This year marks the fifth year of the celebrated fifth anniversary of the Sophos Active Adversary Report. A simple query led to the inception of this report: What transpires post invaders breaching a corporation? Understanding the adversary’s strategies aids defenders in combatting a live assault efficiently. (The origins of our venture were as “The Active Adversary Playbook.”) During the same time frame, deliberations were ongoing on how to develop a testing setting to address that post-invasion quandary, Sophos was readying to introduce an incident response (IR) service. This led to the birth of a collaborative project across teams.
 Over the past five years, our data presentations have evolved – from purely IR service data initially to eventually encompassing data from IR’s affiliated team assisting current MDR clients — combined with analyses of our interpretations. While striving to refine our procedures for acquiring and scrutinizing the data, this report focuses on specific observations and analyses. To mark this five-year milestone, we are granting global access to our 2024 dataset in the hopes of stimulating broader dialogues. Additional details on this initiative and the link to the Active Adversary repository on GitHub are available towards the conclusion of this report.
Over the past five years, our data presentations have evolved – from purely IR service data initially to eventually encompassing data from IR’s affiliated team assisting current MDR clients — combined with analyses of our interpretations. While striving to refine our procedures for acquiring and scrutinizing the data, this report focuses on specific observations and analyses. To mark this five-year milestone, we are granting global access to our 2024 dataset in the hopes of stimulating broader dialogues. Additional details on this initiative and the link to the Active Adversary repository on GitHub are available towards the conclusion of this report.
Principal Insights
- The disparities in findings between MDR and IR underscore the quantifiable importance of active surveillance
- The use of compromised credentials persists as the primary entry point; Multi-Factor Authentication (MFA) is imperative
- Another reduction in dwell time!
- Instances of attackers leveraging living-off-the-land binaries (LOLBins) have skyrocketed
- Remote ransomware presents a distinctive challenge / opportunity for systematically overseen systems
- Attack outcomes offer insights potentially useful for detections
Data Origins
Similar to our prior Active Adversary Report, the data in this edition originates from specific cases managed in 2024 by two Sophos units: a) the Sophos Incident Response (IR) division, and b) the response team handling critical situations among our Managed Detection and Response (MDR) clientele. These entities are predominantly referred to as IR and MDR, respectively, in this report. The study compares outcomes from the 413 chosen cases with data from earlier Sophos X-Ops assignments dating back to the inception of our IR service in 2020.
Of the dataset scrutinized for this report, 84% stemmed from organizations with under 1000 personnel, a decrease from the 88% figure in the previous report; the change predominantly arose (though not exclusively) due to the inclusion of MDR cases in the dataset. Over half (53%) of the organizations necessitating our support employ 250 staff or less.
And what are the industries these organizations represent? As has been the trend in our Active Adversary Reports since their inception, the manufacturing sector was the most frequent requester of Sophos X-Ops response services, although the proportion of customers from Manufacturing diminished from 25% in 2023 to 16% in 2024. Education (10%), Construction (8%), Information Technology (7%), and Healthcare (6%) rounded off the top five sectors. In total, the dataset encapsulates 32 distinct industry sectors.
Additional details on the data and methodology employed to select cases for this report can be found in the Appendix. No SecureWorks incident response data is included in this report.
The Headliner: MDR vs IR
 During the consolidation and standardization of the IR and MDR datasets, the Active Adversary unit postulated that organizations with adept active monitoring and logging mechanisms in place — specifically the MDR instances — would likely exhibit superior security outcomes. Although this might seem intuitive, the scale of some variances took us by surprise, and it is these distinctions that we will showcase in this report.
During the consolidation and standardization of the IR and MDR datasets, the Active Adversary unit postulated that organizations with adept active monitoring and logging mechanisms in place — specifically the MDR instances — would likely exhibit superior security outcomes. Although this might seem intuitive, the scale of some variances took us by surprise, and it is these distinctions that we will showcase in this report.
United Yet Unique: Ransomware and Dwell Time
In the previous reporting cycle, we detected, though did not report on, marked differences in the prevalent attack types for MDR clients versus IR clients, setting the groundwork and focus for this report. Throughout past reports, ransomware has consistently dominated the charts, as anticipated from IR-based data. Given the severe repercussions of a ransomware attack, numerous organizations lack the resources required for a complete remediation, particularly smaller entities.
Ransomware’s prominence in IR-only data over the last four years fluctuated between 68% and 81% of cases. In 2024, it dipped to 40%, yielding the top position to network breaches at 47%. When segregated by data source, the distribution in IR cases closely mirrors all prior data. Ransomware (65%) reigns supreme, followed by network breaches (27%). Conversely, the MDR data portrays a different narrative, with network breaches (56%) outstripping ransomware cases (29%) nearly twofold.
