It’s common knowledge that 2024 has been a turbulent year on various fronts. In our second Live Opponent Report of 2024, we’re specifically focusing on trends and advancements we observed during the initial half of the year (1H24). Although outwardly the year may have seemed uneventful for those responsible for the protection of small- and medium-sized businesses, the ongoing battle between infiltrators and protectors continued with intriguing dynamics simmering just beneath the surface.
Main Highlights
- Increase in exploitation of integrated Microsoft services (LOLbins) is notable
- RDP misuse remains widespread, with a new angle
- The ransomware scene: Banyans vs poplars
Source of the data
The information in this report is extracted from incidents managed in the initial half of 2024 by a) our outward-facing IR team and b) the response team dealing with critical incidents among our Managed Detection and Response (MDR) clients. When relevant, we compare the findings from the 190 incidents chosen for this report with data accumulated from previous Sophos X-Ops casework, dating back to the inception of our Incident Response (IR) service in 2020.
In this report, 80 percent of the data was obtained from organizations with fewer than 1000 employees. This percentage is lower compared to 88 percent in our previous report; the change is mainly (but not completely) due to the inclusion of MDR cases. Nearly half (48%) of the organizations requiring our support have 250 employees or fewer.
What are the activities of these organizations? As has been the trend in our Live Opponent Reports since their initiation in 2021, the manufacturing sector was the sector most likely to seek Sophos X-Ops response services, although the percentage of customers from Manufacturing has significantly decreased, from 25% in 2023 to 14% in the initial half of 2024. Construction (10%), Education (8%), Information Technology (8%), and Healthcare (7%) constitute the top five industries. In total, this dataset encompasses 29 different industry sectors. Additional details regarding the data and selection methodology for this report can be explored in the Supplementary section.
The remainder of the report delves into our discoveries, as outlined in the main highlights above, and includes updates on various issues raised in previous editions of the report. A comprehensive analysis of the 2024 dataset will be conducted in the upcoming report scheduled for early 2025.
Designed for operation (natively): LOLbin usage on a rapid ascent
LOLbins – legitimate but misused binaries already existing on the system or commonly downloaded from legitimate sources associated with the OS – have always been part of the Live Opponent landscape. We differentiate these from what we call “artifacts,” which are unauthorized third-party packages introduced onto the system by attackers (e.g., mimikatz, Cobalt Strike, AnyDesk). LOLbins are genuine files, signed, and when employed in seemingly harmless ways, they are less likely to attract the attention of a system administrator.
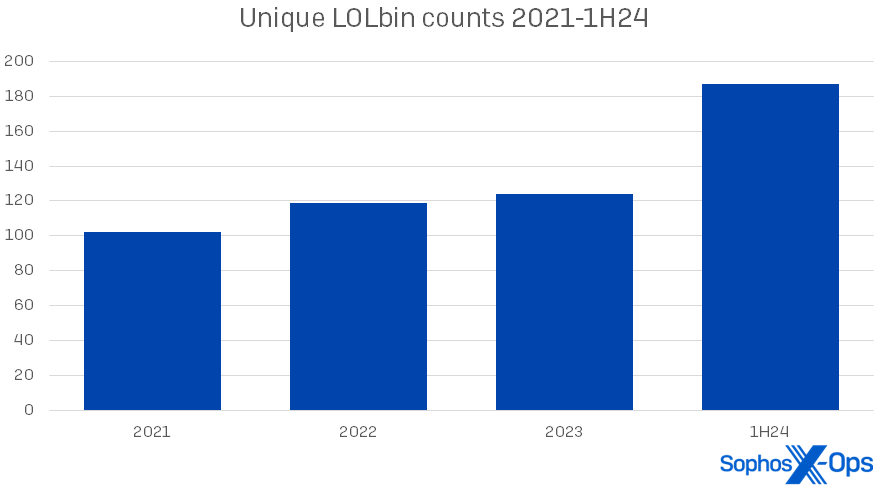
This year, we observed a modest increase in the utilization and diversity of artifacts, which we will examine later in this report. However, the surge in LOLbins is striking. (For this edition of the report, we are primarily focusing on binaries in the Microsoft Windows operating system, although we also observe their misuse in other OSes.) In the initial half of 2024, we identified 187 unique Microsoft LOLbins used across our 190 incidents – with over a third of them (64) appearing only once in our dataset. This marks a 51% increase compared to the LOLbin numbers in 2023. The overall escalation in LOLbin counts since 2021 is depicted in Diagram 1.
