Experts
warn
that
55
zero-day
vulnerabilities
were
exploited
in
attacks
carried
out
by
ransomware
and
cyberespionage
groups
in
2022.
Cybersecurity
firm
Mandiant
reported
that
ransomware
and
cyberespionage
groups
exploited
55
zero-day
flaws
in
attacks
in
the
wild.
Most
of
the
zero-day
vulnerabilities
were
in
software
from
Microsoft,
Google,
and
Apple.
The
figures
show
a
decrease
from
2021,
but
experts
pointed
out
that
they
represent
almost
triple
the
number
from
2020.
The
majority
of
the
zero-day
vulnerabilities
were
exploited
by
China-linked
threat
actors
as
part
of
their
cyberespionage
campaigns.
The
researchers
reported
that
only
four
zero-day
vulnerabilities
were
exploited
by
financially
motivated
threat
actors,
with
75%
of
these
instances
linked
to
ransomware
attacks.
“Products
from
Microsoft,
Google,
and
Apple
made
up
the
majority
of
zero-day
vulnerabilities
in
2022,
consistent
with
previous
years.
The
most
exploited
product
types
were
operating
systems
(OS)
(19),
followed
by
browsers
(11),
security,
IT,
and
network
management
products
(10),
and
mobile
OS
(6). ”
reads
the
report
published
by
Mandiant.
According
to
the
report,
13
zero-days
in
2022
were
exploited
by
cyber
espionage
groups,
a
figure
that
is
consistent
with
2021.
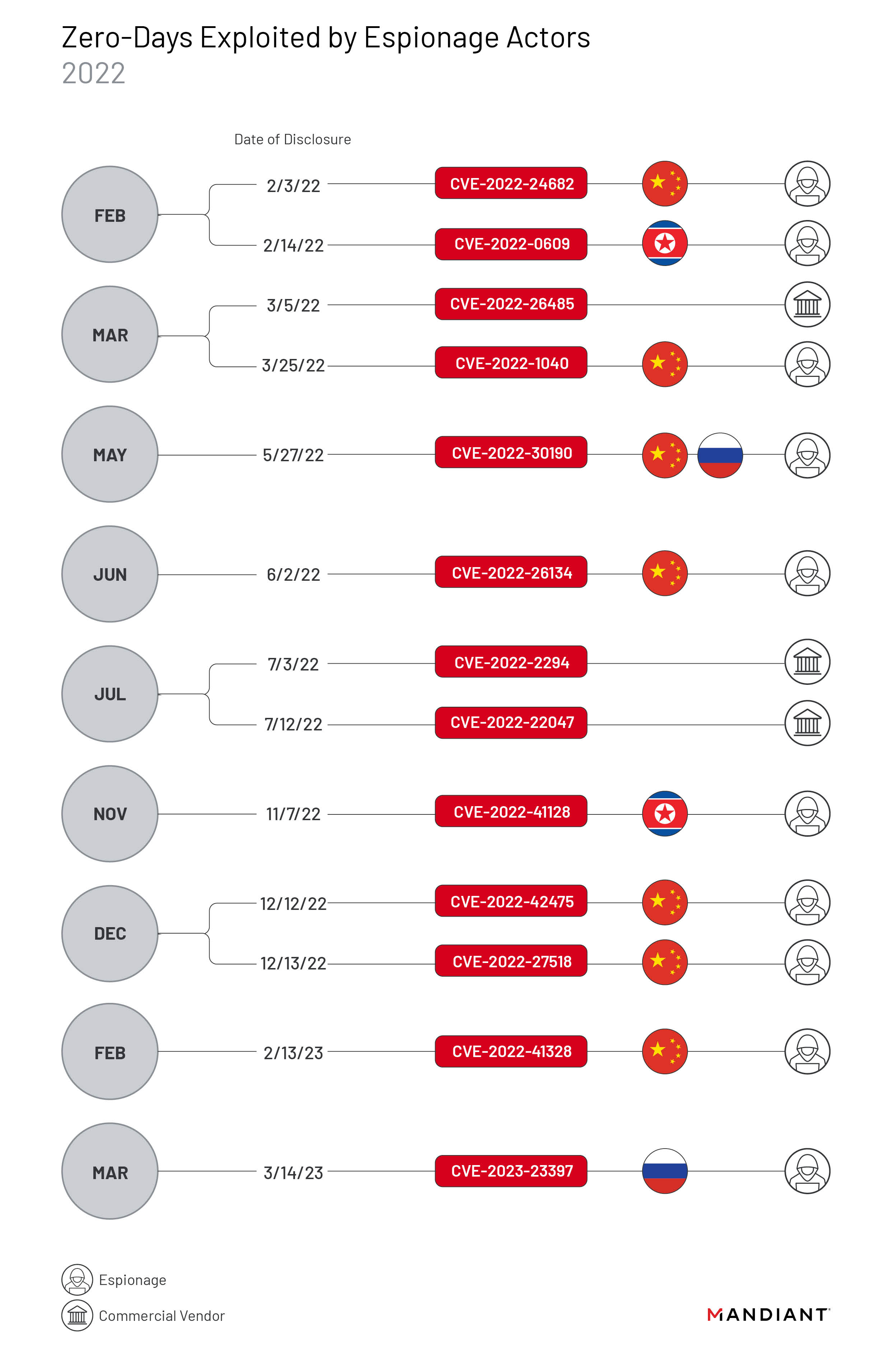
Seven
zero-days
(CVE-2022-24682, CVE-2022-1040, CVE-2022-30190, CVE-2022-26134, CVE-2022-42475, CVE-2022-27518,
and CVE-2022-41328)
were
exploited
in
attacks
in
the
wild
by
China-linked
cyberespionage
groups,
while
two
zero-day
vulnerabilities
were
exploited
by
suspected
North
Korea-linked
APT
groups.
“We
identified
four
zero-day
vulnerabilities
for
which
we
could
attribute
exploitation
by
financially
motivated
threat
actors,
a
quarter
of
the
total
16
zero-days
for
which
we
could
determine
a
motivation
for
exploitation.
75%
of
these
instances
appear
to
be
linked
to
ransomware
operations,
consistent
with
2021
and
2019
data
in
which
ransomware
groups
exploited
the
highest
volume
of
zero-day
