Tenant Isolation in Multi-Tenant Systems: Architecture, Identity, and Security
Tenant isolation is one of those concepts that sounds simple on paper and becomes painfully complex in real systems—especially once authentication, SSO, and identity enter the picture.
Tenant Isolation in Multi-Tenant Systems: Architecture, Identity, and Security
Tenant isolation is one of those concepts that sounds simple on paper and becomes painfully complex in real systems—especially once authentication, SSO, and identity enter the picture.
Most SaaS teams don’t start with tenant isolation as a hard requirement. They add it gradually as customers grow, enterprise deals appear, and security reviews begin. Unfortunately, identity systems have a much larger blast radius than most application features, and isolation mistakes here are far more costly.
This guide is a technical deep dive into tenant isolation strategies and infrastructure patterns, with a strong focus on authentication and identity systems, while remaining applicable to any multi-tenant architecture.
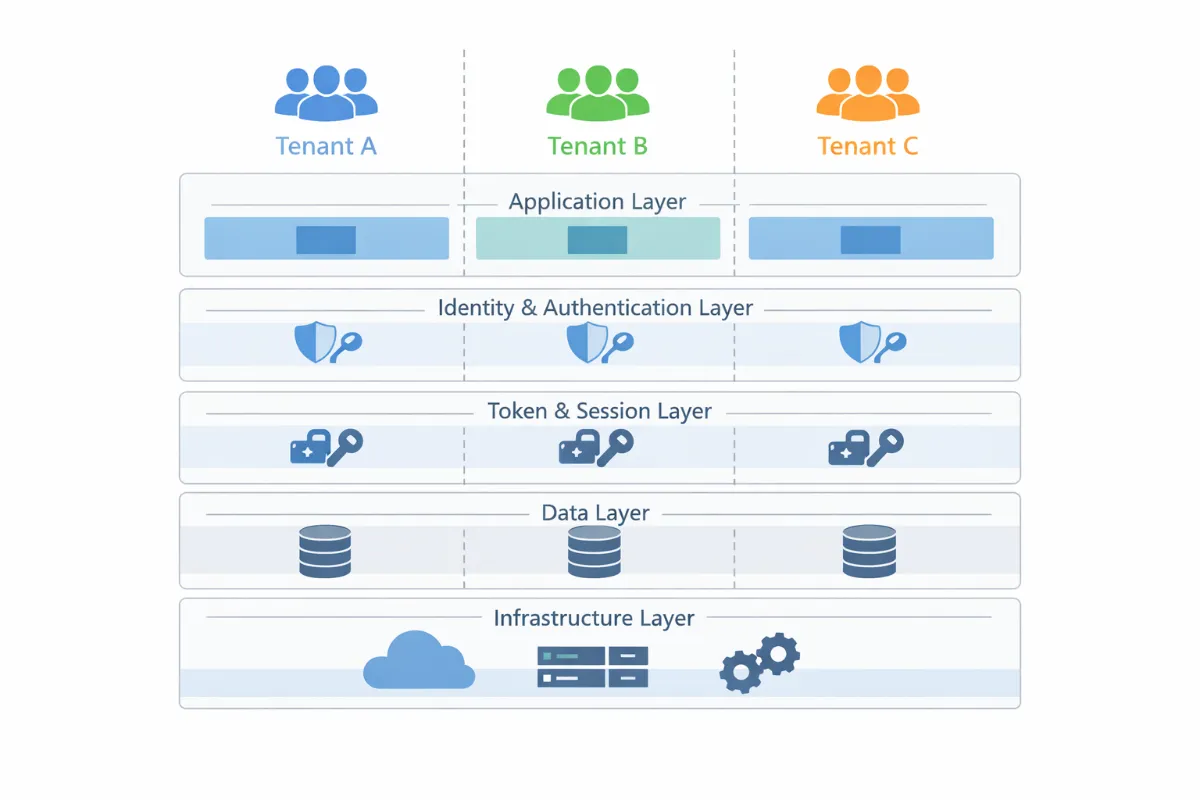
Tenant isolation is the practice of enforcing strict security boundaries between customers in a multi-tenant system, ensuring that data, authentication flows, tokens, and infrastructure belonging to one tenant cannot be accessed by another. In authentication and SSO systems, tenant isolation is especially critical because identity misrouting, shared tokens, or reused configurations can lead to cross-tenant access and security breaches. Effective tenant isolation requires consistent enforcement across application logic, identity providers, token issuance, data access, and infrastructure.