Diagram 1: The sudden spike in LOLbin usage in 1H24 follows years of gradual increase in usage
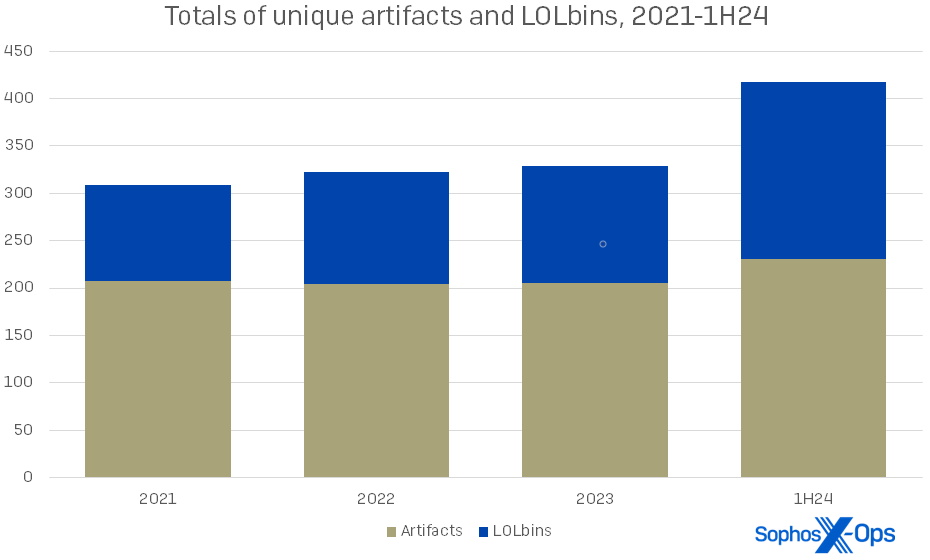
Just three years back, our 2021 statistics revealed that artifacts were over twice as prevalent as LOLbins in our incidents. Today, the ratio is closer to 5:4, as displayed in Diagram 2.
Diagram 2: Both artifact and LOLbin usage are increasing overall, and offenders are deploying more of both to test their effectiveness. In a specific incident this year, the response team documented 14 artifacts and 39 LOLbins in action
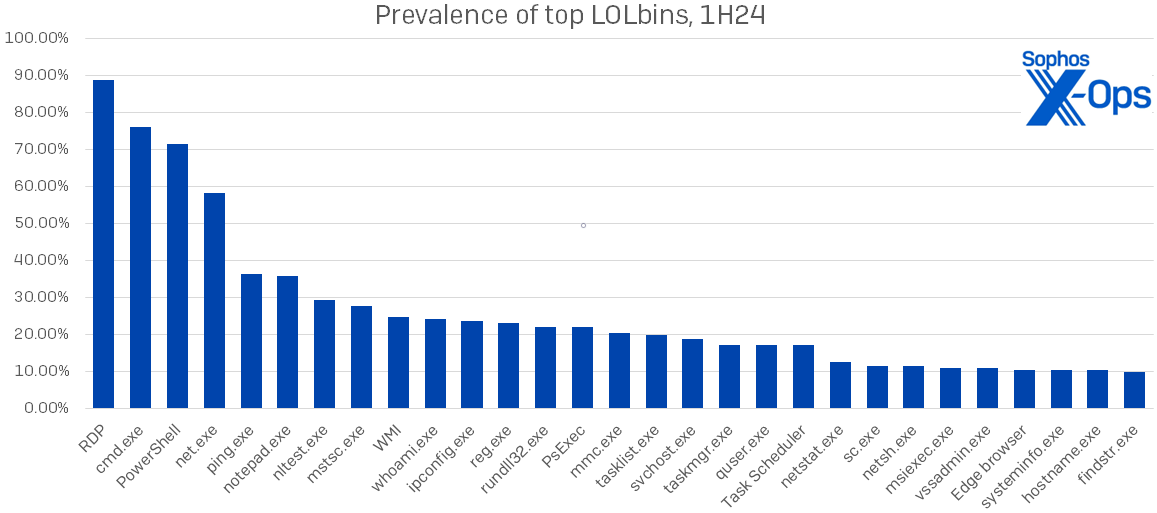
Which LOLbins are attackers exploiting? Notably at the forefront, as always, is RDP, on which we will provide additional insights in the following section. We identified 29 specific LOLbins in use in at least 10% of incidents; their names and prevalence are depicted in Diagram 3. This signifies a significant rise compared to last year’s distribution, where only 15 of the 124 distinct LOLbins identified were present in over 10% of incidents.
