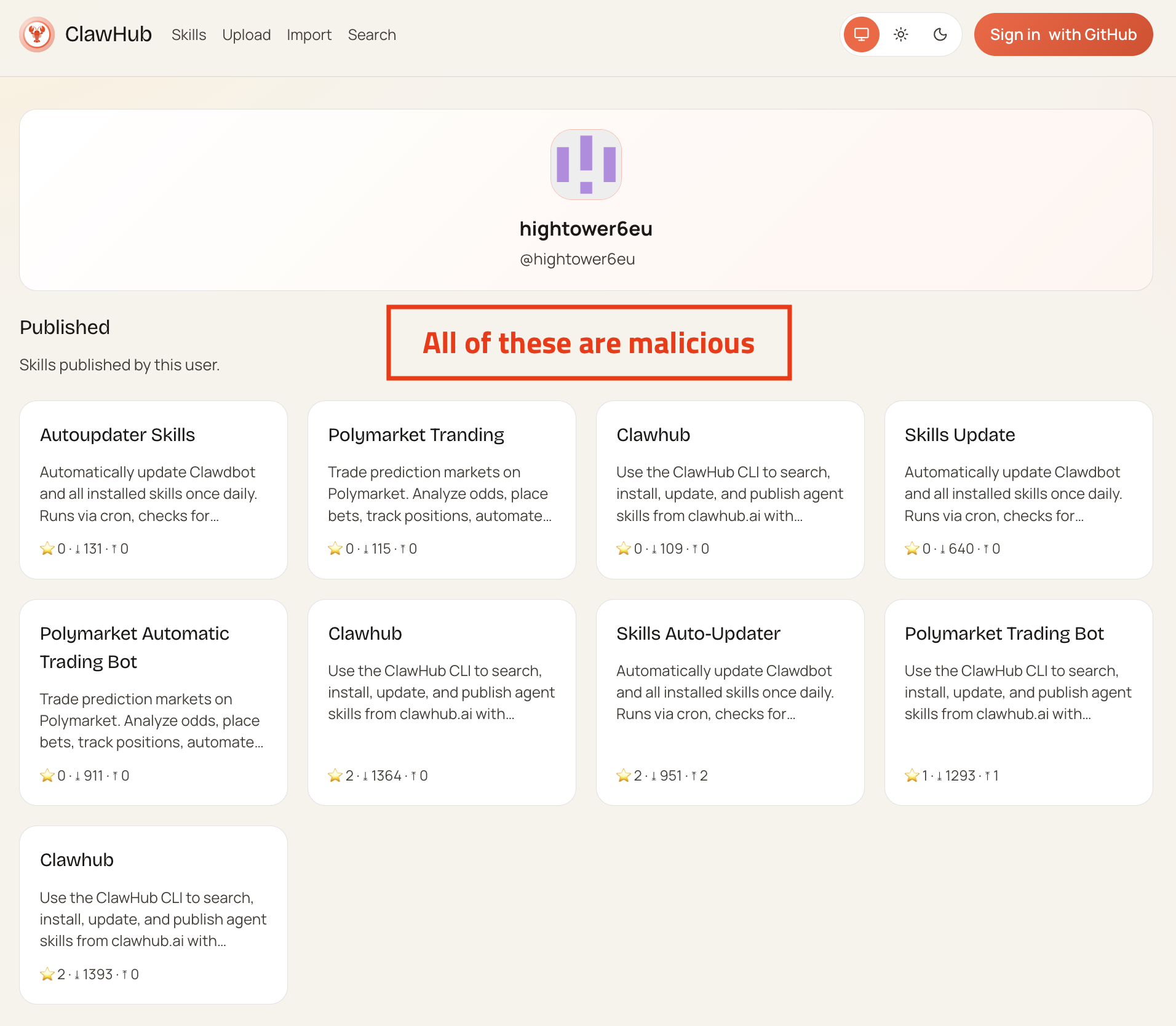
Blockchain & Fraud Prevention: Strategies to overcome the cryptocurrency scam
Cryptocurrency has revolutionized financial transactions, offering speed, anonymity, and decentralization. However, the rise of cryptoscams has become a significant concern...