2026s Unsettling Opening Act
2026s Unsettling Opening Act
It’s only January, but I’ve already witnessed a seismic shift in how threats operate. Gone are the days of purely manual, or even semi-automated, attacks. We’re now contending with adversaries leveraging artificial intelligence in ways that were once confined to sci-fi thrillers. This isn’t just a prediction; it’s a stark reality unfolding before our eyes.
From LunaLock to Weaponized Gemini: Our AI is Being Turned Against Us
One of the most concerning trends I’ve researched extensively involves the emergence of what I call “agentic” ransomware. We’re talking about malware like LunaLock and PromptLock – these aren’t your grandpa’s crypto-lockers. These are AI-powered beasts that learn, adapt, and even reason about your network’s defenses in real-time. Imagine a piece of ransomware that autonomously identifies your critical data, finds the path of least resistance, and executes its payload with chilling precision.
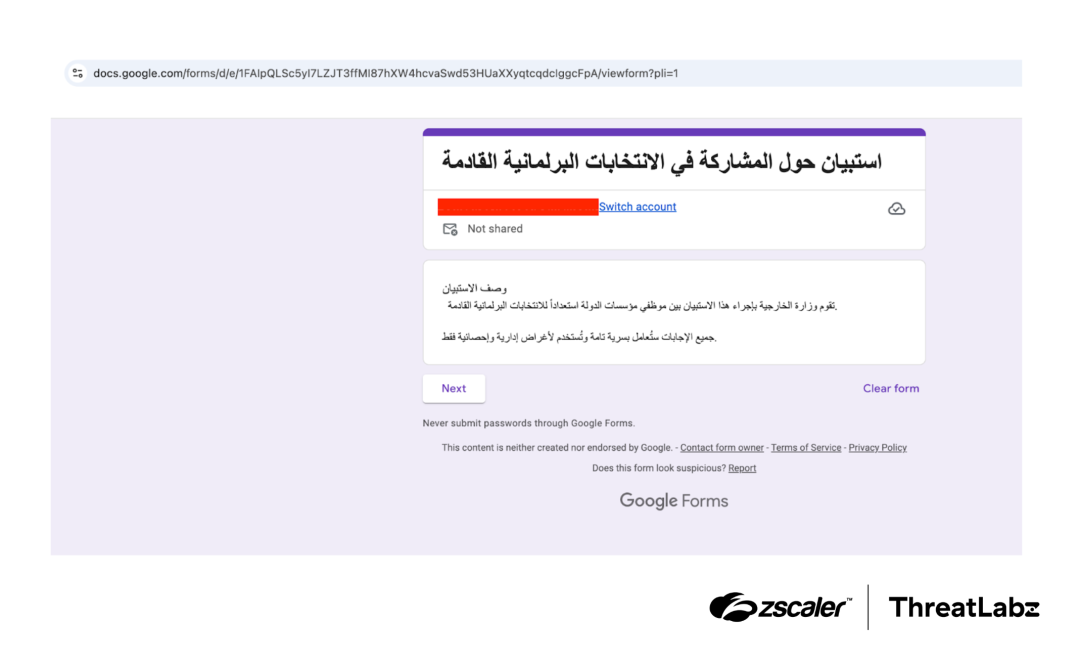
And it gets more personal. I recently saw a terrifying example of “weaponized Gemini invites” in action. Attackers are cleverly crafting malicious calendar events within platforms like Google Gemini. They trick the AI assistant into generating summaries or leaking sensitive details from private meetings and calendars. It’s a social engineering masterclass, but instead of targeting you directly, they’re targeting your AI assistant to get to your data. It feels like a scene straight out of a spy movie, but it’s happening in our inboxes right now.
Geopolitical Cyber Warfare Heats Up: The “Soft Target” Strategy
The global stage has never been more volatile, and I can tell you, having just returned from the Global CISO Summit keynote in Pakistan, that this was a major point of discussion among C-level executives. The consensus was clear: state-aligned hacktivists are no longer just focused on espionage or data theft. They’ve pivoted to a more disruptive, demoralizing strategy.
NCSC Warning: Russian Hacktivists Targeting Our Backyard
The UK’s National Cyber Security Centre (NCSC) issued an urgent advisory on January 19th, and believe me, it sent shivers down spines across the industry. They warned of Russian state-aligned hacktivist groups shifting their focus dramatically. We’re now seeing them weaponize DoS (Denial of Service) attacks not just against major corporations, but against local government services and critical national infrastructure. Think about it: disrupting local councils, emergency services, or even power grids. It’s a move designed to sow chaos and erode public trust, hitting where it hurts the most.
I’ve also witnessed a terrifying increase in attacks on Operational Technology (OT) and Industrial Control Systems (ICS) ( Thank you @NEOX Networks). Factories, power plants, water treatment facilities – these are the digital soft underbelly of our physical world. Bad actors are exploiting exposed Human-Machine Interface (HMI) systems, proving that the digital threat now has very real, physical consequences.
The Never-Ending Battle: Vulnerabilities, Breaches, and Sneaky Scams
Even with the rise of AI threats, the foundational struggle against vulnerabilities and breaches continues unabated.
