
The manual analysis of logs and event data has become increasingly challenging due to the escalating cyber threat landscape. Therefore, organizations now depend on Security Information and Event Management tools, commonly known as SIEM tools, to collect and analyze these data types for valuable security insights.
LogRhythm and Splunk stand as prominent contenders in the SIEM market, with many organizations opting for their deployment to monitor security events, identify threats, and fortify their security stance. However, what truly sets them apart from each other?
This article offers an in-depth comparison of LogRhythm and Splunk, examining their characteristics, pricing structures, advantages, and disadvantages.
- LogRhythm: Ideal for encompassing all SIEM needs, inclusive of User and Entity Behavior Analytics and centralized log management.
- Splunk: Known for its high level of customization, robust log analytics capabilities, and advanced threat detection functionalities.
LogRhythm vs Splunk: Feature Comparison Table
The table below outlines the key features provided by LogRhythm and Splunk.
| Real-time Monitoring | ||
| Advanced Threat Detection | ||
| Centralized Management Dashboards | ||
| Deployment Ease | ||
| Customizable Dashboard | ||
| Threat Remediation Features | ||
| User and Entity Behavior Analytics (UEBA) | ||
|
|
LogRhythm vs Splunk: Pricing Comparison
LogRhythm Pricing
LogRhythm adopts a flexible pricing and licensing model that includes unlimited log resources and users. Customers can opt for perpetual, subscription, or unlimited data pricing plans.
- For specific details on LogRhythm’s pricing, it is advisable to reach out to their sales team for a personalized quotation.
Splunk Pricing
Similar to LogRhythm, Splunk follows a flexible pricing approach, as detailed below.
- Workload: Charges are determined based on the types of workload executed on the Splunk Platform by customers.
- Ingest: Customers are billed according to the volume of data imported into the Splunk Platform.
- Entity: This plan is structured around the number of hosts utilizing Splunk.
- Activity-based: Charges depend on the activities monitored within Splunk.
In addition to these pricing models, Splunk users have the opportunity to receive an estimate of their charges when using Splunk.
LogRhythm vs Splunk: Feature Analysis
Below is a direct comparison between LogRhythm and Splunk based on various features.
Deployment Alternatives
LogRhythm users can opt for versatile deployment options to align with different requirements and objectives. These selections include self-hosting, infrastructure as a service (IaaS), or engagement with a managed security service provider. LogRhythm Cloud offers a software-as-a-service (SaaS) alternative for cloud deployment.
On the contrary, Splunk users can choose between a distributed search or single instance deployment. Splunk Software is available in cloud, on-premise, and multi-cloud formats.
Data Analysis
LogRhythm’s Machine Data Intelligence (MDI) function aids users in deciphering their data effectively. This functionality enriches data at ingestion, making it more understandable and enhancing data analysis precision.
Splunk boasts a data analytic engine tailored to collect, index, and handle large data volumes, irrespective of the data format. Its real-time data analytics capacity enables dynamic schema generation, eliminating the need for extensive data structure understanding and enabling easy data querying and exploration without prior knowledge.
Personalized Dashboard
LogRhythm empowers users to design dashboards to fit their preferences. Users can customize report templates, create tailored log detail reports, revert default logos to reports, manage scheduled reports, rename custom dashboards, and assign dashboard privacy settings as per their needs.
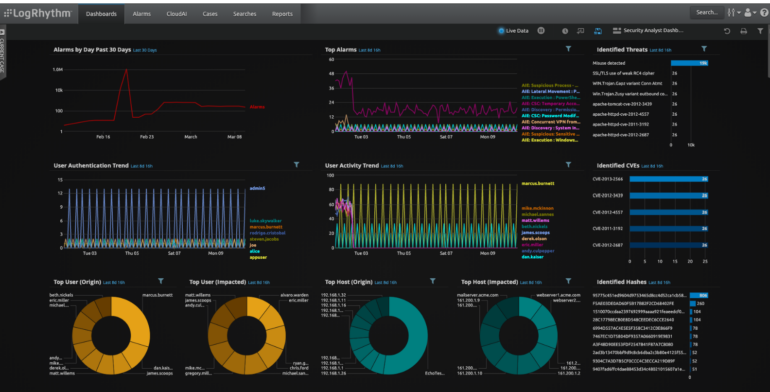
Moreover, Splunk presents a highly adaptable dashboard. Users have the option to select from a variety of charts and alternate visualizations to take action on their data. For example, users can combine reports, graphs, and reusable panels to gain more insights from their data. Moreover, there is also the opportunity to customize data for diverse scenarios and users, such as corporate, security analysts, auditors, developers, and operations teams — to facilitate their processes.