Figure 1: The transition in findings regarding attack types in our dataset is notable – in 2024, network breaches surpassed ransomware as the most common observed attack type. However, at the chart’s base lies another significant narrative – irrespective of the dataset or year, no single attack type crosses the 10 percent threshold of total cases; whether it’s ransomware or network breaches dominating a specific year, all other types remain secondary
Data supporting our hypothesis also revolves around dwell time. Prior years witnessed a decrease in dwell time, but recent reports show stabilization. (We performed an in-depth analysis of dwell time in our 1H 2024 report.) We considered dwell time to be a resolved issue — until we encountered this year’s statistics.
Let’s not bury the lede: The median dwell time for all cases in 2024 was a swift two days. An established pattern emerges in Incident Response (IR) cases: The overall median dwell time is 7 days, with ransomware incidents at 4 days and non-ransomware cases at 11.5 days. In contrast, Managed Detection and Response (MDR) dwell times were consistently lower across the spectrum, with ransomware cases at 3 days and non-ransomware incidents at 1 day, showcasing an inversion.
This phenomenon can be attributed to certain processes (e.g., data exfiltration) that have inherent constraints limiting speed due to human involvement, data transfer rates, or set timeframes. This isn’t to imply that attacks cannot be expedited, as they certainly can, but the data demonstrates that historically, ransomware incidents typically necessitated longer durations compared to other attack types. Therefore, it’s unsurprising that dwell times for ransomware cases handled by each service were almost equal.
In contrast, non-ransomware cases encounter fewer impediments. Here, the data underscores disparities between the services. For example, in IR scenarios, an intruder may remain concealed within the victim’s network for extended periods until an event triggers noticeable activity. In cases where attackers leverage valid credentials to quietly extract data through legitimate channels, detection may only occur upon direct interaction with the victim, if at all. (It’s worth noting that the ransomware sector attracts a considerable number of less sophisticated attackers, typically less adept at maintaining stealth. Ransomware operations are inherently high-volume, accepting a notable loss on numerous systems as part of their operational model.)
MDR responses to non-ransomware incidents are expedited due to a combined approach of detection mechanisms and persistent monitoring. Suspicious activities are scrutinized promptly, and those warranting further examination are escalated. In summary, swift detection often thwarts ransomware attempts, leading to a higher ratio of breaches being reported — resulting in improved outcomes for victims.
Collaboration: Underlying Cause
Conversely, disparities between IR and MDR cases when pinpointing underlying causes were minimal. Once more, compromised credentials (41%) and vulnerabilities exploitation (22%) took the lead, with brute force attacks (21%) securing the third spot, as depicted in Figure 2.
Figure 2: In 2024, differences in root causes were apparent in MDR and IR cases, although compromised credentials remained the prominent issue in both datasets
Brute force attacks, historically relegated to a lesser role in IR data, observed a substantial surge in MDR data, propelling it up the rankings for 2024. This shift may be due to variations in available root-cause data. In IR investigations, the absence of logs often impedes the investigative team’s ability to identify attack root causes. Conversely, MDR investigations benefit from consistent data sources, enabling more precise analyses.
An analysis of year-over-year data, as depicted in Figure 3, illustrates the change in percentages from previous years to 2024.
Figure 3: In 2024, compromised credentials receded from previous elevated levels as the predominant root cause of issues, though it remains a concerning matter. (Data from 2020 cases is excluded in this chart due to a change in our data categorization for this segment)
Logs were absent in 47% of cases in 2024 – 66% in IR and 39% in MDR scenarios. The primary cause of missing logs in all cases was their unavailability (20%) to analysts during investigations, followed by 17% cleared by attackers, and 7% absent due to insufficient retention periods.
(A common tool used to erase logs is the Microsoft binary wevtutil.exe [the Windows Event Utility]. This utility generates Windows event log IDs 1102 [for security logs] and 104 [for system logs]. Organizations where logs were cleared were often unaware of the activity.)
should consider setting up their security tools and conducting threat hunts to identify this behavior.
The increase in brute force as a fundamental cause complements well with early entry (TA0001) data. External Remote Services (T1133) emerged as the preferred initial entry point, detected in 71% of instances. As previously mentioned, this is often linked with Valid Accounts (T1078); this year, the combination appeared in 78% of cases. The exploitation of a Public-Facing Application (T1190) followed closely in causing initial access. The primary vulnerability exploited for initial access was CVE-2023-4966 (Citrix Bleed; 5%). Other contributing factors included exposed Remote Desktop infrastructure (18%), vulnerable VPNs (12%), and exposed internal services (11%).
Are you familiar with TTP?