Diagram 3: The most frequently identified LOLbins in 1H24; all of these were present in at least 10% of incidents
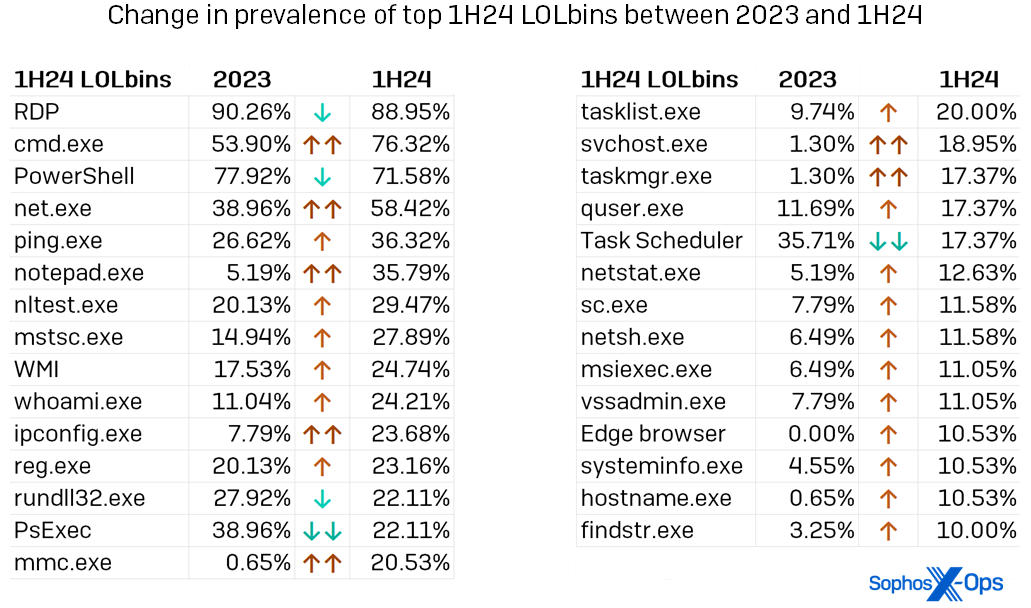
Most of the names in the diagram above are unsurprising to regular readers of the Live Opponent Report – RDP leads the pack, with cmd.exe, PowerShell, and net.exe showcasing their usual prominence. However, we observe increased usage of even some of these well-known LOLbins as detailed in Diagram 4, which also highlights the percentage increase in utilization for each LOLbin identified in over 10% of 1H24 incidents. Note the prevalence of binaries used for system reconnaissance or enumeration – 16, according to our evaluation.
Figure 4: Among the leading 29 LOLbins identified in action during 1H24, only five were noticed less frequently than in 2023. (LOLbins for which utilization significantly altered – either 15 percent higher or lower than the previous year’s data – are highlighted above with dual arrows). Please bear in mind that in the given list context, “Task Scheduler” incorporates both Task Scheduler and schtasks.exe, while WMI includes the obsolete WMIC
What strategies should a safeguard implement? Primarily, this shift in toolset implies that merely monitoring your network for anomalies isn’t sufficient. Every LOLbin is in some manner a component of the operating system, ranging from RDP down to fondue.exe, tracert.exe, and time.exe (three of the single-use LOLbins observed in the figures). Understanding the individuals present on your network and their authorized activities is now more critical than ever. If IT’s Alice and Bob are employing PowerShell, it’s likely acceptable. If PR’s Mallory is utilizing PowerShell, it warrants inquiry.
Moreover, comprehensive logging and informed network monitoring are indispensable. At a certain juncture during our assessment, we pondered whether the upsurges we noted might be partly due to integrating the data from our MDR unit. Following data normalization, we ascertained that this wasn’t the case, yet we were once again taken aback by the difference that having MDR-type oversight on the system makes concerning both initial access and repercussions. (Further details on these will follow shortly.)
To delve deeper into LOLbins, encompassing the functionalities of individual binaries and their typical integration into the MITRE ATT&CK framework, we recommend exploring the LOLBAS collaborative venture on Github.
RDP (Abbreviation for Repeating the Damn Problem)
For a publication that relishes incorporating pop-music allusions, Active Adversary echoes like a scratched vinyl record: RDP, RDP, RDP. As demonstrated in the earlier illustrations, RDP reigns supreme as a source of cybersecurity challenges, with almost 89 percent of the incidents encountered in 1H24 displaying some form of RDP misuse.
