The Condition of Ransomware in State and Local Government 2024

Exploring the recent annual examination by Sophos on the practical ransomware encounters of state and local government entities delves into the complete victim journey, covering attack frequency, primary cause, operational implications, and business consequences.
This year’s analysis unveils new domains of investigation within this industry, including a comparison of ransom requirements versus ransom transactions and the frequency at which state and local government organizations are aided by law enforcement agencies in resolving the attack.
Access the report to acquire the comprehensive discoveries.
Decrease in Attack Frequencies, Yet Increased Recovery Costs
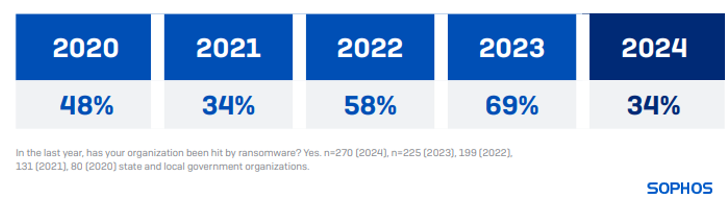
The attack incidents in state and local government bodies have witnessed a decline in 2024. Ransomware impacted 34% of state and local government entities this year, marking a 51% drop in comparison to the 2023 rate of 69%.
Nearly all (99%) of the state and local government entities struck by ransomware in the last year disclosed that cybercriminals tried to infiltrate their backups during the attack. Out of these attempts, slightly over half (51%) succeeded – representing one of the lowest backup breach rates across sectors.
In 2024, 98% of ransomware assaults on state and local government entities led to data encryption, a significant escalation from the 76% encryption rate noted in 2023. This stands as the highest data encryption rate among all sectors reviewed in 2024.
The average expense for state and local government entities to recuperate from a ransomware assault amounted to $2.83 million in 2024, doubling the $1.21 million recorded in 2023.
Devices Affected in a Ransomware Attack
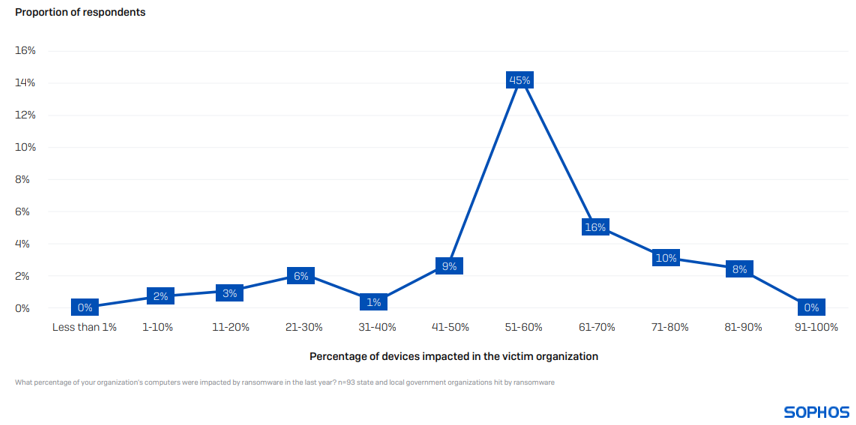
On average, 56% of the computers within state and local government organizations bore the impact of a ransomware incident, surpassing the cross-sector average of 49%. Instances where the entire environment was encrypted are exceedingly rare, with only 8% of organizations reporting that 81% or more of their devices suffered.
The Inclination to Fulfill Ransom Demands has Risen
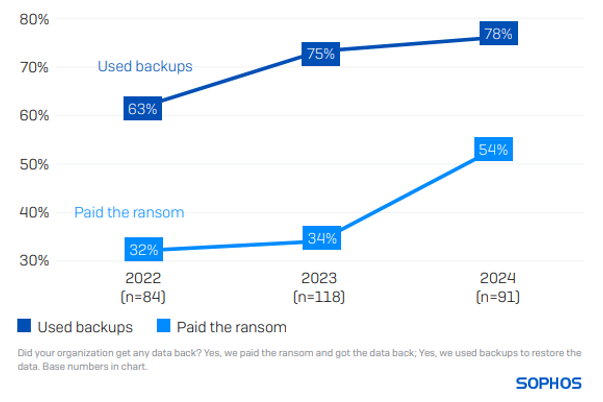
78% of state and local government entities recovered encrypted data by utilizing backups, marking the second highest backup utilization rate reported (on par with higher education). 54% opted to pay the ransom for data retrieval. In contrast, at a global level, 68% resorted to backups, and 56% paid the ransom.
An overview of the behavior observed over three years among state and local government entities reveals a consistent growth in both the usage of backups and the sector’s willingness to meet ransom demands.
An outstanding alteration over the prior year has been the surge in victims resorting to multiple strategies to recover encrypted data (e.g., paying the ransom and utilizing backups). In this year’s examination, 44% of state and local government entities encountering data encryption reported employing more than one approach, quadrupling the rate recorded in 2023 (11%).
Infrequently Meeting the Initial Ransom Sum Requested
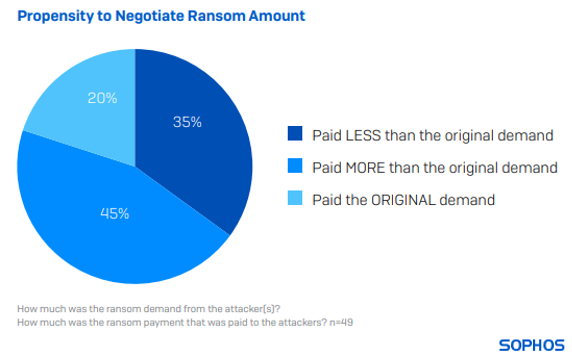
49 respondents from state and local government bodies who paid the ransom disclosed the actual amount transferred, disclosing an average (median) payment of $2.2 million in 2024.
Merely 20% conceded to the initial ransom request. 35% paid less than the original ask, while 45% paid beyond the initial demand. On average, among all respondents from state and local government entities, organizations disbursed 104% of the initial ransom stated by the perpetrators.
Access the comprehensive report for deeper insights into ransom payments and various other domains.
About the survey
This report stems from an independent, impartial survey initiated by Sophos involving 5,000 IT/cybersecurity captains across 14 countries in the Americas, EMEA, and Asia Pacific, including 270 from the state and local government segment. All participants correspond to organizations with staff strength ranging from 100 to 5,000 employees. The survey, carried out by research expert Vanson Bourne between January and February 2024, sought responses based on experiences during the preceding year.