Centralized log and incident management
LogRhythm provides centralized log and incident management services which aid users in gathering, storing, and examining logs/events from various origins for auditing, adherence, and investigative aims. Furthermore, there are case management tools and playbooks that provide incident management features to streamline log and incident handling processes.
In a similar vein, Splunk also delivers a centralized log management service enabling users to aggregate and archive logs from a range of sources in a unified repository. Additionally, users can encrypt the collected logs to mitigate unauthorized access.
Advanced threat detection
Both LogRhythm and Splunk equip users with advanced threat detection functionalities. LogRhythm accomplishes this by merging machine analytics and search analytics to provide users with a risk-centric monitoring approach that automatically detects and prioritizes attacks and threats.
Splunk leverages machine learning to detect advanced threats and other 1790+ pre-configured detections pertaining to frameworks such as MITRE ATT&CK, NIST, CIS 20, and Kill Chain.
SEE: Securing Linux Policy (TechRepublic Premium)
LogRhythm strengths and weaknesses
Highlighted below are the notable aspects of the LogRhythm SIEM solution.
Advantages
- Users can align their security and IT operations with established frameworks like MITRE ATT&CK and NIST.
- Provides real-time visibility across environments for effortless detection and ranking of potential threats.
- Supports centralized log management.
- Offers User and Entity Behavior Analytics capabilities (UEBA).
- Includes complimentary training videos.
Disadvantages
- Complexity in pricing structures.
- The customization options are limited.
- Lack of a trial version.
Splunk advantages and disadvantages
Highlighted below are the benefits and drawbacks of Splunk.
Advantages
- Robust log scrutiny for log supervision and inspection.
- Provides a 60-day costless trial.
- Cutting-edge threat recognition using artificial intelligence and over 1300 advanced detections for well-known frameworks like NIST, CIS 2, MITRE ATT&CK, and Kill Chain.
- Access to more than 50 complimentary training courses and certifications.
- Automated security content updates for users issued from the Splunk Threat Research Team.
- Alerting based on risk assists users in associating incident alerts with cybersecurity frameworks and linking risks to users and systems.
- Incorporation with prevalent cloud services, including AWS, Azure, and Google Cloud Platform.
Disadvantages
- Commencing with Splunk can be challenging.
- Lack of transparent pricing details to inform potential users about the expected charges.
Is LogRhythm or Splunk the proper choice for your enterprise?
The decision between LogRhythm and Splunk relies on various factors, such as the size of the enterprise, financial plan, distinct security prerequisites, and proficiency. LogRhythm’s all-encompassing platform, UEBA functionalities, straightforward interface, and effortless deployment position it as a fitting selection for businesses seeking a unified SIEM solution with sophisticated threat detection capabilities.
Conversely, Splunk’s potent log supervision and scrutiny characteristics, scalability, and personalization choices make it appealing for companies pursuing highly adaptable and scalable log analytics capabilities. Moreover, Splunk is more suitable for proficient technical users.
Approach
This evaluation is grounded on an exhaustive examination of LogRhythm and Splunk’s features, capabilities, and pricing information, as well as feedback from users. It is crucial to acknowledge that the appropriateness of each SIEM tool may fluctuate based on your organization’s particular needs and specifications. As such, it is recommended to assess both solutions to establish their compatibility with your enterprise’s security strategy.
This article was initially issued in August 2023. Luis Millares updated it in January 2025.