A previous report showcased few distinctions in TTPs between attacks with short (5 days or less) versus long (over 5 days) dwell times. These insights were limited to IR cases. Reviewing this year’s report’s TTPs, we observe a similar trend when comparing IR and MDR cases.
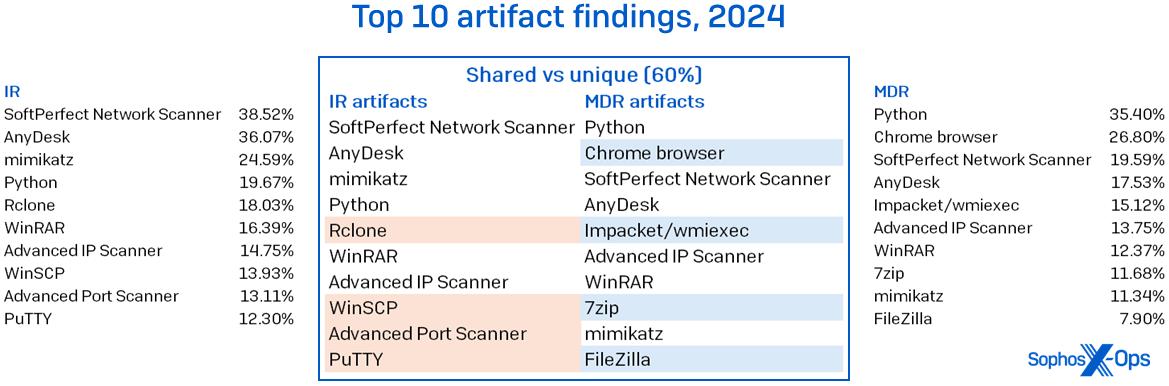
MDR cases exhibited slightly more evidences (+24%), however, the MDR dataset was approximately 240% larger than that from IR. There was a 60% resemblance in the top 10 tools frequently utilized by hackers. Among the commonly misused legitimate tools were well-known names such as SoftPerfect Network Scanner, AnyDesk, WinRAR, and Advanced IP Scanner, as depicted in Figure 4.
Figure 4: The tools commonly exploited in IR and MDR cases show minimal differences at the top, with notable variations and omissions
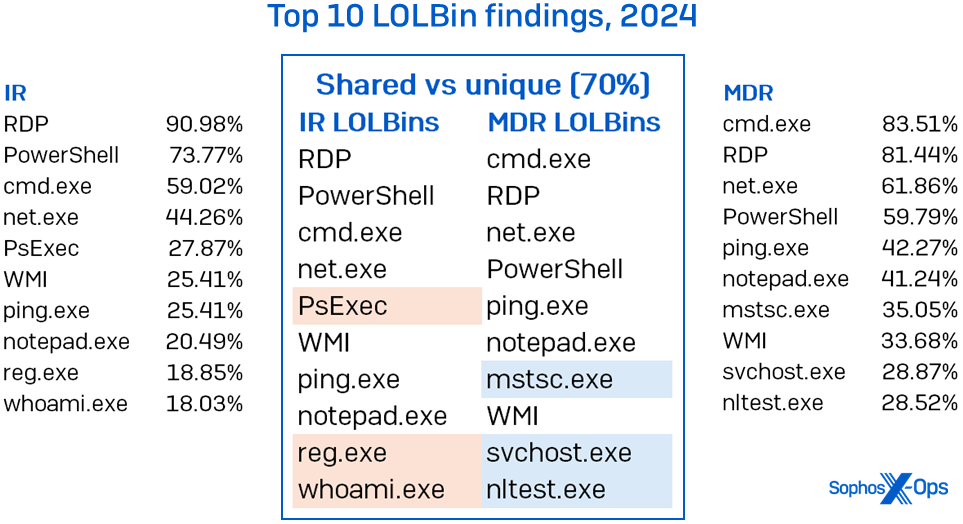
Microsoft binaries showcased a stronger connection between the datasets. The top 10 misused LOLBins exhibited a 70% similarity, as shown in Figure 5. There was a slight shift in the leading position, with cmd.exe surpassing RDP as the most abused LOLBin in the MDR instances. This outcome is not unexpected as many MDR scenarios have a restricted impact zone: Upon permission, analysts promptly quarantine affected hosts, thereby restricting attackers’ lateral movement capabilities.
Figure 5: The abuse of LOLBins is consistent regardless of the team investigating; notably, the variance between MDR and IR in terms of RDP abuse is present but not significant
The final comparison focuses on the “other” category, encompassing techniques and traces not falling under the other two classifications. The top 10 entries displayed an 80% overlap in IR and MDR cases, involving activities such as creating accounts, deleting files, installing services, running malicious scripts, and modifying the registry, as depicted in Figure 6. Certain activities like SAM (Security Account Manager) dumping were more prevalent in one team’s dataset.
