
ESET Investigation
Researchers from ESET stumbled upon a previously unknown security flaw on Telegram for Android, enabling the transmission of disguised malicious files as videos
22 Jul 2024
•
,
6 min. read

ESET technicians unearthed a zero-day loophole that aims at Telegram for Android, which was spotted up for sale at an undisclosed price in an underground forum post dated June 6th, 2024. By tapping into this loophole dubbed EvilVideo, malevolent actors could distribute harmful Android payloads through Telegram channels, communities, and conversations, camouflaging them as multimedia items.
An example of the loophole was discovered, allowing a deeper analysis, and the report was forwarded to Telegram on June 26th, 2024. Subsequently, on July 11th, an update was rolled out resolving the vulnerability in Telegram versions 10.14.5 and onward.
Figure 1 showcases a video presentation and elucidation of the EvilVideo loophole.
Figure 1. Elaboration on the EvilVideo loophole
Highlights from the blog post:
- On June 26th, 2024, an under-the-radar network revealed a zero-day loophole aiming at Telegram for Android.
- We christened the vulnerability as EvilVideo and duly notified Telegram; their team addressed it on July 11th, 2024.
- EvilVideo enables attackers to disperse malicious payloads masquerading as video files on unpatched versions of Telegram for Android.
- The loophole exclusively functions on Android Telegram versions 10.14.4 and earlier.
Unearthing
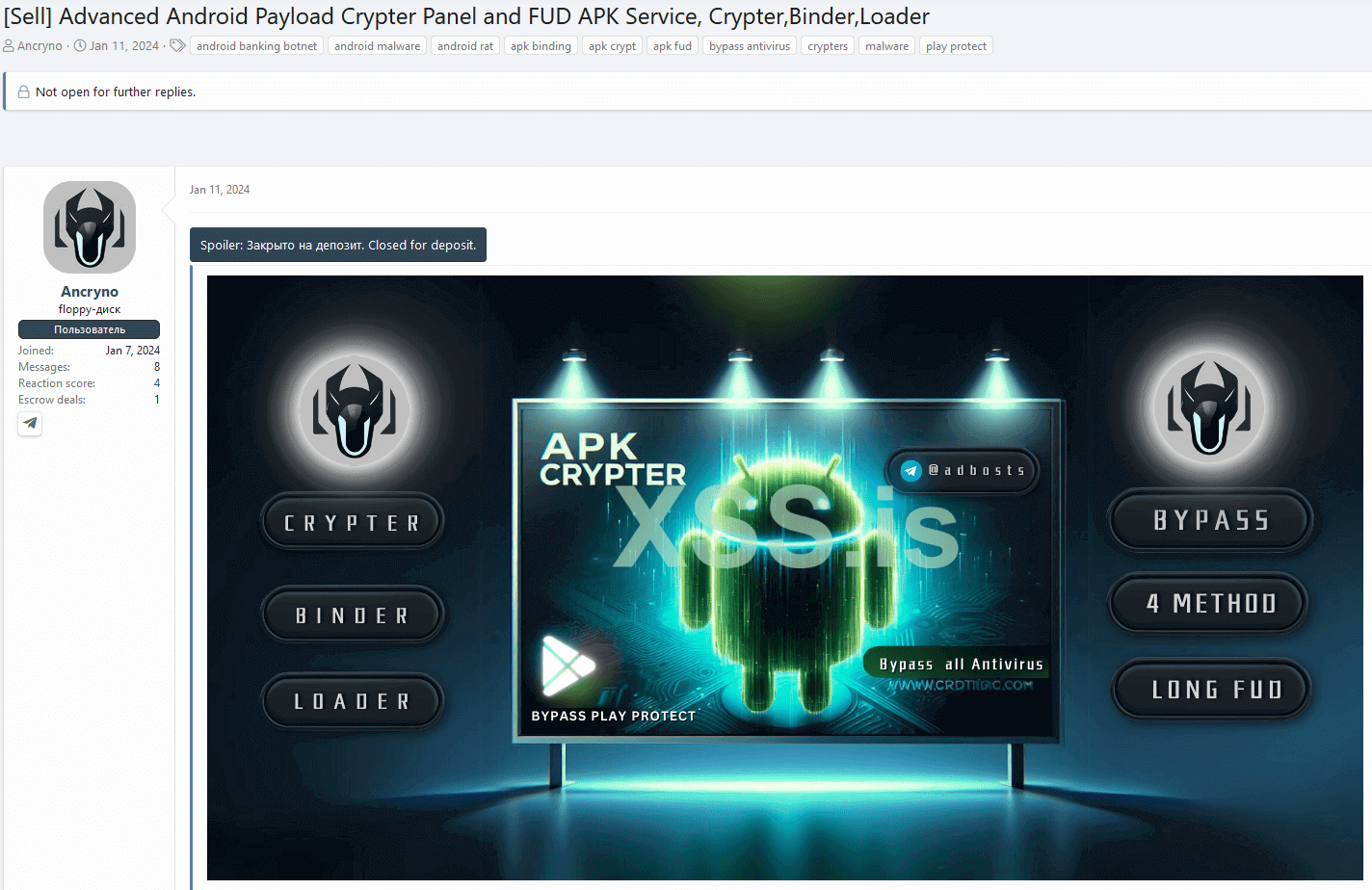
We stumbled upon the loophole being promoted for sale on an under-the-radar network: refer to Figure 2.
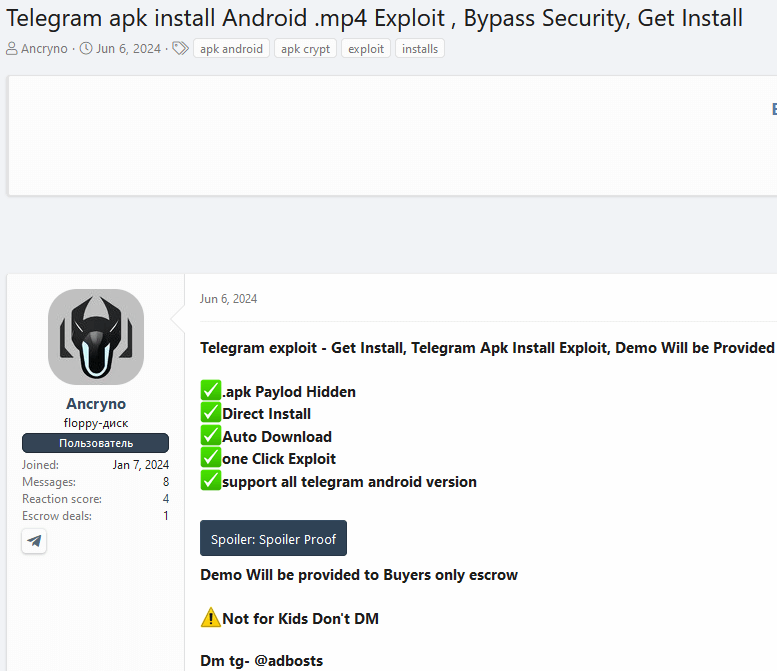
In the post, the vendor showcases screenshots and a video illustrating the testing of the loophole in a public Telegram channel. We identified the specific channel and accessed the loophole, allowing us to acquire the payload and run our own tests.
Assessment
Our evaluation of the loophole disclosed its operability on Telegram versions 10.14.4 and prior. We hypothesize that the custom payload is presumably tailored using the Telegram API, offering developers the ability to programmatically upload meticulously crafted multimedia files to Telegram discussions or channels.
The loophole appears to depend on the malefactor’s capability to develop a payload that presents an Android application as a multimedia preview instead of a binary attachment. Upon being shared in a conversation, the treacherous payload manifests as a 30-second video (Figure 3).