1. Why Tenant Isolation Becomes Critical the Moment You Add Authentication
Imagine this scenario:
You run a multi-tenant SaaS platform. Two companies use your product. Both authenticate via SSO. One small routing mistake sends a login request to the wrong tenant’s identity configuration.
Nothing crashes.No alert fires.But a user from Company A is now authenticated inside Company B’s tenant.
This is why tenant isolation failures in authentication systems are uniquely dangerous:
Authentication is the entry point to everything else
Tokens, sessions, and cookies grant broad access
A single mistake can bypass all downstream authorization
In application logic, isolation bugs might expose data.In authentication, isolation bugs expose trust.
2. What Tenant Isolation Actually Means (Beyond the One-Line Definition)
At a high level, tenant isolation means:
Ensuring that one customer (tenant) can never access another customer’s data, identity configuration, or resources—intentionally or accidentally.
But in real systems, isolation is not one thing. It is a set of enforced boundaries across multiple layers:
Request handling
Identity routing
Token issuance
Data access
Infrastructure and secrets
Operations and observability
Two users can share:
The same email username
The same role name
Even the same identity provider
and still must remain completely isolated if they belong to different tenants.
3. Multi-Tenancy vs Tenant Isolation (Why They’re Not the Same)
These terms are often confused.
Concept
Meaning
Multi-tenancy
Multiple customers share infrastructure
Tenant isolation
Security boundaries prevent cross-tenant access
You can be multi-tenant without being isolated.
True tenant isolation requires intentional design, not just shared tables with a tenant column.
4. Core Tenant Isolation Strategies (Infrastructure & Data)
There is no single “correct” isolation model. Every approach involves trade-offs.
4.1 Shared Database + tenant_id
This is the most common pattern.
All tenants share the same database. Every row includes a tenant_id.
Advantages
Simple to operate
Cost-efficient
Easy to scale horizontally
Risks
One missing WHERE tenant_id = ? breaks isolation
ORMs can accidentally bypass filters
Background jobs often forget tenant context
This model requires discipline and enforcement, not trust.
4.2 Schema-Per-Tenant
Each tenant has its own database schema.
Advantages
Stronger logical isolation
Easier data export and deletion
Lower accidental cross-tenant risk
Trade-offs
Complex migrations
Operational overhead
Harder to manage at large scale
4.3 Database-Per-Tenant
Each tenant has a dedicated database.
Advantages
Very strong isolation
Clear blast radius
Favored in regulated environments
Costs
Infrastructure complexity
Higher operational cost
Connection management challenges
4.4 Hybrid Isolation Models
Many mature systems combine approaches:
Shared core data
Isolated identity data
Dedicated storage for sensitive tenants
Authentication systems frequently adopt hybrid models because identity data has higher security requirements than most application data.
5. Tenant Isolation at the Application Layer
Isolation begins the moment a request enters your system.
Key principle:
Tenant resolution must happen before any business logic executes.
Common resolution strategies:
Organization subdomain
Explicit tenant ID
Login routing based on email domain
Tenant-specific URLs
Relying only on UI-level isolation is a mistake.Every internal API, service call, and background process must carry tenant context explicitly.
6. Identity & Authentication Isolation
Authentication systems amplify isolation failures because they operate before authorization.
