
For enterprises with various online accounts, improving company security is a primary concern to avoid information security breaches or cyber theft. The initial move towards preventing a data breach involves creating distinct passwords for each of your accounts.
However, if you belong to the group of individuals who tend to recycle their former passwords when creating new accounts, it is inevitable that your data and online accounts will become vulnerable sooner or later. Consequently, when your overused passwords get exposed, all the linked accounts are jeopardized.
An effective solution to this issue is utilizing password vaults – applications that aid in producing unique, strong, intricate passwords and storing them securely for easy retrieval. Password vaults safeguard account credentials, making them challenging to breach.
Discover below the mechanism behind the functionality of password vaults and how to pick the most suitable one to enhance your company’s online security.
What is the function of a password vault?
A password vault is a utility that aids in creating, storing, and managing online passwords or credentials. It utilizes encryption to safeguard the saved credentials and permits you to recover them using a master key. The primary concept behind this technology is to boost security by advocating for the utilization of unique, robust passwords for various online services. This practice helps mitigate the risks linked with password recycling and simplifies the task of handling multiple login details.
How does the functioning of password vaults operate?
While numerous web browsers include a basic password vault, only a high-grade third-party password management application can deliver comprehensive security and ease through functionalities like password creation, Virtual Private Network (VPN), monitoring of the dark web, data encryption, and dual-factor authentication.
Though you can simply integrate password vaults into your browsers as an add-on, the initial phase in utilizing several password vaults involves installing the application on your personal computer or smartphone.
To install a password vault on your desktop or mobile device, adhere to the following straightforward steps:
- Fetch the password vault application.
- Launch the application and generate a master key for your vault.
- Add the password vault extension to your browser.
- Log into your accounts.
- Revise your existing passwords.
Once your password vault is activated, instead of manually keying in the password on websites, the password vault, through the extension, prompts you to enter your master key to access your unique passwords. This master key acts as the mechanism to unlock the encrypted repository storing all stored passwords. If you have already authenticated into the password vault, it seamlessly populates the required login details on the website, sparing you the need to remember individual specifics.
If you desire an in-depth video elucidation on password vaults, we’ve got you covered. Take a look at our Password Vaults 101 video segment on the official TechRepublic YouTube channel currently accessible for viewing.
In this video, we delve into the functionalities and merits of password vaults, the safety aspect of utilizing password vaults, and the categories of individuals who should invest in password vault solutions initially.
Variants of password vaultssupervisors
Although various password supervision solutions serve akin functions, their primary attributes and modes of operation set them apart. Provided below are three prevalent classifications that could be beneficial for your company.
Locally embedded or disconnected password overseers
These are PC-based password control resolutions that stock your passwords directly on your gadget, like a notebook. These passwords are typically safeguarded within an encoded vault, boosting the security of your private details.
In contrast to cloud-based substitutes, locally installed password overseers do not depend on external servers to stock or manage your passwords. The benefit here is that your passwords are inaccessible from any other gadget unless they have been harmonized with the device. This local storage method provides you with a strong level of authority and confidentiality if you prefer to keep your information away from public networks.
Well-known illustrations of offline password overseers are KeePass and Enpass. Both password overseers enable users to stock their login details directly on their machine, without having them synchronized or stored on the cloud.
Nevertheless, there is a trade-off: Losing the gadget where the password overseer is set up would also entail losing access to all the saved passwords.
Some password overseers, like 1Password, Keeper, and Dashlane aim to strike a balance between privacy and convenience by providing features that allow you to establish multiple password vaults across your gadgets. These vaults can be synchronized when you connect to the internet. This permits a certain level of flexibility while still retaining a predominantly offline storage strategy. Consequently, you can enjoy the convenience of syncing your passwords across gadgets without wholly depending on external servers for data storage.
Internet-based or web password overseer services
These password overseers function on a cloud-based system, where encrypted passwords are stocked on the service provider’s network. In this context, the service provider assumes direct responsibility for safeguarding your passwords.
