The
NIST
Cybersecurity
Framework
(CSF)
is
a
set
of
standards
and
guidelines
for
managing
and
protecting
critical
infrastructure.
It
provides
a
common
language
and
approaches
for
organizations
to
manage
and
reduce
cybersecurity
risk.
The
framework
is
designed
to
be
flexible
and
adaptable,
so
organizations
can
tailor
their
approach
to
meet
their
specific
needs
and
constraints.
The
key
components
of
the
NIST
CSF
include
the
following:
-
Identifying,
Protecting,
Detecting,
Responding,
and
Recovering
from
cyber-attacks. -
Providing
a
structured
approach
to
managing
and
reducing
cybersecurity
risk
by
aligning
with
business
drivers
and
processes. -
Providing
a
common
language
for
discussing
cybersecurity
risk
and
informing
decision-making. -
Supporting
collaboration
among
organizations,
sectors,
and
government
to
share
information
and
coordinate
responses
to
cyber
threats.
The
NIST
CSF
provides
a
risk-based
approach
to
cybersecurity,
and
organizations
can
use
it
to
identify
and
prioritize
areas
for
improvement.
It
can
also
be
used
to
assess
the
effectiveness
of
existing
cybersecurity
practices
and
to
support
continuous
improvement.
The
NIST
CSF
is
widely
adopted
by
public
and
private
organizations
and
is
considered
a
best
practice
for
managing
and
reducing
cybersecurity
risk.

