24 April 2025
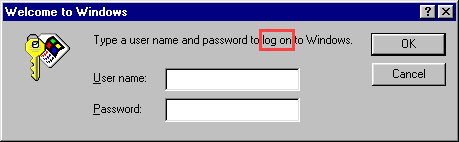
How do seemingly minor tasks manage to occupy so much time?! This week a proposal surfaced suggesting that instead of being capable of accessing the new HIBP website, you should, alternatively, be allowed to log in. Initially, this brought about some confusion since I’ve been accustomed to logging on to applications for decades:
Therefore, I proceeded and signed in (yes, once more) to X and consulted with numerous individuals to determine the correct phrase:
When you go to your @haveibeenpwned dashboard, what should your action be? Pre-view screen for reference: https://t.co/9gqfr8hZrY
— Troy Hunt (@troyhunt) April 23, 2025
As this did not provide a definitive winner, I commenced surveying various sources.
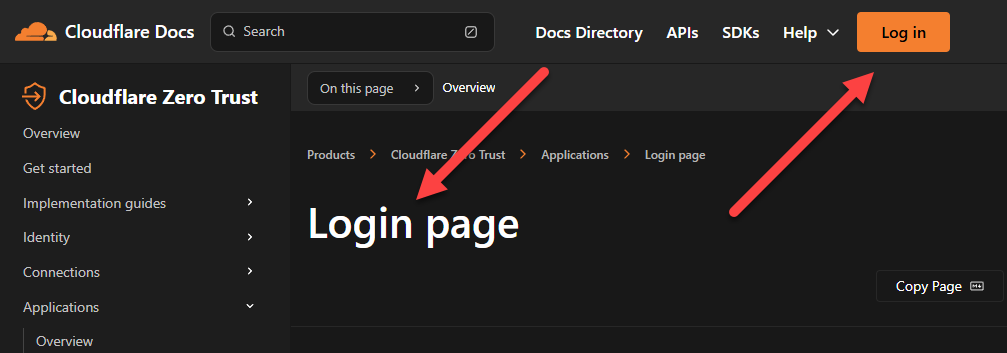
Cloudflare’s Zero Trust documents encompass details about customizing the access page, which presumably can be done after you authenticate:
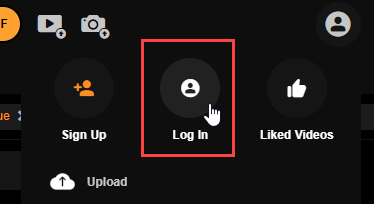
Another, um, “in-demand” platform prompts you to sign in:
Upon completing the initial procedure, you are encouraged to authenticate:
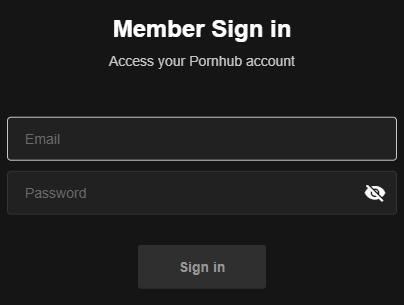
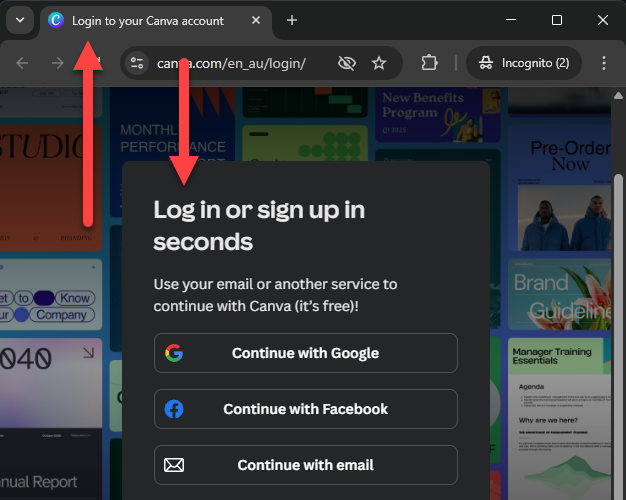
You have the option to sign on to Canva, clearly indicated by the HTML title, which implies that you are on the access page:
You may access the Commonwealth Bank website here in Australia:

However, to gain entry to the login page for ANZ bank, you must authenticate, unless you have misplaced your login credentials:
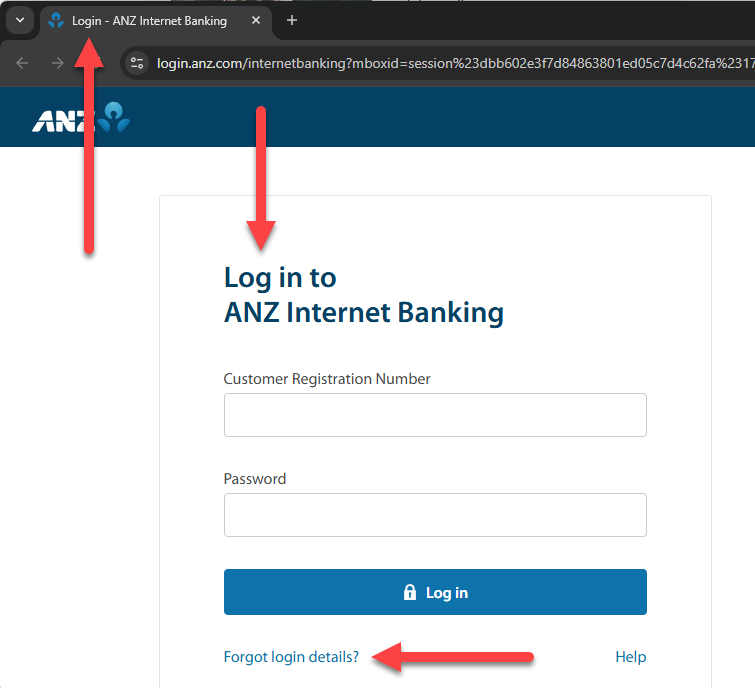
Ah, but many of these distinctions stem from the contrast between the noun “login” (the page is an object) and the verb “log in” (when you carry out an activity), correct? Well… it depends on your banking establishment 🤷♂️
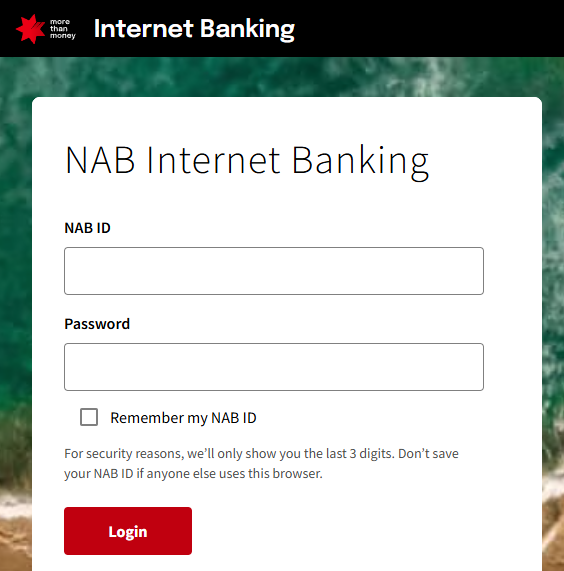