Applications such as 1Password and NordPass exemplify cloud-based password overseers. The prime advantage of these services lies in their accessibility — you can access your password vaults from any gadget with an internet connection.
Online password overseers usually manifest in various forms, frequently as browser extensions, desktop apps, or mobile applications.
Stateless or token-based password overseers
Stateless or token-based password overseers deviate from standard password overseers in that they do not directly stock passwords. Instead, they construct a unique password for each website or service grounded on a master password and a site-specific identifier referred to as a token. This token can be a tangible device, such as a USB key, or a code generated by a mobile app. When you log into a website, the password overseer generates a fresh password based on the prevailing master password and the site’s token.
Instances of token-based password overseers are YubiKey, OnlyKey, and Google Titan Security Key. This token-based approach is widespread in cryptocurrency security and is reminiscent of precise online banking login methods that mandate physical devices.
The lack of a fixed password on the gadget amplifies security, making it arduous for hackers to procure login credentials even if they compromise your account. However, dependence on a physical device exposes you to the danger of losing access in the event the device is misplaced or impaired.
Reasons why your organization requires a password overseer
It is vital for your company to adopt a password supervisor to guarantee centralized control and visibility over your employees’ password behaviors. The tracking and management of passwords can become difficult without it. By introducing a password supervisor, you can facilitate smooth onboarding and offboarding procedures, thereby enhancing overall security and efficiency within your enterprise.
Password supervisors provide the subsequent benefits for businesses:
Additional security with password creators
Password supervisors offer increased security for businesses by integrating password creators. This feature allows you to produce sturdy, distinct passwords for each user within your organization, hence reducing the risk of unauthorized access to crucial data.
Enhances log-in experience
They can streamline the login process for your enterprise, particularly in a remote or hybrid work setup. For instance, 1Password, LastPass, and several other password management solutions have the capability to safely store and auto-fill your credentials across various platforms. This functionality enhances user convenience while adhering to security standards.
Compatible with multiple devices
Presently, most password supervisors are cloud-based, offering the convenience of accessing stored credentials across multiple devices such as smartphones, PCs, or desktops. Your staff will have the flexibility and convenience of logging in to work from their different devices without being tied to a single localized device.
Safe password sharing
Another crucial aspect of a password supervisor is the ability to facilitate secure password sharing within your organization, permitting your team to collaborate without compromising security. You can control who can access sensitive information while promoting efficient teamwork.
Multi-factor confirmation
Many password supervisors incorporate multi-factor confirmation into their security checks, adding an extra layer of protection for your company information. This characteristic significantly minimizes the risk of unauthorized access and safeguards confidential data from potential intruders.
Selecting the optimal password supervisor for your enterprise
Selecting a capable password supervisor for your firm is the first step toward securing your systems and sensitive data. Here are the elements to assess when selecting the best password supervisor for your enterprise:
Pricing
Most password supervisors provide tiered pricing, generally from $1 to $20 per user per month, with feature and storage discrepancies. However, numerous options are still accessible in the market with perpetually free and feature expansion modes.
For instance, Bitwarden and LastPass offer free entry-level plans. Evaluate packages based on your company’s size and specific requirements to ensure scalability without superfluous features. Utilize trials to comprehend the program’s functionality before committing financially.
Distinct features
Advanced functions like secure password sharing, 2FA support, and integration with other tools are becoming common. Noteworthy choices like1Password and Dashlane frequently provide well-organized packages that include two-factor authentication.
Therefore, focus on functionalities that align with your organization’s workflow and security prerequisites. For instance, if your staff works remotely, you need to ensure secure password sharing is part of your choice.
Support Services
Around-the-clock customer service through email, chat, or phone is a common service provided by most password management systems. Assess the timeliness and knowledge of the support team since prompt assistance can be crucial in case of any problems or security issues.
User-Friendly Interface
User-friendly interfaces for both administrators and end-users are aspects you should not overlook. Test the user experience to guarantee ease of functionality.