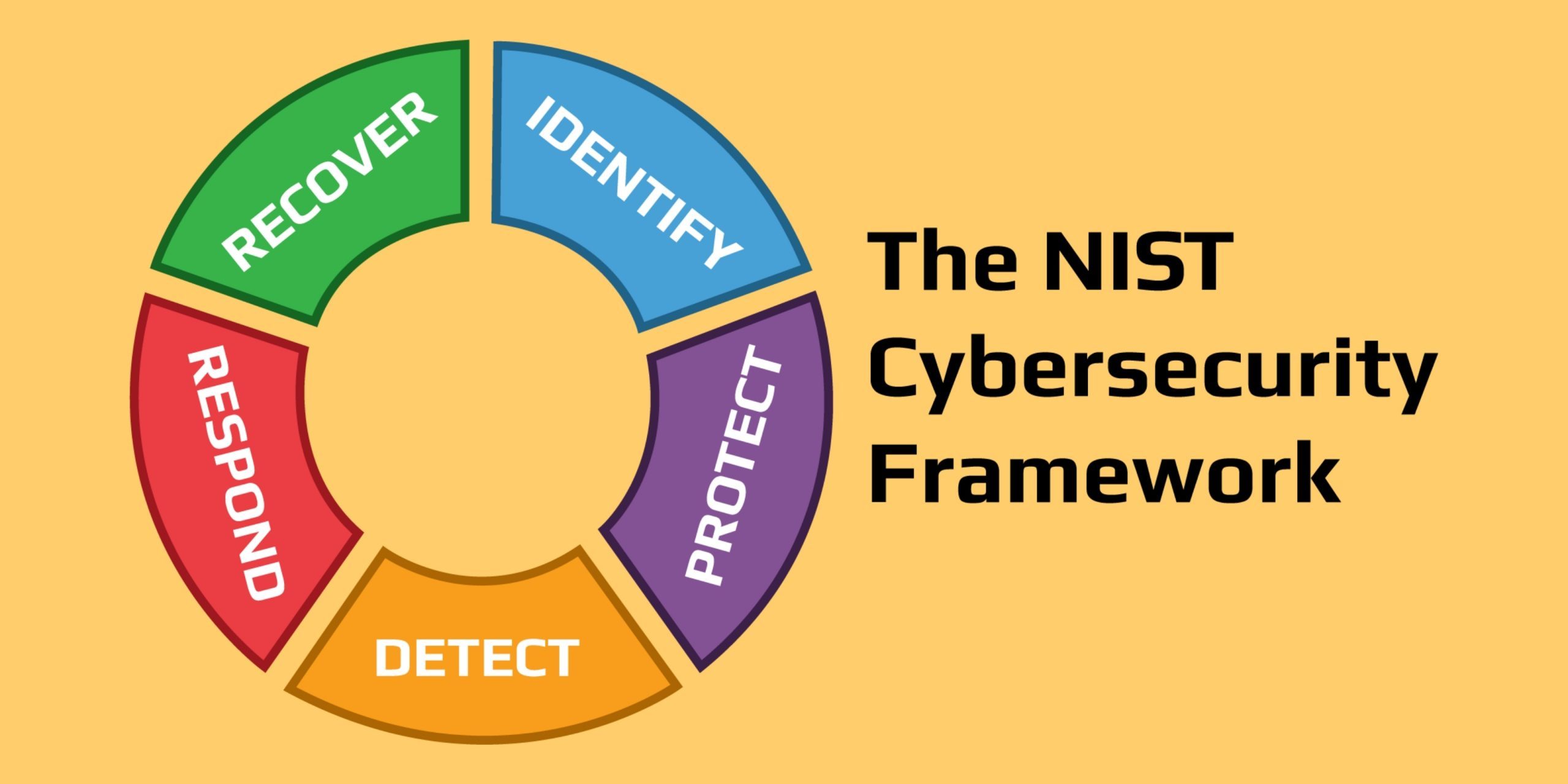
Cybersecurity
Framework
5
Core
Functions
of
the
NIST
Cybersecurity
Framework
The
NIST
Cybersecurity
Framework
(CSF)
is
built
around
five
core
functions.
These
core
functions
provide
a
structure
for
organizations
to
effectively
manage
and
reduce
their
cybersecurity
risk
by
addressing
each
key
element
of
the
risk
management
process.
The
NIST
CSF
is
designed
to
be
flexible
and
adaptable.
Organizations
can
use
the
core
functions
to
align
with
their
unique
needs
and
risk
profile
and
continuously
improve
their
cybersecurity
posture.
Identify:
Establishing
the
context
of
the
organization’s
cybersecurity
risk
and
developing
an
understanding
of
the
assets,
threats,
vulnerabilities,
and
impacts.
-
Establish
the
organizational
context: Understand
the
organization’s
goals,
mission,
and
operating
environment. -
Define
the
assets: Identify
the
systems,
data,
and
other
assets
critical
to
the
organization’s
operations. -
Assess
the
threats: Evaluate
the
potential
risks
and
threats
to
the
organization’s
assets,
including
natural
disasters,
cyber-attacks,
and
other
disruptions. -
Assess
the
vulnerabilities: Evaluate
the
potential
weaknesses
in
the
organization’s
systems
and
processes
that
attackers
could
exploit. -
Evaluate
the
impacts: Determine
the
potential
impact
on
the
organization
if
a
threat
materializes,
including
financial
losses,
reputational
damage,
and
other
consequences. -
Develop
a
risk
management
strategy: Based
on
the
assessment
results,
develop
a
risk
management
strategy
to
address
the
most
significant
risks
to
the
organization.

Protect:
Implementing
and
maintaining
appropriate
and
effective
safeguards
to
ensure
the
delivery
of
critical
infrastructure
services.
-
Implement
security
controls: Establish
and
implement
technical,
physical,
and
administrative
controls
to
protect
the
organization’s
assets. -
Evaluate
the
effectiveness
of
the
controls: Regularly
assess
the
effectiveness
of
the
security
controls
and
make
changes
as
necessary
to
ensure
that
they
are
providing
adequate
protection. -
Monitor
for
new
threats: Continuously
monitor
for
new
and
evolving
threats,
and
adapt
the
security
controls
as
necessary
to
ensure
they
remain
effective. -
Conduct
regular
risk
assessments: Conduct
regular
risk
assessments
to
ensure
that
the
security
controls
remain
aligned
with
the
organization’s
risk
profile
and
risk
management
strategy.