6.1 Tenant-Aware Login Routing
Before authentication starts, the system must know:
Which tenant this login belongs to
Common patterns:
Email domain discovery
Organization selection
Explicit tenant URLs
Dangerous assumptions:
Guessing tenant from email alone
Reusing identity configs across tenants
Defaulting to “first match”
6.2 SAML Isolation Patterns
SAML introduces additional risks because of metadata and certificate reuse.
Strong isolation requires:
One SAML connection per tenant
Separate metadata
Separate certificates
Tenant-scoped ACS URLs
IdP-initiated flows must still validate tenant boundaries, or isolation collapses silently.
6.3 OIDC Isolation Patterns
OIDC isolation failures often come from convenience shortcuts.
Best practices:
One client per tenant
Strict redirect URI enforcement
Tenant-scoped issuer and audience values
Shared OIDC clients create shared trust—often unintentionally.
7. Token, Session, and Cookie Isolation
Tokens are portable trust. Treat them carefully.
Key rules:
sub alone is not sufficient
Tokens must include tenant context
APIs must validate tenant claims explicitly
Sessions and cookies introduce additional risks:
Cookie scoping across subdomains
Shared session stores
Refresh token reuse
If tokens cross tenants, authorization never gets a chance to help.
8. Secrets, Keys, and Cryptographic Boundaries
Isolation isn’t just about data—it’s about cryptography.
Consider:
Per-tenant signing keys vs global keys
Blast radius during key rotation
Secrets stored per tenant
Access control to secret managers
A single global key can undo years of isolation work.
9. Background Jobs, Queues, and Async Systems
Many isolation bugs appear outside request paths.
Common failure points:
Async jobs missing tenant context
Queues shared without tenant tagging
Cron jobs running globally
Event reprocessing without validation
Async systems must treat tenant context as mandatory, not optional.
10. Observability, Logging, and Operational Isolation
Logs and metrics often contain:
User identifiers
Email addresses
Authentication metadata
Isolation best practices:
Tenant-scoped logs
Access-controlled observability
Rate limiting per tenant
Auditing boundaries
Operational visibility should not become a data leak.
11. Testing Tenant Isolation (Rarely Documented, Extremely Important)
Isolation is not real until it’s tested.
Useful tests:
Attempt cross-tenant API access
Replay tokens across tenants
Misroute SSO logins intentionally
Trigger background jobs with wrong context
Treat isolation tests like security tests—not unit tests.
12. Compliance & Security Review Perspective
Security reviewers don’t ask if you’re multi-tenant.
They ask:
How do you prevent cross-tenant access?
What happens when isolation fails?
How do you detect and respond?
Tenant isolation is a foundational control in SOC 2, ISO 27001, and enterprise security reviews.
13. Practical Tenant Isolation Checklist
Resolve tenant before authentication
Enforce tenant context everywhere
Never reuse identity configurations
Scope tokens and sessions by tenant
Isolate secrets and signing keys
Test cross-tenant failures regularly
14. Closing Thoughts: Tenant Isolation Is a Security Boundary, Not a Feature
Tenant isolation is rarely the result of a single design choice. It emerges from hundreds of small, intentional decisions made across application logic, identity systems, infrastructure, and operations.
Authentication and identity amplify every isolation mistake. A misrouted login, a shared token, or a reused configuration doesn’t fail loudly—it fails quietly, crossing trust boundaries before anyone notices.
Teams that scale successfully treat tenant isolation as a first-class security boundary. They design it early, enforce it consistently, and validate it continuously as the system grows. In multi-tenant systems, especially those handling identity, isolation is not optional—it is what separates resilient platforms from inevitable incidents.
*** This is a Security Bloggers Network syndicated blog from SSOJet – Enterprise SSO & Identity Solutions authored by SSOJet – Enterprise SSO & Identity Solutions. Read the original post at: https://ssojet.com/blog/tenant-isolation-in-multi-tenant-systems