A closer examination of the incidents involving RDP reveals little change in the prevalence of internal versus external exploitation. These patterns have remained constant over the years, as illustrated in Figure 5.
Figure 5: In 2022 and 2023, several incidents saw attackers obscure their RDP activities to such an extent that the response team struggled to definitively discern which actions proved successful; 1H24 showed some improvement in this area at least
Looking slightly beyond the scope of this report, the monotonous RDP misuse statistics were momentarily disrupted in September when Microsoft disclosed that the firm is launching a cross-platform “Windows App” (its official title) aimed at offering remote access to Windows 10 and 11 devices from “work or school accounts,” with pledged RDP access in the future. Despite the company’s assertions of bolstered security features, including multifactor authentication capabilities, most observers predominantly viewed Windows App as essentially a rebranded Remote Desktop client. The next Active Adversary Report, whether featuring positive news of reduced RDP misuse or not, remains a mystery.
Stirring the pot: The tall trees and broad-leafed trees of ransomware
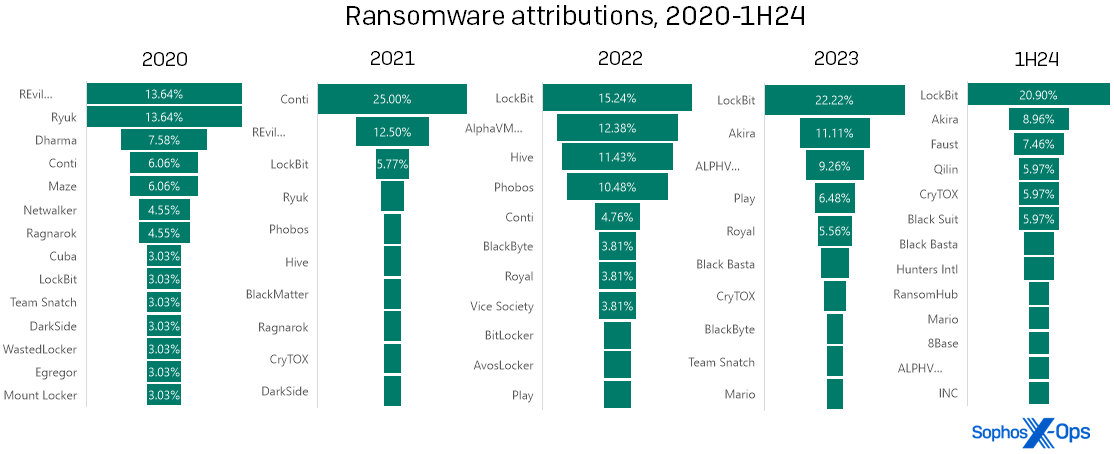
Shifting focus to ransomware, an analysis of the data on ransomware incidents yielded an intriguing observation: Pertaining to attribution, the connection between high-profile ransomware crackdowns and decreased representation on our graphs doesn’t always exhibit the expected correlation.
Historically, certain years witness the dominance of a single ransomware variant overshadowing others akin to the dome of a banyan tree, while other years distribute ransomware incidents fairly evenly among multiple variants, resembling a row of tall poplar trees. Typically, this variance aligns with legal interventions (“crackdowns”) on notable ransomware groups. Nevertheless, the first half of 2024 diverged from this trend in our data. LockBit reigned as the primary ransomware in 2023 but faced law enforcement disruption in late February 2024. Despite this, LockBit persisted as the predominant ransomware encountered by the incident response team in the initial half of the year.
Figure 6: Poplar, banyan, poplar, banyan… banyan?! The pattern we’ve observed in ransomware attributions over the past several years seems to have broken down in 1H24 with LockBit… maybe. (Two of the labels above are truncated for space; “REvil….” is more fully “REvil / Sodinokibi,” while “ALPHV….” is “ALPHV/BlackCat”)
Admittedly, legal actions seldom produce a significant dent in the overall ransomware landscape – they disrupt targeted threat actors but do not permanently eliminate most involved entities. With each substantial legal intervention, the multitude of other contenders vying for prominence means thatThe space is filled and much more. Noticeably, Conti only accounted for 6 percent of infections identified in 2020… and then Ryuk (2020) and Revil (2021) faced takedowns by the gang or, in Ryuk’s case, the Trickbot distribution system it relied upon. Subsequently, Conti (presumably descended from Ryuk) thrived for a year (2021) but dwindled to single-digit levels by the end of 2022. In the case of LockBit, the owner of the brand made an effort for a “comeback” around mid-2024, reconstructing its infrastructure and even reviving its blog. (A version of LockBit’s ransomware builder was also notably exposed by a disaffected associate in September 2022, potentially impacting its prevalence.)