Detect:
Developing
and
implementing
the
appropriate
activities
to
identify
the
occurrence
of
a
cybersecurity
event.
-
Establish
detection
processes: Establish
processes
for
detecting
and
reporting
cybersecurity
events,
including
using
security
tools
and
monitoring
systems. -
Monitor
the
environment: Monitor
the
organization’s
systems
and
networks
for
signs
of
a
cybersecurity
event. -
Implement
incident
response
plans: Develop
and
implement
incident
response
plans
to
ensure
that
the
organization
is
prepared
to
respond
quickly
and
effectively
in
the
event
of
a
cyber-attack. -
Evaluate
the
detection
processes: Regularly
evaluate
the
effectiveness
of
the
detection
processes
and
make
changes
as
necessary
to
improve
the
speed
and
accuracy
of
incident
detection.

Respond:
Developing
and
implementing
the
appropriate
activities
to
take
action
regarding
a
detected
cybersecurity
event.
-
Implement
incident
response
procedures: Establish
and
implement
procedures
for
responding
to
cybersecurity
events,
including
activating
incident
response
teams. -
Contain
the
incident: Take
steps
to
contain
the
incident
and
prevent
further
damage,
including
isolating
affected
systems
and
shutting
down
malicious
processes. -
Collect
and
preserve
evidence: Collect
and
preserve
evidence
of
the
incident
to
support
investigations
and
provide
information
for
recovery
efforts. -
Notify
stakeholders: Notify
stakeholders,
including
management,
customers,
and
law
enforcement,
as
appropriate,
of
the
incident. -
Begin
recovery
efforts: Begin
the
process
of
restoring
normal
operations
as
soon
as
possible,
and
work
to
minimize
the
impact
of
the
incident
on
the
organization.
Recover:
Developing
and
implementing
the
appropriate
activities
to
maintain
plans
for
resilience
and
to
restore
any
capabilities
or
services
that
were
impaired
due
to
a
cybersecurity
event.
-
Develop
recovery
plans: Develop
and
implement
recovery
plans
for
the
organization’s
systems,
processes,
and
data
in
the
event
of
a
cyber-attack. -
Test
recovery
plans: Test
the
recovery
plans
to
ensure
that
they
are
effective
and
that
the
organization
is
prepared
to
respond
quickly
and
effectively
in
the
event
of
an
actual
incident. -
Restore
normal
operations: Restore
normal
operations
as
quickly
as
possible,
and
work
to
minimize
the
impact
of
the
incident
on
the
organization. -
Review
and
improve: Review
the
incident
and
recovery
efforts,
and
make
changes
to
the
organization’s
security
posture
and
risk
management
strategy
as
necessary
to
improve
future
performance. -
Communicate
with
stakeholders: Communicate
the
results
of
the
incident
and
recovery
efforts
to
stakeholders,
including
management
and
customers.

