Trump 2.0 Initiates Reductions in Cybersecurity and Consumer Safeguards

Following the commencement of his second term, President Trump’s endeavors to downsize the government by implementing widespread dismissals, terminations, and withholding funds allocated by Congress, have disrupted federal cybersecurity and consumer protection programs. Simultaneously, agencies are engaged in a continuous battle against the persistent attempts by the wealthiest individual globally to seize control over their networks and data.

Image: Shutterstock. Greg Meland.
The Trump administration has terminated over 130 personnel at the primary federal cybersecurity entity – the Cybersecurity and Infrastructure Security Agency (CISA). These layoffs reportedly included CISA employees responsible for safeguarding U.S. elections and counteracting disinformation and foreign interference campaigns.
In recent days, technologists affiliated with Elon Musk’s Department of Government Efficiency (DOGE) arrived at CISA and gained entry to the agency’s email and networked documents. Among these DOGE members is Edward “Big Balls” Coristine, a 19-year-old ex-resident of the “Com,” a virtual community of Discord and Telegram chat channels operating as a decentralized cybercriminal social network.
An investigative journalist Jacob Silverman disclosed that Coristine is the grandson of Valery Martynov, a double agent for the KGB who provided intelligence to the United States. Silverman recounted how Martynov’s widow Natalya Martynova relocated to the United States with her offspring after her spouse’s passing.
“Her son pursued a career in law enforcement in Virginia and occasionally engages in discussions on blogs about his renowned father,” Silverman stated. “Her daughter ventured into the financial sector and wed Charles Coristine, the owner of LesserEvil, a snack firm. In their descendants lies a 19-year-old individual named Edward Coristine, who presently exerts an undisclosed level of influence and authority over the inner workings of our federal administration.”
Another individual from DOGE is Christopher Stanley, previously serving as the senior security engineering director at X and the principal security engineer at Musk’s SpaceX. Stanley, aged 33, gained notoriety on Twitter in 2015 when he exposed the user database of the DDoS-for-hire service LizardStresser, subsequently facing threats of physical harm directed at his family.
My 2015 article about that breach did not disclose Stanley’s identity, but he revealed himself as the source by uploading a video on his YouTube channel. A review of domain registrations linked to Stanley indicated that he operated under the alias “enKrypt” and previously controlled a pirated software and hacking forum called error33[.]net, along with theC0re, a community for video game cheating.
“AN UNFOLDING NATIONAL CYBER INTRUSION”
DOGE has progressively secured sensitive network access to federal bodies housing vast amounts of personal and financial data on Americans, including the Social Security Administration (SSA), the Department of Homeland Security, the Office of Personnel Management (OPM), and the Treasury Department.
Most recently, DOGE has requested extensive access to systems at the Internal Revenue Service housing tax data on millions of Americans, detailing individuals’ earnings, debts, property records, and even specifics related to child custody arrangements. The New York Times reported on Friday an agreement where a singular DOGE employee – 25-year-old Gavin Kliger – is permitted access solely to anonymized taxpayer data.
The swift exploration by DOGE through various federal databases in pursuit of uncovering “massive fraud” within government agencies has sparked concerns among numerous security experts, highlighting that DOGE’s activities evade critical safeguards and security protocols.
“What’s most disconcerting isn’t just the sanctioned access,” noted Bruce Schneier and Davi Ottenheimer, denoting DOGE as a national cyber disruption. “It’s the systematic deconstruction of security protocols that could detect and prevent misuse – such as standard incident response procedures, auditing, and change-tracking mechanisms – by removing competent professionals responsible for these security measures and substituting them with inexperienced operatives.”
Jacob Williams, a former hacker at the U.S. National Security Agency now serving as the managing director of the cybersecurity firm Hunter Labs, ignited a fierce debate recently on LinkedIn by remarking that DOGE’s network intrusions pose “a greater risk to U.S. federal government information systems than China.”
While Williams expressed doubts that members of DOGE would deliberately jeopardize the integrity and accessibility of these systems, reports (neither confirmed nor refuted) indicated that DOGE implemented alterations to code across multiple federal IT platforms. Williams contended that these code modifications were not subject to the usual vetting and review processes accorded to federal government IT systems.