Figure 6: As demonstrated, in more than half of instances, attackers employed familiar and comparable TTPs. (Note: the percentages may total over 100% as many cases have multiple findings within this category)
The internal assailant revisited
As customary at Active Adversary HQ, we like to revisit some of our findings from previous reports, particularly those covering periods shorter than 12 months. The following section delves into the key insights from our previous report (covering the first half of 2024) and compares them to the complete year’s dataset.
LOLBins Examination
The misuse of Microsoft binaries persisted throughout the latter half of 2024, and the ratio of distinct LOLBins compared to previous years continued to climb. In the first half of 2024, we observed a 51% surge in the count of unique LOLBins, ending the year at 126% above the 2023 figures. There was a 17% increase in cases during 2H 2024 and a 24% rise in usage of unique binaries. There were no notable discrepancies in the individual binaries utilized throughout the year. Across the first and second halves of the year, there was a 95% overlap among the 20 most commonly abused tools in IR and MDR cases. Tools facilitating enumeration – alongside their legitimate and malicious applications – continued to dominate in both datasets, accounting for 50% of the 20 most-abused binaries.
Notepad.exe emerged as a fresh addition to the top 10 this year. This tool was predominantly employed for browsing network files, including those containing passwords stored in plaintext (5%). Tools such as Notepad offer intriguing detection possibilities. We argue that the majority of users do not opt for Notepad over other Office applications. Nonetheless, there’s a significant distinction between clicking on the Notepad icon, searching for Notepad in Windows, or executing notepad.exe via the command line. The ability to differentiate between these
Informing the use intention can be achieved through three distinct launch techniques.
Similar sentiments apply to utilities such as PowerShell. The suggestion is not to cease its utilization within IT teams, but rather to employ quick heuristics through detection engineering. If a PowerShell script was heavily obfuscated and made outbound connections to the internet, then it warrants further scrutiny.
The primary challenge with LOLBins is their tendency to create significant background noise. The difficulty for IT teams lies in discerning the presence of any meaningful signals amidst this noise.
RDP
The abuse of Microsoft’s RDP tool remains prevalent. In 2024, attackers utilized RDP in 84% of cases, with 67% employed solely for internal lateral navigation and 3% for external purposes. When considering the instances where RDP was used both internally and externally, the figures shift to 83% and 19%, respectively.
Despite the ongoing abuse of RDP and the calls for its complete cessation, we acknowledge its persistent presence in networks. This situation presents an opportunity to explore ways of restricting its usage and enhancing detection against potential misuse.
It is ideal to confine RDP usage through network control points and user authentication. Where feasible, the incorporation of MFA into the authentication process and adhering to the principle of least privilege are recommended. By limiting its usage and establishing a baseline of normal activity, abnormal behaviors become easier to detect.
Various methods exist for detecting authentication events, primarily by monitoring Windows logging event IDs 4624 and 4625. The former signifies a successful authentication, while the latter denotes a failed attempt. Successful login events can help identify attackers wielding legitimate credentials beyond normal patterns, while repeated failed attempts serve as an early warning for potential brute force attacks on accounts.
If your organization follows a standard naming convention for devices, deviations from this standard can serve as an additional red flag. Any successful authentication not conforming to the standard warrants investigation. For entities lacking a naming standard, this presents an opportunity to implement one and create passive defenses against attackers. Moreover, instances like the appearance of a hostname like “kali” on your network, as seen in 6% of cases, should be thoroughly investigated.
Furthermore, exploiting the time-zone bias in RDP logging can offer valuable insights. The time offset from UTC of remote clients can highlight suspicious activity. For instance, if most users are in UTC-6 but a client logs in with a time-zone bias of +3, diligent investigation is necessary. Such anomalies can reveal unusual scenarios, like innocuous machines connected to an unexpected Russian-named printer.
The essence of these detection opportunities lies in consolidating independent yet potentially weak or noisy signals to create a robust and dependable defense mechanism, known colloquially as “defense in depth.”
For those seeking more information on RDP exploitation detection, detailed resources can be found in our RDP series.
