Unveiling the Stark Reality Behind the Regeneration of Russia’s Fin7 – Krebs on Security
A cybercrime faction based in Russia and branded as “Fin7,” recognized for engaging in phishing and malware offensives leading to approximately $3 billion in damages for victimized establishments since 2013, was formerly declared defunct by U.S. authorities. However, specialists affirm that in 2024, Fin7 has resurfaced emphatically — constructing myriad websites imitating various media and technology corporations — with the aid of Stark Industries Solutions, an extensive hosting provider recognized for perpetually launching cyber assaults against adversaries of Russia.
In May 2023, the U.S. prosecutor for Washington state proclaimed that “Fin7 is defunct,” following the successful conviction and imprisonment of three individuals identified as senior Fin7 hackers or executives. This pronouncement was a bold stance against a group characterized by the U.S. Department of Justice as an illicit organization comprising over 70 individuals organized into discrete operational units and squads.
The initial indicators of Fin7’s resurgence emerged in April 2024, as Blackberry documented an incursion at a notable automotive corporation that commenced with malicious software disseminated through a typosquatting assault targeting individuals seeking a prevalent no-cost network scanning tool.
Currently, analysts at the security enterprise Silent Push express that they have devised a methodology to outline Fin7’s swiftly proliferating cybercrime infrastructure, encompassing over 4,000 hosts employing various exploitative techniques, ranging from typosquatting and deceptive ads to malevolent browser extensions and fraudulent domain impersonation.
Silent Push noted the unearthing of Fin7 domains mimicking or impersonating brands such as American Express, Affinity Energy, Airtable, Alliant, Android Developer, Asana, Bitwarden, Bloomberg, Cisco (Webex), CNN, Costco, Dropbox, Grammarly, Google, Goto.com, Harvard, Lexis Nexis, Meta, Microsoft 365, Midjourney, Netflix, Paycor, Quickbooks, Quicken, Reuters, Regions Bank Onepass, RuPay, SAP (Ariba), Trezor, Twitter/X, Wall Street Journal, Westlaw, and Zoom, among others.
Zach Edwards, the senior menace analyst at Silent Push, mentioned that numerous Fin7 domains are ordinary-looking websites for general enterprises, often incorporating content from default web templates (the material on these websites frequently has no correlation with the company’s stated business or purpose).
Edwards specified that Fin7 applies this strategy to “mature” the domains and foster a favorable or at least benign image for them before eventually repurposing them for the deployment of brand-specific phishing sites.
“Their revival process lasted six to nine months, but from January of this year onwards, they have been operational, fabricating an extensive phishing infrastructure and maturing domains,” explained Edwards regarding the cybercrime syndicate.
In typosquatting campaigns, Fin7 secures domains resembling those of widespread cost-free software utilities. These imitation domains are then publicized on Google to exhibit sponsored links prominently in search results, typically outpacing the authentic source of the respective software.
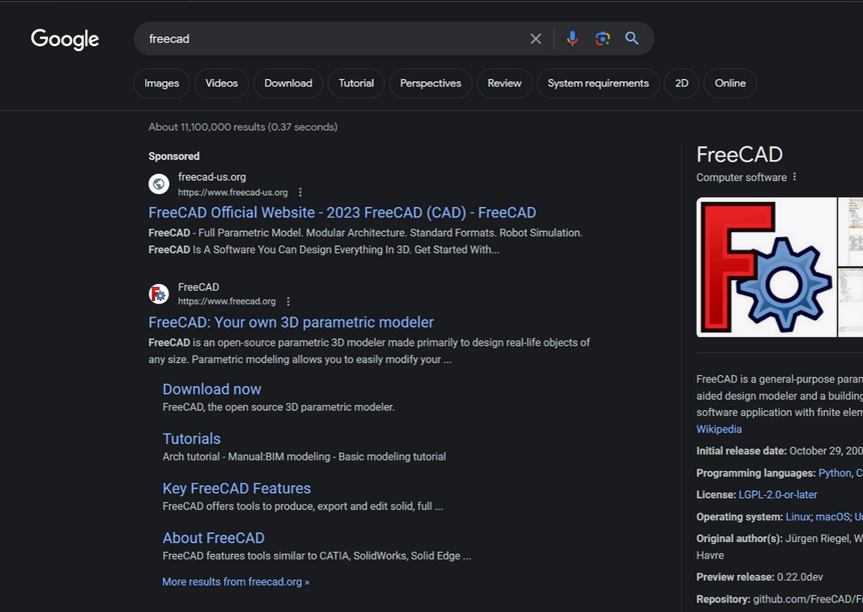
A deceitful website mimicking FreeCAD was prominently featured as a sponsored link in Google’s search outcome earlier this year.