What’s on the horizon? Initially, there’s a possibility that the trend will resolve itself in the data from the latter part of the year – the “banyan” may evolve into a “poplar” as predicted. In the weeks following the LockBit takedown, both Sophos’ MDR and IR teams, respondents from our 2024 State of Ransomware survey, and other industry observers reported a decrease in LockBit infections. These numbers spiked briefly in May; it’s common to observe this type of ripple effect after law enforcement intervention, but eventually, the reverberations subside.
Moreover, the title of the subsequent prevalent ransomware is likely present in the aforementioned chart, suggesting that although system administrators may hesitate to commit to a specific brand, the perpetrator is probably already under the scrutiny of defenders. Those preparing to deflect the next assault on their systems can begin by monitoring updates on known entities and newcomers. It’s rational to acknowledge the apprehension that individuals like Mikhail Matveev and Ekaterina Zhdanova are facing legal repercussions, but the narrative is far from over.
In general, ransomware incidents witnessed a slight decline in the initial half of the year. In IR, ransomware was implicated in 61.54 percent of cases handled, compared to 70.13 percent in 2023. (The shortfall was more than made up for by network breaches, which nearly doubled their occurrence in IR cases – 34.62 percent in 1H24, against 18.83 percent in 2023. A meticulous analysis of all available data leads us to suspect that while the decrease is real, it may not be as distinct when the full year’s figures are scrutinized.)
Meanwhile, MDR mainly dealt with network breaches in 1H24, with only 25.36 percent of their cases attributed to ransomware. It’s worth noting that MDR, due to the nature of its service, typically confronts and mitigates ransomware at a much earlier stage in its propagation cycle than the IR team does – often before encryption or deployment, thus avoiding the necessity for the kind of response detailed in the Active Adversary Report. (Sadly, for the IR team, “attack detected” generally translates to “the client realized they might be under attack upon receiving a ransom demand and finding all their computers encrypted.”) By the end of June, LockBit’s supremacy was already tapering off for the MDR team, with 17.14 percent of their ransomware attributions linked to that brand, and both Akira and BlackSuit following closely at 11.43 percent each. (And to close the loop, both Akira and BlackSuit are offshoots of… Conti. The same saga, with a new twist.)
**Comin’ in and out of your life: Initial access and impact**
The third and fourteenth stages of the MITRE ATT&CK Matrix consistently captivate readers; we previously touched upon the variations we observed between two very alike cases managed by our IR and MDR processes in a previous report. For this report, our MITRE-focused analysis will delve into the categories themselves, Initial Access, and Impact.
**Initial Access** in the first half of 2024 mirrored previous years. As anticipated from the RDP statistics, External Remote Services techniques dominated the category, constituting 63.16 percent of cases compared to 64.94 percent in 2023. Valid Accounts (59.47%, down from 61.04%) and Public-facing Application Exploitation (30%, up from 16.88%) complete the top three. (Given that cases might involve several initial access techniques, the percentages will not sum up to 100.)
The scenario is more intriguing in regard to **Impact**, the final category in the MITRE matrix. After consistently prevailing in the Impact category, being part of at least two-thirds of all cases, Data Encryption for Impact (a standard step in ransomware assaults) dwindles to the second spot with 31.58 percent, slightly above the emerging Data Manipulation (30%) and trailing No Impact at 38.95 percent.
We previously highlighted the nuanced definition of “No Impact” within the realm of ATT&CK. ATT&CK currently acknowledges fourteen techniques as “Impact.” These methods are evolving to align with contemporary ransomware payout realities and productivity losses. Incident responders are keenly aware that there is a discrepancy between the literal interpretation of “No Impact” and the actual consequences encountered. Although it’s satisfying to hear “No Impact,” it doesn’t negate the aftermath; rather, it suggests that the outcome surpasses ATT&CK’s vocabulary to encapsulate it completely.
**Where are they now: Checking on the previous AAR findings**
To keep this edition concise, we will briefly touch on a few subjects of previous interest before our comprehensive report for 2024.