It should boast a user-friendly design presenting an intuitive interface for swift password generation, storage, and management as this can influence adoption rates and overall security alignment within the organization.
Examination and Reporting Characteristics
Robust auditing tools for monitoring user actions and creating reports on password health should be encompassed in any effective password management solution. Having a thorough log of who accessed the system, which resources were utilized and when, in addition to details on every action executed by users within the system, is vital.
Mobile Support
Password managers must provide dedicated mobile applications with secure synchronization across devices. Evaluate the mobile usage to ensure usability without compromising security, particularly for staff who frequently work remotely.
Backup and Restoration Alternatives
Regular backups and a trustworthy recovery process for encrypted data are indispensable features that any reliable password management application should possess. Assess the backup frequency, methods, and recovery options of any solution you opt for. This is essential to decrease the risk of data loss and to guarantee business continuity.
Adherence and Certifications
Password managers should conform with data security regulations and might hold certifications such as SOC 2 or ISO 27001. Embracing ISO 27001 offers a holistic approach to information security. Therefore, verify that the chosen password management system complies with applicable industry standards to safeguard sensitive corporate data.
Highly Recommended Password Managers
While numerous password managers exist, not all of them provide equivalent levels of security and convenience. Below are the top three commercial password managers to consider:
1Password: Optimal for Extensive Security Attributes

1Password delivers numerous features for both personal and business users. Some notable features include single sign-on, two-factor authentication, end-to-end encryption, breach alerts, dark web monitoring, and more. If you are a business proprietor seeking to manage multiple accounts, collaborate with teams, and securely share sensitive data, then this password manager is the ideal selection. It is compatible with Chrome, Safari, Edge, Firefox, Brave, macOS, Windows, Linux, iOS, and Android browsers and platforms. It provides a 14-day trial period, and pricing starts at $2.99 for individuals and $7.99 for businesses.
Read our comprehensive 1Password review here.
Bitwarden: Ideal for Budget-Friendly Enterprises

Bitwarden offers an excellent solution for small businesses in need of a secure and cost-effective password manager. Its open-source structure and transparent security approach ensure an economical solution without compromising essential features. It offers both a free and a paid plan starting at $1 per user per month for individuals and $6 per user per month for enterprises.
Read our thorough Bitwarden review here.
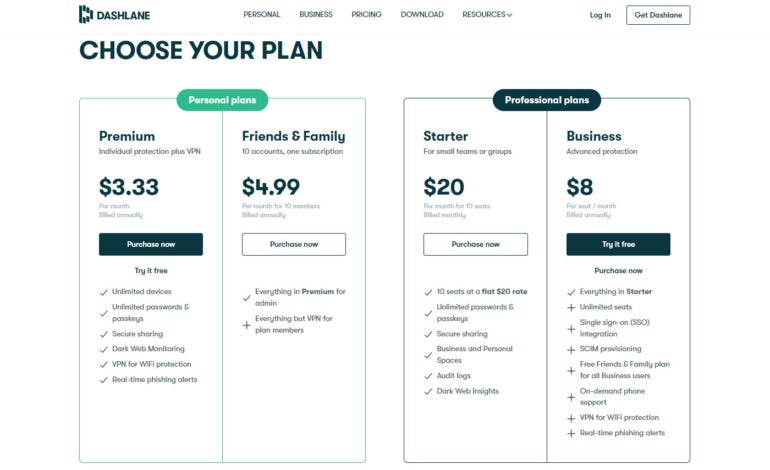
Dashlane: Top Choice for Quality Features and Security Compliance

Dashlane stands out among its competitors with its broad range of features. It excels in core password management functions, offering high-level security and smooth auto-saving and auto-filling capabilities across different operating systems, browsers, and devices. It sets itself apart with outstanding additions like a premium VPN service and live dark web monitoring. Its pricing begins at $4.99 per user per month for individuals and $8 per user per month for businesses.
Read our complete Dashlane review here.