Attribution
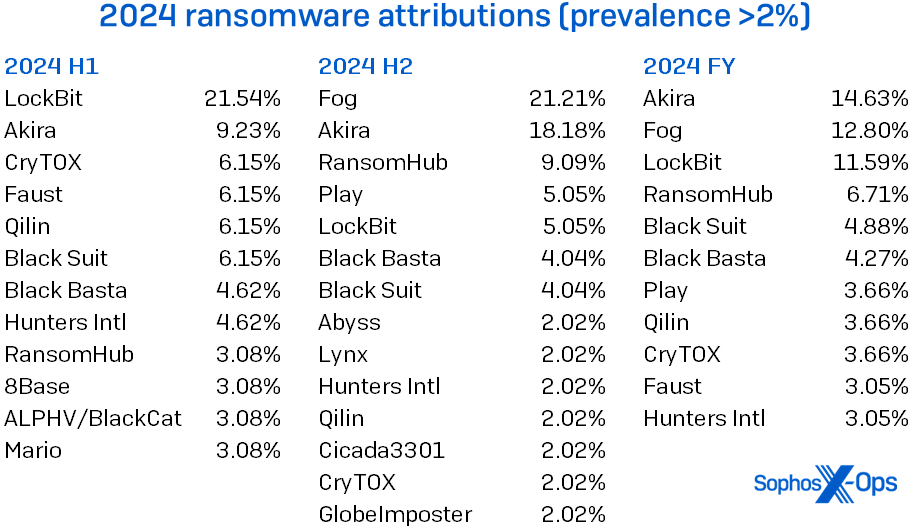
In the previous report, the prediction was made that there would be no single dominant ransomware adversary in 2024. Following a law enforcement intervention that significantly impacted LockBit, the prominent threat actor from 2023, the stage was set for the emergence of a new formidable adversary. As depicted in Figure 7, this prediction materialized with Akira ascending to the top spot, narrowly surpassing the competition. LockBit’s early dominance in the year ensured it still ranked third despite the disruption. In the latter part of the year, Fog emerged as a strong contender, outpacing Akira for the leading position. While a few trailing instances of LockBit infections were observed in the second half, they gradually diminished by the year’s end. The landscape may evolve in 2025 due to anticipated shifts in law enforcement initiatives and other factors; intriguingly, LockBit remains resilient, hinting at a potential resurgence. Thus, we await future developments with keen interest.
Figure 7: LockBit’s decline in prominence observed in the latter half of 2024, coinciding with Fog’s emergence
Assigning specific troubles to a particular adversary can be reassuring. However, security practitioners often find themselves battling not only external threats but also grappling with internal challenges arising from business processes and change management. A case study presented in this report depicts the struggles faced by a seemingly “unlucky” MDR client.
Case study: Two in conflict
While emphasizing fundamental security principles such as securing RDP access points, implementing MFA, and promptly patching vulnerable systems remains essential, navigating through organizational changes can present unforeseen hurdles. Security professionals are not just combatting external threats but are also embroiled in internal conflicts stemming from business operations and change control. This internal tug-of-war proved detrimental for one MDR client. Following a network breach initiated through an unpatched VPN vulnerability, the client faced a challenging timeline of two months to resolve the VPN appliance patching issue. With a ransomware threat looming, the clash between security imperatives and the broader business agenda culminated in a disastrous outcome.
A Balancing Act
The Sophos MDR team promptly responded to the critical incident involving the aforementioned client, pinpointing the unpatched VPN appliance as the entry point for the breach. Specifically, a FortiGate firewall running on firmware version 5.6.11, released in July 2010, and reaching end-of-life in October 2021, posed a significant security risk. Additionally, the misconfiguration in VPN user-access controls further compounded the vulnerability landscape.
Upon gaining initial access, the threat actor swiftly advanced to the domain controller, utilizing AV evasion tools, conducting reconnaissance, and establishing persistence on numerous devices throughout the network. MDR’s response team effectively mitigated the attacker’s actions, restoring the situation to stability.
MDR’s recommendation to the client included, at minimum, an urgent patching of the antiquated VPN firmware to fortify their security posture.
and deactivate the Secure VPN in the interim. Nonetheless, the client’s operational procedures were not accommodating; completely deactivating the VPN would result in an unacceptable operational impact, and the updates could not be implemented for a duration of two months (!). The misconfiguration, as per the client’s estimation, was anticipated to require one week to rectify.
Already engaged in the battle
It’s regrettable truth in the incident response realm that we cannot enforce; we can merely suggest – and at times, we can only observe history repeating itself. And indeed, it was repeating: The same client had previously encountered a comparable violation, linked to the same susceptible VPN, 14 months earlier. Back then, MFA had not yet been enabled for VPN logins; a brute force attack had succeeded, allowing the attacker to bypass protections and extract credentials. In the process, the attacker succeeded in compromising a vital service account, rendering the client unable to execute a crucial credential reset due to – once more – operational requirements. (Recall that service account; we’re about to cross paths with it once more.)
The time gap between the initial breach and the second was, as aforementioned, 14 months. However, the interval between the second and the third was considerably shorter.
So what’s an additional occurrence?
