
A fresh study from cloud security firm ZScaler illuminates the escalating mobile risks on Android operating systems, alongside IoT and OT devices hazards. These discoveries arrive at a time when mobile devices contribute to more than 60% of global Internet traffic and monetary-focused mobile risks have spiked by 111% in the past year.
A compilation of mobile malware threats
The team at ZScaler’s ThreatLabz noted a 29% uptick in banking mobile malware from the previous year, with banking malware accounting for 20% of the overall Android threat spectrum.
Current leading banking malware variants include:
- Vultur, predominantly dispersed through the Google Play Store.
- Hydra, spread via phishing messages, websites, and unscrupulous Google Play Store applications.
- Ermac, engineered to pilfer financial data from banking and wallet apps.
- Anatsa, also recognized as TeaBot
- Coper, also referred to as Octo
- Nexus, focusing primarily on cryptocurrency accounts
Most of these banking malware strains log keystrokes, seize credentials, and intercept SMS messages to bypass Multi-Factor Authentication.
SEE: How to Develop a Robust Cybersecurity Awareness Program (TechRepublic Premium)
Surge of over 100% in Spyware threats
Alongside banking malware, spyware threats have also increased, with reports showing a 100% surge in blocked transactions compared to the previous year.
The prevailing spyware culprits are SpyLoan, SpinOk, and SpyNote.
- SpyLoan can extract personal data from devices like accounts, device details, call logs, installed applications, calendar events, metadata, and more.
- SpinOk spyware gathers sensitive data and files from various device locations before transferring the information to a server controlled by malicious actors.
- SpyNote, also known as CypherRat, furnishes supplementary remote access capabilities for executing software control on the mobile device.
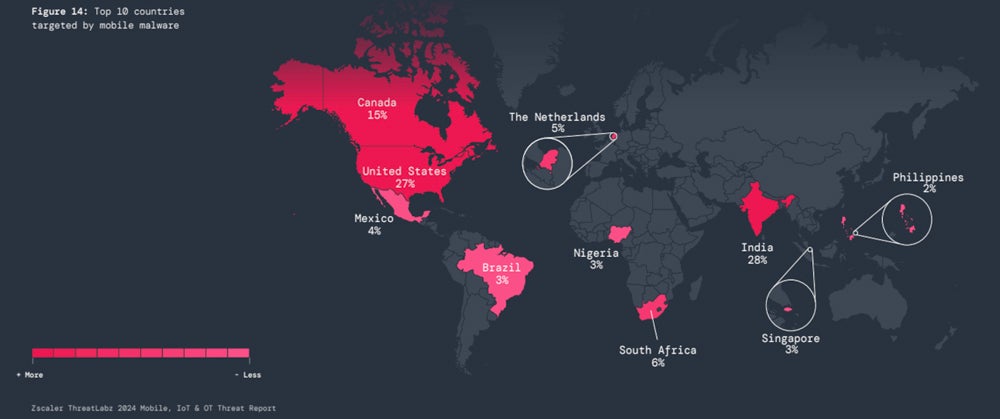
According to ZScaler, the most targeted countries by mobile malware are India (28%), the U.S. (27%), and Canada (15%), followed by South Africa (6%), The Netherlands (5%), Mexico (4%), Nigeria (3%), Brazil (3%), Singapore (3%), and the Philippines (2%).
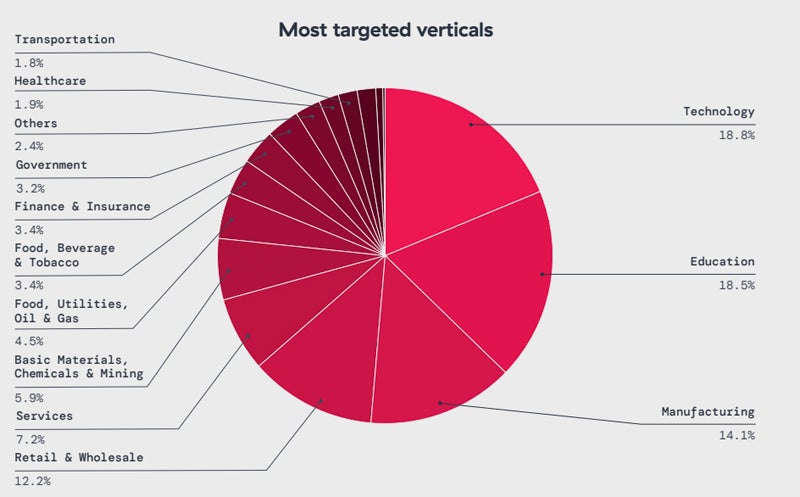
Industries impacted by this include technology (18%), education (18%), manufacturing (14%), retail and wholesale (12%), and services (7%).
