
As part of an extensive global campaign, the U.S. Department of Justice, Federal Bureau of Investigation, and various international law enforcement agencies have launched “Operation Magnus” aimed at dismantling RedLine Stealer and META, two of the most infamous information-stealing malware networks in the world.
A press release issued on Oct. 29, detailed the outcomes of the operation, including the confiscation of multiple servers, the unsealing of charges against a RedLine Stealer developer, and the apprehension of two individuals in Belgium.
RedLine and META Information Stealers
RedLine Stealer and META are categorized as “infostealers,” designed to gather sensitive user data. RedLine Stealer was first identified in 2020, while META emerged in 2022.
In an interview, a representative of META disclosed that the malware’s development initially depended on sections of RedLine Stealer’s source code, obtained through a purchase. Both malwares have the ability to extract sensitive data from compromised systems, including:
- Credentials for online platforms, such as email accounts.
- Financial details like credit card numbers and banking credentials.
- Session cookies for impersonation on online services.
- Cryptocurrency wallets.
SEE: Strategies for Building an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Both malwares also offer functions to evade multi-factor authentication. The stolen data can be utilized by the malware operator or traded as “logs” in underground cybercrime platforms.
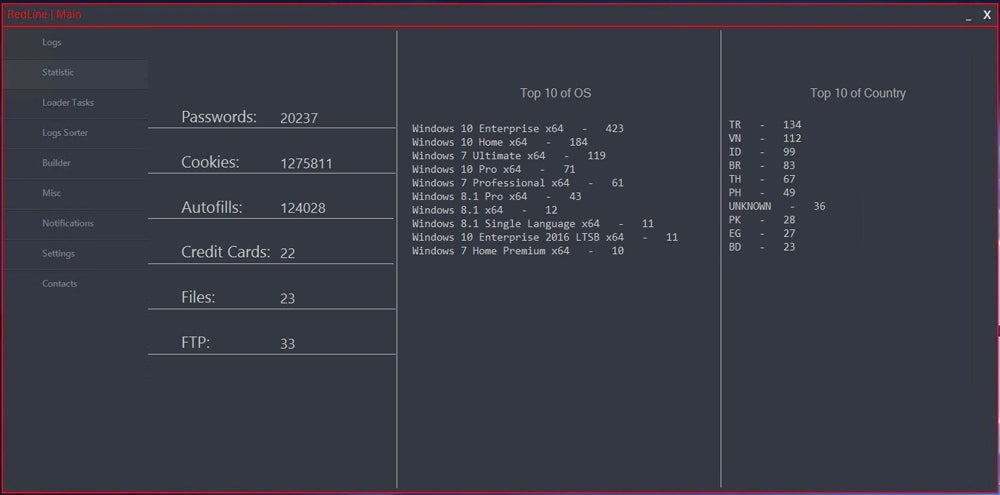
RedLine Stealer and META have infected millions of devices globally, compromising a significant number of credentials. According to Specops Software, RedLine Stealer gathered over 170 million passwords in just six months, while META exfiltrated 38 million passwords during the same timeframe.
The DOJ press release highlighted RedLine Stealer’s involvement in breaching major corporations.
Malware-as-a-Service (MaaS) Business Model
Both malware variants are retailed through a Malware-as-a-Service business approach, enabling cybercriminals to procure licenses for deploying different versions of the malware in their own attack campaigns. This can be achieved through malicious emails, malvertising, fake software downloads, software sideloading, and instant messaging. Various social engineering tactics, including false Windows updates, are employed by cybercriminals to infect targets.
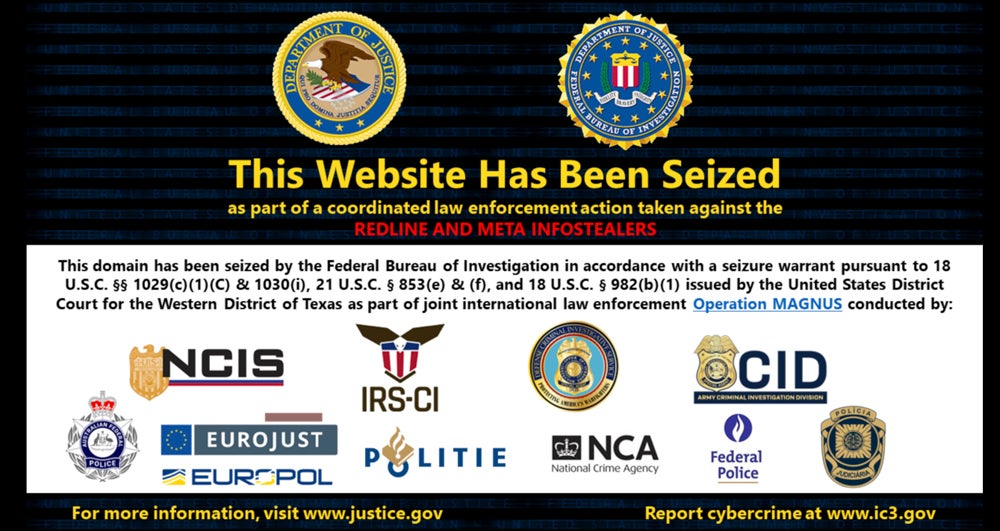
Shutdown of Multiple Servers and Communication Channels
A warrant issued by the Western District of Texas authorized the authorities to seize two control domains used by RedLine Stealer and META.
Both domains now display information relating to the enforcement action.
Authorities in the Netherlands have closed down three servers, and Belgian officials have taken down several communication channels related to RedLine Stealer and META.
Furthermore, a platform concerning Operation Magnus provides information and assistance to victims. A presentation on the site delivers a stern warning to cybercriminals utilizing RedLine or META, revealing a list of aliases referred to as VIPs — “Very Important to the Police” — culminating in an image of handcuffs with the message: “We are looking forward to seeing you soon!”
The site also offers an internet scanner for RedLine/META infections by cybersecurity firm ESET.
The U.S. Department of Justice has unveiled accusations against Maxim Rudometov, one of the developers and administrators of the RedLine Stealer malware, who routinely accessed and supervised the infrastructure. Rudometov has ties to various digital currency wallets used for collecting and laundering payments from RedLine clients.
Two other individuals have been detained in Belgium, though details about one’s release have not been disclosed to the public.
How to safeguard against information stealers
Information stealers can infiltrate computers through various means, emphasizing the importance of updating systems and software to prevent exploitation of a known vulnerability.
Additionally, organizations can fortify defenses against cybercriminals by:
- Integrating Security solutions and antivirus programs across all systems.
- Enforcing multi-factor authentication to enhance security for authentication-reliant services.
- Changing all passwords upon system compromise, a crucial step once the stealer has been eradicated from the system.
Users are advised against reusing the same password for multiple services. Utilizing password management tools is highly effective in maintaining a single robust password for each service or tool, and should be a mandatory practice within organizations.
Disclaimer: I am employed by Trend Micro, but the opinions expressed in this post are my own.