**Dwell time:** The numbers for dwell time have been on a decline, as presented in our initial 2023 report. The 1H24 statistics indicate that this decline has halted or perhaps slightly reversed for cases managed by our Incident Response team. Median dwell times for ransomware hover around 5.5 days; encompassing all other incident types, the median stands at 8 days. While we do not possess MDR cases from prior years for the report team to analyze, a glimpse at their 1H24 data underscores the impact of monitoring – medians of 3days for ransomware and a single day for all kinds of incidents. Given that the cases requiring incident response in Managed Detection and Response (MDR) are a small portion of the overall daily activity seen, the importance of constant vigilance remains a task for the reader.
Time-to-AD: In our second report of 2023, we examined the timeframe for attackers to assume control of the target’s Active Directory – a critical point indicating a compromised target – and the duration from seizing control of AD to detecting the attack. This data shows significant discrepancies between MDR and Incident Response (IR) figures. In the first half of 2024, the time taken by attackers to reach Active Directory increased slightly from previous years, with the interval extending by about two hours (15.35 hours in 2023, 17.21 hours in 1H24). Notably, the time lapse between AD seizure and attack detection decreased (29.12 hours in 1H24, down from 48.43 hours in 2023), a trend that may warrant further investigation in future reports based on more extensive data.
We observed Active Directory compromises most frequently on Server 2019 (43%), Server 2016 (26%), and Server 2012 (18%), collectively comprising 87% of compromised AD servers. All these versions are presently beyond mainstream Microsoft support, despite the Patch Tuesday updates specifying applicable patches for each version. If your systems are running outdated Server versions, consider this data as a prompt to initiate updates. (For those monitoring our Patch Tuesday updates, we will now provide additional details on the affected Server versions in each month’s patches.)
Compromised credentials: Our second 2023 report highlighted the surge in incidents rooted in compromised credentials. In 2023, compromised credentials were found in 56% of all incidents. However, this dominance lessened somewhat in the first half of 2024. While compromised credentials still remained the primary root cause of incidents in 2024, this was predominantly driven by IR cases, as depicted in Figure 7. For MDR clients, exploited vulnerabilities assumed the lead in the root-cause breakdown, albeit by a slim margin.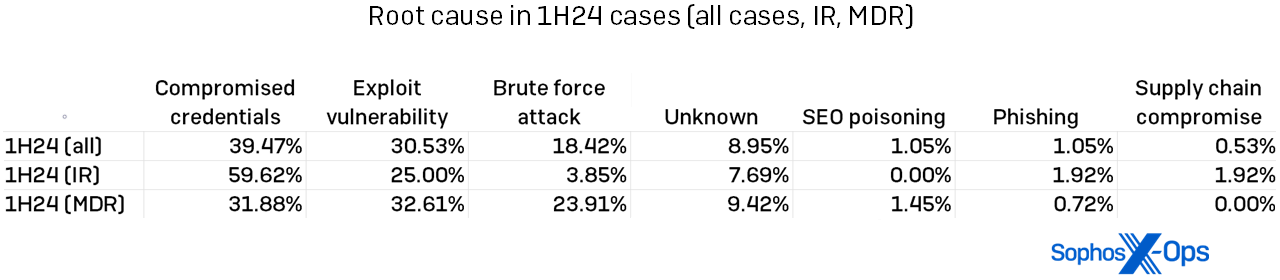
Figure 7: The distribution of root causes between IR and MDR handled incidents was varied, with compromised credentials being a predominant factor in IR scenarios
An Ode to Artifacts Before Farewell
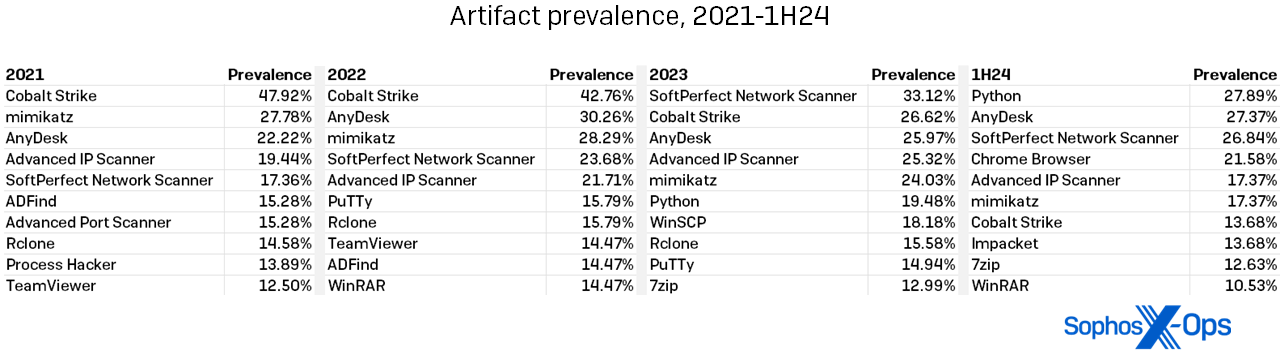
As mentioned earlier, our analysis revealed a rise in third-party artifacts alongside LOLbins in the cases observed in the first half of 2024. Though the increase in artifact usage was less pronounced compared to LOLbins, certain aspects warrant further examination.
