A passkey serves as a distinct form of validation, akin to a password but with an added layer of security. Unlike passwords, passkeys employ both private and public cryptographic keys to verify users, whereas a password relies solely on a set number of characters.
Google highlights that passkeys offer immediate advantages such as being resistant to phishing attempts and alleviating the burden of memorizing complex numbers and special characters associated with passwords.
As the paradigm shifts towards passwordless authentication to combat phishing threats, incorporating passkeys can fortify the security measures safeguarding your online accounts and data.
This piece will delineate the technology behind passkeys, expound on their functioning, and underscore the enhanced security benefits of utilizing passkeys.
The Essence of a Passkey:
A passkey is a sequence of characters or code utilized to access secure systems, devices, networks, or services. Often paired with usernames or user IDs, passkeys play a crucial role in facilitating two-factor authentication.
EXAMINE: Constructing an Impactful Cybersecurity Awareness Program (TechRepublic Premium)
Once a passkey is established, users can efficiently complete the authentication process by simply logging in, typically utilizing biometric data such as fingerprints or facial recognition. This streamlined login process benefits legitimate users while posing significant challenges to malicious entities.
The versatility of passkeys is notable, as they can be tailored to sync with the cloud or bind to specific hardware, depending on the user’s preferences and the requirements of the application, service, or device in question.
The Mechanics Behind Passkeys:
During the initial login, users aiming to access an application or website using passkey technology — exemplified by solutions like NordPass — will be prompted to create an original passkey. This unique passkey becomes pivotal for future authentications, accessible through biometrics or personalized PINs, tailored to the user’s choice and device capabilities.
Figure A
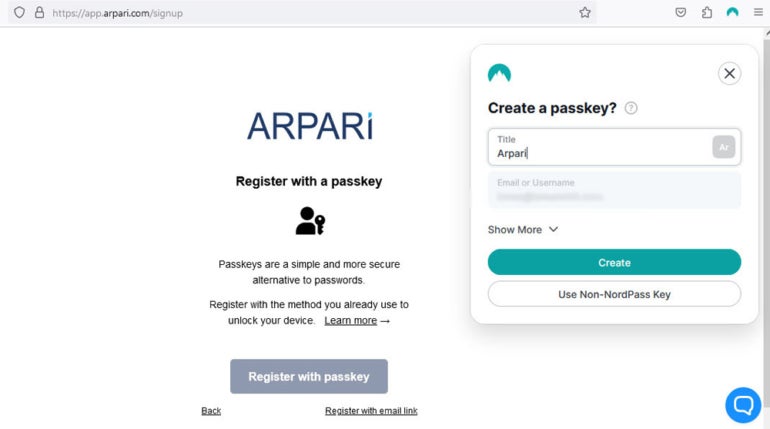
In this phase, two mathematically related cryptographic keys are created: a public key that remains with the website, service, or application but is associated with the account, and a private key that stays on the user’s hardware or cloud account.
How can you log in using a passkey instead of a password?
The process of passkey authentication occurs in the background, enabling seamless login on the user’s side — with a simple button click.
Figure B
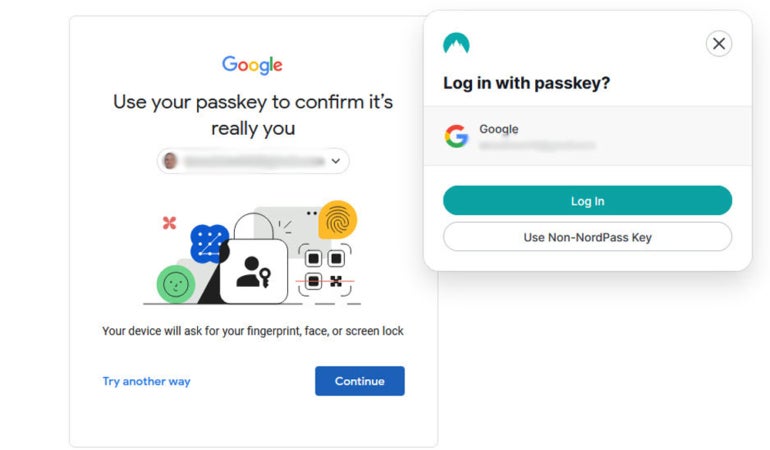
When logging in, the service or application will transmit a randomly generated “challenge” to the user’s device, which the user must respond to by authenticating with the private key.
SEE: Passkey Adoption Is Picking Up in APAC — With the Exception of Australia (TechRepublic)
To verify the private key’s legitimacy, the app or website will use the corresponding public key to validate the response. Access is granted, and authentication is confirmed if the user’s verified signature attached to the response matches the original randomly generated challenge; if not, access is denied.
How do passkeys vary from passwords?
