers or cloud services that perform the updates.
- Inconsistent standards and regulations that may create confusion and complexity for the organization that has to comply with multiple and sometimes conflicting requirements.
Regular Updates are a vital component of cyber risk assessment and management. They can help the organization protect its data and systems from external threats and enhance its security posture and resilience. You can learn more about Regular Updates and their importance by following the links in the references.
Cyber risk management requires regular cybersecurity risk assessments. These assessments help security teams evaluate the risks and choose the best ways to reduce or eliminate them. They also provide security and business leaders with reliable information to make sound business decisions, which is not possible with outdated security data. I hope this Step by Step Guide will help you a bit :
Risk assessment a step by step guide
While the specific steps may vary depending on the chosen approach, a general cyber risk assessment process can be summarized as follows:
- Define the scope and objectives of the assessment, such as the assets, systems, processes, and data that need to be protected, the regulatory requirements that need to be met, and the stakeholders that need to be involved.
- Identify the threats and sources of risk, such as malicious actors, natural disasters, human errors, or technical failures, that could exploit the vulnerabilities and cause harm to your organization.
- Identify the vulnerabilities and weaknesses, such as outdated software, misconfigured settings, or lack of training, that could expose your organization to the threats and increase the likelihood of an attack.
- Analyze the impact and likelihood of the risks, such as the potential damage, disruption, or loss that could result from an attack, and the probability that the attack will occur.
- Evaluate and prioritize the risks, based on their severity, urgency, and frequency, and compare them to your risk appetite and tolerance levels.
- Implement and monitor the risk mitigation strategies, such as preventive, detective, corrective, or compensating controls, that can reduce the impact or likelihood of the risks, or transfer or accept them as part of your business operations.
- Review and update the risk assessment, based on the changes in your environment, the feedback from your stakeholders, and the results of your monitoring activities.
Keywords
risk assessment a stepbystep guide – security risk assessment a step by step – cyber security risk assessment – Risk level – risk assessment a stepbystep guide security risk assessment a stepbystep risk assessment a stepbystep guide
How do you perform a cybersecurity risk assessment?
What are the five general steps of a security risk assessment?
What is the formula for cyber risk assessment?
What are the 5 steps cybersecurity?