“For those entertaining the notion ‘I am pleased they are skirting the standard federal IT protocols, as they are too cumbersome,’ I understand your perspective,” Williams commented. “However, another term for ‘red tape’ is ‘controls.’ If you feel at ease circumventing controls for the advancement of your objectives, I have reservations – especially regarding whether you apply the same approach in your professional duties. Kindly notify your employer when indicating that controls hold no significance (particularly if you operate in cybersecurity). Satire aside, if you are comfortable discarding controls for expediency, I urge you to delineate the boundaries where you draw the line on this matter.”
The DOGE website’s “testimonials wall” affirms that Musk and his team have economized over $55 billion for the federal government through downsizing staff, canceling leases, and terminating contracts. However, The New York Times‘ investigative team found discrepancies in the calculations supporting these savings, involving accounting inaccuracies, flawed assumptions, outdated data, and other miscues.
For instance, DOGE asserted savings of $8 billion in a single contract, which was founded on
when the overall sum turned out to be $8 million, The Times discovered.
“A Times article with six authors points out that some contracts the group takes credit for were counted multiple times,” can be read on this story. “One contract initially had a mistake that inflated the numbers by billions of dollars. While the DOGE group may have saved some billions of dollars, their careless accounting contributes to a track record of negligence by the group, which recently obtained access to critical government payment systems.”