And there’s also the possibility that you neither access nor log on at all:
Finally, amidst the darkness of seemingly interchangeable terms that may or may not contradict English language standards, a trend emerged. You also authenticate with Google:
As well as Microsoft:

And Amazon:
And Yahoo:

And, as previously mentioned, X:
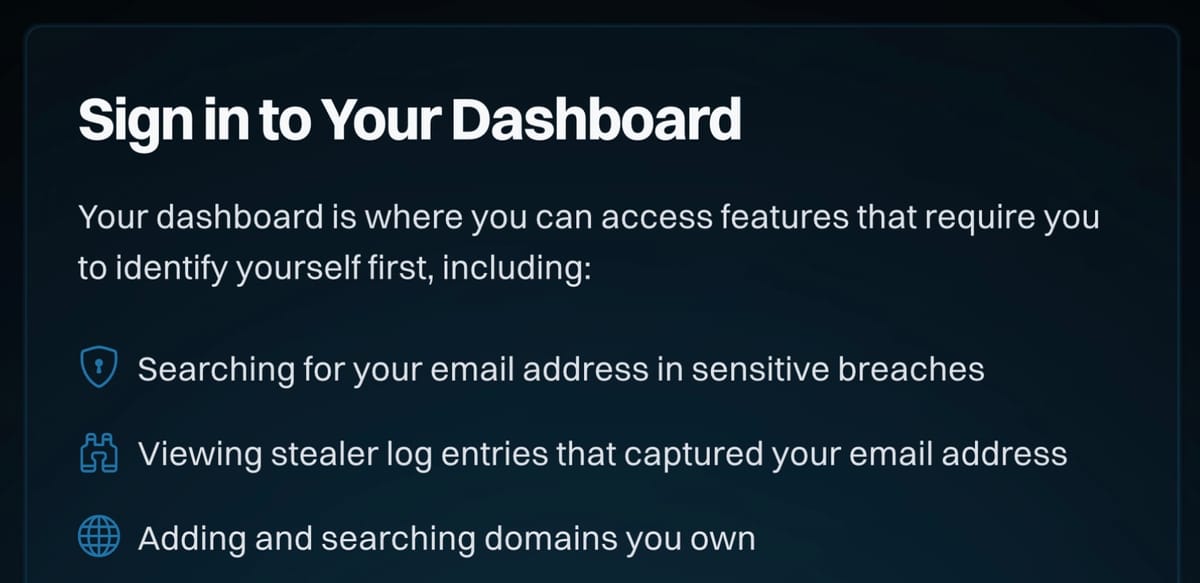
And now, Have I Been Pwned:
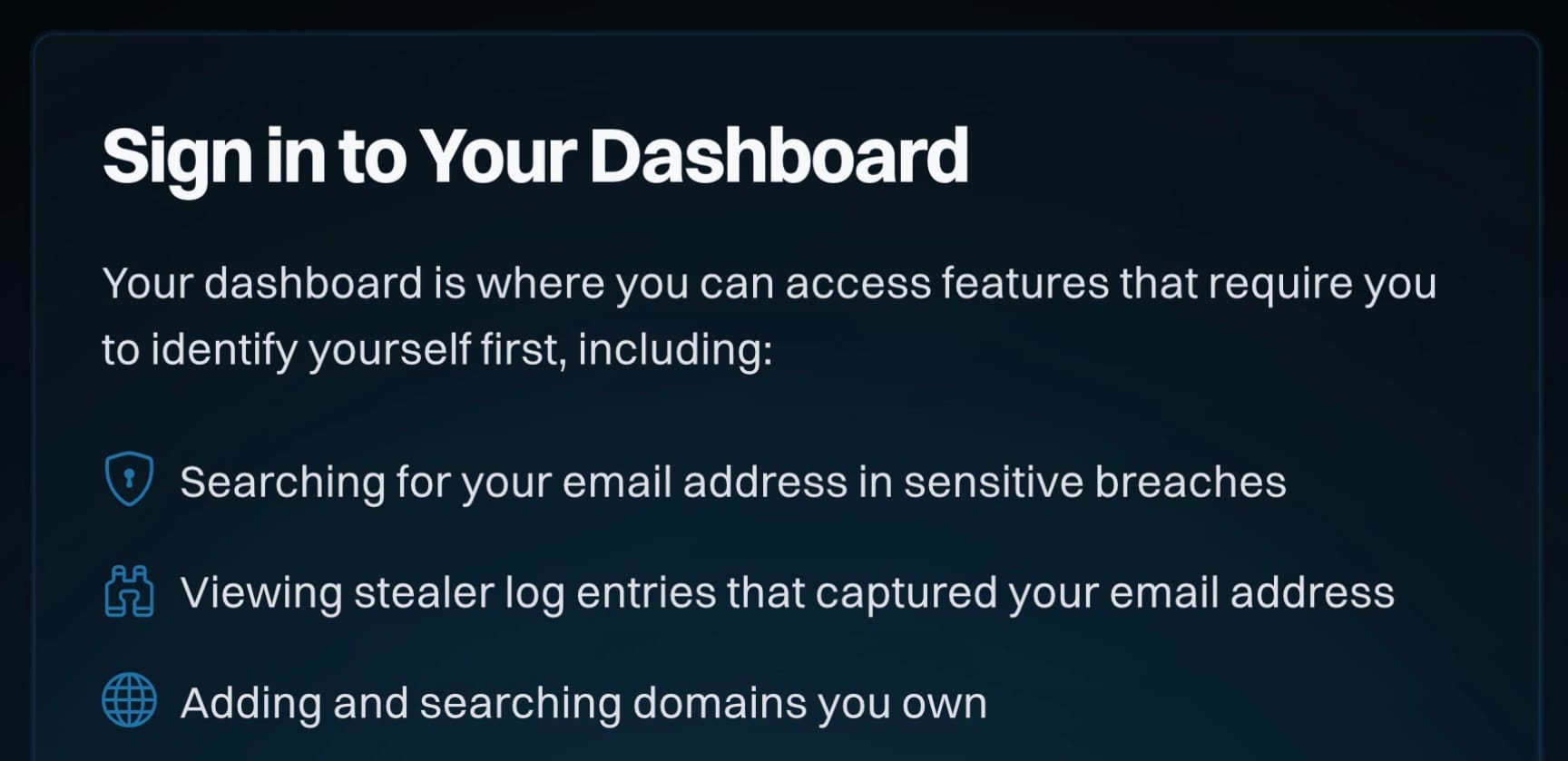
There are some standout exceptions (like Facebook and ChatGPT, for instance), but “sign in” did emerge as the top choice among the most visited sites worldwide. On deeper reflection, “log[whatever]” seems to suggest something different from how we currently authenticate to systems and may be a holdover from the past. Nonetheless, this argument is likely no more meaningful than the distinction between performing an action or interacting with an object.
UX







