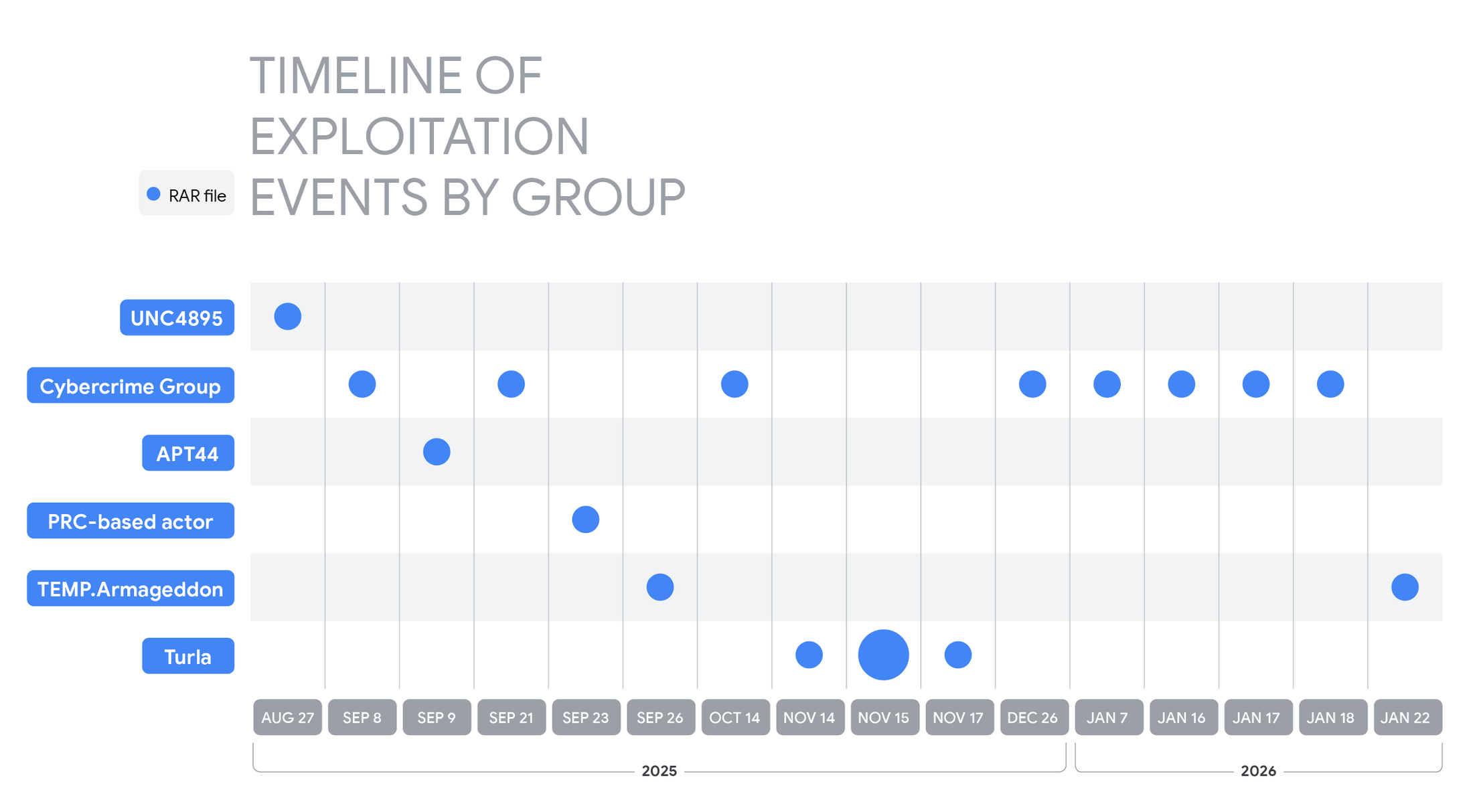
Nation-state hack exploited hosting infrastructure to hijack Notepad++ updates
Nation-state hack exploited hosting infrastructure to hijack Notepad++ updates Pierluigi Paganini February 02, 2026 Notepad++ maintainer says nation-state attackers hijacked...