Presently, the DOGE webpage does not instill trust: It was revealed last week that the doge.gov administrators mistakenly left their database exposed, giving someone the opportunity to post messages that mocked the site’s vulnerability.
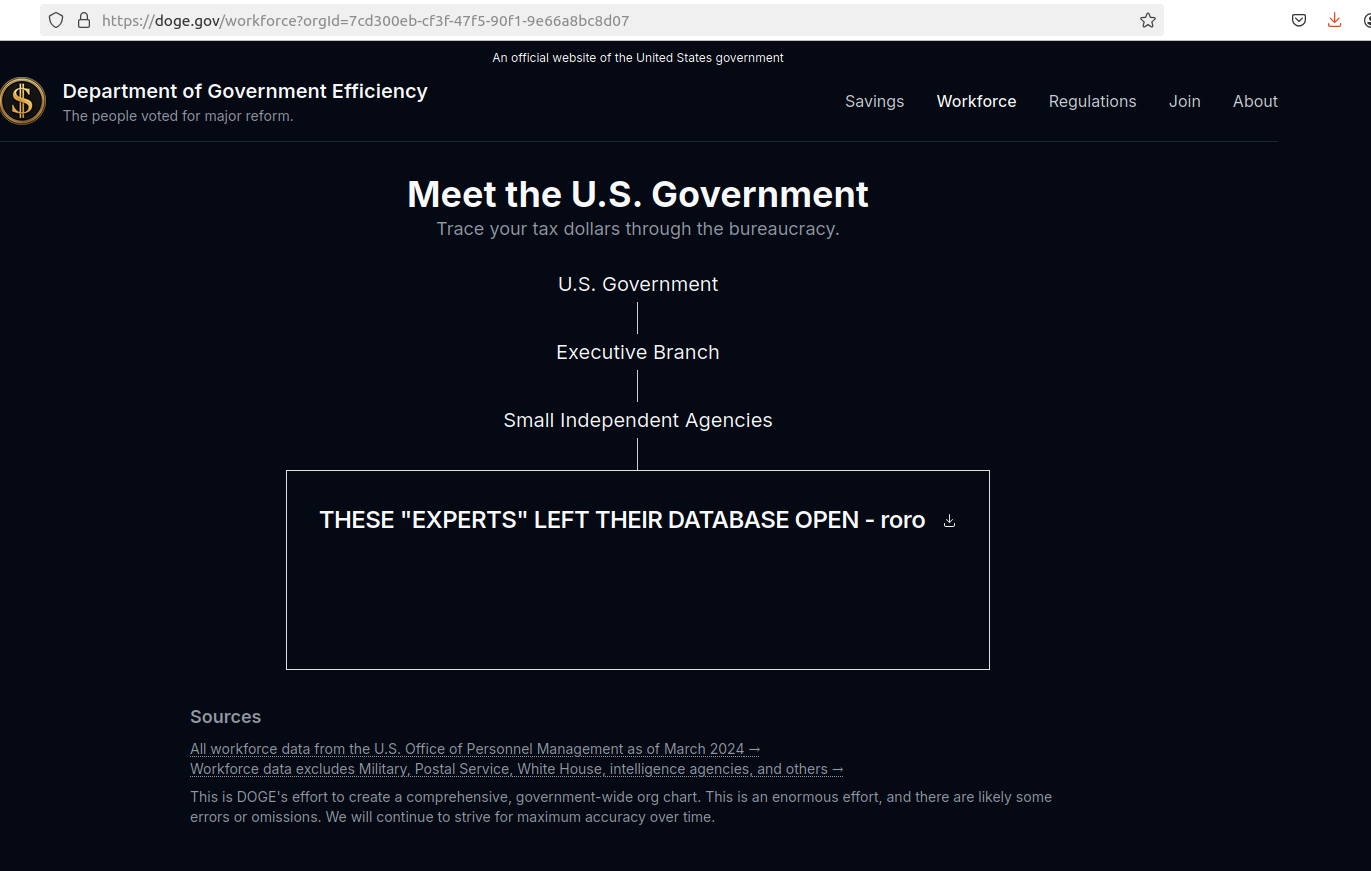
Screenshot depicting the DOGE website after being defaced with the message: “These ‘experts’ left their database open – roro”
ENGAGEMENTS
Trump’s push to take over federal agencies by their data resulted in the replacement of long-serving civil servants who had refused to grant DOGE access to agency networks. According to CNN’s report, Michelle King, who had been the acting commissioner of the Social Security Administration for over three decades, was dismissed after denying DOGE access to sensitive data.
King was succeeded by Leland Dudek, formerly a senior advisor in the SSA’s Office of Program Integrity. Dudek recently posted a now-deleted message on LinkedIn confirming that he had been put on leave for collaborating with DOGE.
“I must admit,” Dudek disclosed. “I pressured agency executives, shared executive contacts, and bypassed the hierarchy to connect DOGE with the individuals who implement decisions. I confess. I inquired about the redundancies in our contracts to ensure appropriate decisions are made.”
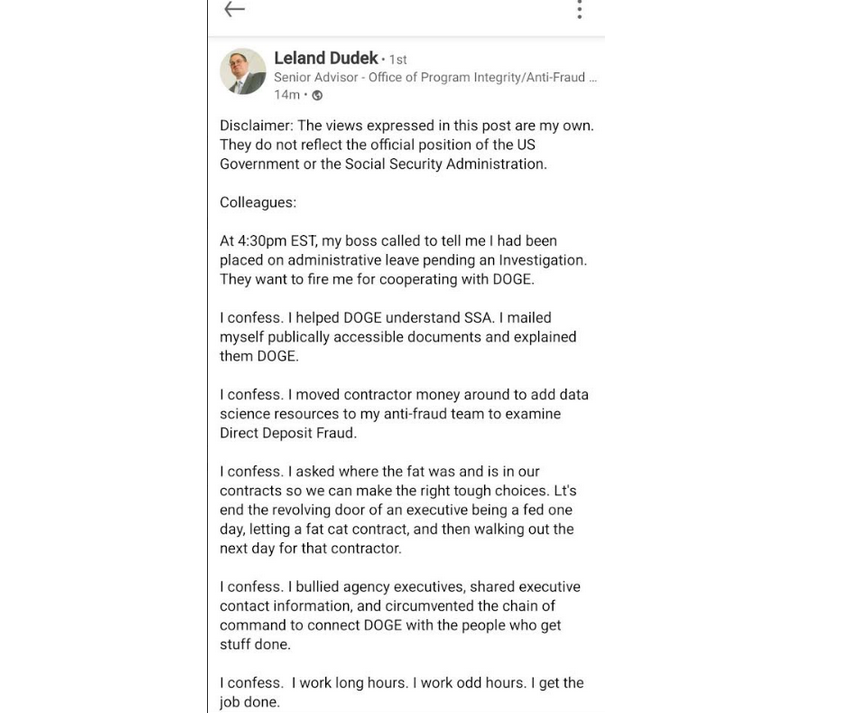
Screenshot of Dudek’s message on LinkedIn.