vulnerabilities
compared
to
other
financially
motivated
actors.”
continues
the
report.
“However,
the
overall
count
and
proportion
of
the
total
of
financially
motivated
zero-day
exploitation
declined
in
2022
compared
to
recent
years.”
Multiple
China-linked
APT
groups
exploited
the
vulnerability
CVE-2022-30190,
aka
Follina,
while
the
exploitation
of
FortiOS
vulnerabilities
CVE-2022-42475
and
CVE-2022-41328
was
observed
in
particularly
notable
campaigns
in
2022.
Mandiant
believe
that
there
is
a
shared
development
and
logistics
infrastructure
behind
the
attacks.
Mandiant
also
observed
two
instances
of
Russian
state
zero-day
exploitation.
A
first
campaign
carried
out
by
the
Russia-linked
APT28
group
exploited
the
CVE-2022-30190
flaw
(aka
Follina)
in
early
June
2022.
A
second
activity
is
related
to
a
months-long
campaign
exploiting
Microsoft
Exchange
vulnerability
CVE-2023-23397
conducted
by
a
threat
actor
tracked
as
UNC4697
(likely
linked
to
the
APT28
group).
The
experts
explained
that
increased
focus
on
disrupting
Russian
cyber
operations
since
Russia’s
invasion
of
Ukraine
may
have
discouraged
Russia-linked
groups
from
widely
using
zero-day
exploits
for
access
they
expected
to
lose
quickly.
This
implies
that
the
exploitation
of
the
CVE-2022-30190
flaw
was
likely
opportunistic.
“Almost
all
2022
zero-day
vulnerabilities
(53)
were
exploited
for
the
purpose
of
achieving
either
(primarily
remote)
code
execution
or
gaining
elevated
privileges,
both
of
which
are
consistent
with
most
threat
actor
objectives.
While
information
disclosure
vulnerabilities
can
often
gain
attention
due
to
customer
and
user
data
being
at
risk
of
disclosure
and
misuse,
the
extent
of
attacker
actions
from
these
vulnerabilities
is
often
limited.”
concludes
the
report.
“Alternatively,
elevated
privileges
and
code
execution
can
lead
to
lateral
movement
across
networks,
causing
effects
beyond
the
initial
access
vector.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
zero-day)