The second occurrence concluded. The VPN and that service account – one thing outdated for nearly four years, one thing acknowledged as compromised for over a year – lingered in operational limbo, alongside the VPN misconfiguration. The cybersecurity professionals were patient. Conversely, the attacker was not. Merely nine days following the resolution of the second violation, CryTOX made an entrance. Exploiting the compromised service account and maximizing the unpatched and (still) misconfigured VPN, the ransomware spread uninhibited through the network, progressing sideways, terminating endpoint protection processes, and finally encrypting the entire infrastructure.
In this scenario, it could be asserted that ransomware emerged victorious in the struggle between security protocols and operational change processes. (On the positive side: Following the third incident, the VPN was ultimately deactivated, although impacted accounts were still reactivated without credential resets.) While not all entities experience such unfortunate events, in this instance, the delay in operational change approval proved to be a failed risk assessment gamble.
Creme de la creme
As we conclude our observations for 2024, let’s explore other statistics that caught our attention.
In addition to a surge in case numbers, this year’s data encompassed the most significant year-over-year increase in all observed TTPs. Compared to 2023, the usage of exploited tools rose by 80%, LOLBins increased by 126%, and the category labeled as “other” escalated by 28%. What’s intriguing about these figures is the extended tail for each classification – indicating the number of tools, LOLBins, or “other” that appeared ten times or less in the data set. When we tally all observations in every single case, these rare occurrences account for 35% of all tool utilization (689 observations out of 1945 total; 334 distinct items), 12% of LOLBins usage (508 observations out of 4357; 184 distinct items), and 12% of “other” category (476 observations out of 4036; 189 distinct items). A biologist might refer to these as vestigial tails; to us, they signify a lower priority in investigations compared to the dominant entities at the top of the TTP charts.
No opportunity to squander
When targeting specific goals, attackers do not idly waste their time. Our initial report on the race to compromise Active Directory in 2023 continued to show a decline, with the median now standing at 0.46 days. Essentially, once an attacker infiltrates the environment, it takes a mere 11 hours before they pivot towards the AD server. The majority (62%) of compromised servers operated on systems outside mainstream support.
Game sans boundaries
Another time-related metric we initially highlighted in 2023 was the timing of ransomware payload deployments by attackers. While new data has slightly altered the values, the findings remain compelling. In 2024, 83% of ransomware executables were deployed outside the target’s local business hours; the historical figure stands at 88%. Though it may seem that ransomware activities predominantly occur at night, there appears to be no evident preference for specific days of the week.
Utilitarian instruments for navigating existence
The composition and varieties of tools – whether benign or malicious – within this classification have remained relatively consistent over numerous years. Here are several highlights from this year’s data, alongside the aforementioned issues.
We have witnessed a significant decline in the utilization of Cobalt Strike for attacks. This tool held the top position in exploited tools from 2020-2022, slipping to second place in 2023. Moreover, this year witnessed a further decline, placing it thirteenth on our list, detected in merely 7.51% of cases. Due to its historical appeal among attackers, it still retains the top position in the all-time rankings, with involvement in 25% of attacks within the past five years. The reduction is likely attributable to enhanced prevention and detection capabilities. Cobalt Strike formerly thrived due to its efficacy. Now that its effectiveness has waned, so has its prevalence. While this is positive news, it implies the emergence of an alternative tool of choice.
One tool experiencing a tenfold rise in exploitation is Impacket. Impacket tools have been in circulation for at least a decade, capable of executing various actions like manipulating network protocols, extracting credentials, and conducting reconnaissance. Its usage steadily climbed in recent years, from 0.69% in 2021 to 21.43% in 2023; in 2024, attackers significantly escalated their utilization of Impacket, propelling it to the top spot. The most prevalent Impacket tool was wmiexec.py, featured in 35% of attacks. (In our data, whenever possible, we identify the precise Impacket subclass; if uncertain, it is labeled as Impacket without a subclass.)
An enduring tool witnessing a slight annual decrease is mimikatz. This credential-harvesting utility was consistently noted in approximately a quarter of attacks in prior years but dipped to 15% in 2024. While the cause of its decline remains inconclusive, it’s plausible that the increased adoption of Impacket tools played a role; specifically, the secretsdump.py script used for hash extraction from remote machines. This coincides with a surge in remote registry extraction year-over-year and a 50% reduction in LSASS extractions (often attributed to mimikatz in our data). Secretsdump.py featured in at least 6% of attacks and ranked as the second most utilized Impacket tool following wmiexec.py.
Among the top 15 abused tools, 47% are frequently employed for data exfiltration. These tools encompass renowned archiving software and file transfer utilities.