As reported by Wired, the National Institute of Standards and Technology (NIST) was preparing for around 500 employees to be terminated, potentially impacting NIST’s work on cybersecurity standards and software vulnerability monitoring.
“Also, last week’s cuts at the US Digital Service saw the removal of the cybersecurity lead for the central Veterans Affairs portal, VA.gov, which could make VA systems and data more susceptible without someone in his position,” detailed Wired’s Andy Greenberg and Lily Hay Newman in their write-up.
CITIZEN SAFEGUARDS?
The president directed workers at the Consumer Financial Protection Bureau (CFPB) to halt most operations. Established by Congress in 2011 to serve as a repository for consumer grievances, the CFPB has taken legal action against some of the nation’s major financial institutions for breaching consumer protection statutes.
The CFPB claims it has helped return nearly $18 billion to Americans through compensation or debt forgiveness, and imposed $4 billion in fines against transgressors. The CFPB’s website has displayed a “404: Page not found” message for several weeks now.
Trump designated Russell Vought, the creator of the conservative strategy guide Project 2025, as the CFPB’s acting head. Vought has publicly advocated for the agency’s abolishment, a viewpoint also shared by Elon Musk, whose plans to transform X into a payment platform could fall under CFPB regulation.
A detailed overview of all government staffing changes, including the dismissal of numerous senior officials from agencies involved in federal investigations or regulatory disputes with Musk’s firms, was recently released by The New York Times. Furthermore, Democrats on the House Judiciary Committee published a comprehensive report (PDF) on Musk’s various conflicts of interest.
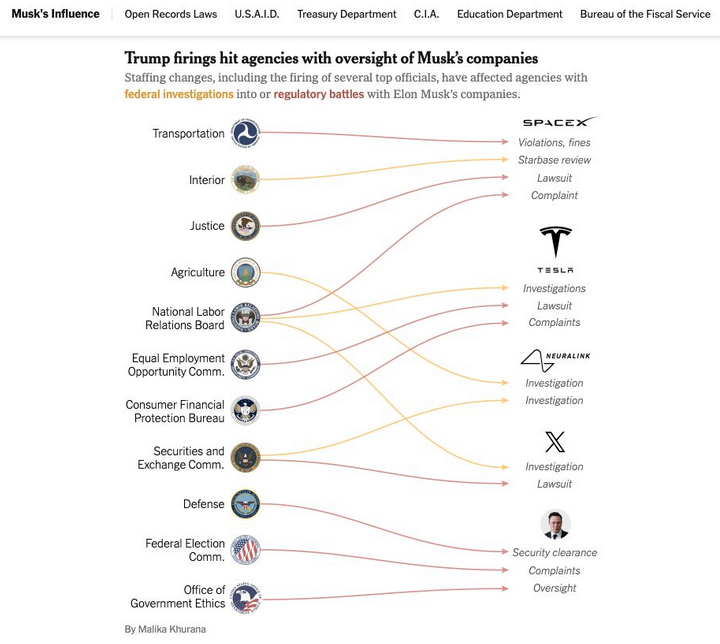
Image Source: nytimes.com
As highlighted by The Times, Musk and his enterprises have repeatedly flouted compliance.
Under the federal guidelines for safeguarding state secrets, the inadequacies have led to at least three federal evaluations. These encompass an investigation initiated by the Defense Department’s Office of Inspector General last year. Trump dismissed the DoD inspector general just four days after assuming office, along with 17 other inspectors general.
The enforcement focus of the U.S. Securities and Exchange Commission (SEC) was altered by the Trump administration from prosecuting misconduct in the cryptocurrency industry to reassigning attorneys and restructuring the unit to concentrate more on “cyber and emerging technologies.”