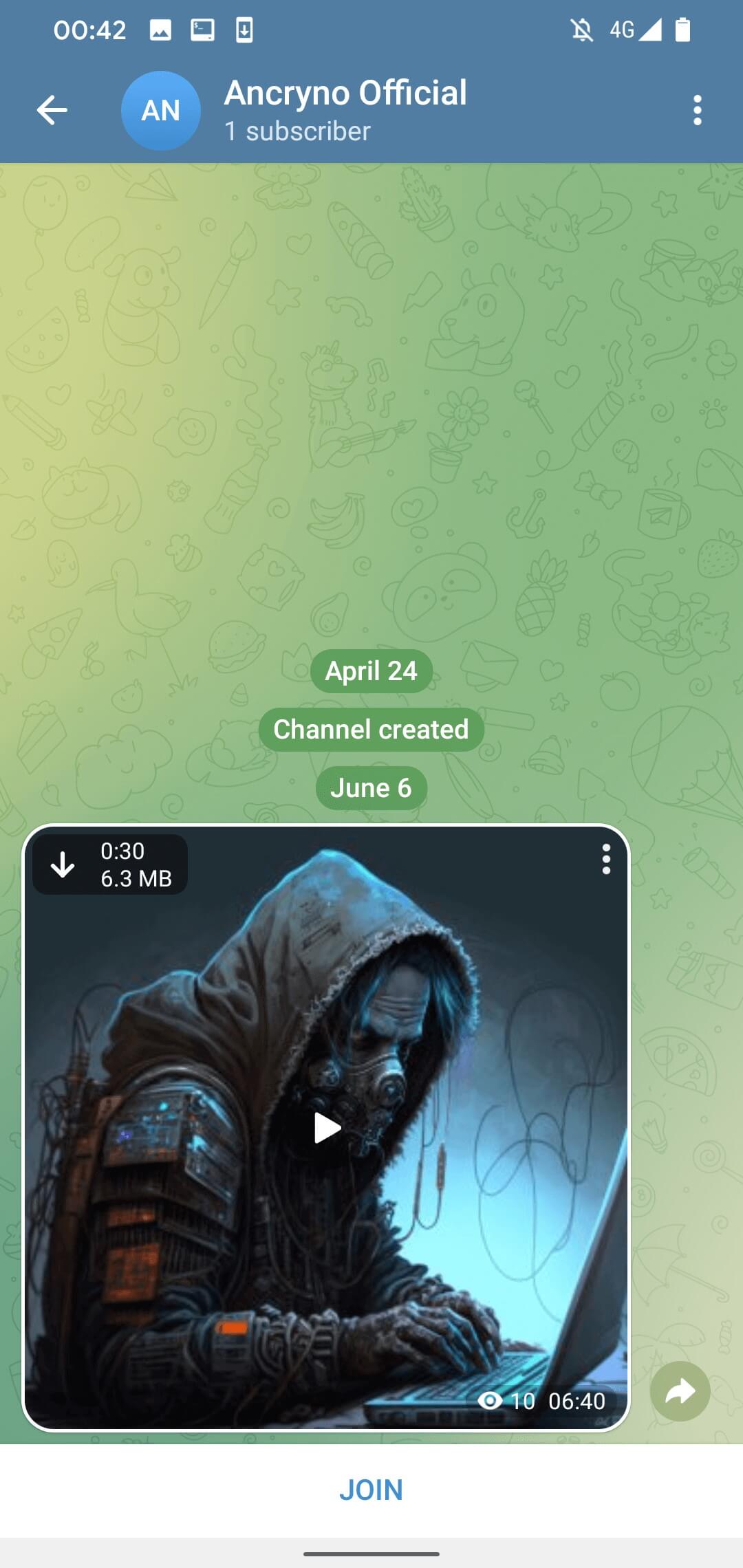
By default, media files obtained via Telegram are configured for automatic download. Consequently, users with this feature enabled automatically download the malicious payload once they open the conversation where it was disseminated. This setting can be manually disabled – in such a scenario, the payload remains downloadable by tapping the download icon in the upper left corner of the apparent video, as exhibited in Figure 3.
