
Recent findings from both Microsoft’s Digital Crimes Unit and the U.S. Department of Justice unveil an operation aimed at disrupting over 100 servers utilized by “Star Blizzard” — a Russian cyber threat entity specialized in infiltrating email accounts to extract sensitive information or hamper the targets’ operations.
Unveiling the Identity of Star Blizzard
Star Blizzard, also known as Seaborgium, Callisto Group, TA446, Coldriver, TAG-53, or BlueCharlie, is reportedly linked to the Russian Federal Security Service (FSB) Centre 18 as stated by various government bodies worldwide.
Operating since at least late 2015, Star Blizzard, as identified in a report by cybersecurity firm F-Secure, has been targeting military personnel, government officials, as well as think tanks and journalists in Europe and the South Caucasus, with a primary focus on gathering intelligence concerning foreign and security policies in those regions.
Key findings suggest:
- Starting from 2019, the cyber threat group has been directing its attacks towards defense and governmental organizations in the U.S. along with sectors such as academia, NGOs, and politicians.
- In 2022, the group extended its scope to include defense industry targets and facilities under the US Department of Energy.
- Since January 2023, Microsoft has pinpointed 82 diverse targets of the cyber threat group, averaging approximately one attack per week.
EXPLORE: Building an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Operational Approach
Star Blizzard’s strategy involves creating infrastructure to execute spear phishing campaigns, primarily aimed at the personal email accounts of selected individuals, which typically have weaker security measures compared to professional email accounts.
As highlighted by Steven Masada, Assistant General Counsel at Microsoft, in a press statement: “Star Blizzard exhibits persistence by meticulously studying their targets and masquerading as trusted contacts to achieve their objectives.”
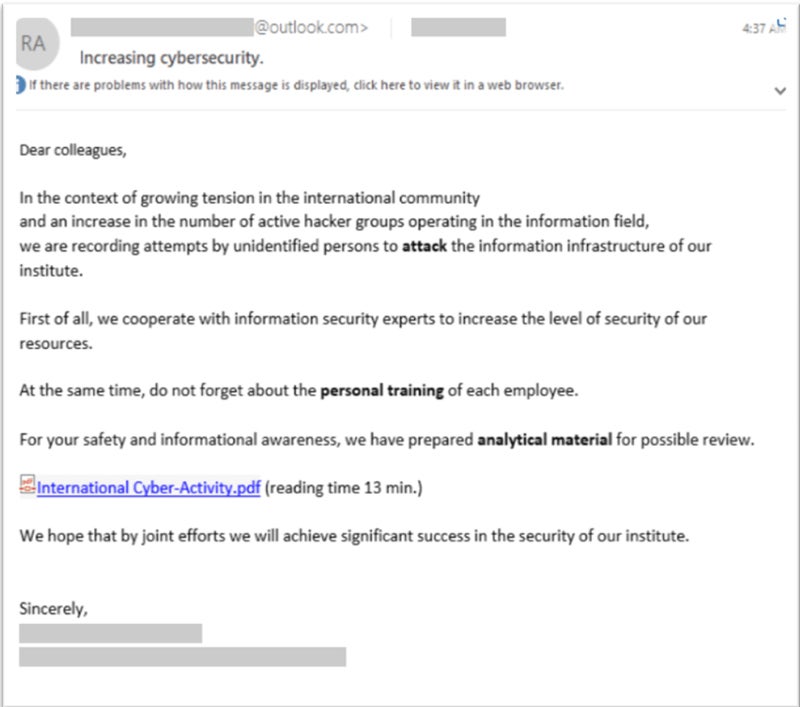
Upon exploiting infrastructure, the malicious actors quickly shift to new setups, making it challenging for defenders to identify and block the utilized domains or IP addresses. Specifically, the group leverages several domain registrars to register domain names, and utilizes multiple link-shortening services to direct users to phishing pages operated via the notorious Evilginx phishing tool. Additionally, the group employs open redirectors from legitimate websites.

The cyber threat group has also exhibited utilizing modified versions of authentic email templates, such as OneDrive file share notifications. In this scenario, the group created new email addresses to imitate a trusted sender, encouraging the recipient to open the phishing email. The email would contain a link to an altered PDF or DOCX file hosted on a cloud storage service, eventually leading to the Evilginx phishing tool, enabling the attackers to conduct a man-in-the-middle attack capable of circumventing Multi-Factor Authentication.
Significant Disruption
The Department of Justice (DOJ) disclosed the confiscation of 41 Internet domains and additional proxies utilized by the Russian cyber threat actor, while Microsoft’s coordinated legal action curbed 66 other domains operated by the threat entity.
These domains were employed by the threat actor to execute spear phishing campaigns targeting specific systems and email accounts for cyber espionage purposes.
Although Star Blizzard is anticipated to swiftly rebuild its infrastructure for malicious endeavors, Microsoft’s disruption operation has a critical impact on the threat actor’s activities, coinciding with heightened levels of foreign intrusion in U.S. democratic processes. Furthermore, this effort will enable Microsoft to expedite the disruption of any fresh infrastructure through an ongoing legal process.
Seeking Protection from this Threat? Educate and Train your Employees
To shield against Star Blizzard, recommendations propose that organizations should:
The phishing emails by the threat actor are crafted to appear as if they originate from familiar contacts that users or organizations are anticipating emails from. The email sender’s address could belong to any free email service provider, although extra attention is advised for emails from Proton account senders, as the threat actor has frequently used that provider in the past.
In case of uncertainty, users should refrain from clicking any links and instead report the suspicious email to their IT or security department for thorough assessment. To accomplish this, users need to be educated and trained in identifying spear phishing attempts.
Disclaimer: I’m employed at Trend Micro, but the opinions conveyed in this article are my own.