As per Silent Push, the software currently targeted by Fin7 incorporates 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
In May 2024, the security firm eSentire cautioned about Fin7 resorting to sponsored Google advertisements to dispense pop-ups instructing individuals to download counterfeit browser extensions that embed malware. Malwarebytes commented on a similar operation in April but did not attribute it to a specific faction.
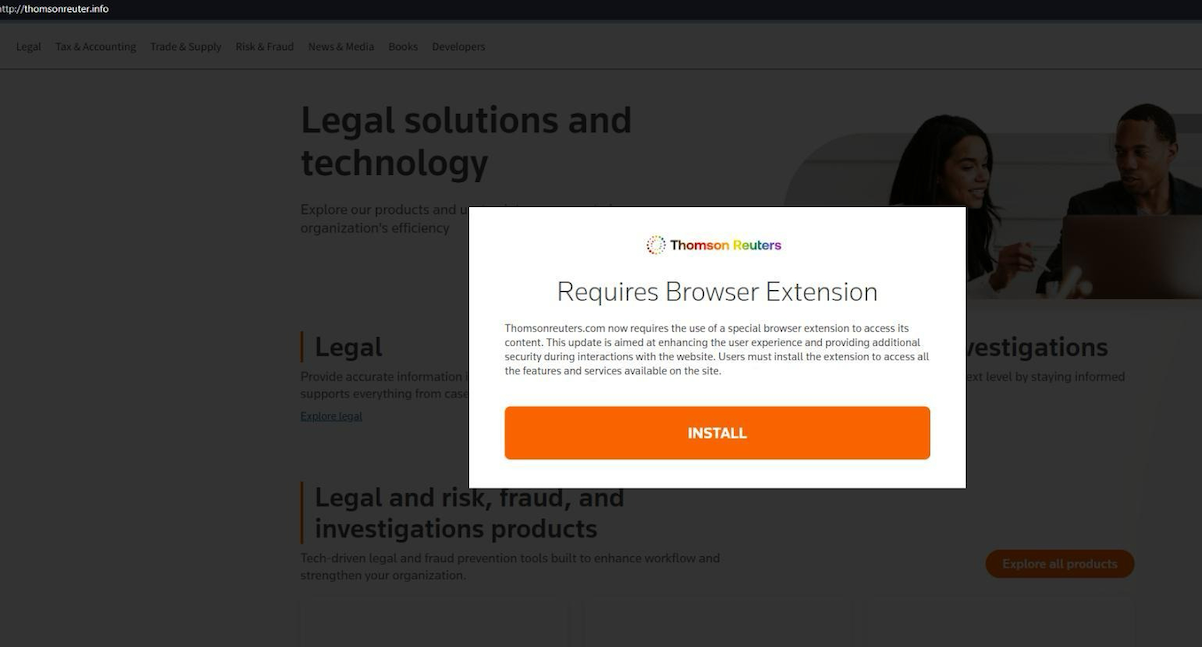
A pop-up on a Thomson Reuters typosquatting domain urging visitors to install a browser extension to access news content.
Edwards stated that Silent Push identified the new Fin7 domains following a report from an entity targeted by Fin7 in the past and harboring suspicions of the group’s reactivation. A quest for hosts resembling Fin7’s known characteristics revealed scarcely one operational site. Nevertheless, Edwards highlighted that this single site signifiedto many other Fin7 properties at Stark Industries Solutions, a large hosting provider that came into existence just a fortnight prior to the invasion of Ukraine by Russia.
KrebsOnSecurity detailed in May that Stark Industries Solutions is serving as a launching pad for continuous cyberattacks against Ukraine, which have been linked to Russian military and intelligence entities.
“A significant number of dedicated IPs are leased by FIN7 from Stark Industries,” stated Edwards. “Our analysts have identified numerous IPs solely dedicated to hosting FIN7 infrastructure within Stark Industries.”
Fin7 was previously known for operating under the guise of fake cybersecurity firms — such as entities bearing names like Combi Security and Bastion Secure — utilizing them to recruit cybersecurity professionals for supporting ransomware attacks. In a recent discovery by Silent Push, one of the new domains operated by Fin7 is cybercloudsec[.]com, which claims to provide “IT, cyber security, and cloud solutions to boost your business.”

The pseudo Fin7 cybersecurity firm Cybercloudsec.
Similar to other phishing collectives, Fin7 capitalizes on current occurrences, with its current focus being on individuals planning to attend the Summer Olympics in France this month. Some of the latest Fin7 domains spotted by Silent Push are deceptive websites targeting individuals seeking tickets for the Louvre.
“This study indicates the rapid resurgence and expansion of Fin7,” remarked Edwards. “We anticipate that the authorities will take notice and resume action against Fin7, and that our industry peers can leverage this data to extend their influence over a sizable portion of Fin7’s infrastructure.”
Additional resources:
Stark Industries Solutions: An Iron Hammer in the Cloud.
An in-depth report on Fin7 from the Swiss threat intelligence firm Prodaft in 2022 (PDF).