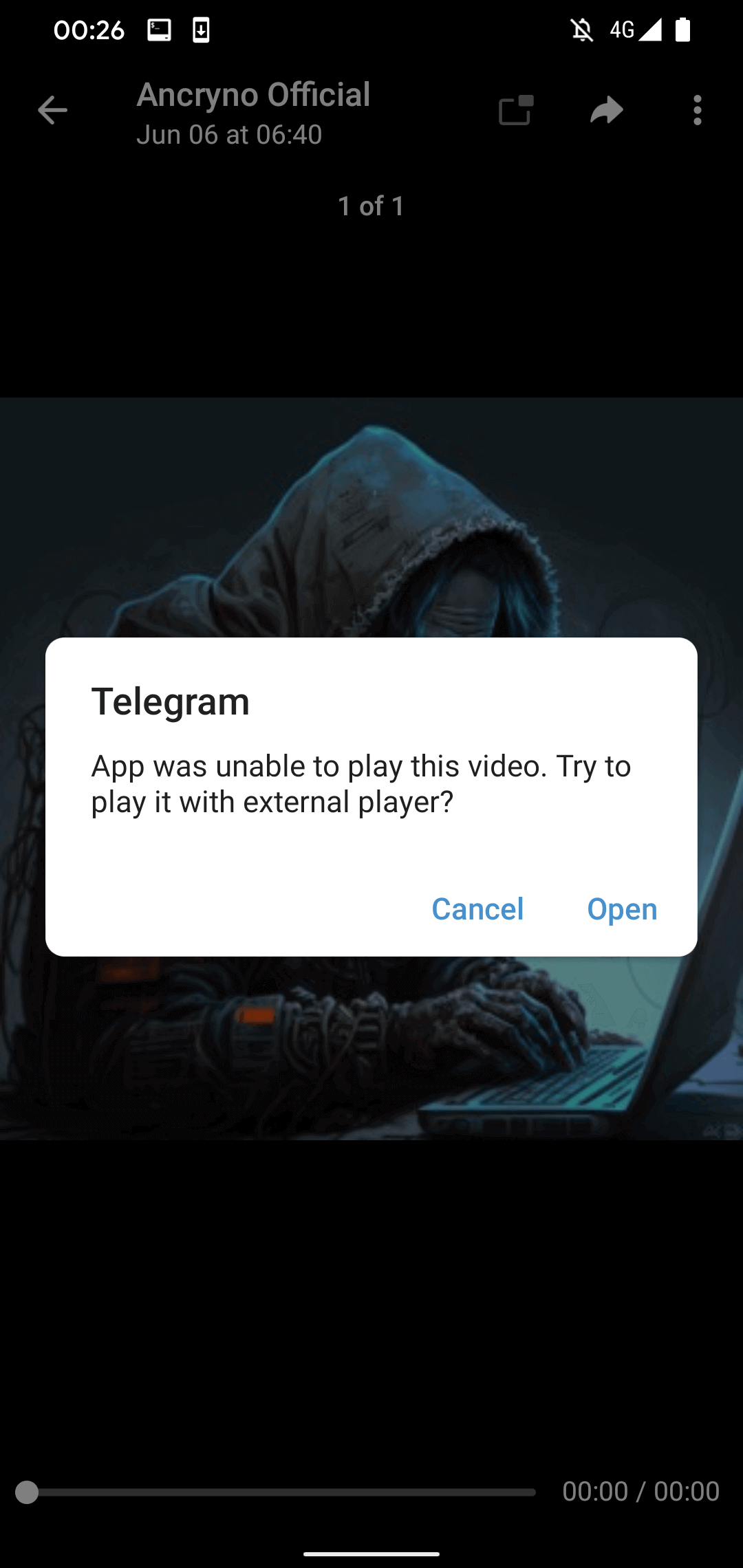
If a user endeavors to play the “video”, Telegram issues a notification expressing its inability to play it and recommends employing an external player (refer to Figure 4). This notice, sourced from the legitimate Telegram for Android application’s code, is original and not constructed or prompted by the malicious payload.