The key distinctions between passkeys and passwords are:
- Passwords can be unlawfully acquired through brute-force hacking, social manipulation, and data leaks, whereas passkeys are more challenging (albeit not impossible) to pilfer. Hackers would need to physically seize your device or breach your cloud account and guess your PIN or find a way to bypass your biometric authenticator.
- Effective password management requires users to generate and remember numerous intricate credentials or utilize a password manager, which comes with its own difficulties and hazards. Passkeys automatically validate users with their device’s unlocking mechanisms, making them notably simpler and more convenient to use.
- Passwords can be applied across any device without additional setup, while passkeys are usually tied to specific hardware. Although a cloud-based passkey solution may function on multiple devices, users should be mindful that their private keys will be stored on external servers rather than locally.
What advantages does using a passkey provide?
- Distinct logins: A password is recurrently used every time you log in to an account, enabling any malicious individual who obtains it to have unrestricted access. On the other hand, passkeys leverage cryptographic key pair technology to generate unique authentication credentials for every login, leaving hackers with nothing to predict or steal. Passkeys are resilient against brute-force attacks and social engineering tactics like phishing, and they cannot be disclosed in a data breach.
- Added security safeguard: Passkeys utilize your device’s authenticator, such as a biometric login or PIN code, as an inherent 2FA layer that secures your account. Whether your private key is stored locally on your device or in the cloud, a potential attacker would need to authenticate with your device before gaining access to it and jeopardizing your account.
- User-friendly approach: Passkeys do not require memorization or periodic changes, and logging in with them necessitates only a single button press, delivering a much more straightforward experience than passwords. Additionally, as mentioned earlier, they incorporate 2FA for enhanced account protection, but users are not prompted for secondary authentication for each individual login — once you’ve logged into your device, that authentication extends to every account you access during that session.
Which devices support passkeys?
Various devices from leading tech manufacturers are compatible with passkeys. Passkey technology was designed following W3C and FIDO Alliance standards to enhance compatibility, with major device manufacturers (Apple, Google, and Microsoft),
Moreover, all major internet browsers already provide support for it.
The progress of passkey technology is ongoing, with some companies suggesting the potential for sharing credentials among users, as long as the actual passkeys are securely stored in the cloud and away from potential hackers. Since sharing account access with family, friends, and colleagues is a straightforward and swift process, this feature could enhance the overall user experience. Nevertheless, how this function can be securely managed in a business environment remains unclear.
VIEW: How to Use Google’s Titan Security Keys With Passkey Support (TechRepublic)
Another critical aspect to contemplate is whether companies should heighten their reliance on cloud service providers and relinquish more ownership and control over credential management, recognizing that a data breach from those parties would undoubtedly have disastrous repercussions.
Unlike cloud-based passkeys, hardware-bound passkeys are stored on security keys, physical hardware authenticators, or specialized hardware integrated into laptops and desktops. Consequently, the passkey cannot be transferred or duplicated. For organizations seeking to prevent employees from copying or sharing keys across devices, hardware-bound passkeys can serve as an alternative.
Are passkeys more reliable than passwords?
In general, passkeys are more dependable than passwords. However, their reliability hinges on various factors, such as the robustness of the cryptographic methods used to encrypt public and private keys, the security of the device’s authenticator, and the reliability of the passkey provider.
VIEW: Nearly 10 Billion Passwords Leaked in Biggest Compilation of All Time (TechRepublic)
Users can enhance the security of passkeys by using their device credentials as a secondary authentication method, opting for biometric login over a PIN. Additionally, minimizing cookie collection and regularly clearing cached credentials are recommended practices to enhance overall web security. Complementing passkeys with other security measures and controls, like encrypted hard drives, device malware protection, and firewalls, is essential.
Is it possible to hack a passkey?
Indeed, passkeys can be compromised, but it is considerably more challenging than obtaining a password. As previously mentioned, passkeys are safeguarded by multiple layers of security, including local device authentication and robust encryption. Merely acquiring the private key is insufficient because, even with cloud-based passkey solutions, local device authentication is necessary before accessing any online accounts.
Will passkeys supplant passwords and password managers?
In my perspective, passkeys will eventually supersede passwords and password managers, although the transition is currently in its early stages. As passkey technology advances and more businesses integrate it, passwords are likely to dwindle even among individual users.
What does the future hold for passkeys in technology?
Currently, most developments in passkey technology are rightly emphasizing features that are more developer and business-friendly to drive adoption.
For instance, presently, passkeys created in one ecosystem do not readily function in others. Thus, if a user creates a passkey on their iPhone, using the same passkey on a Windows laptop or transferring all passkeys from one environment to another is challenging, if not impossible.
Nevertheless, this restriction primarily applies to the environment-specific passkey tools available on newer Apple, Windows, and Android devices. With more third-party passkey providers entering the market, the standard is gradually moving toward cross-platform support and enhanced portability to enhance the user experience.