Diversified methods are used to distribute mobile malware. One such method involves employing social manipulation tactics. For instance, ZScaler mentions that perpetrators spread the Copybara mobile malware by executing voice phishing (vishing) assaults, where the victim receives verbal instructions to install the malware on their Android devices.
QR code fraud remains prevalent, where individuals are deceived into scanning malicious QR codes that lead to malware infiltration or, in certain cases, to counterfeit pages.
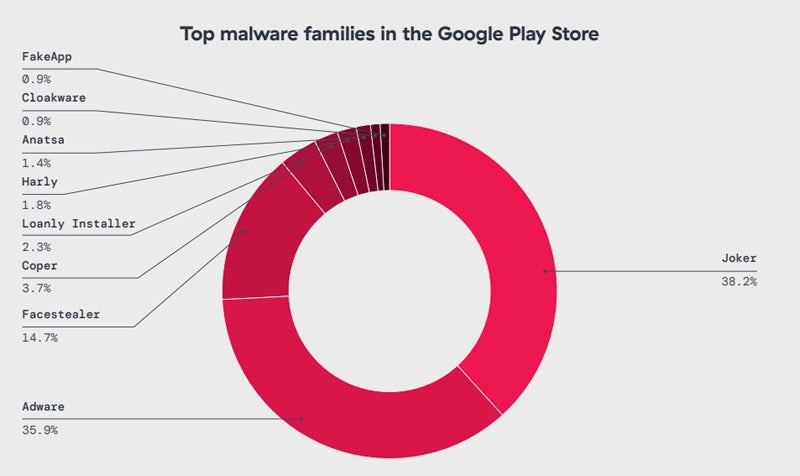
Some malware is also accessible on the Google Play Store. Notable examples include Joker— which stealthily enrolls users into premium services without their consent to incur charges— followed by adware malware types and facestealer, a tool for pilfering Facebook accounts.
Despite a general decrease in Android attacks, financially-motivated mobile threats have shown a 111% increase in the past year.
IoT and OT vulnerabilities
The report notes that Internet of Things and Operational Technology environments are continually expanding and are becoming more attractive targets for attackers. According to the findings, the number of IoT devices engaging with them has seen a 37% growth year over year.
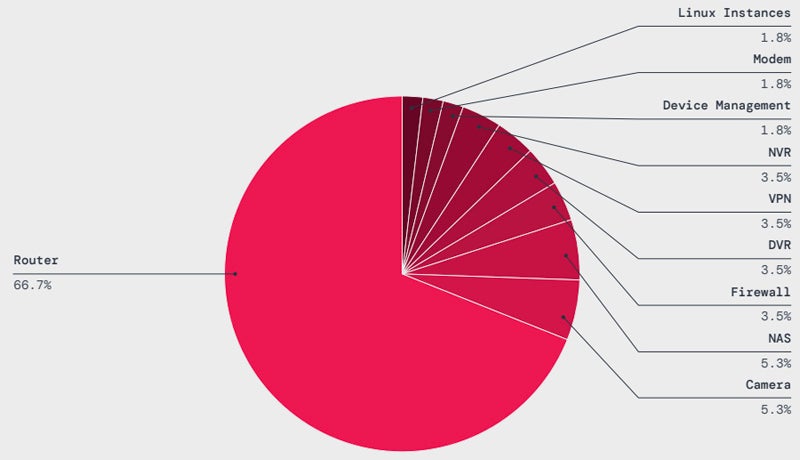
In the last year, IoT malware attacks have risen by 45%, with routers being the primary targets, attracting over 66% of these attacks. The key malware strains affecting IoT devices are Mirai (36.3%) and Gafgyt (21.2%). These malware-infected IoT devices can be incorporated into botnets to launch significant Distributed Denial of Service attacks.