Why
should
organizations
use
the
NIST
Cybersecurity
Framework?
Organizations
should
use
the
NIST
Cybersecurity
Framework
(CSF)
because
it
provides
a
comprehensive
approach
to
managing
and
reducing
cybersecurity
risk.
The
CSF
provides
a
structure
for
organizations
to
understand
and
manage
their
risk
by
addressing
each
key
element
of
the
risk
management
process.
The
benefits
of
using
the
NIST
CSF
include
the
following:
Improved
risk
management:
The
NIST
CSF
provides
a
systematic
approach
to
identifying,
protecting,
detecting,
responding
to,
and
recovering
from
cybersecurity
threats,
which
helps
organizations
manage
and
reduce
their
risk.
Improved
alignment
with
business
goals:
The
CSF
is
designed
to
be
flexible
and
adaptable,
so
organizations
can
use
it
to
align
with
their
unique
needs
and
risk
profile
and
ensure
that
their
cybersecurity
efforts
are
aligned
with
their
business
goals.
Improved
compliance:
Many
regulations,
including
the
Federal
Risk
and
Authorization
Management
Program
(FedRAMP)
and
the
Health
Insurance
Portability
and
Accountability
Act
(HIPAA),
require
organizations
to
implement
a
risk
management
program
based
on
a
framework
like
the
NIST
CSF.
Improved
collaboration:
The
NIST
CSF
promotes
collaboration
between
organizations,
stakeholders,
and
the
government,
which
can
help
improve
critical
infrastructure
security
and
reduce
cyber-attacks
risk.
Improved
resilience:
The
CSF
helps
organizations
prepare
for
and
recover
from
cyber-attacks,
which
can
improve
the
organization’s
overall
resilience
and
minimize
the
impact
of
a
security
breach.
Overall,
the
NIST
CSF
provides
a
comprehensive
approach
to
managing
and
reducing
cybersecurity
risk
that
can
help
organizations
improve
their
risk
management,
alignment
with
business
goals,
compliance,
collaboration,
and
resilience.
In
conclusion,
the
NIST
Cybersecurity
Framework
provides
a
comprehensive
approach
to
managing
and
reducing
cybersecurity
risk,
making
it
an
essential
tool
for
organizations
looking
to
strengthen
their
cybersecurity
posture.
The
framework’s
five
core
functions
provide
a
roadmap
for
identifying
and
mitigating
cybersecurity
risks,
improving
resilience,
and
aligning
cybersecurity
efforts
with
business
goals.
By
using
the
NIST
Cybersecurity
Framework,
organizations
can
proactively
address
potential
threats
and
reduce
the
risk
of
cyber-attacks,
leading
to
a
more
secure
and
prosperous
future
in
the
digital
age.
So,
whether
you’re
a
large
corporation
or
a
small
business,
incorporating
the
NIST
Cybersecurity
Framework
into
your
security
strategy
can
be
the
recipe
for
cybersecurity
success.
Unleash
The
Power
of
Open-Source
Security
with
Our
Free
Open
EDR
Open
Source
Endpoint
Detection
and
Response
(EDR) !
Our
Free
OpenEDR
is
designed
to
give
you
peace
of
mind
to
protect
your
business
from
cyber
threats.
With
its
powerful
threat
detection
and
response
capabilities,
you
can
rest
assured
that
your
network
is
secure
from
even
the
most
advanced
attacks.
With
our
FREE
Open
Source
EDR,
you
can
benefit
from
the
advantages
and
features
of
open-source
technology,
such
as
cost-effectiveness,
flexibility,
and
transparency.
Our
solution
is
community-driven
and
always
up
to
date
with
the
latest
security
features.
Deploy
Our
Free
OpenEDR
To:
-
Enable
continuous
and
comprehensive
endpoint
monitoring. -
Correlate
and
visualize
endpoint
security
data. -
Perform
malware
analysis,
anomalous
behavior
tracking,
and
in-depth
attack
investigations. -
Enact
remediations
and
harden
security
postures
to
reduce
risk
on
endpoints. -
Stop
attempted
attacks,
lateral
movement,
and
breaches.

Security

Fundamentals
Open
EDR
Training
Click
here
to
get
your
certification
Cybersecurity
Frameworks
A
cyber
security
framework
provides
national
and
industry
security
leaders
a
common
language
and
a
set
of
standards
that
can
help
them
evaluate,
improve,
and
monitor
their
security
posture.
Using
a
framework
makes
it
easier
to
define
the
processes
and
steps
organizations
should
take
to
assess,
monitor,
and
mitigate
cyber
security
risks.
It
can
also
help
organizations
evaluate
the
security
posture
of
their
vendors
or
partners,
and
coordinate
security
with
third
parties.
Generally
speaking,
cyber
security
frameworks
are
voluntary,
but
they
can
be
extremely
important
for
organizations
that
need
to
comply
with
regulations
and
industry
standards
that
include
cyber
security
requirements.
These
frameworks
are
an
essential
stepping
stone
on
the
way
to
achieving
compliance.
Source:
Tutorial
Spot,
Nowadays,
safeguarding
precious
data
from
cybercriminals
has
never
been
so
essential
in
this
modern
world.
An
organization
has
vast
data,
and
it
is
challenging
to
manage
all
that
without
a
structured
plan.
Any
organization’s
IT
professionals
cannot
do
it
on
their
own.
Hence,
they
rely
on
something
called
Cyber
Security
Framework.
We
will
discuss
many
of
these
Cyber
Security
Frameworks
here,
and
you’ll
walk
away
knowing
all
the
core
concepts
of
these
frameworks.
Click
here
to
read
the
rest
Keywords
story
of
cybersecurity
–
nist
cybersecurity
metrics
–
How
to
measure
cybersecurity
success?
cybersecurity
and
information
technology