Additional discoveries
Since we commenced tracking the implementation of multifactor authentication (MFA) in compromised organizations, the situation has deteriorated. In 2022, we observed that 22% of victims had not configured MFA. This percentage nearly tripled to 63% in 2024. This discrepancy was consistent across both IR and MDR cases, with MFA absent in 66% of IR cases and 62% of MDR cases. This underscores a scenario where even the most adept detection and response framework can leave organizations susceptible to breaches.
Another troubling metric was the presence of unprotected systems within breached organizations. In 40% of the cases we investigated, such systems were discovered. When considering the instances where unprotected systems were detected, there were alsoExposed VPNs (12%), susceptible systems (11%), and outdated systems (5%) in certain ecosystems (the case study in this report, for example, presented all three), might make intruders feel like sly predators infiltrating a vulnerable sanctuary.
One might question the persistence of ransomware incidents in an MDR service. A primary factor lies in unprotected systems and their association with distant ransomware. The entirety of malevolent activities – entry, execution of malicious payloads, and encryption – unfolds on unmonitored machines, thus circumventing the organization’s security measures. The only telltale sign of compromise is the exchange of files among various systems. Our data signals a 141% surge year-over-year in calculated remote encryption strikes since 2022, as depicted in Figure 8. (We’ve previously delved into remote ransomware and combating it, like the discussion on our CryptoGuard technology; as the figures escalate, remote ransomware might be a focal point in an upcoming Active Adversary Report.)
Figure 8: Based on Sophos X-Ops data, the volume of remote ransomware incidents in 2024 was 141% compared to 2022; note the striking escalation in cases over the last 18 months of the data
The absence of file movement transparency across the network – and the absence of essential logs – also contributes to exfiltration statistics. In 2024, analysts confirmed exfiltration in 27% of instances. Incorporating indicators of data staging and potential exfiltration, this figure increases to 36%. Data was exfiltrated in 43% of ransomware incidents under scrutiny. Another 14% exhibited potential exfiltration or hints of data staging. Unlike the time-to-active directory, exfiltration discoveries typically occur towards the attack’s end. The median duration stood at 72.98 hours (3.04 days) from the attack’s start to exfiltration, but merely 2.7 hours (0.11 days) from exfiltration to attack detection in cases of ransomware, data exfiltration, and data extortion.
Noise Creation
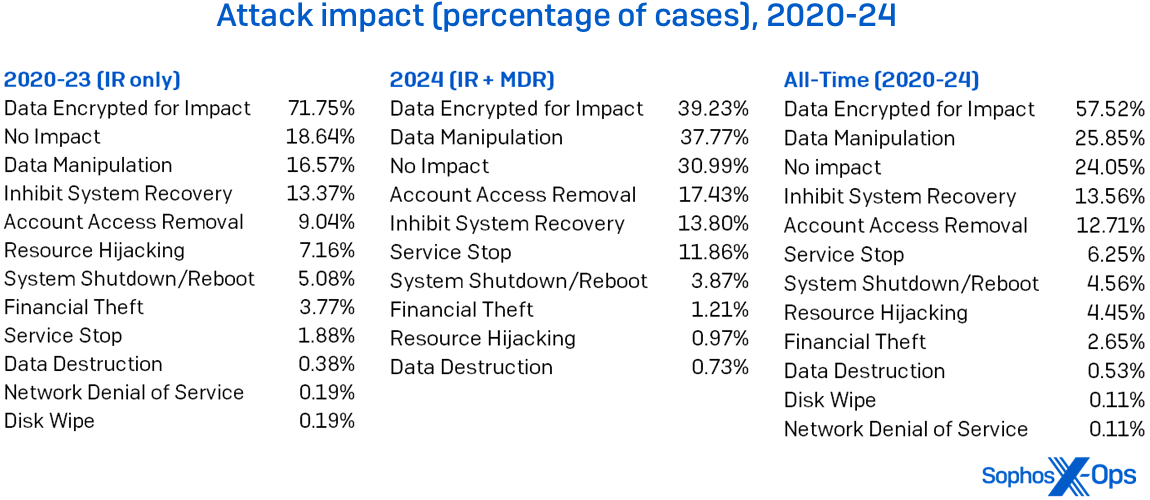
This report traditionally explores MITRE impacts (TA0040). Given the prevalence of ransomware in the data, it’s unsurprising that Data Encrypted for Impact (T1486) dominates the chart, persisting at the top every year, as illustrated in Figure 9. However, examining the remaining impacts reveals an opportunity for defenders: Many of the other impacts stem from detectable events.