According to a report by Reuters report, the former SEC chair, Gary Gensler, prioritized combating misconduct in what he dubbed the “wild west” sector for the agency, aiming not only at cryptocurrency fraudsters but also at major firms facilitating trading like Coinbase.
Coinbase announced on Friday that the SEC intended to drop its lawsuit against the crypto platform. Concurrently, the cryptocurrency exchange Bybit stated on X that a cybersecurity breach resulted in the theft of over $1.4 billion in cryptocurrencies — marking it as the largest crypto theft to date.
CRIME RINGS AND FRAUD
On Feb. 10, Trump issued an order instructing executive branch agencies to cease enforcing the U.S. Foreign Corrupt Practices Act, halting investigations into foreign bribery and allowing for “remedial actions” on past enforcement cases deemed “improper.”
Trump also dissolved the Kleptocracy Asset Recovery Initiative and KleptoCapture Task Force — teams that demonstrated their effectiveness in corruption matters and in seizing the assets of sanctioned Russian oligarchs — and diverted resources from investigating white-collar offenses.
This information is per the independent Organized Crime and Corruption Reporting Project (OCCRP), an investigative media outlet that until recently received funding in part from the U.S. Agency for International Development (USAID).
The OCCRP suffered a significant funding cut and had to lay off 43 reporters and staff after Trump moved to close USAID and halt its spending. NBC News reports that the Trump administration aims to significantly reduce the agency, leaving less than 300 personnel out of the current 8,000 direct hires and contractors.
The Global Investigative Journalism Network stated this week that the sudden stop in USAID foreign aid funds has frozen an estimated $268 million in approved grants for independent media and the unrestricted sharing of information across more than 30 nations, some under oppressive regimes.
Without providing evidence, Elon Musk has labeled USAID as “a criminal organization” and has used his social media platform X to propagate fringe theories claiming the agency operated without supervision and was plagued with fraud. A few months before the election, USAID’s Office of Inspector General announced an inquiry into USAID’s oversight of Starlink satellite terminals received by the Ukrainian government.
According to KrebsOnSecurity, all outgoing emails from USAID are now labeled as “sensitive but unclassified,” a classification that experts say could complicate efforts for journalists and others to obtain records of USAID emails under the Freedom of Information Act (FOIA). Fedscoop reported on Feb. 20 that they also received similar information from multiple sources, noting that the added message would not be visible to senders until after the email is sent.
FIVE POINTS
On Feb. 18, Trump issued a directive stating that only the U.S. attorney general and the president have the authority to provide official interpretations of the law within the executive branch, extending this mandate to independent agencies under the executive branch.
Trump contends that the power is vested in the president by Article II, Clause 1 of the Constitution. However, jurist.org explained that Article II does not explicitly assign the president or any other executive branch figure the authority to interpret laws.
“The article mandates the president to ‘take care that the laws be faithfully executed,’” Juris pointed out. “The jurisdiction to interpret laws and ascertain their constitutionality is reserved for the judicial branch under Article III. The founders of the Constitution established the division of responsibilities to prevent a single branch from consolidating too much power.”
The directive mandates that all agencies comply with “performance standards and management objectives” set by the White House Office of Management and Budget and periodically report to the president.
These performance benchmarks are already being requested: Employees from several federal agencies received an email on Saturday from the Office of Personnel Management instructing them to respond with a set of bullet points outlining their accomplishments for the previous week.
“Kindly reply to this email with around 5 bullet points detailing your achievements last week and cc your supervisor,” the directive read. “Avoid sending classified details, links, or attachments. Deadline is this Monday at 11:59 p.m. EST.”