Firstly, there was a slight uptick in the numbers. We identified 230 unique artifacts on targeted systems in the first half of 2024, up from 205 in all of 2023 – a 12% increase. (For perspective, 2022 had 204 artifacts and 2021 had 207.)
Secondly, frequently encountered artifacts retained consistent names year over year, as indicated in Figure 8. Notably, Cobalt Strike usage continued its decline that began in 2023, being present in only 13.68% of infections in the first half. (Previously, Cobalt Strike featured in nearly half of the cases and remains the most prevalent artifact finding to date. Improved defender detections likely explain this reduction.) 127 artifacts were single-use discoveries in the 1H24 data, fewer than the 102 unique findings in 2023.
Figure 8: The trend of increasing diversity in artifact use persisted, with no single artifact appearing in over 30% of cases in the first half of 2024
A defender learning that over half of all artifacts are single-use tools may perhaps despair of catching everything an attacker might throw at them. We would encourage that defender to peruse the table above and note that while the supporting cast may vary, the “star” artifacts in the galaxy persist. The table above comprises all artifacts present in over 10.00% of cases across four years. Diligently monitoring these packages is practical and beneficial. Consider implementing a default-block policy for applications on your systems; while it requires some initial effort, it helps prevent issues as attackers diversify their toolsets.
Final Thoughts
It has been truly enlightening for the AAR analysis and authoring team to observe the shifts in statistics as we integrated extensive data from Sophos X-Ops’ MDR division with the longstanding database from our IR partners. Exploring this data led us to profound changes – who would have thought LOLbins could be fascinating? – and recurring patterns like RDP misuse that persist despite established best practices such as vigilant monitoring.
Above all, we are struck by the number of cases rooted in basic principles – not just the three immortalized in the Sophos “haiku”
but in simple pattern recognition that could have potentially prevented customers from ever entering a dataset like this. Our aspiration is that this detailed snapshot of the recent Active Adversary Report landscape will assist professionals in intensifying their focus on fundamental practices that enhance safety and security for all.
Acknowledgements
The authors extend their gratitude to Chester Wisniewski, Anthony Bradshaw, and Matt Wixey for their valuable contributions to the AAR process.
Appendix: Participant Statistics and Methodology
For this study, we examined 190 cases that yielded valuable insights on the current adversary landscape in the first half of 2024. Safeguarding the confidential relationship between Sophos and our clients remains our top priority.Importance is paramount here, and the information provided has been thoroughly checked at various points during this procedure to guarantee that no individual customer can be identified through the data – and that no individual customer’s data distorts the total inappropriately. If uncertain about a particular scenario, we opted to omit that customer’s data from the dataset.
Let’s highlight a multi-year scenario involving our MDR team. This scenario, which dealt with nation-state operations across several regions, has previously been documented as “Crimson Palace.” Although intriguing and serving as a sign of specific attack strategies we’ve observed elsewhere since, it diverges significantly from the vast majority of the Active Adversary dataset in multiple aspects, thus its figures have been excluded from the report.