If the user taps the Open tab in the displayed message, they will be urged to install a malicious application embellished as the aforementioned external player. As demonstrated in Figure 5, before installing, Telegram prompts the user to authorize the installation of unfamiliar applications.
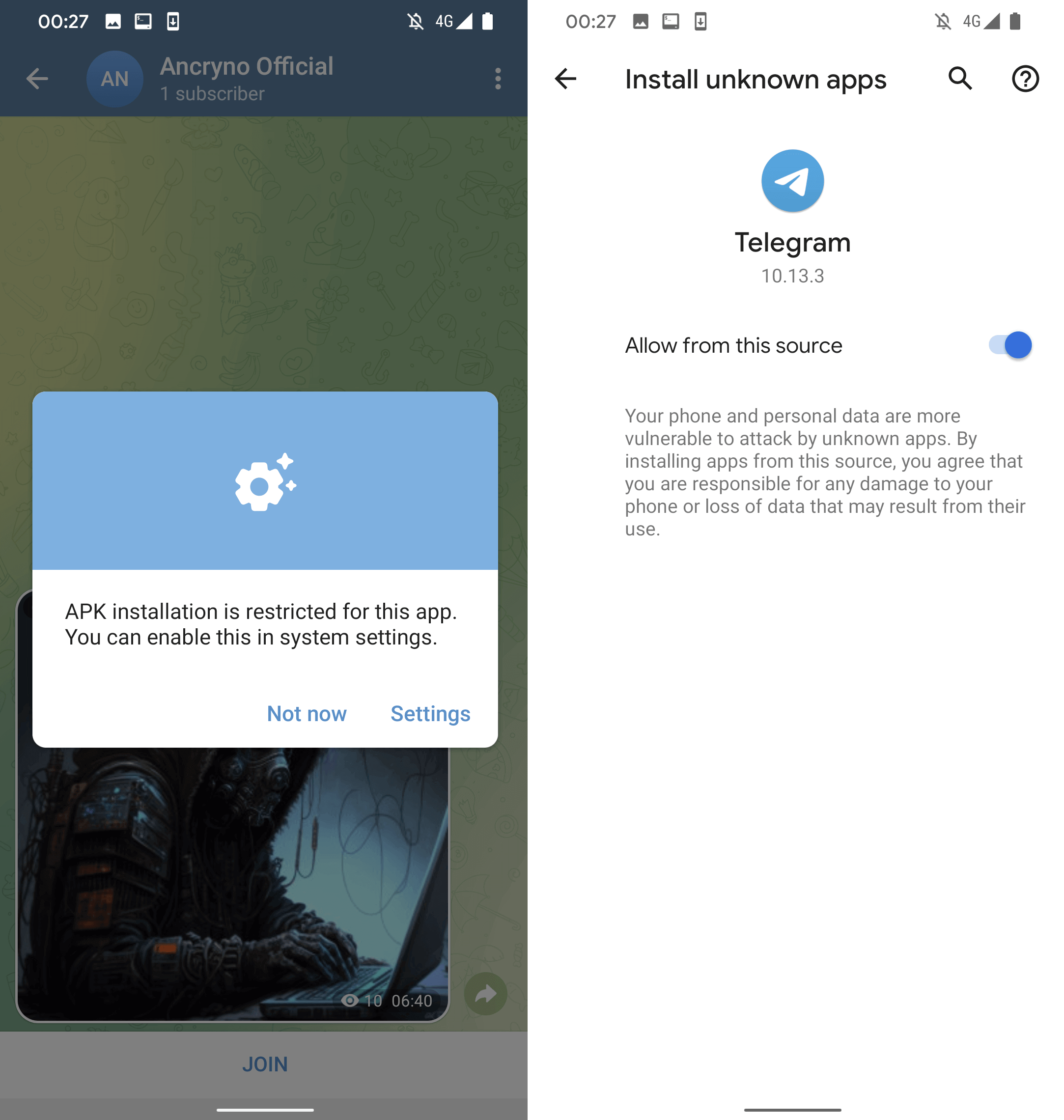
At this juncture, the malicious app has already been downloaded, masquerading as the apparent video file but labeled with the .apk extension. Interestingly, it’s the loophole’s nature that impels the distributed file to resemble a video – the actual malicious app wasn’t modified to pose as a multimedia file, suggesting exploitation in the upload procedure. The impetus to install the malicious app is discernible in Figure 6.