Figure 9: MITRE’s Impact categories evolve over time, but Data Encrypted for Impact’s reign atop the Active Adversary charts remains unchallenged across our five-year history, including both IR and MDR cases this year. (Note that percentages surpass 100%, given multiple impacts in some cases)
For example, Inhibit System Recovery (T1490) is often deployed when threat actors erase volume shadow copies. Monitoring tools like vssadmin.exe, the shadow-copy management utility (exploited in 10% of cases), or the WMI command line (abused in 24%) facilitate the process. Detecting instances where vssadmin generates shadow copies, preceding potential exfiltration, is feasible. We also observed files being deleted in 26% of cases. In such scenarios, being vigilant for unusual utilization of del.exe may indicate adversary intervention. Detection mechanisms can be programmed to identify suspicious occurrences of this nature, capturing the sounds intruders make while endeavoring to unleash harm.
Final Thoughts
To all the professionals out there, your efforts are recognized. You are dedicated to your work and comprehend the operational side of things. You are also mindful of the constraints on what can be achieved. The encouraging news is that you need not passively hope for improvements, especially when there is assistance within reach.
Speaking to business and technology leaders, afford your teams an opportunity. We understand the constraints of finances and resources. This often results in burdening your IT personnel with excessive workload and responsibilities. While it may sound biased coming from a research unit linked to a security provider, we advocate that IT teams should concentrate on enabling the business, letting experts handle combating adversaries. The data unmistakably demonstrates that when someone is attentive to the environment and can react promptly and decisively, outcomes drastically improve. The alternative is a repetition of past errors. The decision lies with you: Embrace progress, or stick with the status quo. We are confident that opting for advancement is the way forward.
Acknowledgements
The authors express gratitude to the Sophos IR and MDR teams, as well as Mark Loman, Chester Wisniewski, and Matt Wixey, for their valuable contributions to the AAR process.
Appendix: Demographics and Methodology
In this report, our focus was on 413 cases that could offer meaningful insights into the status of the adversary landscape throughout 2024. Protecting the confidential ties between Sophos and our clients remains our paramount concern, and the data presented here underwent rigorous scrutiny at various stages to ensure that no individual customer could be identified through the data – and that no single customer’s information skewed the overall dataset inappropriately. When uncertain about a particular case, we excluded that specific customer’s data from the dataset.
The illustration A1: We get around: It’s Sophos Incident Response and MDR working globally (map created with the help of 29travels.com)
The following 57 nations and other locations are included in the complete dataset:
| Angola | Hong Kong | Qatar |
| Argentina | India | Romania |
| Aruba | Indonesia | Saudi Arabia |
| Australia | Israel | Singapore |
| Austria | Italy | Slovenia |
| Bahamas | Jamaica | Somalia |
| Bahrain | Japan | South Africa |
| Belgium | Kenya | South Korea |
| Bolivia | Kuwait | Spain |
| Botswana | Malaysia | Sweden |
| Brazil | Mexico | Switzerland |
| Canada | Netherlands | Taiwan |
| Chile | New Zealand | Thailand |
| Colombia | Nigeria | Turkey |
| Egypt | Panama | Turks and Caicos Islands |
| Finland | Papua New Guinea | United Arab Emirates |
| France | Philippines | United Kingdom |
| Germany | Poland | United States of America |
| Honduras | Portugal | Vietnam |
Sectors
The subsequent 32 sectors are presented in the complete dataset:
| Advertising | Financial | News Media |
| Agriculture | Food | Non-profit |
| Architecture | Government | Pharmaceutical |
| Communication | Healthcare | Real estate |
| Construction | Hospitality | Retail |
| Education | Information Technology | Services |
| Electronics | Legal | Transportation |
| Energy | Logistics | Travel and tourism |
| Engineering | Manufacturing | Utilities |
| Entertainment | Mining | Wholesale |
| Finance Services | MSP/Hosting |
Approach
The information in this analysis was gathered throughout separate inquiries conducted by Sophos’ X-Ops Incident Response and MDR groups. For the initial report of 2025, we collected case data on all inquiries carried out by the teams during 2024 and standardized it across 52 categories, evaluating each instance to ascertain that the data obtained was appropriate in terms of depth and coverage for composite analysis as defined by the focus of the intended report. We then proceeded to standardize the information between our MDR and IR reporting methodologies.
In instances where data was ambiguous or unavailable, the authors collaborated with specific IR and MDR case leaders to address any uncertainties. Cases that couldn’t be clarified adequately for the report’s purpose, or where inclusion could pose risks to exposure or potential harm to the relationship with Sophos clients, were excluded. Subsequently, we analyzed the timeline of each remaining case to gain more insight into aspects such as initial breach, time spent in the system, data extraction, and other pertinent details. A total of 413 cases were retained, forming the basis of this report. The data shared in the downloadable dataset has been further edited to safeguard customer confidentiality.