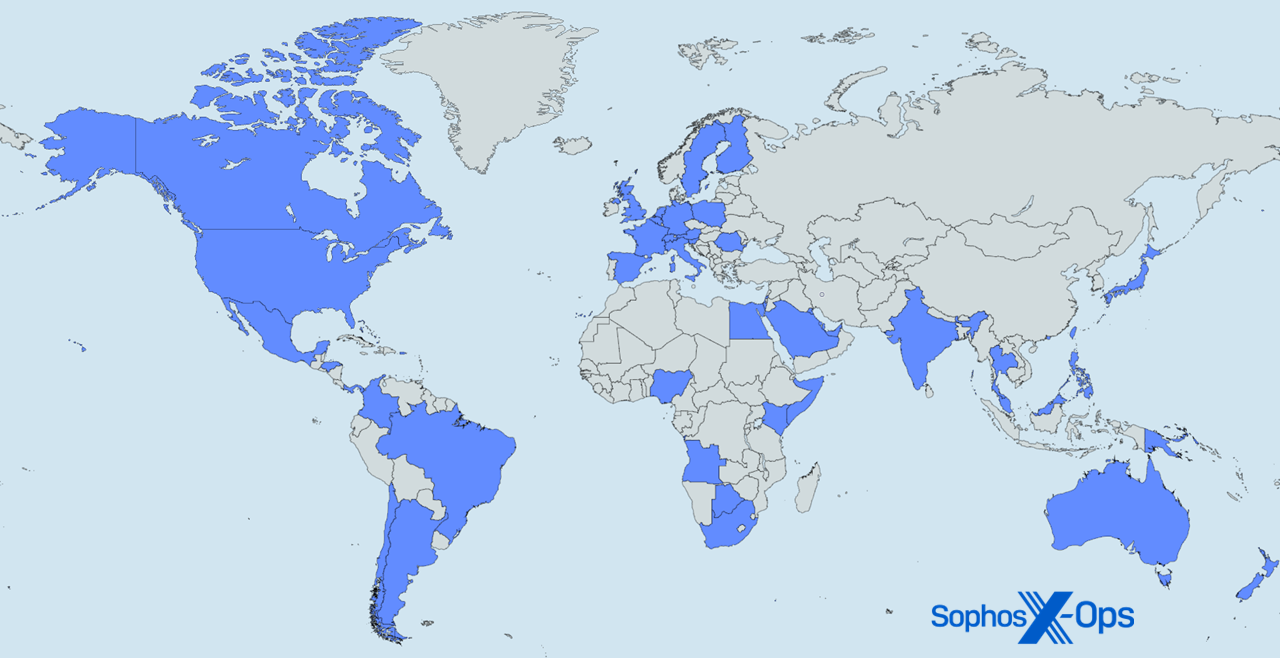
Figure A1: Over here, over there, everywhere — It’s the global reach of Sophos X-Ops MDR and IR (Map courtesy of mapchart.net)
The subsequent 48 countries and other regions are reflected in the 1H24 information examined for this report:
| Angola | Honduras | Poland |
| Argentina | Hong Kong | Qatar |
| Australia | India | Romania |
| Austria | Israel | Saudi Arabia |
| Bahamas | Italy | Singapore |
| Bahrain | Japan | Slovenia |
| Belgium | Kenya | Somalia |
| Botswana | Kuwait | South Africa |
| Brazil | Malaysia | Spain |
| Canada | Mexico | Sweden |
| Chile | Netherlands | Switzerland |
| Colombia | New Zealand | Taiwan |
| Egypt | Nigeria | Thailand |
| Finland | Panama | United Arab Emirates |
| France | Papua New Guinea | United Kingdom |
| Germany | Philippines | United States of America |
Sectors
The subsequent 29 sectors are depicted in the 1H24 information scrutinized for this report:
| Marketing | Banking | Service Providers/Hosting |
| Agribusiness | Culinary | Non-governmental |
| Design | Public Sector | Medicinal |
| Comms | Health | Property |
| Building | Hotelier | Merchandising |
| Teaching | IT | Facilitation |
| Electronics | Legal Services | Transport |
| Fuel | Shipment | Public Services |
| Designing | Manufacture | Distributive |
| Amusement | Extraction |
Approach
The information in this report was collated over the course of various inquiries conducted by Sophos’ X-Ops Incident Response and MDR teams. For this second report of 2024, data on all inquiries conducted by the teams in the first half of the year was consolidated and standardized across 63 fields, with each inquiry being carefully scrutinized to ensure that the data provided was suitable in both detail and breadth for collective reporting as outlined in the report’s focus. Further efforts were made to align the data collection between our MDR and IR reporting procedures.
In cases where data was ambiguous or absent, the authors collaborated with individual IR and MDR case leaders to clarify uncertainties or misunderstandings. Cases that could not be sufficiently clarified for the report’s purpose, or where the inclusion posed a risk of exposure or other potential harm to the Sophos-client relationship, were set aside. Subsequently, each remaining case’s timeline was examined in detail to gain additional insight into aspects such as initial breach, time spent within the system, data extraction, among others. A total of 190 cases were retained, forming the basis of this report.