Regrettably, replicating the loophole proved unattainable; nevertheless, we scrutinized and authenticated the specimen relayed by the vendor.
Telegram Web and Desktop
Despite the payload being crafted exclusively for targeting Telegram for Android, we proceeded to evaluate its behavior on alternative Telegram clients. Trials were conducted on the Telegram Web client and Telegram Desktop client for Windows – as anticipated, the loophole did not function on either platform.
In the context of Telegram Web, following an attempt to play the “video”, an error message was displayed advising to endeavor opening the video using the desktop application instead (refer to Figure 7). Manual downloading of the attached file unveiled its nomenclature and extension to be Teating.mp4. Though the file technically comprised an Android executable binary (APK), Telegram’s interpretation as an MP4 file thwarted the operation of the loophole; for a successful exploit, the attachment would necessitate the .apk extension.
A comparable scenario unfolded with the Telegram Desktop client for Windows: the downloaded file bore the name Teating.apk.mp4, signifying another APK binary file masquerading with an .mp4 extension. This scenario implies that even with a calculated effort to craft a
A Windows executable could be used instead of the Android APK, and it would still be recognized as a multimedia file, making the exploit ineffective.

Threat perpetrator
Although scant information is available about the threat actor, we discovered an additional dubious service they offer based on the Telegram handle shared in their forum post. Apart from the exploit, they have been promoting an Android cryptor-as-a-service on the same underground forum. They claim it has been completely undetectable (FUD) since January 11th, 2024. The forum post is depicted in Figure 8.
Report on Vulnerabilities
Upon identifying the EvilVideo vulnerability on June 26th, 2024, we adhered to our coordinated disclosure policy, and notified Telegram about it, receiving no initial response. We reported the vulnerability again on July 4th, and this time, Telegram responded on the same day to confirm their team’s investigation into EvilVideo. They rectified the issue by releasing version 10.14.5 on July 11th, and informed us via email.
The vulnerability impacted all versions of Telegram for Android up to 10.14.4 but has been patched in version 10.14.5. As verified, the chat preview now correctly indicates that the shared file is an application (Figure 9) rather than a video.

Outcome
We unearthed a zero-day exploit for Telegram on Android being sold on an underground forum. This exploit enables the transmission of malicious payloads disguised as multimedia files through Telegram chat. If a user attempts to play the seemingly innocent video, they are prompted to install an external application, which in reality installs the malicious payload. Fortunately, the vulnerability was resolved on July 11th, 2024, following our report to Telegram.
For any queries regarding our articles on WeLiveSecurity, please reach out to us at threatintel@eset.comESET Research offers exclusive APT intelligence reports and data feeds. For information about this service, visit the ESET Threat Intelligence page.
Indicators of Compromise (IoCs)
A detailed list of Indicators of Compromise (IoCs) and samples are available in our GitHub repository.
Documents
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK methods
This table was constructed using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
Android malware can exploit the EvilVideo vulnerability to gain initial access to devices. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability deceives victims into installing a malicious application disguised as a multimedia file. |