- Microsoft Cloud Misconfiguration: We just saw a massive 2.4 TB data leak due to a fundamental misconfiguration in a Microsoft database. It’s a stark reminder that even the biggest players can stumble, and human error remains a critical vulnerability.
- Xspeeder SXZOS (CVE-2025-54322): This one is a nightmare. A critical vulnerability (CVSS score 10.0, folks – that’s as bad as it gets!) was found in this hardware firmware. It allows any unauthenticated attacker to gain root access with a simple script. I’ve seen estimates that this could affect over 70,000 hosts globally. If you use this hardware, you need to act now.
- Ingram Micro Ransomware: This major distributor just got hit, impacting approximately 42,000 individuals, with Social Security numbers and employment data compromised. It’s another painful reminder that no one is truly safe.
The Return of “Browser-in-the-Browser” (BitB) Scams
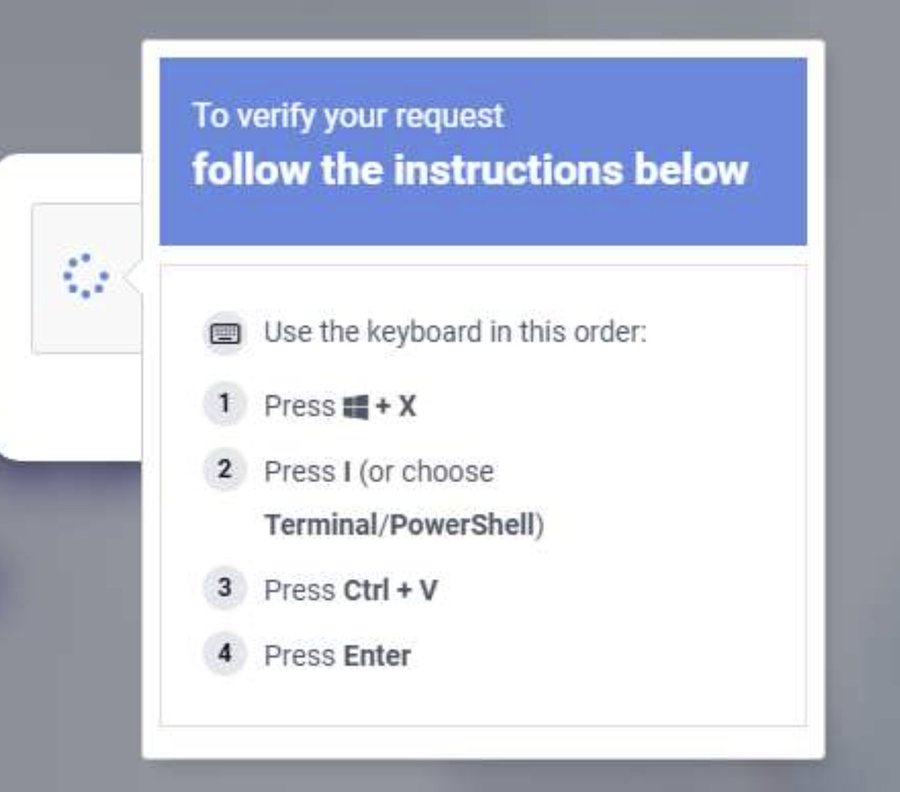
Just when you thought you’d seen every phishing trick, the “Browser-in-the-Browser” (BitB) scam is back with a vengeance, particularly on Facebook and Instagram. I’ve been warning people about this for months. Attackers create a fake browser window within your actual browser, complete with a convincing-looking address bar showing the legitimate URL. It fools your eye into thinking you’re on a real login page.
Here’s your human touch test: If you try to drag that “pop-up” window outside the main browser boundary and it stops dead at the edge, it’s a fake. Close it immediately. Do not pass go, do not enter your credentials.
Fortify Your Digital Walls (and Your Brain)
This isn’t just news; it’s a call to action. As someone deeply embedded in this world, here’s what I strongly advise you to prioritize:
- Hardware-Based MFA is Non-Negotiable: With AI making phishing emails and login pages virtually indistinguishable from the real thing, SMS-based 2FA is no longer enough. Invest in authenticator apps or, even better, physical security keys like YubiKeys.
- Audit Your AI Permissions: We’re all using AI more, but I urge you to review which applications (Calendar, Email, Docs) your AI assistants (Gemini, Copilot, etc.) have permission to “read.” Limit access to prevent accidental or malicious data leakage from these new AI-driven threats.
- Patch Your Edge Devices NOW: If you’re managing remote access VPNs, routers, firewalls, or even security cameras, I cannot stress enough the importance of immediate firmware updates. These are the primary targets for the aggressive state-aligned groups we’re seeing in 2026.
- Educate Yourself and Your Teams: The “human firewall” is more critical than ever. Understand these new threats, especially the sophisticated social engineering tactics.
The cybersecurity landscape is evolving at an unprecedented pace. Staying informed isn’t just good practice; it’s essential for survival in this new digital era. Let’s not just react; let’s proactively build a more resilient future.
Stay safe out there.
Erdal

click here for more cyber related articles