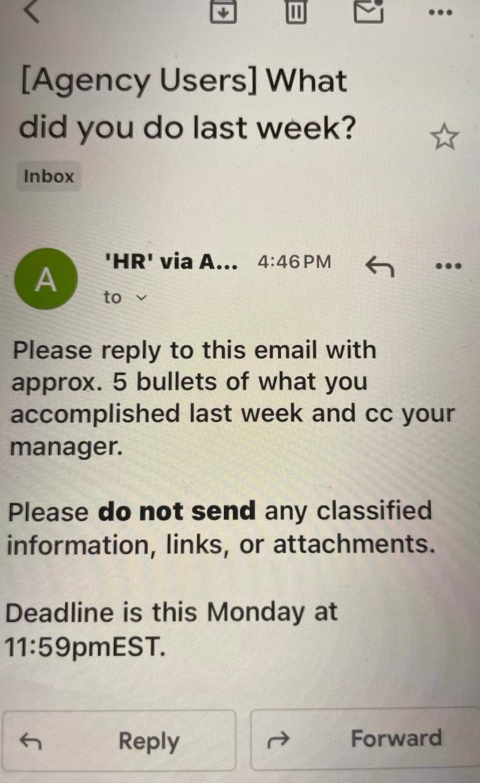
An email sent by the OPM to more than two million federal employees late in the afternoon EST on Saturday, Feb. 22.
In a social media post on Saturday, Musk indicated that the instruction came from President Trump and a failure to comply would be considered a resignation. Meanwhile, Bloombergstates that the Justice Department is advising workers to refrain from responding due to potential ethics breaches. The Federal Employees Union is also counseling its staff not to engage.
A legal dispute over the recent executive order issued by Trump is set to be part of a broader selection of more than 70 ongoing lawsuits aiming to block the government’s plans to significantly downsize the federal workforce through terminations, dismissals, and attrition.
THE REIGN OF TRUMP?
On the 15th of February, the president shared on social platforms, “He who rescues his Nation doesn’t violate any Statute,” citing a phrase often linked to the French dictator Napoleon Bonaparte. Four days later, Trump described himself as “the monarch” on social media, while the White House casually posted an image of him adorned with a crown.
Trump has been publicly contemplating the idea of pursuing an unconstitutional third tenure in office, a notion that some of his advocates shrug off as Trump merely attempting to provoke his progressive critics. However, just days after commencing his second term, Congressman Andy Ogles (R-Tenn.) proposed a bill to amend the Constitution in order for Trump — and any future president — to be eligible for a third term.
During this week’s Conservative Political Action Conference (CPAC), Rep. Ogles purportedly spearheaded a coalition of Trump enthusiasts known as the “Third Term Project,” which aims to garner support for the bill from Republican legislators. The gathering showcased depictions of Trump resembling Caesar.

A banner at the CPAC conference this week in support of The Third Term Project, a group of conservatives trying to gain support for a bill to amend the Constitution and allow Trump to run for a third term.
Russia continues to stand amongst the globe’s leading purveyors of cyber mischief, drugs, illicit finances, human exploitation, misinformation, warfare, and fatality, while the Trump administration has abruptly veered away from Western norms in normalizing ties with Moscow.
This week, President Trump startled U.S. affiliates by echoing Kremlin viewpoints that Ukraine is somehow accountable for Russia’s incursion, and that Ukrainian President Volodymyr Zelensky is a “tyrant.” The president reiterated these untruths even as his administration insisted that Zelensky relinquish half of his nation’s mineral assets to the United States in return for a pledge that Russia would cease its territorial aggression there.
President Trump’s subservience to an authenticated tyrant — Russian President Vladimir Putin — does not augur well for the enhancement of U.S. federal IT systems’ security, or the corporate infrastructures on which the government is vastly reliant. Furthermore, this administration’s perplexing gestures to estrange, provoke, and sideline our closest partners could complicate the U.S.’s efforts to secure their continual cooperation in cyber misconduct investigations.
It’s astonishing how closely DOGE’s strategy mirrors the tactics frequently employed by ransomware syndicates: A clique of individuals in their twenties with monikers like “Daring Adventurers” arrives on a weekend and accesses your servers, erases data, locks out crucial personnel, shuts down your website, and prevents you from catering to clients.
When the federal leadership starts emulating ransomware methods against its internal agencies while Congress observes mostly in either confusion or jest, we are reaching a critical juncture. In theory, one can negotiate with ransomware distributors.