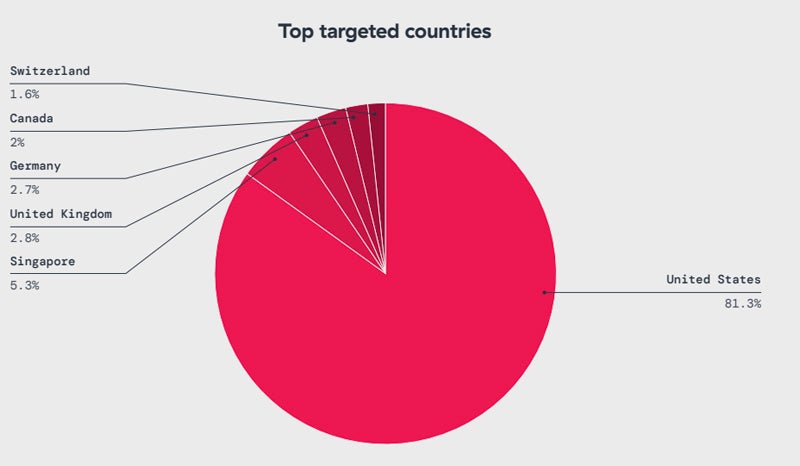
When it comes to the geographic breakdown, the U.S. is the target for more than 81% of IoT malware attacks, followed by Singapore (5.3%), the United Kingdom (2.8%), Germany (2.7%), Canada (2%), and Switzerland (1.6%).
The primary sectors influenced by IoT malware attacks include manufacturing (36.9%), transportation (14.2%), and food, beverage, and tobacco (11.1%).
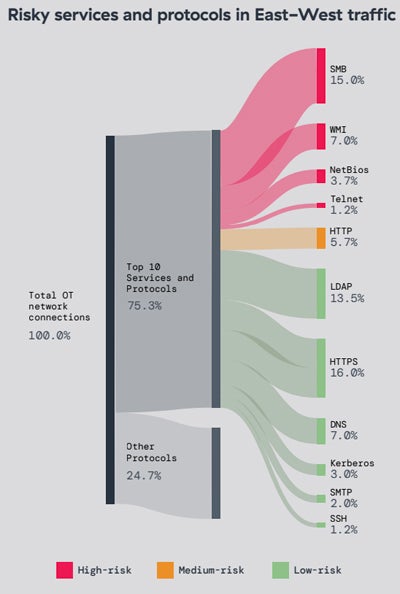
On the Operational Technology front, many deployments consist of devices running outdated, end-of-life operating systems. OT environments often expose protocols susceptible to various vulnerabilities, such as SMB or WMI.
For instance, ThreatLabz studied the OT infrastructure of a large manufacturing entity, with over 17,000 connected OT devices spread across 40 different locations. Each location had more than 500 OT devices using obsolete Microsoft Windows operating systems, many of which had well-documented vulnerabilities.
Unauthorized or blocked traffic accounted for 67% of the global OT device traffic.
Anticipated Future Developments
According to ZScaler, the primary threat vectors for IoT and OT devices will persist, with the manufacturing industry continuing to be heavily targeted for IoT attacks, such as ransomware.
ZScaler also predicts that artificial intelligence will be increasingly utilized to execute sophisticated phishing campaigns aimed at mobile users. Despite this, AI will enable defenders to automate key functions and enhance their prioritization efforts.
Securing IoT and OT Devices from Cyber Threats
To enhance protection against threats on IoT and OT devices, the following measures are essential:
- Prioritize gaining insight into IoT and OT devices. Entities should identify, categorize, and manage inventories of all IoT and OT devices utilized within their complete ecosystem.
- Maintain all systems and software current and patched to thwart exploitation via common vulnerabilities.
- Collect and scrutinize network logs. Anomalies in user account access and system activities necessitate focused monitoring.
- Implement multi-factor authentication where feasible, and alter or deactivate default passwords and accounts.
- Implement Zero-Trust device segmentation for IoT and OT assets to curtail data exposure.
Safeguarding Mobile Devices from Cyber Threats
To fortify defenses against threats on mobile devices, the following precautions are crucial:
- Deploy security apps on devices to guard against malware and potential phishing attacks.
- Approach any link received on the mobile phone, irrespective of the application, with caution. Suspicious links should not be clicked and should be reported to IT security personnel.
- Avoid unknown apps. Additionally, refrain from downloading apps from untrusted third-party sources.
Enterprises should exercise caution with apps requesting immediate updates post-installation. An app from the official store should always be the latest version. Any request for quick updates should raise suspicions and may indicate a malware attempt to download malicious components.
Disclosure: I am employed by Trend Micro, but the opinions expressed in this article are solely my own.


